Summary
Delivery,a Linux box created by HackTheBox user ippsec. The Box don’t contain any exploitation and was about Enumerating the box properly. The Initial Enumeration Shows that mattermost is running and we need an @delivery.htb email to register to the box. Along side that an HelpDesk is running and creating a Ticket give us an email to that ticket. We can combine both to register an User and use that to get get into Mattermost. Checking Mattermost we get multiple hints for root also credential to get user. After ssh in the box we can use the hint and find root password hash for mattermost in mysql db. and from the hint we know we can crack the password PleaseSubscribe! along with rule and get root shell.
Initial Enumeration
nmap
1 | # Nmap 7.91 scan initiated Mon Jan 11 11:44:17 2021 as: nmap -sC -sV -oN nmap/delivery 10.10.10.222 |
We see port 80 is open
Web
Clicking around we see contact us page
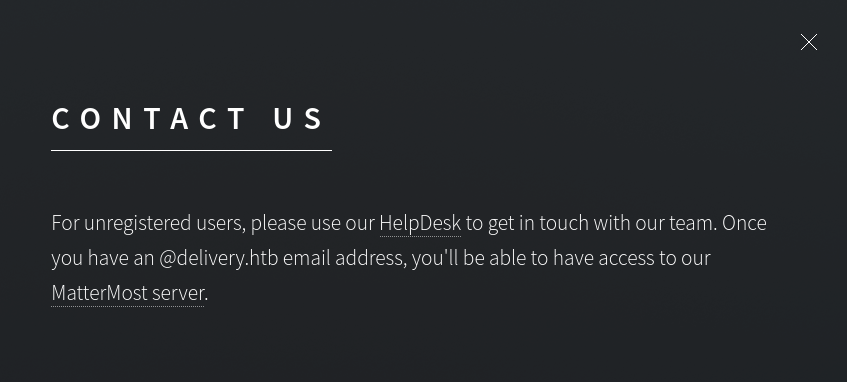
Okay we get two domains from the link one is delivery.htb also on the HelDesk link we get helpdesk.delivery.htb as another subdomain
Mattermost
Checking about we know it is some kind of internal chat tool.
Opening the page
We see an login page but also an Create one now
and from the contact us page we know we need an @delivery.htb email id to register.
So lets just try that.
After filling in the details we are redirected to verify email page
So now i think we need to get an @delivery.htb so we can register on Mattermost
Help Desk
Lets explore helpdesk
Lets try to create a Ticket
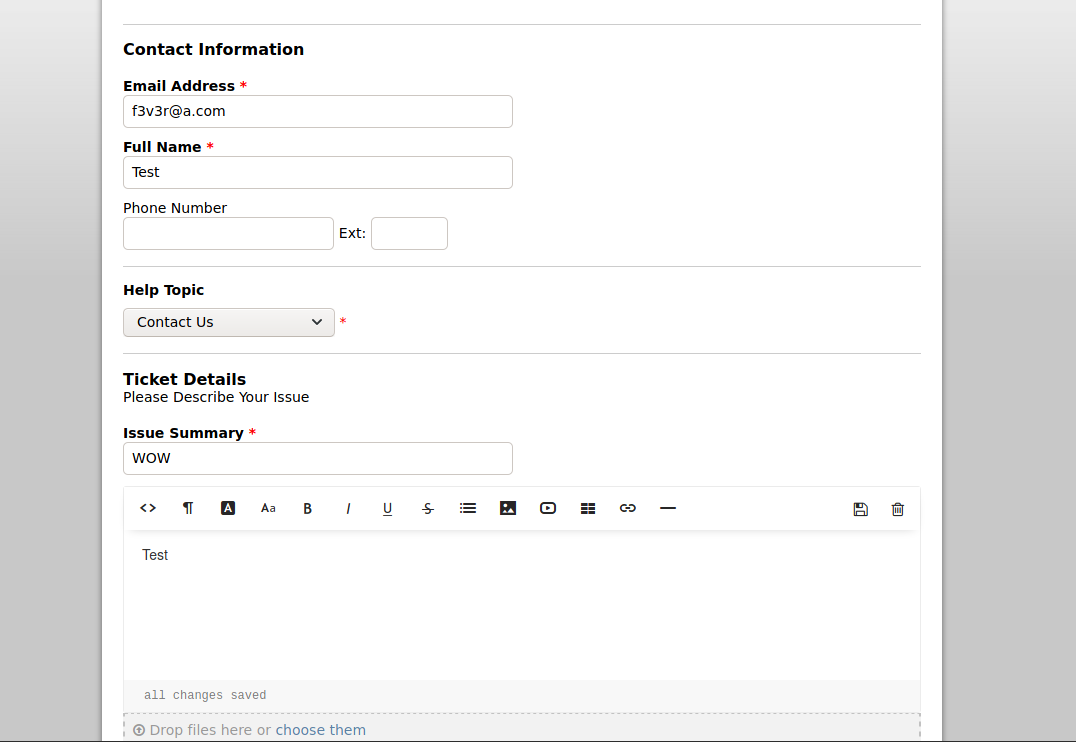
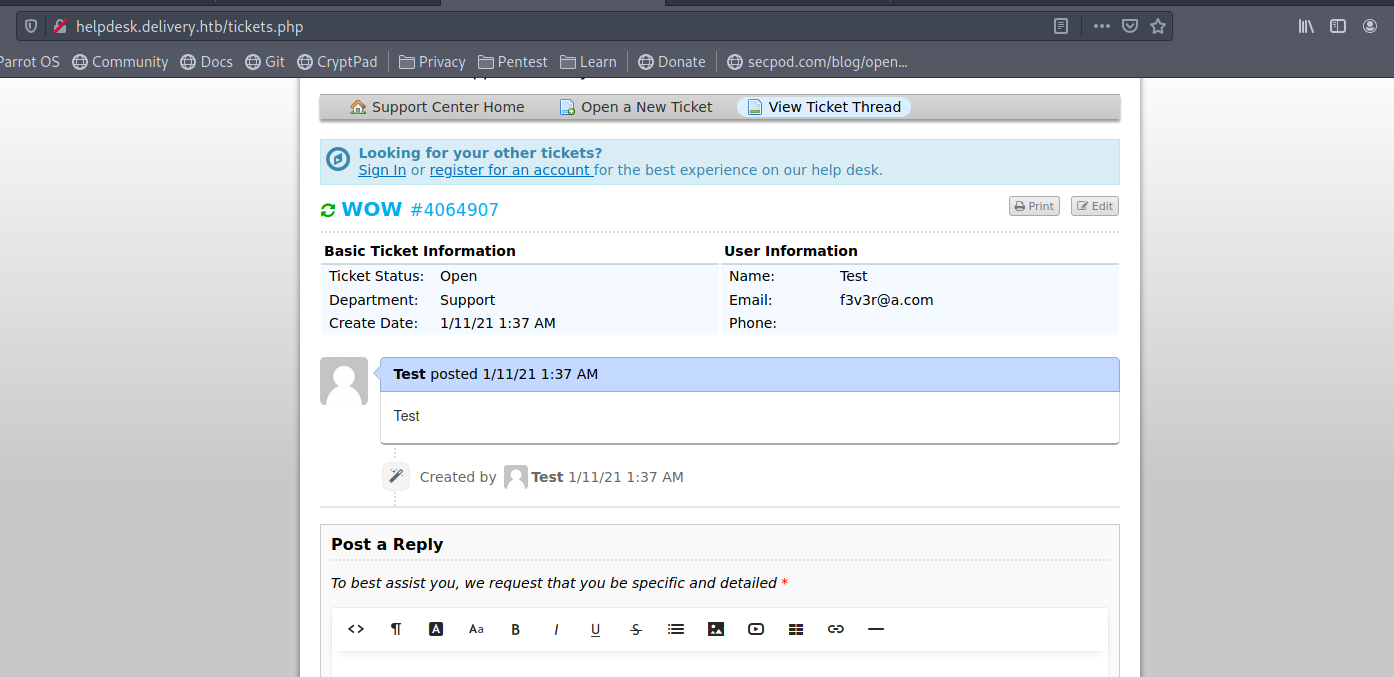
after creating the ticket we get an temporary email as 4064907@delivery.htb
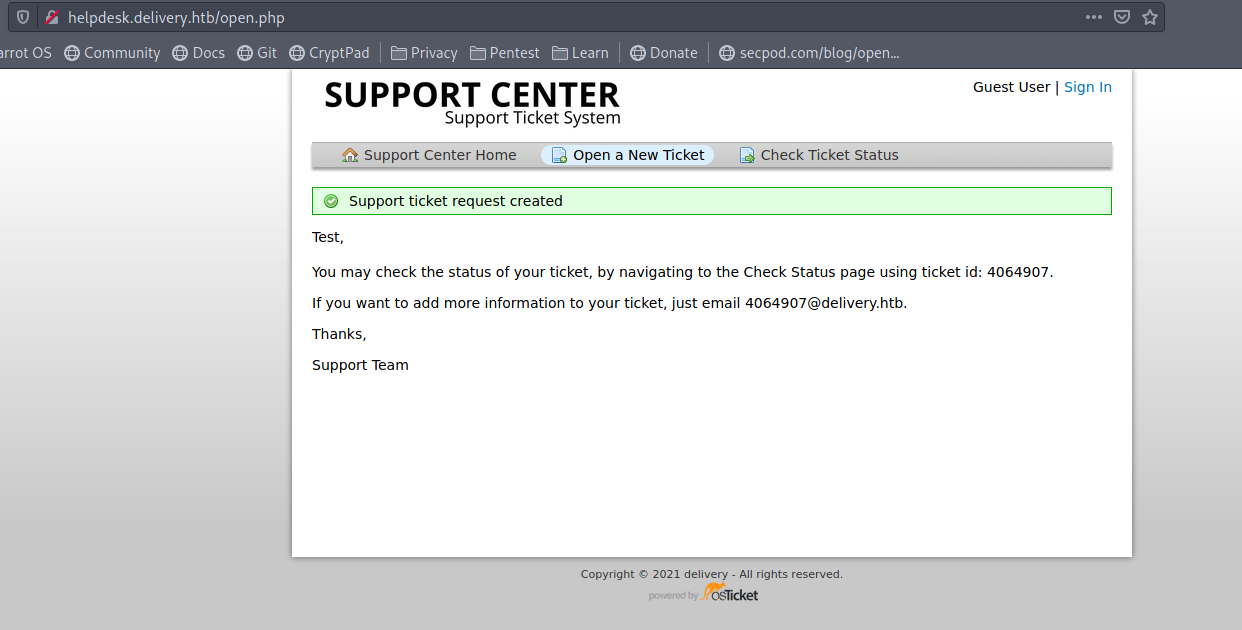
Checking ticket status using Check Ticket Status
Which get us an Support Thread but that can also act as a mailbox
Going back to Mattermost we can use the above email and register an account
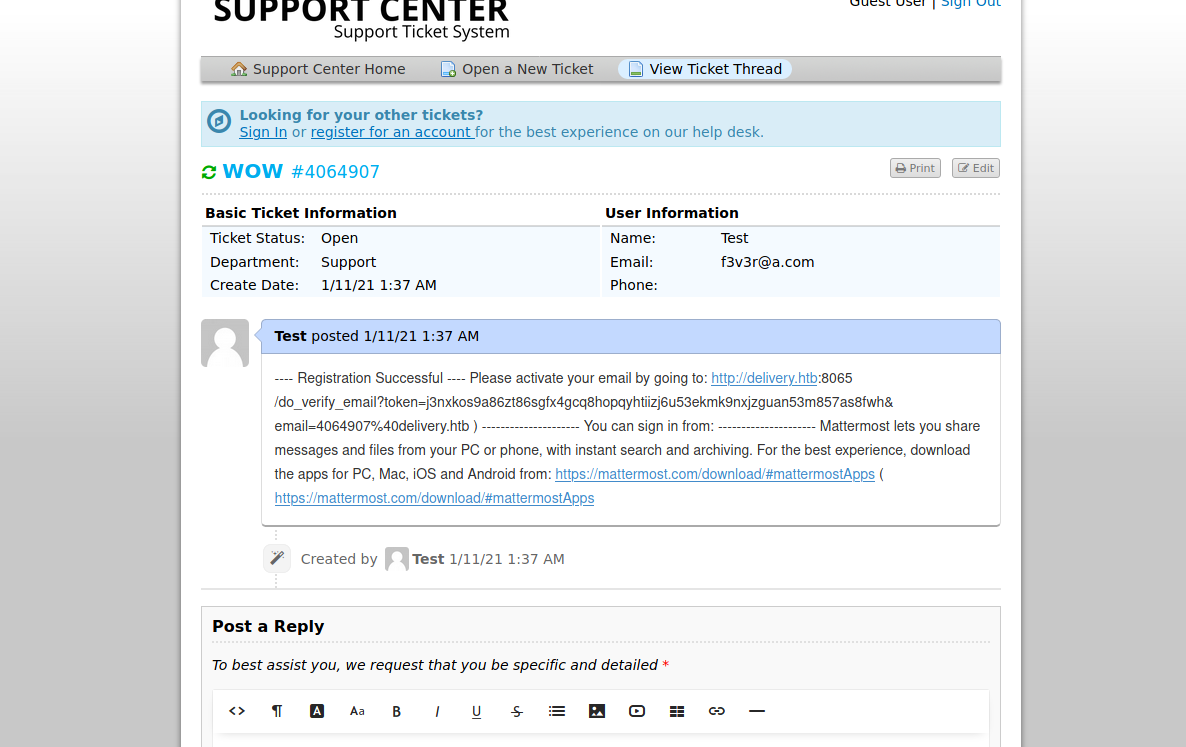
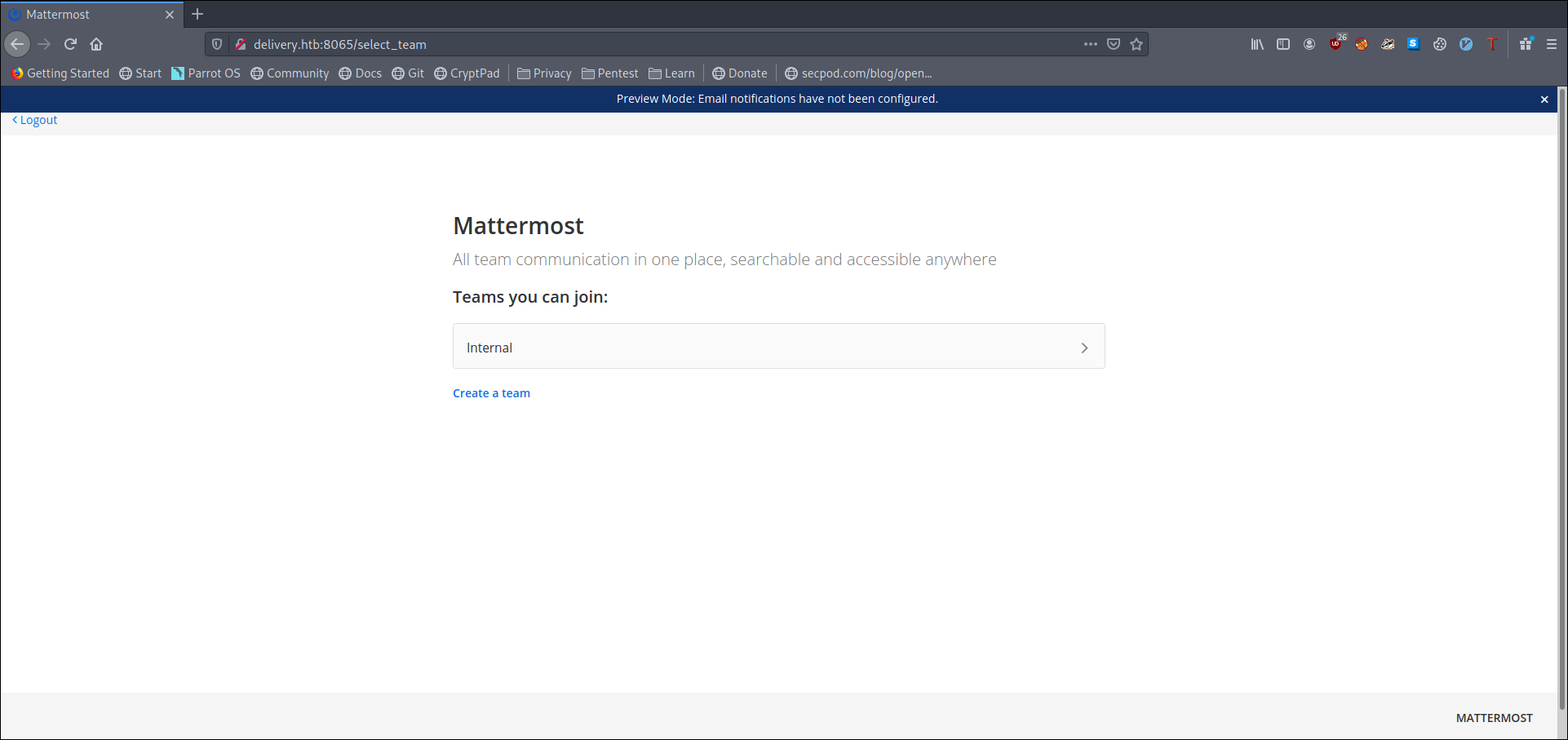
and we see a message from root which contain credential
as
1 | maildeliverer:Youve_G0t_Mail! |
and also few hints
1 | Also please create a program to help us stop re-using the same passwords everywhere.... Especially those that are a variant of "PleaseSubscribe!" |
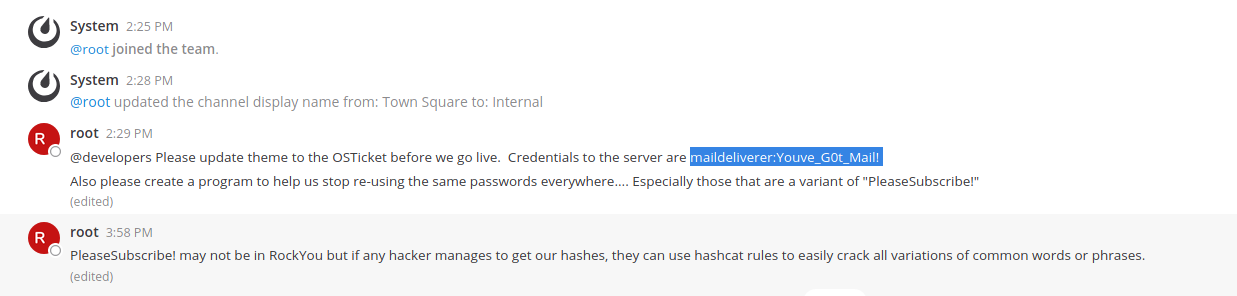
User
Using the above Credential maildeliverer we get user
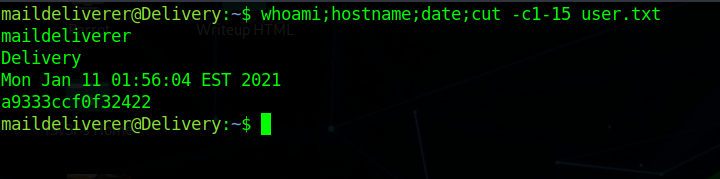
Enumerating the box we find a db-creds
in mattermost config in /opt/mattermost/config/config.json
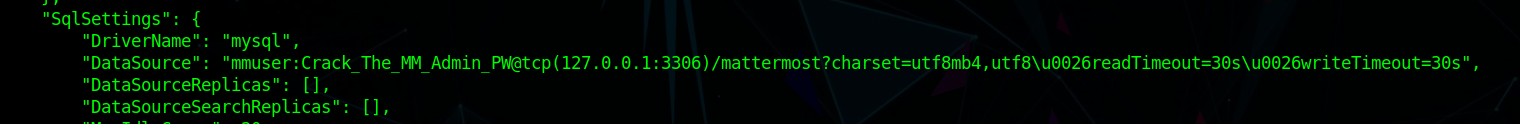
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
1 | mysql -u mmuser -p'Crack_The_MM_Admin_PW' mattermost |
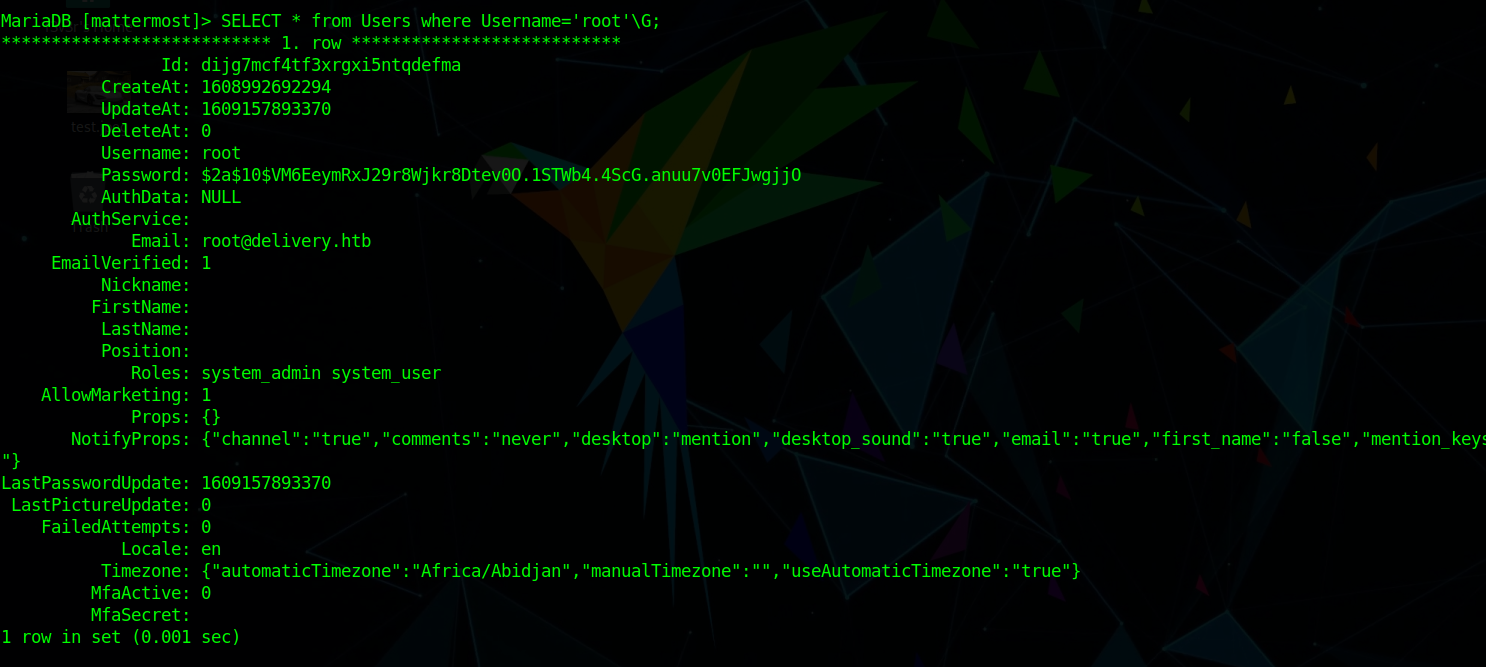
tring show tables we see User table
1 | SELECT * from Users where Username='root'; |
We get root password hash
1 | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
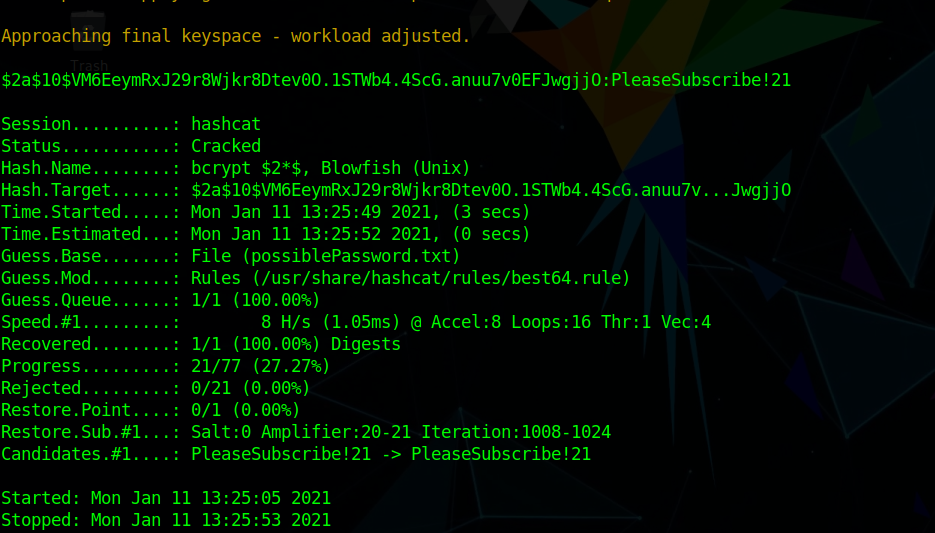
I tried cracking the password using
1 | hashcat -m 3200 hash.txt possiblePassword.txt -r /usr/share/hashcat/rules/best64.rule --force |
which cracked the password as
PleaseSubscribe!21
Root
Using the password PleaseSubscribe!21 we get root shell
and we can grab root.txt