Summary
Meta was a Medium difficulty Linux box created by Nauten. Initial foothold on the box was to find RCE in exiftool and uploading the modified image with payload to get a shell we get a shell as www-data. Running pspy we see an cron running every minute with a script running we upload a modified svg and we get a shell as user. Rooting the box was pretty simple with just modifying the XDF_CONFIG_HOME and running neofetch with sudo and we get a shell as root.

Initial Enumeration
Running nmap we find
1 | # Nmap 7.92 scan initiated Sun Jan 23 08:30:42 2022 as: nmap -sC -sV -oN nmap/meta 10.129.140.72 |
We also see artcorp.htb
We find
1 | judy |


1 | gobuster vhost -u http://artcorp.htb -w /opt/tools/SecLists/Discovery/DNS/subdomains-top1million-110000.txt |
Running go-buster give us a different subdomain.
Opening the subdomain we see the application MetaView

Checking that we

Trying it out it seem to be an image MetaView viewer.

Trying with a php file we see only jpg and png are allowed. Trying multiple way to bypass we are unable to bypass this.

Now focusing on the output we see it is seem to be an exiftool output

Trying some command injection we see we are unable to inject anything.
Lets look for some vurnebility in exiftool and we find blog
Using exploit
we are able to get a shell as www-data
www-data

Running pspy we see a cronjob running as user thomas
which is
1 | <image authenticate='ff" `echo $(id)> ./0wned`;"'> |
We can get the ssh key of thomas and login on the box and grab user.txt
Privilege Escalation

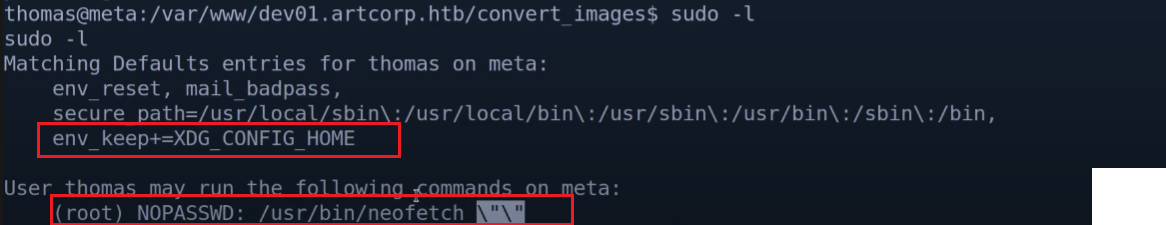
We see XDG_CONFIG_HOME is kept so we can modify that and pass that as env and get root.


Rooted the box