Tab Nabbing in profile page which can lead to a phishing attack on www.Instahyre.com
Reported: 2021-01-05
Introduction
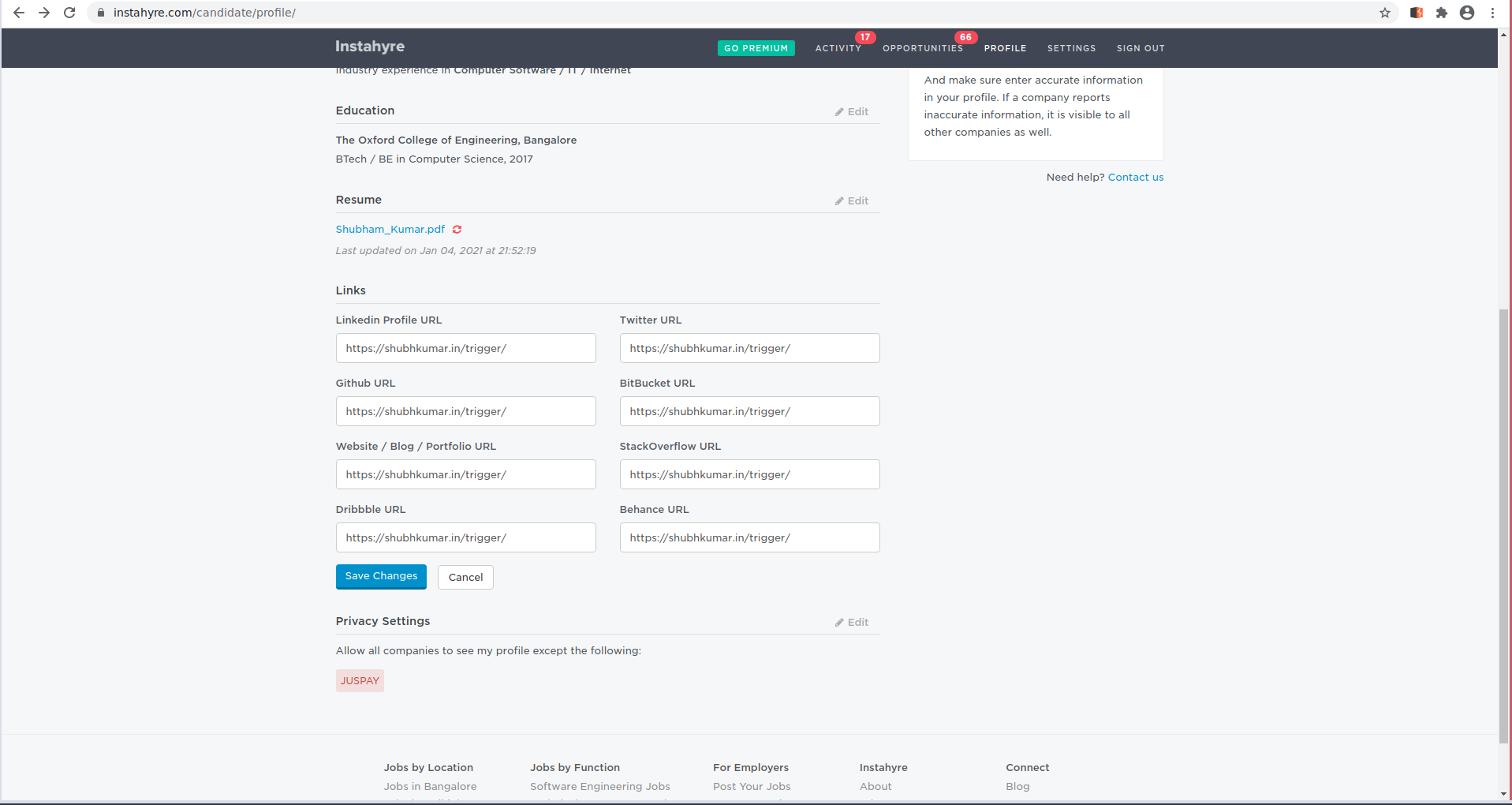
An issue which reside on the Instahyre profile page, where any user is allowed to submit a link to Link Section.
The handling of how the page is opened to a new tab have a issue of tab nabbing, where the child page(new tab) can access the previous page with window.opener property.
Description
Tabnabbing is a computer exploit and phishing attack, which persuades users to submit their login details and passwords to popular websites by impersonating those sites and convincing the user that the site is genuine.
which is found on https://www.Instahyre.com/candidate/profile/ page where users can submit URL in Link Section.
A malicious actor can submit a link which they control. can submit a link which contain a JavaScript code like
1 | if (window.opener){ |
along with a valid content on the page.
The Issue lies in how the link open a page in new tab, with target="_blank".
Steps to reproduce
I have kept a malicious page hosted which contain the following code.
1 | <html> |
On https://shubhkumar.in/trigger/
On User Profile You can submit the above URL On any of the Links.
You can use the same profile or login with different Employer account who is looking at the user profile.
Click on the link to open the content i.e https://shubhkumar.in/trigger/.
This will open that page on the new tab but also redirect https://www.Instahyre.com/candidate/profile/ to https://shubhkumar.in/poc/ in background.
PoC
Remediation
The Above issue can be easily solved by adding rel="noopener nofollow" as the attribute to the link.
Impact
As most of the people who are viewing the candidate profile are from Hiring team who are attacker prime target for Phishing attack. An attacker can create few or multiple account on Instahyre and start submitting these malicious links and applying to random or targeted companies. When a employer clicked on any such link they might be presented with a fake Instahyre login screen where they may submit there credentials and leading to compromise of there account.
The same thing can with any internal Support or admin user, where an instahyre employee credentials could be compromised using Phishing with the above attack vector.
References
- https://owasp.org/www-community/attacks/Reverse_Tabnabbing
- https://dev.to/ben/the-targetblank-vulnerability-by-example
- https://mathiasbynens.github.io/rel-noopener/
- https://raw.githubusercontent.com/cure53/browser-sec-whitepaper/master/browser-security-whitepaper.pdf
- https://medium.com/@jitbit/target-blank-the-most-underestimated-vulnerability-ever-96e328301f4c